[ad_1]
Microsoft Threat Intelligence has uncovered a sophisticated malware campaign where cybercriminals disguise malicious software as the popular ChatGPT Desktop Application to deploy ransomware across multiple sectors worldwide.
The malware, dubbed PipeMagic, represents a significant evolution in attacker tactics, combining social engineering with advanced technical capabilities to compromise organizations in the IT, financial, and real estate sectors across the United States, Europe, South America, and Middle East.
Exploiting Zero-Day Vulnerability for Maximum Impact
PipeMagic serves as the delivery mechanism for exploiting CVE-2025-29824, a critical elevation of privilege vulnerability in Windows Common Log File System (CLFS).
Microsoft attributes this campaign to Storm-2460, a financially motivated threat actor who uses the backdoor in targeted attacks to deploy ransomware after gaining elevated system privileges.
The attack chain begins when threat actors use the certutil utility to download malicious MSBuild files from previously compromised legitimate websites.
These files appear to be the legitimate open-source ChatGPT Desktop Application but contain embedded malicious code that decrypts and launches PipeMagic directly in memory, making detection significantly more challenging.
Once active, PipeMagic establishes communication with command-and-control (C2) servers through a dedicated networking module, using the domain aaaaabbbbbbb.eastus.cloudapp.azure.com:443, which Microsoft has since disabled.
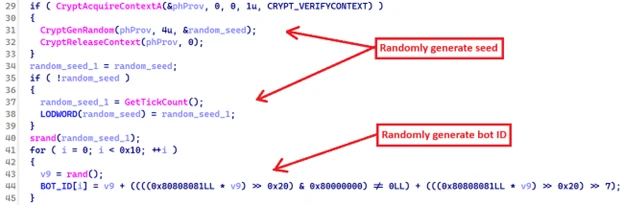
The malware generates a unique 16-byte bot identifier for each infected host and creates a named pipe with the format ‘\.\pipe\1.
Advanced Modular Architecture Enables Persistent Control
PipeMagic’s sophistication lies in its modular design, utilizing four distinct doubly linked list structures to manage different aspects of its operation.
The malware maintains separate lists for payload storage, execution modules, networking components, and an unknown function that researchers believe is leveraged dynamically by loaded payloads.
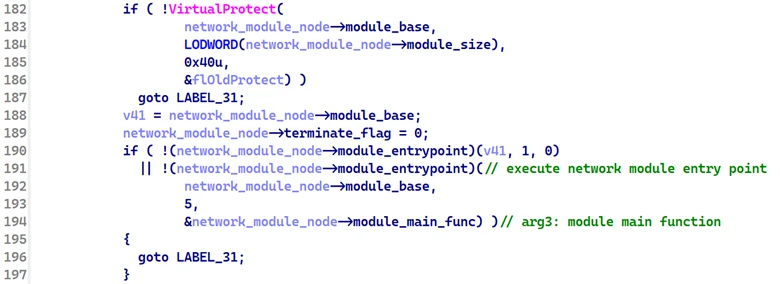
The backdoor supports over 20 different commands, enabling threat actors to perform comprehensive system reconnaissance, manage payload modules, and maintain persistent access.
These capabilities include process enumeration, module manipulation, system information collection, and even self-deletion functionality to cover tracks.
Security researchers have identified the malware’s use of RC4 encryption with hardcoded 32-byte keys and aPLib compression to protect its communications and payload modules.
The malware also implements integrity checking through SHA-1 hash validation to ensure payload authenticity.
Microsoft recommends enabling tamper protection, network protection, and endpoint detection and response (EDR) in block mode within Microsoft Defender for Endpoint to mitigate this threat.
Organizations should also ensure cloud-delivered protection is activated and maintain current vulnerability management practices to prevent exploitation of the underlying Windows CLFS vulnerability.
Indicators of compromise
| Indicator | Type | Description |
| aaaaabbbbbbb.eastus.cloudapp.azure[.]com:443 | Domain | PipeMagic’s C2 domain |
| dc54117b965674bad3d7cd203ecf5e7fc822423a3f692895cf5e96e83fb88f6a | File SHA-256 hash | In-memory dropper (trojanized ChatGPT desktop application) |
| 4843429e2e8871847bc1e97a0f12fa1f4166baa4735dff585cb3b4736e3fe49e | File SHA-256 hash | PipeMagic backdoor (unpacked in memory) |
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
[ad_2]

