[ad_1]
Hacker infighting exposes Qilin ransomware affiliate panel
The internal workings of a popular ransomware-as-a-service operator have been exposed by a rival hacking group.
A heated dispute between hackers has seen the operations of the Qilin ransomware group exposed, with cyber security researchers getting a rare glimpse into what makes the ransomware-as-a-service provider tick.
It all began with a Qilin affiliate calling themselves hastalamuerte, who accused Qilin of engaging in an exit scam in a thread on a Russian hacking forum. This hacker claims that Qilin’s operators had defrauded him out of US$48,000 during a ransom negotiation, when the entire chat “mysteriously disappeared” from the Tox messaging platform.
You’re out of free articles for this month
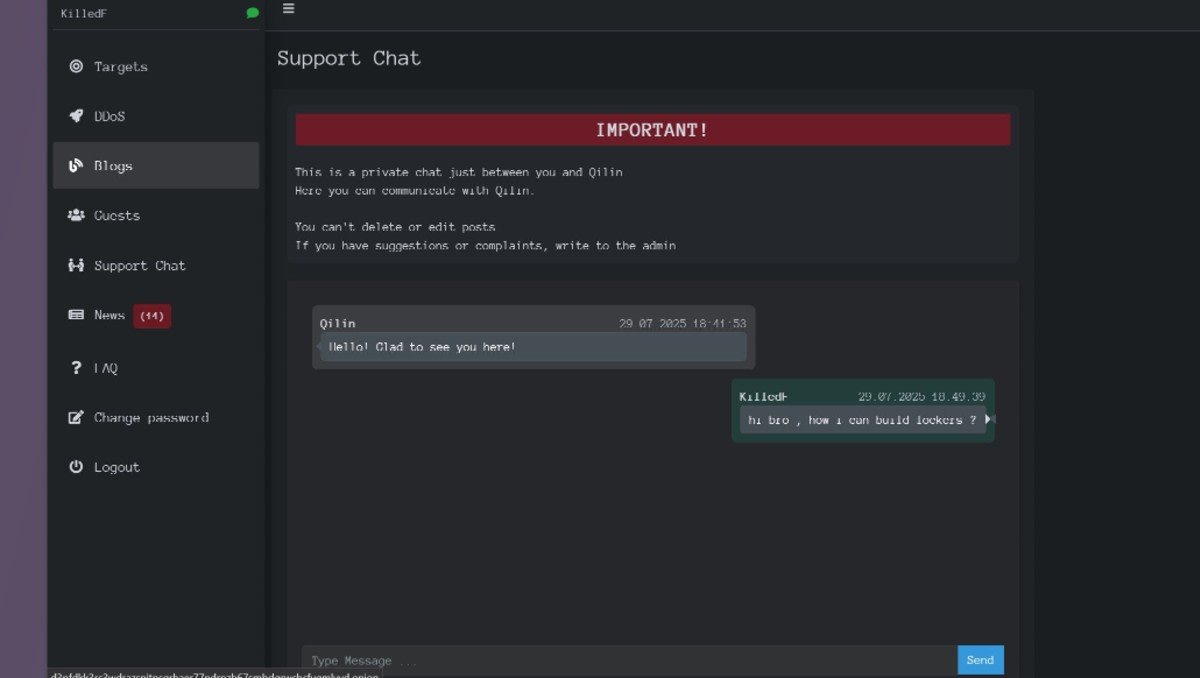
In the same hacking forum chat, another user by the name of Nova shared the login details to Qilin’s affiliate panel, alongside a screenshot of the panel’s chat support function. It’s thought that Nova may be representative of the ransomware actor of the same name.
The possible Nova spokesperson also included a message regarding Qilin’s stability as an ongoing concern.
“Their accounts are full of FBI agents and security researchers, and they use their own wallets, so you should understand that your money will be confiscated if you deposit funds into their accounts, especially if it’s large amounts in the millions of dollars,” Nova said.
“Windows Defender quickly serves all programs at once, as it uses convenient software to build, or at least for mobile devices, at least other combinations. Their security system will be confiscated along with all the money within a few minutes. If law enforcement agencies cooperate, information about the assembly software they use will soon be disclosed by the researchers. Consider them a fraudulent operation of the future, and this is one of the clearest examples.”
It’s likely wise to take those claims with a grain of salt, but it certainly seems like keeping an eye on Qilin’s leak site may be wise.
The look inside Qilin’s affiliate panel is revealing, as it shows a mature malware environment, complete with a support chat, news & blogs, and panels for targeting victims and performing DDoS attacks. We can assume the operators behind Qilin are aware of the leaking of the affiliate panel credentials, as they are no longer valid.
Security researcher Rakesh Krishnan went a step further and was able to find hastalamuerte’s GitHub repository. Krishnan was able to compile a list of the software used by the hacker, both legitimate penetration testing tools and malware. Among the more than 40 tools projects in the repository are Chinese AI chatbot DeepSeek, web testing suite OpenBullet, TamperDev to intercept and edit HTTP requests, and Venom, a C2 shellcode generator/compiler/handler.
Notably, the hacker appears to make use of a version of the popular password stealer MimiKatz made stealthier by the addition of Thermida encryption, and a Russian-language version of the open-source pen-testing tool NetExec.
You can read more about the full list of tools used by the hacker, and potentially other Qilin affiliates, here.
Qilin has amassed an alarming 633 victims since it was first observed in 2022. It’s most recent Australian victim was popular home builder Metricon Homes, which was listed on the gang’s leak site on July 21.

David Hollingworth
David Hollingworth has been writing about technology for over 20 years, and has worked for a range of print and online titles in his career. He is enjoying getting to grips with cyber security, especially when it lets him talk about Lego.
[ad_2]
Source link