[ad_1]
LAS VEGAS—People do strange things in the middle of a house robbery, like make a sandwich or take selfies. Is it all that odd, then, that an infostealer malware cyberattack might leave some selfies behind? It’s true: Many malware campaigns leave screenshots behind that the attackers use to sell the data they’ve stolen. But a presentation at the Black Hat cybersecurity conference in Las Vegas explored how LLMs (large language models) can process these images and other traces to understand infostealer attacks and ultimately prevent them.
Estelle Ruellan, threat intelligence researcher at cybersecurity company Flare, came up with the idea and built the LLMs to implement the analysis. She presented her research, backed by Olivier Bilodeau, Flare’s principal security researcher.
What Is Infostealer Malware?
Bilodeau first explained how infostealer malware works. “The user downloads malware, usually cracked software. That malware steals everything it can access. It doesn’t require admin rights, though if it gets that access, it can steal more. It grabs crypto wallets, password manager data, even the clipboard contents.” Sound familiar? It may be a new term, but you’re probably familiar with the type of attack.
(Credit: Flare)
“The malware packages up this data and uploads it to its command and control server,” he continued. “It often uses Telegram. Then the logs are resold to cyber criminals, again on Telegram. You buy a subscription, and the stealer campaign will send you logs daily.”
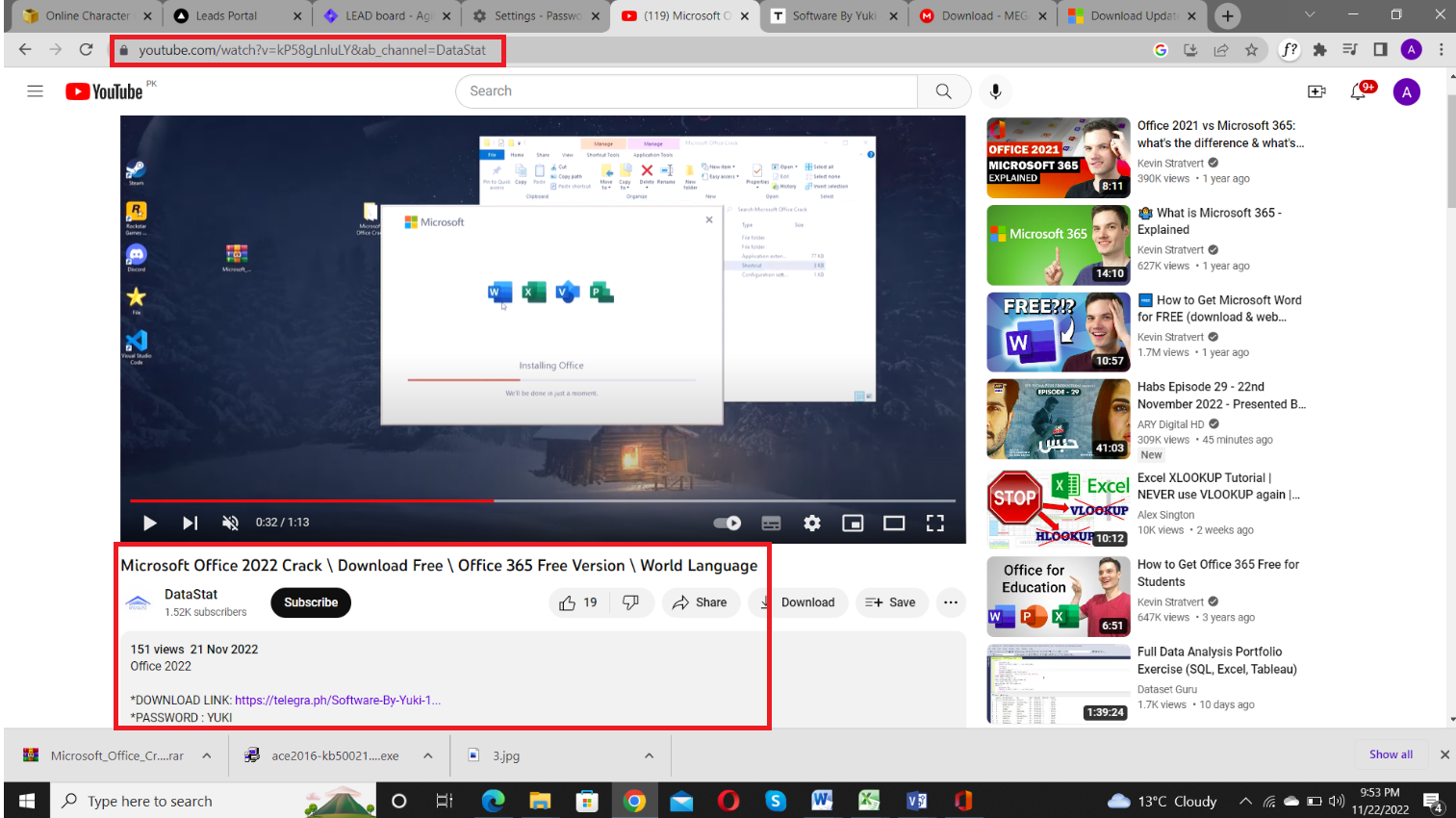
Bilodeau didn’t specify just how they did it, but the team acquired millions of these stolen information packages. “We are looking at these post-infection artifacts, and today we are focusing on screenshots,” he said. He explained that the campaigns take screenshots of their own activities to help do things like detect if they’re running in a sandbox. “They are taking selfies of a crime scene,” he said. “There’s so much info we can extract.”
“But analyzing a screenshot is time-consuming,” he continued. “There’s too much information. Hey, it’s 2025, everything is AI and large language models. This is where Estelle’s genius comes in.”
How Do PCs Get Infected With Infostealer Malware?
When it comes to how people end up getting this malware on their PCs, it turned out to be less about email attachments or random downloads. More often, it’s people hoping they’re grabbing a free or cheap copy of software they want, but ending up downloading malware. “We saw YouTube as a massive distribution system,” Ruellan said. “It works, and it’s free. Second was Google ads, leveraged to get the top spot. It’s a fast lane to the users’ trust.”
If it’s free and shady, you are likely the victim.
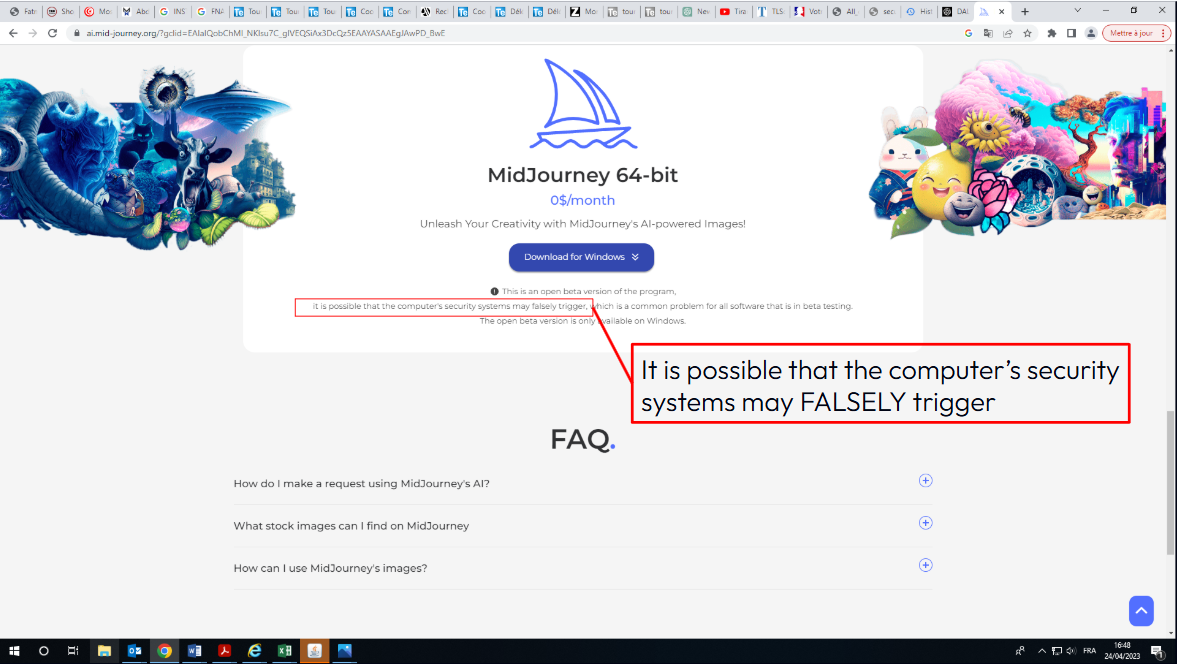
Bilodeau presented two demos of the technique: a campaign promising free access to MidJourney and a Java campaign that they named Java Blitz (because it spread worldwide in a single weekend). “These two successful campaigns used simple tricks,” he noted. “Threat actors rely on simple psychological tactics because they still work.”

Get Our Best Stories!
Stay Safe With the Latest Security News and Updates
Thanks for signing up!
Your subscription has been confirmed. Keep an eye on your inbox!
Two LLMs Are Better Than One
“When I came to this project, I thought I’d just translate my thoughts to the LLM, as if it were a human,” said Ruellan. “It’s a simple task—identify the infection vector. But the LLM did not think or act like a human.”
Recommended by Our Editors
She found that the secret was to use two separate LLMs. The first would analyze each image and generate a formatted text description containing things like visible URLs, descriptions suggesting cracked software, and any text advising the victim to turn off antivirus software for proper installation.
(Credit: Flare)
These formatted descriptions become the input to the second LLM. “The second layer identifies the vector as well as the theme of the campaign,” said Ruellan. “We were able to track the campaigns and, more important, see the tactics used to infect the most people.” She explained that cracked software proved to be a very popular lure, as all too many people would compromise their own security to get something for nothing.
It’s Up to Everyone to Protect Our Data
“Infostealers are quite the threat,” concluded Ruellan. “They are still super active. As long as they keep sharing screenshots, we will be able to track them.” She advised attendees to find ways they can apply their own analyst intuition to an LLM. Going forward, she plans to work on all the artifacts of the stealer logs.
Knowledge is power. By learning the details of infostealer campaigns, researchers can help foil them. The rest of us can do our part by paying attention, not trying to get something for nothing, and practicing good cybersecurity hygiene.
About Neil J. Rubenking
Principal Writer, Security

Read the latest from Neil J. Rubenking
[ad_2]
Source link
Click Here For The Original Source.


