[ad_1]
A spike in infostealers and ransomware reveals how stolen credentials are now central to large-scale attacks.
The first half of 2025 has brought major changes to how cyberattacks are launched and carried out. Threat groups have begun relying more on tools that steal personal data from browsers and devices. This shift has helped them carry out more damaging attacks against companies and individuals around the world.
Flashpoint’s latest analysis shows that identity-based intrusions have become the fastest-growing threat this year. The report tracks a steep rise in the use of infostealers, malware designed to extract saved passwords, login cookies, and payment details from everyday devices. These tools now serve as a starting point for more serious threats like ransomware and large data breaches.
Over six months, the number of stolen credentials has jumped by 800 percent. Analysts say this has allowed attackers to move quickly between targets using stolen access, rather than trying to break through with brute-force methods.
How infostealers shape larger breaches
Once malware gains access to a browser or device, it often retrieves saved account data. This can include email logins, work credentials, and session tokens. If attackers can get hold of even a single active session, they may be able to bypass multi-factor security or access internal systems without raising alarms.
This kind of access lets attackers explore deeper layers of a network. In many recent cases, a single compromised device has led to a full-scale breach of a company’s data.
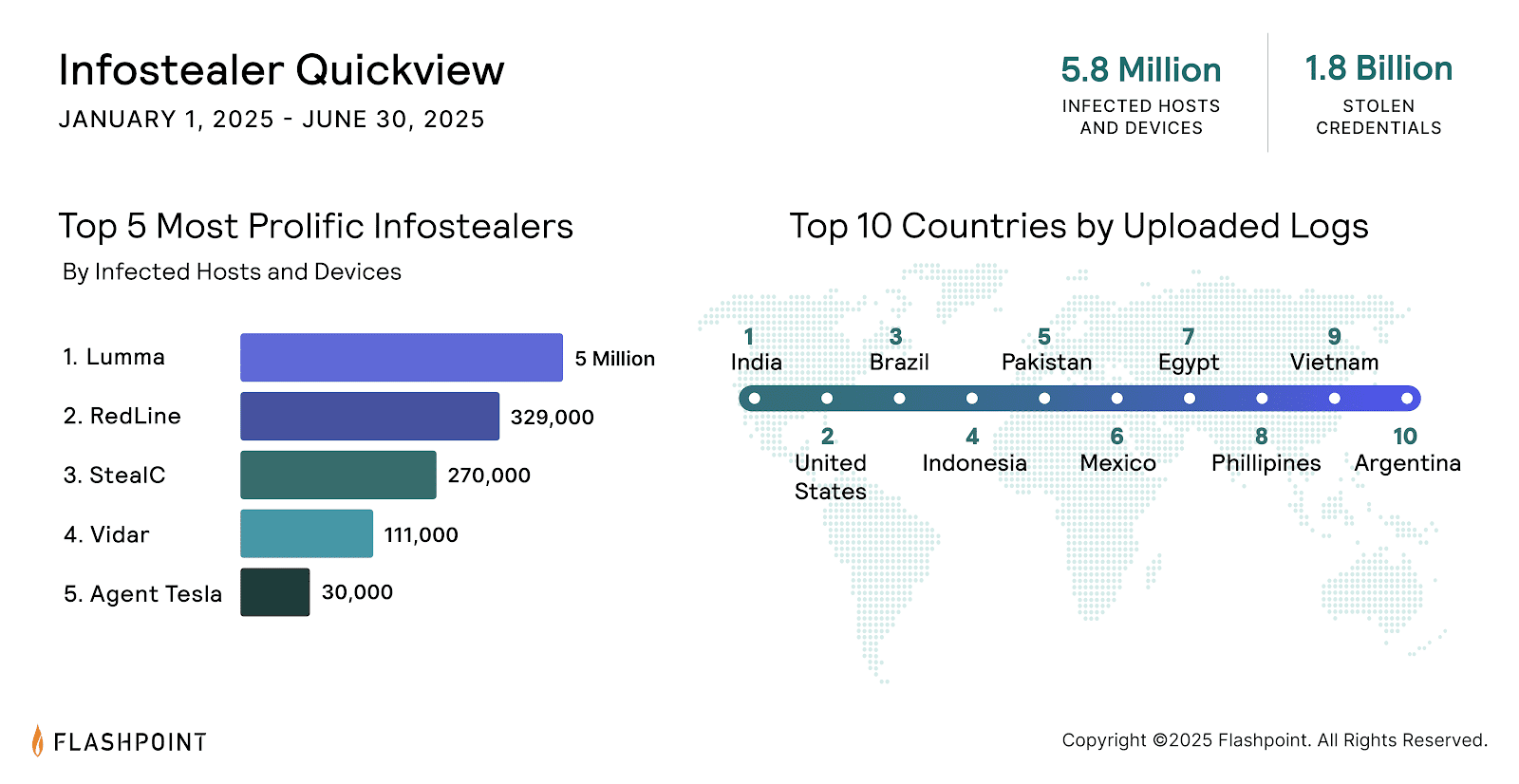
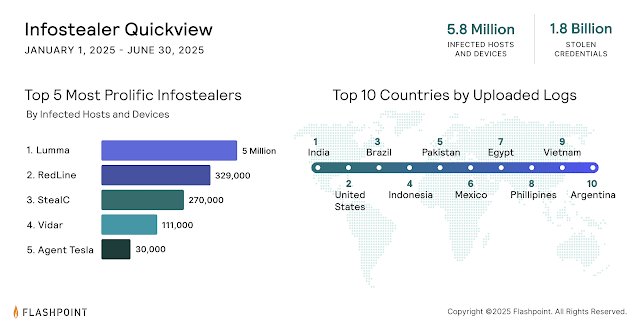
Flashpoint identifies several malware types leading the surge. Lumma and RedLine remain the most active, although other families like StealC and Acreed are appearing more often on cybercrime forums. The tools are often sold at low cost and used repeatedly across different targets.
Ransomware spreads through the same infection points
The same stolen credentials often help ransomware groups break into corporate systems. This type of malware locks files, demands payment, and can also leak sensitive data. Since January, the number of ransomware incidents has risen 179 percent.
Many of these attacks trace back to earlier infostealer infections. The initial access gained through stolen logins often opens a path to internal systems, where attackers then install ransomware. This two-step approach has become a common pattern this year.
Security teams now face threats that combine multiple tools and stages, rather than relying on a single method. The ability to link these threats early is becoming essential.
Public vulnerabilities grow faster than defenses can keep up
Another issue making things worse is the sharp rise in known software flaws. Since February, public disclosures of vulnerabilities have grown by 246 percent. Exploit code for many of these flaws is widely available, up 179 percent in the same time.
Researchers also points to a major lag in public databases that track vulnerabilities. Tens of thousands of issues remain unanalyzed in sources like the National Vulnerability Database. This leaves security teams without critical information as they try to manage growing exposure.
The speed at which attackers take advantage of newly published exploits continues to shrink. In some cases, malware begins using a vulnerability within hours of it appearing online.
Data breaches reflect a wider failure to contain access
Data breaches have also spiked. So far in 2025, their frequency has climbed 235 percent. In 78 percent of the cases tracked, attackers got in through unauthorized access, most often by using stolen credentials.
The United States has been the most affected, with two-thirds of global breaches recorded there. Much of the stolen data includes personal information, which is often used for fraud or resold on dark web platforms. Once released, this kind of data tends to circulate for years.
Some of the biggest breaches in recent months have been linked to logs from infostealers. These logs are often posted on underground sites shortly after collection and then reused in follow-up attacks. Industries like healthcare, telecommunications, and legal services remain especially vulnerable.
Geographic spread of infostealer infections
Flashpoint’s research lists the countries where the most infostealer logs have been uploaded. India ranks first, followed by the United States, Brazil, and Indonesia. Other nations with high infection rates include Pakistan, Mexico, Egypt, the Philippines, Vietnam, and Argentina.
These countries have become prime sources of stolen credentials now circulating online. In many cases, the malware behind these logs was never detected by the original user.
Broader patterns in a shifting landscape
This year’s attacks show a move toward layered threats. A typical campaign might begin with a cheap malware infection, move into credential theft, and end in ransomware or data extortion. This structure allows attackers to cause more damage without increasing effort.
At the same time, the boundary between cybercrime and global conflict is becoming less clear. Threat actors tied to state interests or working in politically unstable regions are using similar tools and tactics. This makes it harder for defenders to separate criminal groups from state-aligned campaigns.
Security teams now face both technical and strategic challenges. Many organizations are still focused on incident response, but that approach no longer matches the speed or complexity of current threats.
A shift toward early detection, attack surface reduction, and more timely intelligence will be critical for stopping these threats before they spread.
Notes: This post was edited/created using GenAI tools.
Read next: AI Models Write Code That Works, But Often Miss Security Basics
[ad_2]
Source link
Click Here For The Original Source.