[ad_1]
A sophisticated scam operation dubbed “GhostVendors” that exploits over 4,000 fraudulent domains to impersonate dozens of major brands and defraud consumers through fake online marketplaces.
Silent Push Threat Analysts revealed this massive campaign targets social networks, major brands, advertising companies, and consumers worldwide through thousands of fake websites that abuse well-known retailers, including Amazon, Costco, Nordstrom, Rolex, and Brooks Running.
The operation represents a significant escalation in e-commerce fraud, with threat actors systematically targeting brands that purchase large quantities of online advertisements.
Strategic Exploitation of Facebook’s Ad Policies
The GhostVendors campaign demonstrates a sophisticated understanding of Meta’s advertising platform, exploiting a critical policy loophole that allows advertisers to erase evidence of their malicious activities completely.
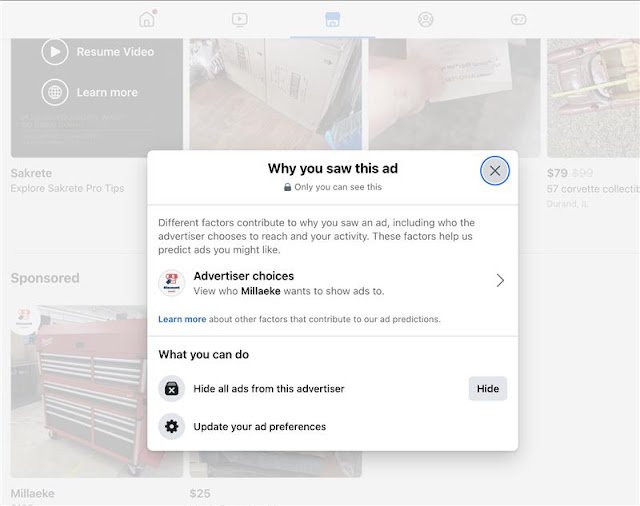
Unlike ads related to social issues, elections, and politics, which Meta retains for seven years, other advertisement types are only saved while campaigns remain active.
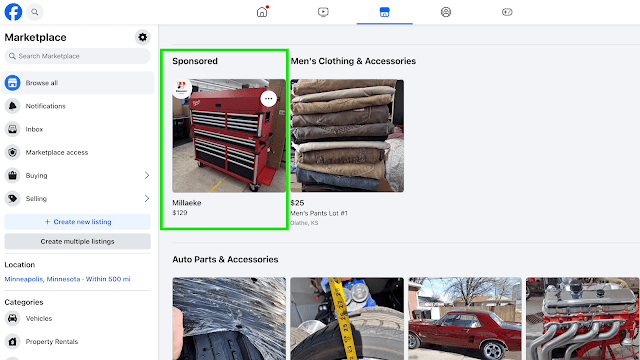
Silent Push documented this exploitation in real-time when they discovered Facebook Marketplace ads impersonating Milwaukee Tools on May 7, 20251.
The malicious advertiser “Millaeke” promoted fake tool products through the domain wuurkf[.]com, but within five days of stopping their campaign, all traces disappeared from Meta’s Ad Library. This systematic removal of evidence makes tracking such threats extremely challenging for cybersecurity professionals.
The fraudulent network targets an extensive range of retailers across multiple sectors. Beyond major retailers like Saks Fifth Avenue, Lowes, and L.L. Bean, the campaign also impersonates specialty brands including Tommy Bahama, Birkenstock, Crocs, Total Wine, and Omaha Steaks.
The operation extends to outdoor gear companies like Mammut and Icebreaker Clothing, gaming companies like Arcade1Up, and even luxury brands such as Goyard and Tom Ford Beauty.
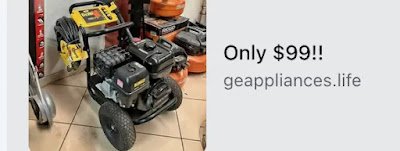
Investigators identified the scam through impossibly low pricing strategies designed to attract victims. For example, fake advertisements promoted Milwaukee tool boxes and heavy-duty rolling tool chests for unrealistic prices ranging from $39 to $128, far below legitimate market values. These advertisements appeared across multiple Facebook pages, including “Rabx-B,” “Tools Clearance,” and “Holiday Celebration Sale”.
The GhostVendors operation employs domain-generated algorithms (DGA) to create vast networks of fraudulent websites, a common tactic for evading takedown efforts.
Silent Push used Google search techniques to identify connected domains, discovering that threat actors clone websites rather than creating unique ones for each domain.
Multiple Facebook advertiser accounts participated in the scheme, including pages that redirected users between different domains to obscure their true destinations. For instance, ads promoting “wrocxop[.]com” actually redirected users to “wesonhz[.]shop,” demonstrating the sophisticated infrastructure behind the operation.
The campaign’s primary objectives appear to involve financial fraud through either failing to deliver promised products or stealing victims’ payment information during fake purchase processes.
While researchers have not tested the actual purchase mechanisms, the scale and sophistication of the operation suggest significant potential for consumer harm across the targeted markets.
Looking for AI-Powered Nex-Gen malware protection? – Download Malware Protection Plus for Free
[ad_2]



.png.png)