[ad_1]
Check out the U.S. government’s latest call for developers to use memory-safe programming languages, as well as its warning for cybersecurity teams regarding cyber risk from hackers tied to Iran. Plus, get the latest on ransomware trends, the quantum computing cyber threat and more!
Dive into five things that are top of mind for the week ending June 27.
1 – CISA and NSA call for adoption of memory-safe languages
Once again the U.S. government is urging developers to use programming languages that prevent memory-related vulnerabilities, which allow attackers to maliciously manipulate how memory is accessed, written and allocated.
“Memory-safe languages (MSLs) offer the most comprehensive mitigation against this pervasive and dangerous class of vulnerability,” reads the document “Memory Safe Languages: Reducing Vulnerabilities in Modern Software Development” published this week by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the National Security Agency (NSA).
Specifically, CISA and the NSA recommend that developers use languages such as Ada, C#, Delphi/Object Pascal, Go, Java, Python, Ruby, Rust, and Swift. These languages feature built-in protections against memory safety issues, such as buffer overflows.
For example, memory-safe languages typically offer features such as:
- Bounds checking, which proactively prevents buffer overflows
- Memory management, which reduces the risk of manual memory management mistakes
- Data race prevention, which by default prevents two or more threads from getting unsynchronized concurrent access to a piece of data
- Runtime safety checks, which detect and prevent memory corruption issues
Languages that aren’t considered to be memory safe require developers to be extremely disciplined when coding in order to ensure that memory-handling in their applications will be secure.

CISA, the NSA, the White House and other U.S. federal government agencies have in recent years publicly advocated for the use of memory-safe programming languages.
In addition to improving the security of applications, memory-safe languages also make them more stable, scalable and reliable, which reduces application crashes, lowers the need to issue patches and improves developer productivity, the report states.
However, CISA and the NSA also provide suggestions for hardening existing applications written in non-memory safe languages, in cases where it’s not possible to entirely re-program them.
In addition, the agencies caution against adopting a memory-safe language without doing proper due diligence. “Reducing memory safety vulnerabilities requires understanding when MSLs are appropriate, knowing how to adopt them effectively, and recognizing where non-MSLs remain practical necessities,” the agencies wrote.
They outline elements that organizations should take into consideration when mulling whether to adopt a particular memory-safe language, including:
- The need for an initial, one-time investment in developer training and tools
- The time it will take for developers to master it
- How well the language will integrate with existing codebases, APIs and external libraries
- The availability of tools, libraries and community support for it
- The requirements of the new application
“Achieving better memory safety demands language-level protections, library support, robust tooling, and developer training,” the document reads.
For more information about memory-safe programming languages:
2 – DHS: Beware of cyber threat from Iran
Cybersecurity teams in the U.S. should be on guard against cyber attacks from Iran-backed hackers and hacktivists, resulting from the U.S. involvement in the military conflict between Iran and Israel.
“Low-level cyber attacks against U.S. networks by pro-Iranian hacktivists are likely, and cyber actors affiliated with the Iranian government may conduct attacks against US networks,” the U.S. Department of Homeland Security warned in a National Terrorism Advisory System bulletin.
The agency urges organizations to adopt cybersecurity best practices recommended by CISA in order to boost the protection of networks and internet-connected devices.

Tenable CSO Bob Huber called the DHS bulletin “a stark reminder of the volatile environment that organizations and their cyber leaders operate in” in a blog post this week.
“This isn’t just a geopolitical issue; it’s a direct and immediate challenge to every organization, public and private, operating within the U.S. and beyond,” wrote Huber, who is also Tenable’s Head of Research and President of Public Sector.
That’s why it’s key for organizations to adopt a proactive approach to cybersecurity grounded in exposure management.
“The current geopolitical climate demands a proactive, comprehensive approach to cybersecurity. It’s no longer enough to react to threats, organizations need to anticipate them, understand their exposure and prioritize their defenses where they matter most,” he wrote.
Meanwhile, the Tenable Research Special Operations (RSO) team also published a blog this week answering frequently asked questions about Iranian cyber operations, such as the tools, tactics and techniques employed by Iran-based threat actors.
“This FAQ provides a focused analysis of Iranian state-sponsored cyber threats, detailing the types of threats used by Advanced Persistent Threat (APT) groups, tools, tactics and techniques (TTPs) mapped to the MITRE ATT&CK framework and the specific vulnerabilities they consistently exploit,” the RSO team’s blog reads.
To get more details, read the Tenable blogs “Navigating a Heightened Cyber Threat Landscape: Military Conflict Increases Attack Risks” and “Frequently Asked Questions About Iranian Cyber Operations,” and check out these articles:
3 – Report: Ransomware attacks dropped in May, but AI vector widens risk
Although May saw a drop in global ransomware attacks for the third straight month, the threat level remains high, partly due to the growing risk from organizations’ use of vulnerable AI systems.
That’s according to NCC Group’s “Cyber Threat Intelligence Report – Review of May 2025,” published this week, which also cited geopolitical conflicts and emerging ransomware groups as signs of heightened risk.
“Although reported ransomware incidents declined in March, April, and May, cybersecurity efforts must be strengthened, not scaled back,” Matt Hull, Global Head of Threat Intelligence at NCC Group, said in a statement. The approach of summer may explain the dip in attacks.
Ransomware Attacks by Month
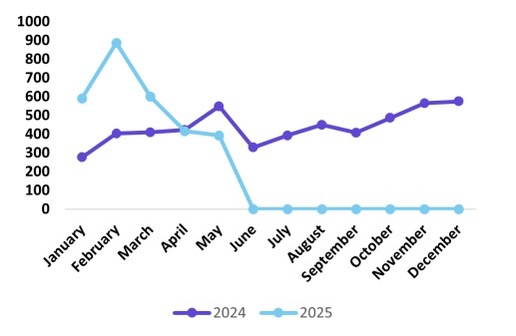
(Source: NCC Group’s “Cyber Threat Intelligence Report – Review of May 2025”)
With regards to the expanded attack surface from AI systems, the report highlighted specifically prompt-injection attacks aimed at breaching AI models, accessing their data and tampering with their responses.
Key takeaways from the report include:
- Global ransomware attacks dropped by 6% in May, compared with April.
- The most active ransomware group was Safepay, a newcomer, with 18% of the attacks.
- The industrials sector was the most targeted sector with 30% of the attacks.
For more information about ransomware trends:
4 – Quantum threat: The time to get ready is now
Here’s another urgent warning regarding the quantum computing threat to data security.
In its report “Approaching Quantum Dawn: Closing the Cybersecurity Readiness Gap Before It’s Too Late,” the Cyber Threat Alliance joins the chorus of experts telling organizations they must start the process to transition to quantum-resistant cryptography as soon as possible.
Here’s the problem: When super-powerful quantum computers become generally available – expected at some point between 2030 and 2040 – hackers will be able to use them to decrypt data protected with today’s public-key cryptographic algorithms.
“Quantum computing is advancing steadily, and while cryptographically relevant quantum computers (CRQCs) capable of breaking current encryption do not exist yet, adversaries are already adapting their strategies,” the report reads.
One of the tactics attackers are embracing is known as “harvest now, decrypt later,” in which they steal sensitive data and store it, with the plan to crack its cryptographic protections with a quantum computer in the future.
The report frames the problem as one that’s steadily unfolding – thus the “dawn” metaphor in its title – as opposed to a problem that’ll erupt all at once at a particular time. It encourages organizations to develop what it calls “cryptographic agility” so that they can progressively upgrade and replace their cryptographic algorithms.
The report includes a “maturity scorecard” for organizations to track their progress in transitioning to post-quantum cryptography (PQC), which is complex, and thus requires careful planning and detailed execution.
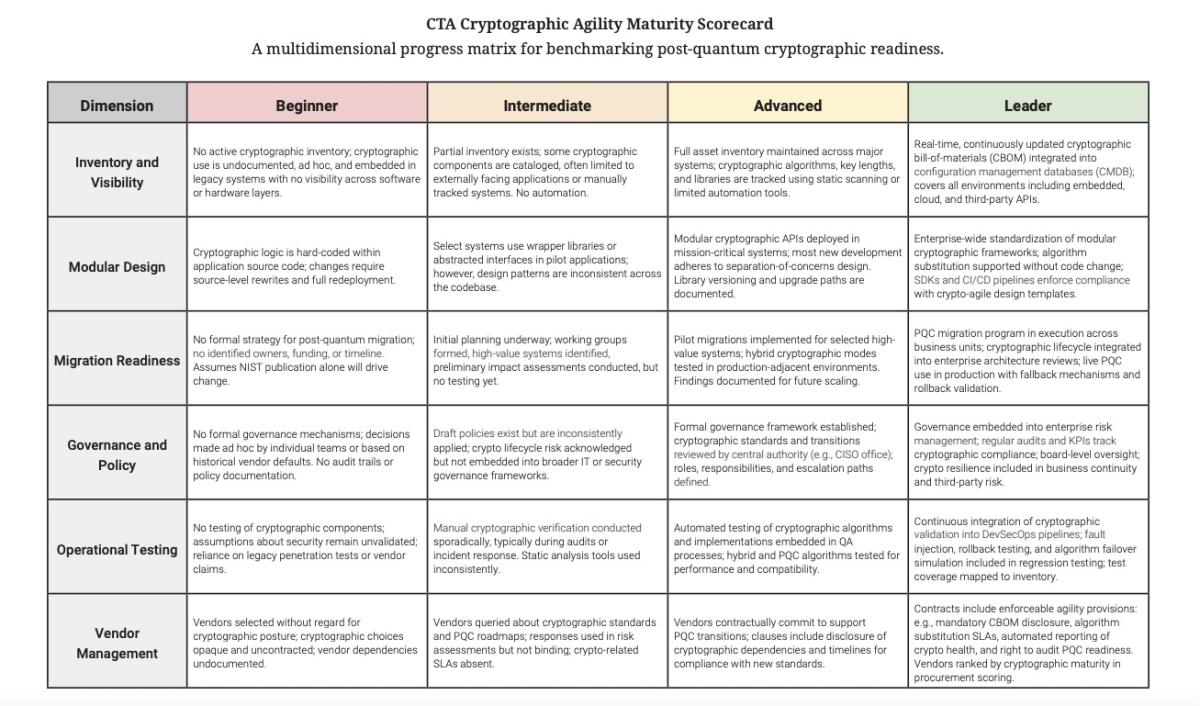
(Source: “Approaching Quantum Dawn: Closing the Cybersecurity Readiness Gap Before It’s Too Late” report from Cyber Threat Alliance, June 2025)
The report also outlines a transition roadmap with short-term objectives to be achieved by next year, and with medium-term objectives to be accomplished by 2030.
Short-term goals include:
- achieving cryptographic inventory visibility
- deploying crypto-agile architectures
- implementing post-quantum pilot programs
- modernizing key and certificate management.
Medium-term goals include:
- full cryptographic agility across critical systems
- complete PQC migration for high-value assets
- fully operationalized crypto-agility governance
- a quantum-ready vendor ecosystem
“Quantum disruption is unfolding—not all at once, but steadily—and preparation must start immediately,” the report reads.
In March, the National Institute of Standards and Technology (NIST) picked its fifth algorithm for post-quantum encryption, which it expects will be widely available for use in 2027. NIST released three quantum-resistant algorithm standards last year and expects to release a fourth one in 2026.
Other resources for planning organizations’ migration to quantum-resistant cryptography include NIST’s draft white paper “Considerations for Achieving Crypto Agility,” the U.K. National Cyber Security Centre’s “Timelines for migration to post-quantum (PQC) cryptography” and the Post Quantum Cryptography Coalition’s “Post-Quantum Cryptography (PQC) Migration Roadmap.”
For more information about the quantum computing cyber threat:
5 – NCSC: Password managers and passkeys are good for you
Individuals, businesses and government agencies should all embrace password managers and passkeys as a way of simplifying and enhancing the management of their digital identities.
The U.K. National Cyber Security Centre (NCSC) made the recommendation this week in the blog post “Trusting the tech: using password managers and passkeys to help you stay secure online.”
These tools “simplify your digital life, and reduce login stress and password fatigue” as long as users understand their pros and cons, the NCSC said.

In the case of password managers, not only do they store passwords but also help you generate strong ones. When choosing and configuring one, the NCSC recommends:
- Pick a reputable vendor with a strong security track record.
- Protect your password-manager account with multi-factor authentication, and with a strong password you haven’t used elsewhere.
- Recognize that browser-based password managers can be more convenient to use, but usually lack advanced security features found in standalone ones.
Regarding passkeys, the NCSC encourages users to take advantage of this emerging alternative to passwords based on public-key cryptography.
“Passkeys are rolling out fast. Websites like Google, eBay, and PayPal already support them. They’re easy to use, hard to compromise, and eliminate password fatigue,” the blog reads.
For more information about passkeys:
[ad_2]
Source link



