[ad_1]
TL;DR:
- In 2023, Caesars Entertainment was hit by a $15 million ransomware attack carried out by the Scattered Spider group.
- Chainalysis tools were instrumental in helping the FBI trace and freeze millions in ransom funds across multiple blockchains and protocols.
- The case illustrates how blockchain’s transparency, paired with the right technology and ecosystem cooperation, can turn ransom payments into recoverable assets — even months after the attack.
The 2023 ransomware attack on Caesars Entertainment made international headlines. Scattered Spider, the ransomware group behind the attack, used sophisticated social engineering tactics to infiltrate Caesars’ systems. After gaining entry on August 18, they exfiltrated sensitive customer data and demanded $30 million in ransom, ultimately accepting $15 million in cryptocurrency.
The hackers likely believed they would be able to use cryptocurrency to shield their windfall from authorities. But crypto’s inherent transparency ultimately worked against them, as blockchain intelligence helped investigators trace the flow of funds.
Newly unsealed court documents reveal how the Federal Bureau of Investigation (FBI) used Chainalysis to track the ransom across multiple blockchains and protocols — freezing millions of dollars worth of cryptocurrency before it could be cashed out.
Inside the social engineering attack
A recently unsealed filing in Nevada District Court reveals that the United States has initiated a civil forfeiture action involving cryptocurrency tied to the proceeds of a ransomware attack. Although the court document does not explicitly name Caesars, referring instead to “Victim A,” the timeline and details leave no room for doubt: a Las Vegas company hacked on August 18, 2023 (the same date Caesars reported its breach) initially faced a $30 million ransom demand that was negotiated down to $15 million.
According to a filing with the Maine attorney general’s office, Scattered Spider targeted an outsourced IT support vendor on August 18, likely using voice-phishing techniques to trick IT support into bypassing multi-factor authentication. By August 23, the attackers had accessed the casino’s customer loyalty database containing Social Security numbers and drivers license information.
Caesars only discovered the intrusion on September 7, giving the threat actors nearly three weeks inside their systems. By September 14, Caesars publicly disclosed the hack in an SEC filing and paid the ransom. MGM Resorts was also hit by the same group, but refused to pay and suffered about $100 million in operational disruptions.
Real-time intervention breaks the flow of illicit proceeds
In January 2024, five months after the initial ransom payment, investigators were alerted to a suspicious movement of about 402 BTC (valued at around $11.8 million at the time) through Avalanche Bridge.
The FBI immediately contacted Ava Labs, which froze 277.56 BTC. Though 125 BTC had already moved through the bridge before authorities could act, this intervention still prevented millions from reaching the criminals’ control.
Soon after, about $690,000 in cryptocurrency was transferred to another wallet hosted by Gate.io. The assets included around $519,845 in stablecoins and roughly 1,135 Monero (XMR). The following day, the FBI contacted Gate.io with a request to freeze the funds. According to the document, Gate.io confirmed it had complied on February 4.
This real-time intelligence and intervention capability is a critical advantage in cryptocurrency investigations. While ransomware groups like Scattered Spider are known for their speed during the initial stages of an attack, blockchain analysis allowed investigators to move with equal agility in tracking the proceeds — turning what criminals viewed as an operational advantage into a liability.
The pattern observed in the Caesars case mirrors what we’re seeing across the ransomware ecosystem, where threat actors are shifting away from formerly popular money laundering methods like mixers (which declined significantly in 2024) toward cross-chain bridges in an attempt to obfuscate the source of funds.
Blockchain analytics turns transparency into leverage
Although attackers attempt to exploit the pseudonymity and accessibility of cryptocurrency, its inherent transparency and immutability provided an investigative edge. Using Chainalysis tools, the FBI successfully traced the ransom through a web of wallets and blockchains.
Case documentation included Chainalysis Reactor graphs that visualized the flow of funds:
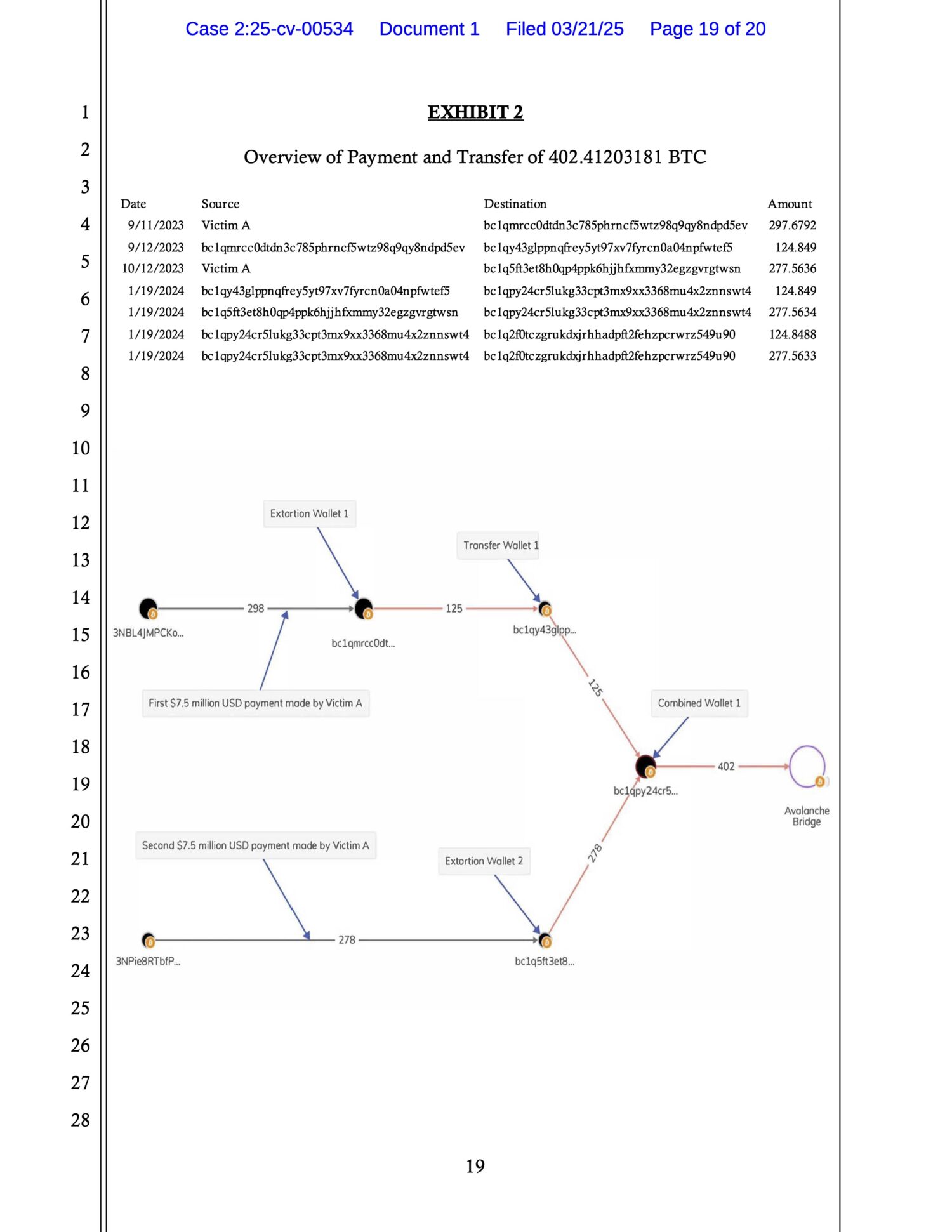
We can see that the BTC ransom was initially sent to two unique wallets (Extortion Wallet 1 and 2). Funds were then transferred through a series of wallets, described in the document as having no prior transaction history — evidence they were created solely for laundering.
The BTC was combined into a single wallet and moved to Avalanche Bridge, converting BTC into wrapped tokens on the Avalanche blockchain.
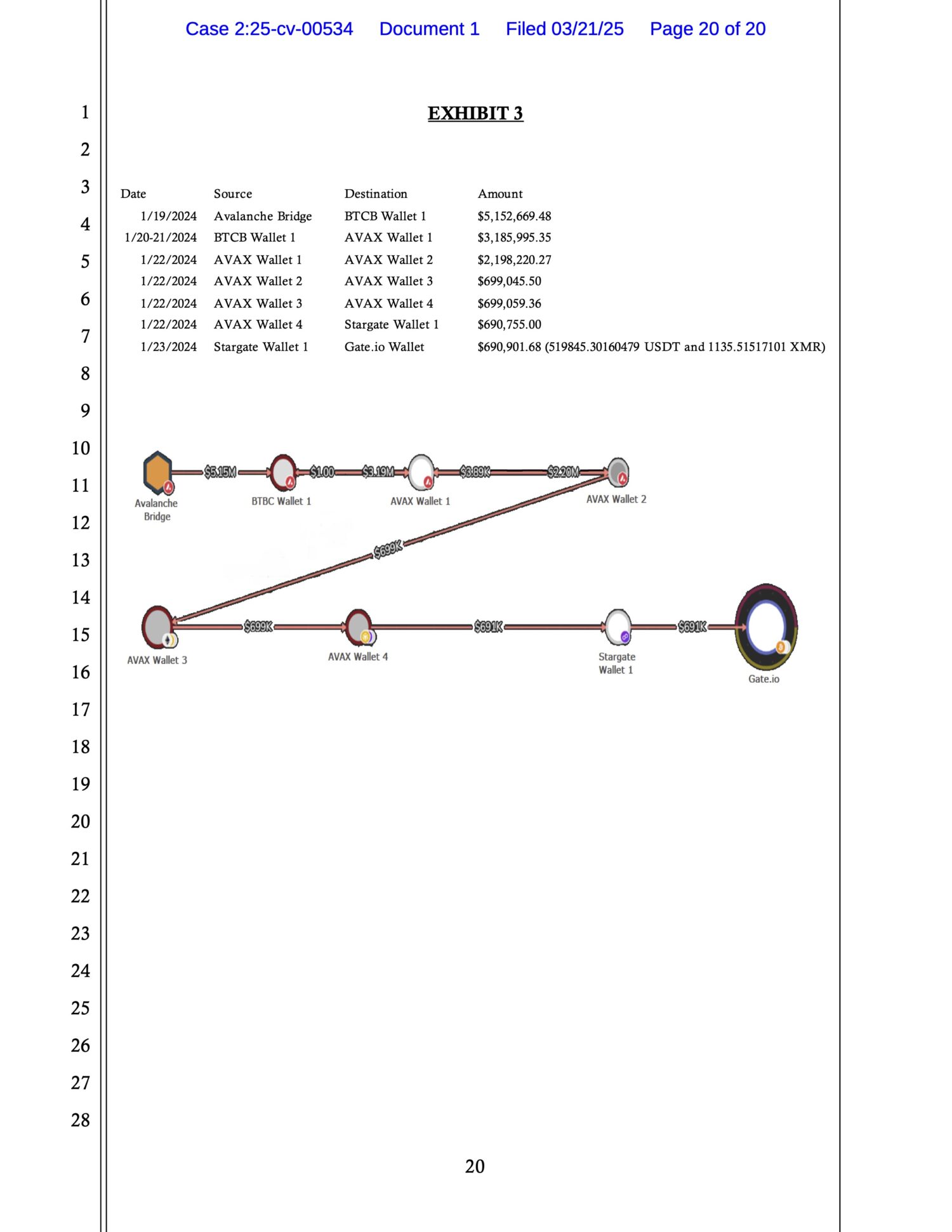
These tokens were laundered through multiple wallet hops using the Avalanche and Stargate protocols, further obscuring their origin. The funds eventually landed in a Gate.io wallet, where the FBI intervened.
Reactor helped investigators uncover money laundering patterns, connect crypto addresses to real-world entities, and build the evidence needed for asset forfeiture.
The broader context: A changing ransomware landscape
The Caesars attack wasn’t an isolated event. Scattered Spider also targeted MGM Resorts during the same timeframe as part of a coordinated extortion campaign. However, the ransomware landscape has changed dramatically since then.
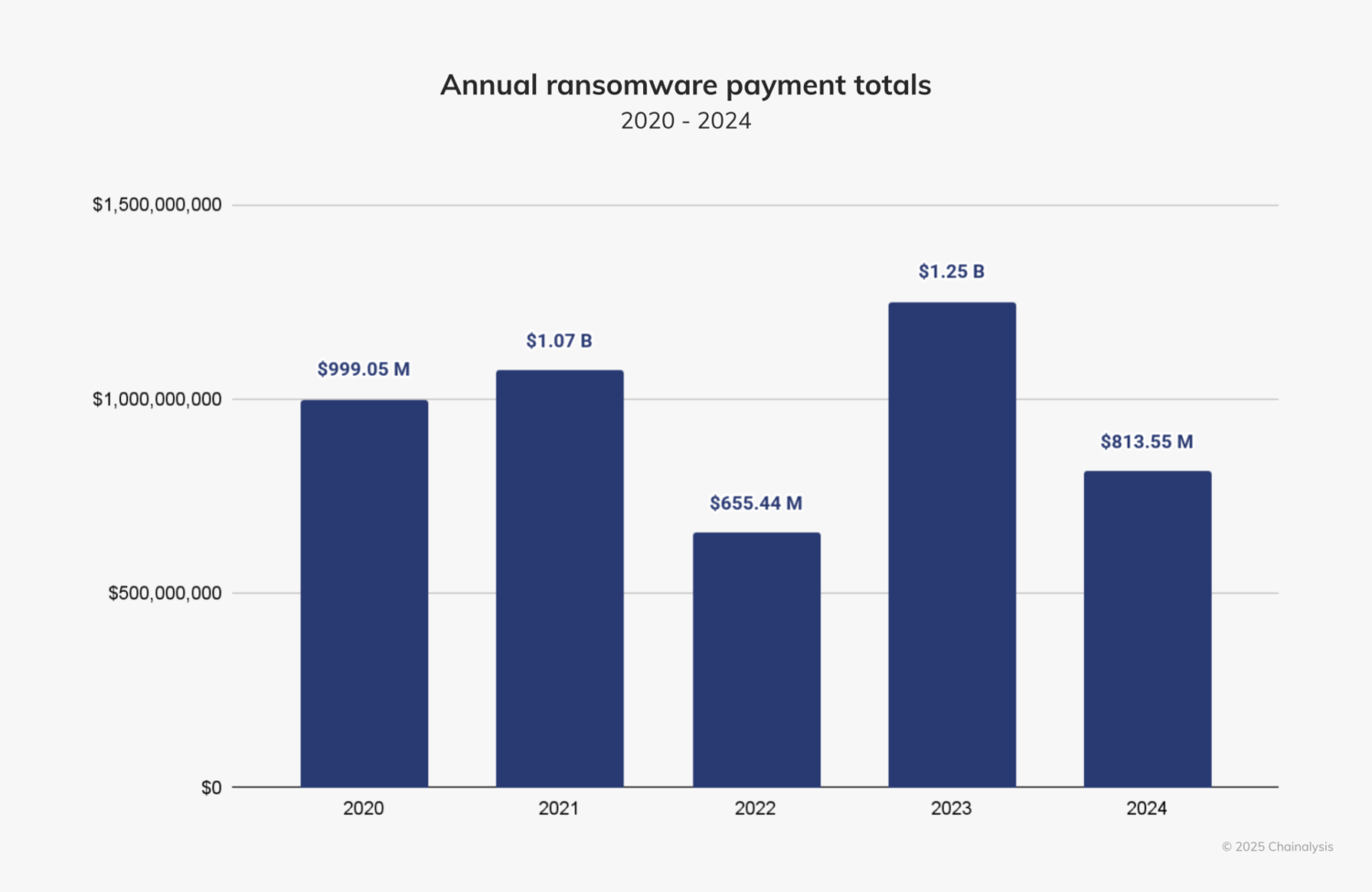
In 2024, global law enforcement action significantly disrupted major ransomware operations. LockBit was dismantled, BlackCat exit scammed, and newer groups scrambled to fill the void. These disruptions contributed to a 35% year-over-year drop in total ransomware payments — down from $1.25 billion in 2023 to approximately $813.6 million in 2024. Notably, fewer than half of ransomware incidents resulted in victim payments, highlighting increased resistance and better victim preparedness.
The Caesars case is more than a singular recovery: it’s a testament to how blockchain intelligence is shaping modern cybercrime enforcement. Each successful trace and seizure helps refine methodologies, build precedent, and affirm that the transparency of blockchain technology works against criminal actors rather than enabling them.
Chainalysis supports our partners in asset recovery
To date, Chainalysis has supported partners around the world in seizing and freezing over $12.6 billion in cryptocurrency. Every recovery builds not just momentum but confidence that in a crypto-activated world, financial crime can be fought and victim funds can be restored.
This case exemplifies how blockchain’s transparency, supported with the right tools and partnerships, can lead to high-value recoveries — even after ransom payments have been made. In many ways, this is a turning point: paying a ransom no longer guarantees impunity for threat actors.
The ability to intervene after payment and recover funds before they’re cashed out is what makes blockchain intelligence a powerful game-changer for ransomware response.
This website contains links to third-party sites that are not under the control of Chainalysis, Inc. or its affiliates (collectively “Chainalysis”). Access to such information does not imply association with, endorsement of, approval of, or recommendation by Chainalysis of the site or its operators, and Chainalysis is not responsible for the products, services, or other content hosted therein.
This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with Recipient’s use of this material.
Chainalysis does not guarantee or warrant the accuracy, completeness, timeliness, suitability or validity of the information in this report and will not be responsible for any claim attributable to errors, omissions, or other inaccuracies of any part of such material.
[ad_2]
Source link

