[ad_1]
New data from Dragos reveals that ransomware groups and their affiliates intensified operations in the first quarter of 2025, combining emerging and long-standing tactics, techniques, and procedures. Established operators such as Cl0p, Akira, and RansomHub maintained high levels of activity, while emerging threats, including FunkSec, Sarcoma, and Lynx, introduced advanced techniques like AI-driven malware and sophisticated EDR (endpoint detection and response) evasion strategies.
These adversaries primarily focused on exploiting vulnerabilities in IT systems, specifically Cleo Managed File Transfer (MFT) platforms, remote access tools, and unpatched software, which led to notable operational disruptions across various industries.
“Industrial sectors, particularly manufacturing, transportation, and ICS equipment and engineering, remained primary targets,” Abdulrahman H. Alamri wrote in a Wednesday Dragos blog post. “Attackers exploited gaps in remote access security, credential management practices, and supply chain vulnerabilities, intensifying operational impacts and complicating incident responses.”
During the quarter, Dragos identified 708 ransomware incidents impacting industrial entities worldwide, representing an increase from approximately 600 incidents documented in the fourth quarter of last year. Q4 2024. This rise underscores the escalating frequency and complexity of ransomware operations affecting sectors such as manufacturing, transportation, ICS equipment, and engineering.
North America reported 413 incidents in the first quarter of the year, up from 360 in the previous quarter. Europe also experienced a rise, with incidents increasing from 102 to 135.
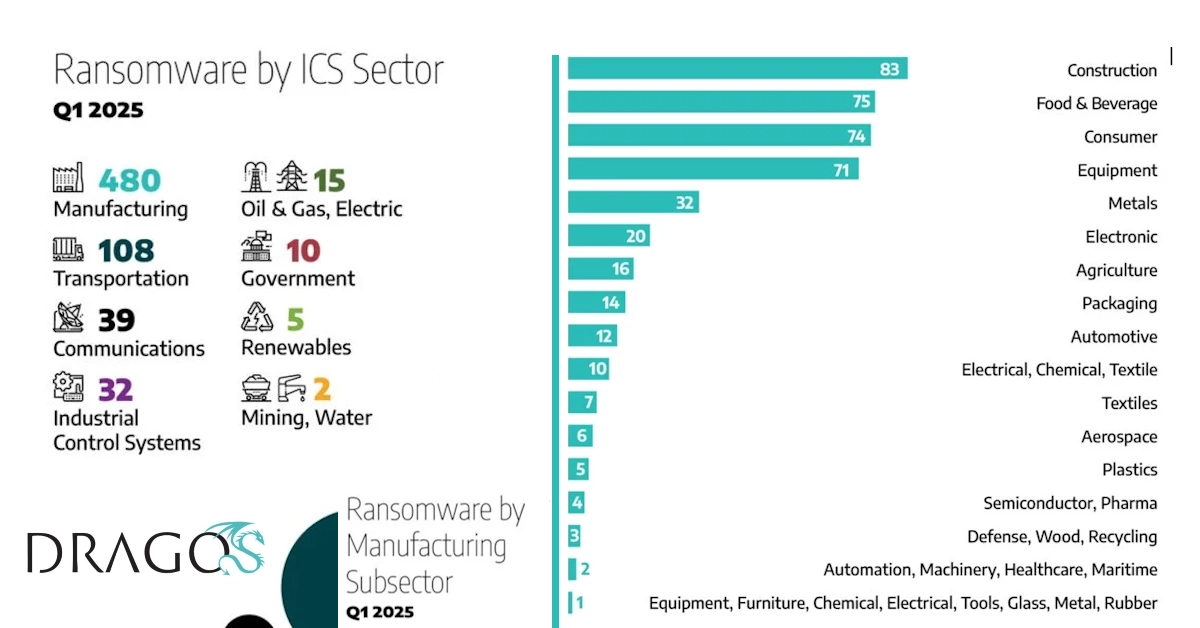
Manufacturing continued to be the most impacted sector, accounting for 68 percent (480 incidents) in the first quarter compared to 70 percent (424 incidents) in the fourth quarter of last year. While Dragos did not detect any new ransomware variants specifically engineered to target ICS environments this quarter, high-impact incidents such as the South African Weather Service (SAWS) outage, which severely disrupted aviation and agricultural forecasting, and the attack on Unimicron, a leading printed circuit board manufacturer, highlight the substantial operational and supply chain disruptions ransomware can inflict on industrial organizations.
During this quarter, ransomware groups and affiliates leveraged a combination of emerging and persistent tactics, techniques, and procedures (TTPs). Notable emerging TTPs included AI-driven malware employed by FunkSec, encryption-less extortion methods, nation-state convergence as exemplified by Moonstone Sleet’s use of Qilin ransomware, and advanced EDR evasion tools like RansomHub’s EDRKillshifter.
Persistent TTPs observed were the continued exploitation of zero-day vulnerabilities such as the Windows Common Log File System (CLFS), sophisticated AI-enhanced phishing campaigns, abuse of remote access tools, targeted ESXi ransomware attacks with SSH tunneling, credential theft, and brute-force attacks.
Cl0p ransomware activity saw a dramatic surge, rising from just two incidents in the fourth quarter of 2024 to 154 in the first quarter of 2025. This spike was largely driven by the exploitation of vulnerabilities in Cleo’s MFT software.
Between December 2024 and the end of the first quarter of this year, Cl0p published multiple victim lists linked to this campaign. Some lists featured redacted or partial company names intended to pressure victims into paying, while others included full names along with scheduled dates for public release of stolen data on Cl0p’s data leak site. The group claimed responsibility for more than 300 victims overall, including 154 in industrial sectors such as manufacturing, food and beverage, and transportation.
Alamri highlighted that the intensifying convergence of IT and OT further amplified operational impacts, causing IT disruptions to cascade into operational environments, as evidenced by the manufacturing delays experienced by National Presto Industries. Further complicating defense strategies, he added that ransomware groups like Babuk Locker increasingly employ deceptive extortion tactics. These adversaries made numerous unsubstantiated breach claims, leveraging psychological pressure by recycling outdated or falsified data leaks. Such misleading claims complicated incident response and verification processes, burdening affected organizations.
During the quarter, Dragos identified several new ransomware groups that emerged, escalating threats to industrial and enterprise organizations through highly targeted and sophisticated cyber operations. These groups employed advanced and continually evolving tactics, techniques, and procedures, posing new and complex challenges for defenders across critical sectors.
Among the newly identified ransomware groups impacting industrial environments were FunkSec, NightSpire, Kairos, Weyhro, Apos, Morpheus, CiphBit, Skira, CrazyHunter, Hellcat, Van Helsing, and Ralord. Each group contributed to the expanding threat landscape, with distinct methods and targeting strategies that reflect a shift toward more adaptive and specialized cybercriminal activity.
Alamri mentioned that ransomware groups are increasingly using advanced AI tools to enhance phishing campaigns, making them more precise, personalized, and difficult to detect. By leveraging generative language models, attackers craft emails tailored to specific roles, interests, and communication styles, increasing the credibility of their lures and reducing the chances of being flagged by traditional security systems.
Groups like Black Basta have adopted AI-assisted social engineering tactics, including realistic impersonations of internal IT staff via platforms like Microsoft Teams. These tactics convincingly mimic legitimate communication, tricking employees into granting remote access and significantly boosting the success rate of attacks.
Also, during this quarter, Dragos identified that ransomware groups increasingly shifted to encryption-less extortion, focusing on data theft and the threat of public exposure rather than file encryption. This approach streamlined operations and allowed attackers to apply immediate pressure on victims.
Cl0p, for example, exploited Cleo MFT vulnerabilities to steal data and demand ransoms without encrypting systems. Hunters International also formally moved to a data-only extortion model, mirroring earlier behavior seen in groups like BianLian. This trend highlights a strategic pivot toward psychological pressure, posing new challenges for industrial organizations where data leaks can disrupt operations, violate regulations, and damage reputations.
Alamri noted that credential theft, brute-force attacks, and exploitation of remote access tools continued to dominate ransomware groups’ initial access strategies during this quarter. Groups such as Black Basta, RansomHub, and DragonForce increasingly relied on compromised or weakly secured credentials as primary intrusion vectors, utilizing automated brute-forcing frameworks and credential-stuffing techniques to systematically target network perimeter devices, including VPNs, firewalls, and remote desktop services.
Notably, Black Basta’s leaked chat logs revealed extensive use of an automated brute-force framework, referred to as BRUTED, to target widely used enterprise edge devices such as Palo Alto Networks GlobalProtect, Cisco AnyConnect, and Fortinet SSL VPN.
He added that once inside, adversaries commonly leveraged legitimate remote administration tools like AnyDesk or QuickAssist to blend malicious activity with normal administrative operations, thereby maintaining persistence and evading detection. Credential-based intrusions further enabled lateral movement, privilege escalation, and deployment of secondary payloads such as ransomware, significantly complicating incident response and recovery efforts.
Dragos reported that Ransomware incidents during the first quarter of 2025 continued to heavily target industrial organizations, with manufacturing remaining the most affected sector. The data highlights a persistent focus on critical infrastructure, including transportation, logistics, and industrial control systems, while underreporting remained a concern in the utilities sector.
The manufacturing sector experienced 480 reported ransomware incidents, up from 424 in the fourth quarter of 2024, accounting for 68 percent of all activity. Transportation and logistics followed with 108 incidents, an increase from 69 in the previous quarter, making up 15 percent of total cases. The industrial control systems equipment and engineering sector reported 32 incidents, a decline from 58, representing 4.5 percent of the total.
The electric sector recorded 15 incidents, rising from 5 in the previous quarter and representing 2 percent of all ransomware activity. The oil and natural gas sector also reported 15 incidents, down from 19, and also accounted for 2 percent. Communications saw 39 incidents, representing 5.5 percent of the total.
Government-related incidents doubled to 10 from 5, comprising 1.4 percent. The water and mining sectors each reported 2 incidents, down from 5 and 4, respectively. Renewables saw a slight increase with 5 incidents, up from 3.
Within the manufacturing sector, Dragos tracked ransomware activity across a variety of subsectors. Construction led with 83 incidents, making up 17 percent of all manufacturing-related attacks. The food and beverage sector followed with 75 incidents, or 16 percent, while consumer goods reported 74 incidents, representing 15 percent. Equipment manufacturing accounted for 71 incidents, also 15 percent. Electronics saw 39 incidents, representing 8 percent, and metals reported 28, or 6 percent.
Other subsectors included machinery with 24 incidents (5 percent), automotive with 21 (4 percent), chemicals with 15 (3 percent), pharmaceuticals with 12 (3 percent), agriculture with 11 (2 percent), and textiles with 8 (2 percent). The remaining incidents were spread across smaller numbers in sectors such as aerospace, electrical, automation, packaging, paper, plastics, defense, printing, recycling, rubber, semiconductors, healthcare, maritime, and glass.
Organizations must urgently enhance cybersecurity defenses through the implementation of robust multi-factor authentication (MFA), stringent monitoring of critical network points, secure offline backups, and strengthened remote access management protocols.
Comprehensive training programs, regular reviews of network architectures, and adoption of AI-driven detection solutions are essential to counter advanced threats such as AI-crafted phishing, encryption-less extortion, and nation-state ransomware convergence observed with actors like Qilin. Furthermore, organizations must rigorously validate threat intelligence to effectively manage deceptive practices, such as the unverified claims seen from Babuk 2.
“As the ransomware ecosystem continues to fragment and adapt, proactive defense strategies, timely intelligence sharing, and collaborative mitigation efforts will be critical for securing critical infrastructure and industrial operations,” Alamri concluded. “Addressing IT-OT convergence risks, securing vulnerable supply chains, and improving threat reporting practices in critical infrastructure sectors will significantly enhance resilience against the persistent threat posed by ransomware groups.”
[ad_2]
Source link