[ad_1]
The cybercrime underground is seeing a dramatic shift in Android malware operations, driven by the rise of new malware-as-a-service (MaaS) platforms such as PhantomOS and Nebula.
What once required substantial technical skill and infrastructure can now be rented as a plug-and-play toolkit for a few hundred dollars per month, marking a pivotal transformation similar to the early days of ransomware-as-a-service (RaaS).
Turnkey Malware-as-a-Service Platforms
No longer limited to highly skilled criminals, these new MaaS offerings are marketed directly on cybercrime forums and encrypted messaging services such as Telegram, often with full support infrastructure and backends set up for the customer.
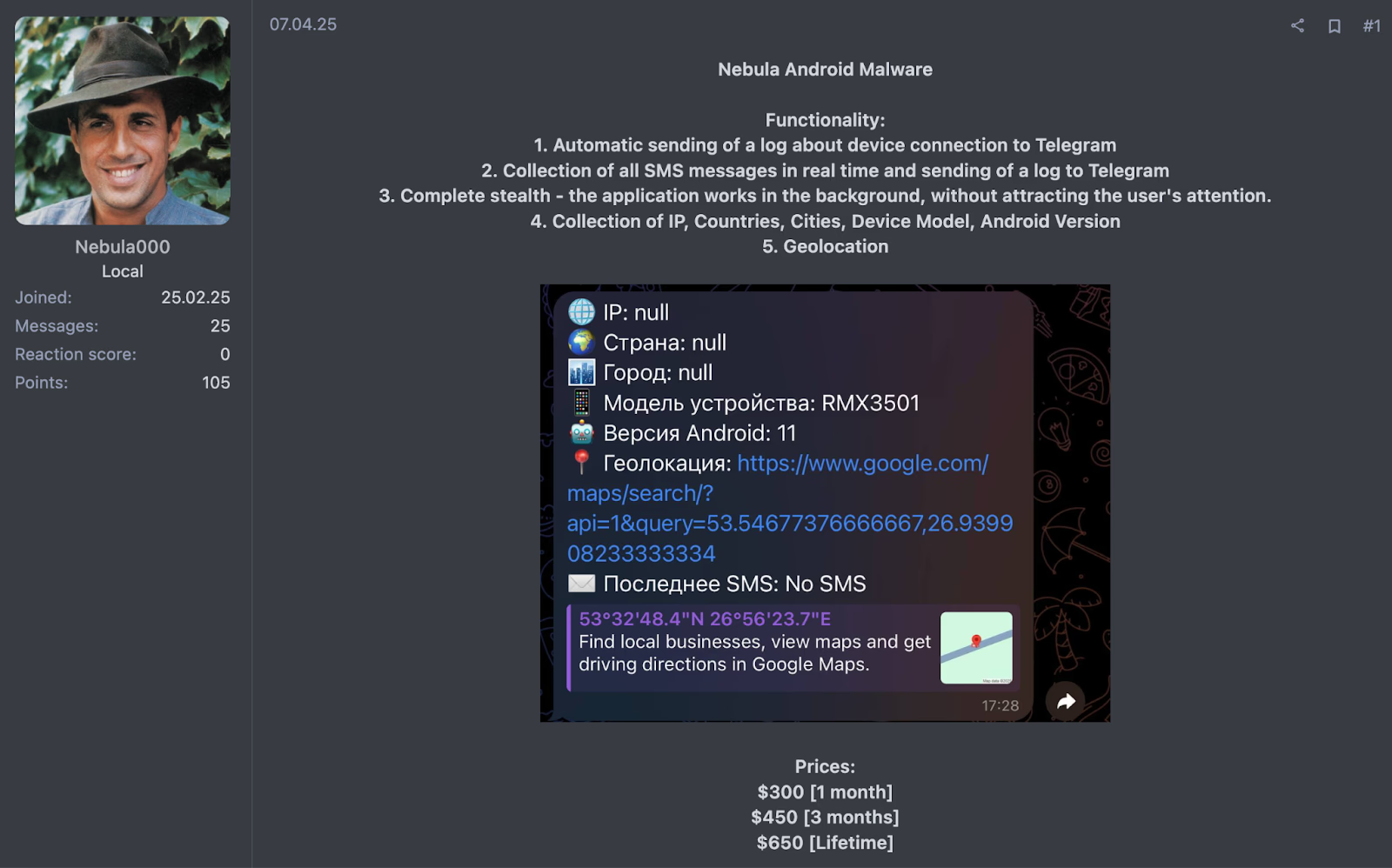
Attackers can rent fully managed Android trojans, banking malware, spyware, and botnets with advanced features that include interception of one-time passcodes (OTP) for two-factor authentication (2FA), antivirus bypass, silent app installation, GPS tracking, and even phishing overlays customized for specific brands or financial institutions.
PhantomOS, for example, touts “the world’s most powerful Android APK malware-as-a-service” and enables remote installation and hiding of malicious apps on a victim’s device, alongside automated harvesting of SMS, OTP codes, and credentials.
The entire backend infrastructure the core command-and-control servers, Telegram-based management bots, and update delivery are provisioned for the attacker.
This allows even those with zero coding ability to operate complex malware through a straightforward chat interface, issuing commands, fetching stolen data, or even specifying targets by name (“Coinbase”, “HSBC”) to receive tailored phishing overlays.
Similarly, cheaper offerings like Nebula promise stealth background operation, exfiltration of texts, call logs, and location data, and automated updates bundled in a monthly subscription that often starts at just $300.
Phishing Overlays
Detection evasion is a core selling point for these services. MaaS developers and their distribution partners arm their APKs with advanced crypting and packing technologies, making them “fully undetectable” (FUD) by antivirus scanners and Google Play Protect.
Some even claim capability to disable security protections on the device directly. This constant cat-and-mouse game encourages operators to offer regular cryptographic packer updates to subscribers, ensuring that each new version has unique signatures and evades detection.
Many services both bundle their own crypting tools and integrate with dedicated crypter-as-a-service vendors, reinforcing industrial-grade obfuscation as a routine feature.
Distribution techniques have also matured and scaled. MaaS platforms provide exploit kits and social engineering frameworks for large-scale deployment, with overlays for hundreds of banks and payment services, making credential theft largely automated.
Some sellers offer technical exploit kits exploiting devices with open Android Debug Bridge (ADB) ports or known vulnerabilities, enabling mass infection of misconfigured or outdated devices with minimal interaction.
According to the report, these exploit frameworks, priced from a few hundred to over a thousand dollars, allow attackers to “point and shoot” simply selecting lists of IPs to quickly compromise new Android bots.
Perhaps the most notable development is the emergence of bulk “install” markets for compromised devices.
Operators can bypass the challenge of initial infection by simply purchasing access to already-infected phones, chosen by geography or device type, with pricing varying accordingly.
Sellers deliver fresh installations in the buyer’s preferred region, charging per 1,000 devices, and even offer botnet management tools such as Hydra for additional fees.
Comprehensive packages for malware rental, bulk installs, and control infrastructure can be assembled for under $3,500, democratizing access and making professional-grade Android fraud possible for anyone with basic underworld connections and a few thousand dollars in crypto.
The convergence of ready-to-deploy malware, crypting services, turnkey distribution, and bulk-infected device markets represents a fundamental shift.
Android MaaS is rapidly normalizing professional-grade cybercrime, breaking down technical barriers, and putting potent surveillance, banking fraud, and ransomware capabilities within reach of even the least-skilled threat actors.
As detection evasion and delivery continue to improve, the risk landscape for Android users is set to escalate sharply posing a major challenge for defenders and security teams worldwide.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates
[ad_2]
Source link
Click Here For The Original Source.

