[ad_1]
DragonForce, a ransomware group first identified in fall 2023, has claimed over 120 victims in the past year, marking its rapid ascent as a formidable player in the ransomware ecosystem.
Initially operating under a Ransomware-as-a-Service (RaaS) model, DragonForce has since pivoted to a ransomware cartel structure, as announced in March 2025 on its data leak site.
This strategic shift, coupled with its expanding affiliate network and tactical partnerships, positions DragonForce as a critical threat to monitor in 2025.
.png)
A Rising Threat in the Ransomware Ecosystem
The group has targeted organizations across diverse industries, including manufacturing, construction, technology, healthcare, and retail, in countries such as the United States, Italy, and Australia.
Their encryptors target Windows, Linux, and ESXi environments, demonstrating a versatile and sophisticated attack arsenal.
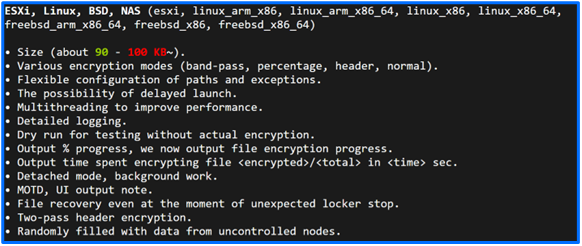
DragonForce’s operational tactics reveal a calculated approach to maximize impact and influence.
The group has shown adaptability by evolving its ransomware variants, initially mirroring traits of LockBit 3.0 in late 2023 and adopting a Conti variant by mid-2024 under its RaaS model.
Their attack methodology includes exploiting vulnerabilities such as CVE-2024-21412, CVE-2024-21887, and CVE-2024-21893 for initial access, alongside phishing and credential stuffing.
Operational Tactics
Post-access, DragonForce employs techniques like Living Off the Land (LotL) using legitimate tools such as Schtasks.exe and Taskkill.exe for persistence, while leveraging Remote Monitoring and Management (RMM) tools like SimpleHelp for lateral movement within networks.
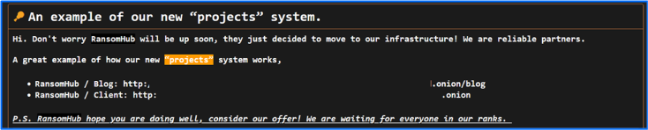
Their ransomware appends the “.dragonforce_encrypted” extension to compromised files and issues detailed ransom notes demanding payments ranging from hundreds of thousands to millions of dollars, tailored through meticulous research of victims’ revenue.
A notable instance involved a $7 million ransom demand in 2024, underscoring their financial motivations over geopolitical agendas, distinguishing them from hacktivist groups despite historical associations with a Malaysian entity of the same name.
Further amplifying their threat profile, DragonForce maintains a data leak site featuring the DragonNews blog, where stolen data details and publication deadlines are posted to pressure victims.
According to Bitdefender Report, their strategic collaborations or coerced partnerships include interactions with groups like RansomHub and Scattered Spider, often using social engineering for initial access.
Intriguingly, DragonForce has been linked to the takedown of competitors like RansomHub and LockBit, with actions such as defacing rival data leak sites and mocking messages left on compromised infrastructure, hinting at a broader goal of dominance within the ransomware sphere.
By offering affiliates 80% of profits and comprehensive infrastructure support including automation, petabyte-scale storage, and advanced encryption for multiple platforms DragonForce not only attracts partners but also exerts control, potentially terminating services to non-aligned actors.
This blend of technical prowess and strategic aggression suggests a nuanced agenda of power consolidation over mere financial gain, especially amidst speculations of Russian-aligned interests and infrastructure ties.
As DragonForce continues to refine its encryption methods, drawing from public decryptor insights like Akira’s GPU cluster techniques, the cybersecurity community braces for escalated challenges in mitigating this evolving threat.
Indicators of Compromise (IOCs)
| SHA256 Hash |
|---|
| e1b147aa2efa6849743f570a3aca8390faf4b90aed490a5682816dd9ef10e473 |
| 7126b9932dc0cdfe751340edfa7c4a14b69262eb1afd0530e6d1fdb2e25986dd |
| ba1be94550898eedb10eb73cb5383a2d1050e96ec4df8e0bf680d3e76a9e2429 |
| 88169b1d4778ed6c5fda97375efb5b9171ea52649c8715bb449801c39bce4ad4 |
| 5c54bd1aa2abf024f53490b7d93101496b5842a5a81a51955fe7f1d5e4281409 |
| 01f1e82d4c2b04a4652348fb18bb480396db2229c4fd22d2be1ea58e6bf4a570 |
| 312ca1a8e35dcf5b80b1526948bd1081fed2293b31d061635e9f048f3fe5eb83 |
| d4de7d7990114c51056afeedb827d880549d5761aac6bdef0f14cb17c25103b3 |
To Upgrade Your Cybersecurity Skills, Take Diamond Membership With 150+ Practical Cybersecurity Courses Online – Enroll Here
[ad_2]

