[ad_1]
A sophisticated Chinese state-sponsored cyber threat group, APT41, has been found using an unprecedented method for malware command and control: Google Calendar. This discovery, highlighted in a new report by US-based cybersecurity firm Resecurity, underscores the evolving and often unexpected tactics employed by state-backed actors.
APT41, also known as BARIUM, Wicked Panda, and Brass Typhoon, is notorious for its dual focus on cyber espionage and financially motivated cybercrime. This group has been active since at least 2012, targeting a wide range of global sectors including healthcare, telecom, software, and government entities.
A Hybrid Threat: Espionage Meets Cybercrime
APT41 stands out from other threat groups due to its unique blend of traditional cyber espionage with cybercrime tactics. The group deploys custom malware and ransomware in some of its attacks, showcasing a versatile and dangerous operational model. This hybrid approach allows APT41 to pursue both strategic intelligence gathering and direct financial gain, making it a particularly challenging adversary for cybersecurity defenders.
Taiwan Government Website Targeted
Resecurity’s recent research revealed APT41’s use of Google Calendar in an attack on a government of Taiwan website. This specific campaign involved sophisticated delivery methods and stealthy malware, demonstrating the group’s continued innovation in bypassing security measures. Resecurity has shared detailed technical information and indicators of compromise (IOCs) to help incident responders and cybersecurity professionals combat these threats.
Read Full Report Here: APT 41: Threat Intelligence Report and Malware Analysis
How the Attack Unfolded: A Step-by-Step Breakdown
The initial infection chain for this campaign was cunningly designed to deceive victims:
- Spear-Phishing Initiation: The attack began with spear-phishing emails. These emails directed victims to a ZIP archive.
- Compromised Government Website: The malicious ZIP archive was hosted on a compromised government website, lending an air of legitimacy to the download.
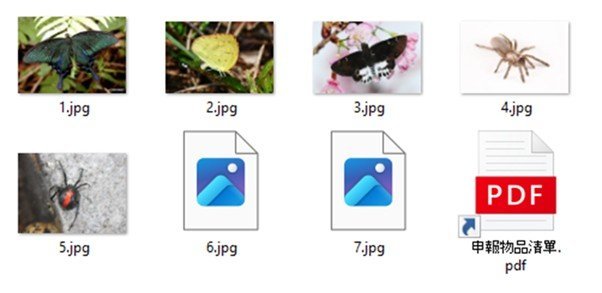
- Disguised Malicious Files: Inside the archive, victims found a Windows shortcut (LNK) file, cleverly disguised as a PDF document. Alongside it were several JPG images.
- Hidden Malicious Payload: Two of these JPG images, specifically “6.jpg” and “7.jpg,” were not genuine images. They were part of the malicious payload.
- Decoy PDF and Silent Launch: When a victim opened the shortcut LNK file, a decoy PDF appeared. This PDF stated that listed species needed to be declared for export. Simultaneously, and silently, a stealthy malware called ToughProgress launched in the background.
ToughProgress: A Multi-Module Stealth Machine
ToughProgress operates through three sequential modules, each designed with advanced stealth and evasion techniques. These techniques include:
- In-memory execution: The malware runs directly in the computer’s memory, making it harder to detect.
- Encryption and compression: Obfuscating its code and data.
- Process hollowing: Injecting itself into legitimate processes to hide.
- Control flow obfuscation: Making its code difficult to analyze.
- Google Calendar C2: A novel method for command-and-control communications.
The Three Malicious Components:
- PLUSDROP: This module decrypts “6.jpg” and executes it using Rundll32.exe, a legitimate Windows utility.
- PLUSINJECT: This component performs process hollowing. It injects the final payload into a legitimate svchost.exe process, a critical Windows service, to evade detection.
- TOUGHPROGRESS: Once installed, ToughProgress begins communicating with attacker-controlled Google Calendar events. This communication acts as a covert command-and-control (C2) channel.
Execution and Payload Deployment: Deeper Dive
Once Rundll32.exe launched, the malware initiated a complex sequence of operations:
- In-Memory Decryption: The malware loaded its path into memory. It then opened “6.jpg” and read its contents into a buffer. An XOR-based decryption routine was applied to the data. This allowed the malware to hide its payload within a seemingly harmless image and execute it directly from memory without writing its decoded form to disk.
- Process Environment Block (PEB) Traversal: The malware then accessed the Process Environment Block (PEB) to walk the list of loaded modules in memory. This technique is commonly used to locate system DLLs without relying on API calls like GetModuleHandle, which security tools might monitor.
- Custom Hashing for Obfuscation: For each module, the malware retrieved its name and applied a custom hash function. This function converted characters to an uppercase-like form, skipped non-printable characters, and applied a rolling hash. The result was then masked to 32 bits.
- Module Matching and Injection: When the hash matched a specific constant (0x1CCA9CE6), the malware saved the module’s base address and injected the decrypted code into svchost.exe.
FCRF x CERT-In Roll Out National Cyber Crisis Management Course to Prepare India’s Digital Defenders
Why Process Hollowing?
Process hollowing is a sophisticated evasion technique used by the malware for several reasons, as detailed by Resecurity:
- Avoids Suspicious Strings: Security tools scanning for keywords like “svchost.exe” or “kernel32.dll” will not flag a hash. This makes it harder for automated defenses to detect the malicious activity.
- Obfuscation: It slows down analysts who must reverse-engineer the hash function and brute-force to discover the original string. This buys the attackers time.
- Function Resolution: It allows the malware to dynamically resolve critical functions like LoadLibrary, VirtualAlloc, or even inject into trusted processes.
Targeting the Heart of Windows
The malware did not stop there. It proceeded to target ntoskrnl.exe, the core of the Windows operating system. This calculated effort aimed to map, analyze, and potentially manipulate critical sections of the system. This behavior, buried within a specific function, initiated a complex sequence of memory operations, a hallmark of advanced low-level persistence mechanisms.
The malware actively located and accessed internal structures in a stealthy, dynamic way. It performed pattern matching in the .text section to find non-exported kernel routines. It also mapped physical memory to bypass standard protections and used driver-like memory handling to avoid detection. These techniques are designed for advanced goals like privilege escalation and anti-forensics, making analysis incredibly difficult for reverse engineers, as noted in Resecurity’s findings.
Google Calendar: The Covert Command Center
What truly distinguishes ToughProgress is its novel use of Google Calendar as a command-and-control (C2) mechanism, a detail highlighted by Resecurity.
- Stealthy Communication: The malware communicates with an attacker-controlled Google Calendar by creating and modifying events to facilitate covert data exchange.
- Encrypted Data in Events: Upon installation, ToughProgress creates a calendar event, typically dated back in 2023, embedding encrypted, exfiltrated data within the event’s description.
- Remote Command Execution: Attackers embed encrypted commands in calendar events. The malware retrieves these events, decrypts the commands, executes them on the infected Windows system, and then uploads the execution results into a new calendar event.
This process enables the threat actors to remotely collect data and issue commands, maintaining a highly stealthy communication channel that is difficult to detect using traditional network monitoring tools.
Defensive Measures and Future Outlook
In response to the TOUGHPROGRESS campaign, Google took swift action. They developed custom detection fingerprints to identify and remove malicious Google Calendar instances. They also disabled attacker-controlled Workspace projects associated with the campaign. Furthermore, harmful domains and files linked to the threat were added to Safe Browse blocklists to enhance user protection.
This incident, brought to light by Resecurity’s comprehensive report, serves as a critical reminder for organizations and individuals. Do you scrutinize every link and attachment, even if it appears to come from a trusted source? How well are your security systems equipped to detect and prevent such sophisticated, multi-layered attacks? As APT41 and similar groups continue to evolve their tactics, the need for robust, adaptive cybersecurity defenses becomes ever more urgent.
[ad_2]
Source link
Click Here For The Original Source.

