[ad_1]
A new and menacing player has emerged in the cybercrime landscape with the introduction of Anubis, a Ransomware-as-a-Service (RaaS) operation that blends traditional file encryption with a devastating file destruction capability.
Active since December 2024, Anubis has quickly gained notoriety in 2025 for its unique “wipe mode” feature, which permanently erases file contents, rendering recovery impossible even if victims comply with ransom demands.
A Dual-Threat Evolution in Ransomware-as-a-Service
According to Trend Micro Report, this dual-threat approach marks a significant escalation in ransomware tactics, targeting industries like healthcare, engineering, and construction across regions including Australia, Canada, Peru, and the U.S.
With seven victims already listed on its leak site, Anubis demonstrates an opportunistic strategy, exploiting a wide range of targets through sophisticated attack chains that include spear-phishing as the initial access vector (T1566) and command-line execution (T1059) for deployment.
Delving into the technical intricacies, Anubis operates with a multi-layered extortion model, supported by a flexible affiliate program advertised on cybercrime forums like RAMP and XSS under monikers such as “superSonic” and “Anubis__media.”
Technical Depth of a Destructive Attack Chain
Its attack chain leverages tactics like privilege escalation through access token manipulation (T1134.002) by checking for administrative rights via low-level operations like accessing “.\PHYSICALDRIVE0.”
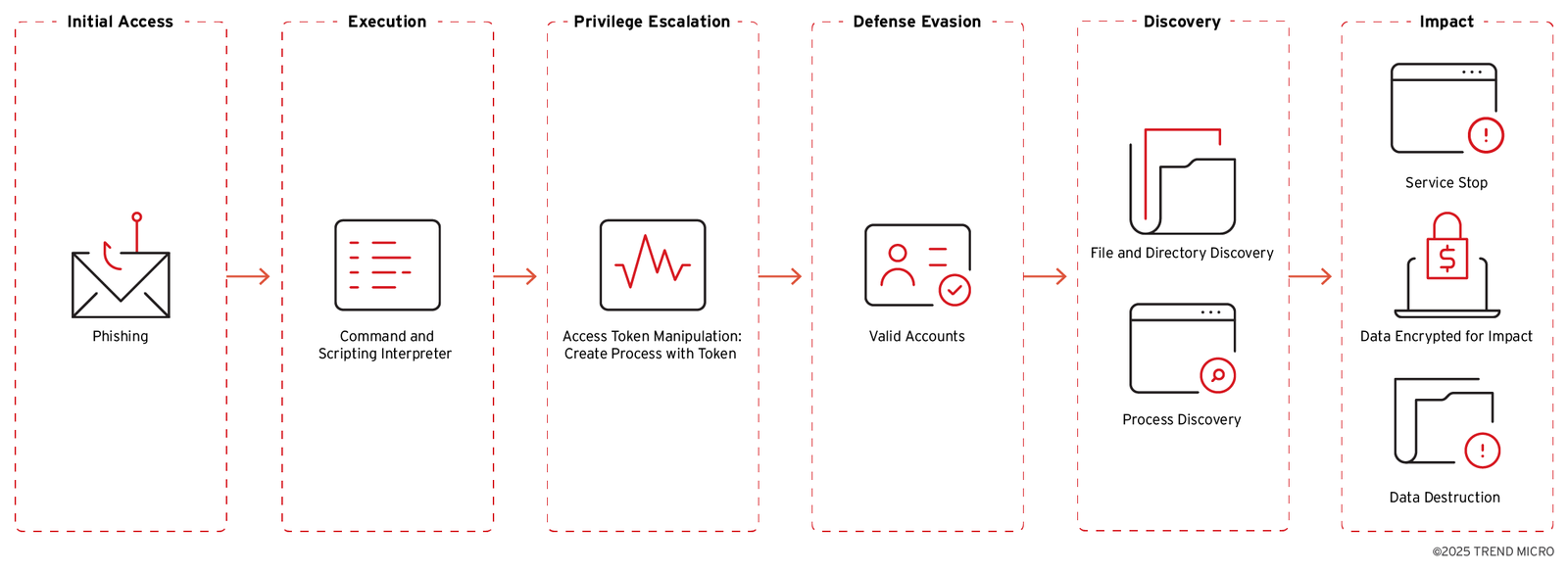
If admin privileges are detected, it elevates to SYSTEM level; otherwise, it prompts for user input or relaunches with elevated parameters.
The ransomware employs the Elliptic Curve Integrated Encryption Scheme (ECIES), publicly available on GitHub in Go, for encryption (T1486), appending the “.anubis” extension to files and altering system icons with its logo.
Beyond encryption, its destructive “wipe mode,” activated via the /WIPEMODE parameter, obliterates file contents, leaving them as 0 KB shells (T1485).
It further inhibits recovery by deleting Volume Shadow Copies using commands like “vssadmin delete shadows” (T1490) and stops critical services (T1489).
Additional defense evasion techniques include using valid accounts (T1078) and avoiding specific system directories during encryption (T1083), showcasing its calculated approach to maximizing damage.
Anubis also enhances its psychological impact by dropping custom icons (“icon.ico”) and attempting to change desktop wallpapers (“wall.jpg”), alongside delivering a ransom note named “RESTORE FILES.html” that threatens data leaks via double extortion.
First observed as a prototype named Sphinx in December 2024 with an incomplete ransom note, Anubis has since evolved into a polished threat, combining core malware similarities with updated branding.
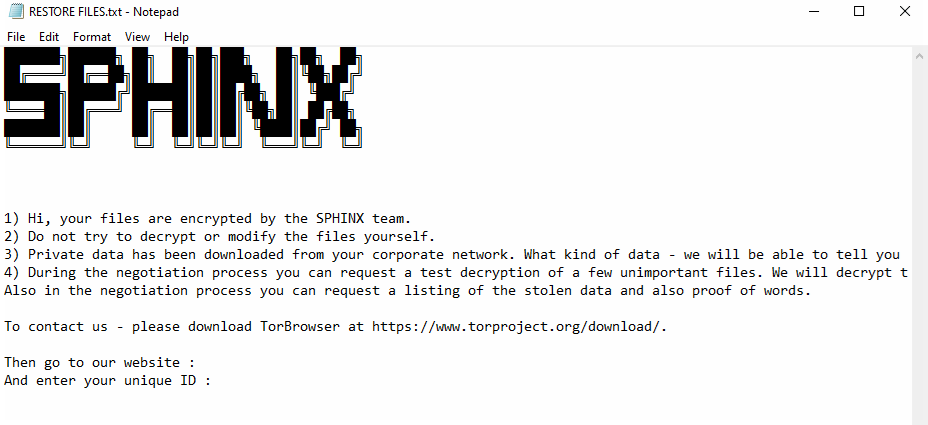
Its affiliate program, negotiable for revenue splits, extends monetization through data extortion and access sales, positioning it as a formidable force in the RaaS ecosystem.
Enterprises are urged to counter this threat with robust defenses, including offline backups to mitigate wiping capabilities, strict access controls to limit privilege escalation, and multilayered security with endpoint protection and phishing awareness training.
As Anubis continues to refine its destructive potential, its emergence signals a critical need for heightened vigilance and proactive cybersecurity measures to safeguard against such evolving cyberthreats.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates
[ad_2]
Source link
Click Here For The Original Source.


.png)