[ad_1]
Authorities in the United States have charged a British national, Kai Logan West, widely known online as “IntelBroker“, with a series of high-profile data breaches that collectively caused at least $25 million in damages to companies worldwide. The 23-year-old was arrested in France in February 2025 and now faces extradition to the United States to stand trial in the Southern District of New York.
As reported by Hackread.com, IntelBroker’s arrest was followed by several others, including four individuals linked to the ShinyHunters hacker group. Both IntelBroker and members of ShinyHunters were involved in administering and moderating the cybercrime and data breach forum BreachForums.
The unsealed complaint (PDF), dated February 2025, lays bare the FBI’s two-year investigation into West’s cybercrime operations, connecting him to dozens of data breaches, sales of stolen data, and the leadership of a hacking collective operating on clear and dark web forums.
Who Is IntelBroker?
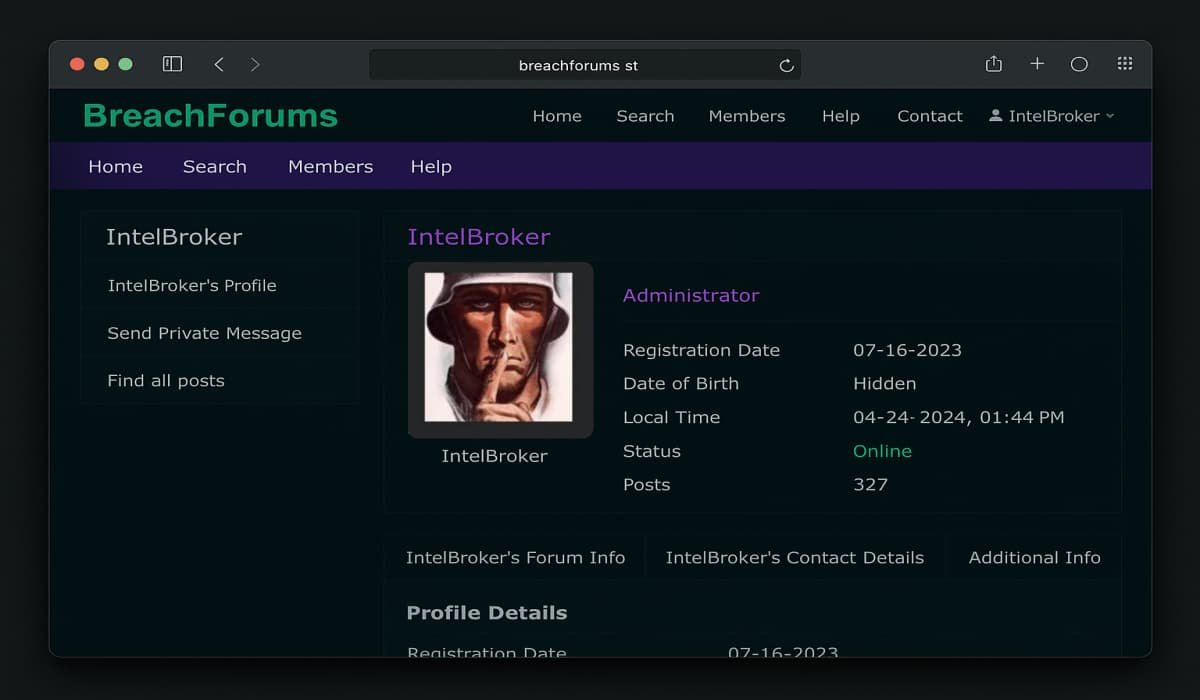
Using aliases like “IntelBroker” and “Kyle Northern”, West built a reputation on a clear and dark web forum known in the indictment as “Forum‑1” ( BreachForums). Operating under the banner of a hacking crew called CyberN (formerly “The Boys”), IntelBroker offered hacked databases from government agencies, healthcare providers, telecommunications firms, and internet service providers.
Between 2023 and early 2025, West authored at least 158 threads offering stolen data on Forum‑1, with 41 of them involving US companies. The FBI notes that at least $2 million worth of Monero cryptocurrency was solicited for the stolen information.
In 2024, IntelBroker was listed as the “owner” of Forum‑1, and his fame skyrocketed as he gave away some data leaks for free to boost credibility, gather a following, and attract buyers.
How the FBI Tracked Down IntelBroker
What West didn’t know was that FBI agents were watching closely. The bureau deployed undercover officers posing as buyers on Forum‑1. On at least two occasions, agents purchased stolen data directly from IntelBroker.
In January 2023, one agent bought an API key and login credentials for a company dubbed “Victim‑7.” Although the credentials were limited in value, the transaction became a key element in tracking his identity when IntelBroker asked for payment in Bitcoin (instead of Monero) and provided a wallet address that could be traced on the blockchain.
FBI blockchain analysts followed the money and found that:
- The Bitcoin wallet used for the transaction had been seeded from another wallet linked to an account on a financial platform called Ramp.
- That Ramp account was registered using a UK provisional driving license issued to Kai Logan West.
- The same identity, Kai West, also owned a Coinbase account under the alias Kyle Northern, but with KYC verification; confirming it was the same individual.
Further connecting the dots, both accounts were linked to a Gmail address used by West for personal matters, including:
- Cloud-stored selfies
- Receipts and ID documents
- UK University Housing and Tuition communications
- Videos showcasing networking tools like “GPRS Smash”
The email also included a student certificate showing West was enrolled in a Cyber Security program.
Online Footprints and Forum Activity
West didn’t just transact carelessly, he also exposed himself by linking his online activity to personal behaviour. His IntelBroker posts on Forum‑1 often referenced YouTube videos that he had just viewed from his personal email account, and he regularly updated his signature block to list members of his hacking group, which made it easier to trace his involvement across multiple threads.
When Forum‑1 was seized and shut down in 2024 and relaunched, all old posts inherited the updated signature, creating a consistent trail of West’s activity and affiliations dating back to early 2023.
The Victim List: Telecoms, Healthcare, ISPs
The indictment outlines at least six victims, referred to only as Victim‑1 through Victim‑6. Victim‑1, a telecom provider, had data exfiltrated and deleted from a hosting server in Manhattan, resulting in damage estimated in the hundreds of thousands.
Victim‑3, a municipal healthcare provider, had the personal and health data of over 56,000 individuals stolen, which West later sold to an undercover FBI agent for $1,000 in Monero. Victim‑6, an internet service provider, was compromised using information from previous leaks to breach an internal server.
In each case, West publicly offered proof samples, negotiated sales via private messages, and accepted only Monero to maintain anonymity, though the paper trail caught up.
However, since Hackread.com exclusively reported on IntelBroker’s data breaches, here is a comprehensive list of data breaches and leaks claimed by the hacker:
Here is the list sorted from shortest to longest by character count:
- AMD
- Apple
- Cisco
- Nokia
- US DoD
- Europol
- T-Mobile
- Robert Half
- Space Eyes
- Home Depot
- Tech in Asia
- General Electric
- LA Intl. Airport
- HSBC & Barclays Bank
- Facebook Marketplace
- Weee! Grocery Service
- UAE’s Lulu Hypermarket
- US Federal Contractor Acuity
- Hewlett Packard Enterprise (HPE)
- MIT Technology Review Magazine
- An unnamed but “Top” Cybersecurity Firm
Criminal Charges
West has been charged with four federal offences:
- Wire fraud
- Conspiracy to commit wire fraud
- Conspiracy to commit computer intrusions
- Accessing a protected computer to defraud and obtain value
Each carries the potential for several years in prison, particularly when involving health data or affecting critical infrastructure.
The FBI’s Special Agent Carson Hughes and US Attorney Jay Clayton emphasized the global reach and danger of IntelBroker’s operations. The FBI called the case “a warning” to cybercriminals who believe online anonymity shields them from consequences.
Did IntelBroker Work for the UK’s National Crime Agency?
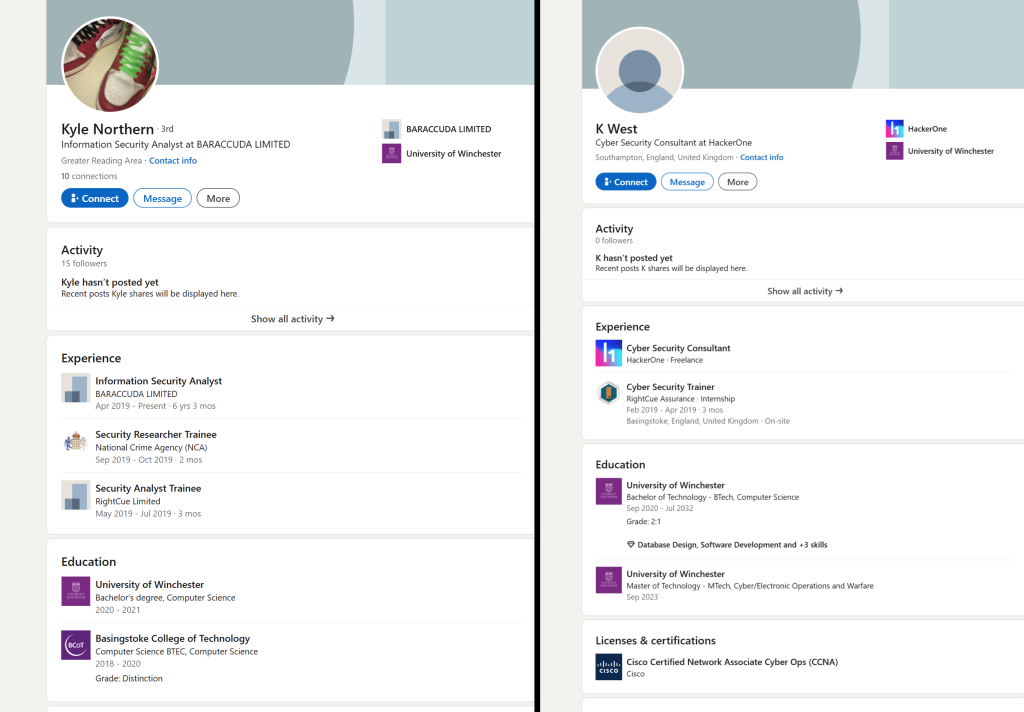
Kai West presented himself professionally as a cybersecurity researcher and operated under two separate identities on LinkedIn, one as Kyle Northern and the other as K West. This was first flagged by Nathaniel Fried, Co-founder and CEO at 0xbowio, who shared details of West’s dual profiles with Hackread.com.
Notably, the Kyle Northern profile claimed he worked as a Security Researcher Trainee at the UK’s National Crime Agency (NCA) from September to October 2019. If accurate, this role could have involved access to classified systems, as the NCA deals with serious organized crime and national security. While the NCA affiliation remains unverified, West’s claimed background in cybersecurity and his academic path suggest the possibility shouldn’t be dismissed outright.
West in France as the US Seeks Extradition
West remains in French custody, and US officials are actively seeking extradition. If convicted, he could face decades behind bars. Meanwhile, Forum‑1 has been offline since April 2025, reportedly due to a MyBB zero-day vulnerability. Many of its members have since migrated to other platforms, including DarkForums and the Russian-language cybercrime forum XSS.
The exposure of IntelBroker stands out as a major cybercrime takedown. What made it possible was a mix of undercover FBI work, cryptocurrency tracking, and even old-school email evidence, all of which helped track one of the most well-known figures on cybercrime forums.
[ad_2]
Source link
Click Here For The Original Source.