[ad_1]
Hyderabad: In the early 2000s, when accessing the internet meant screeching modem sounds or a quick trip to a cyber café, most of the programmes on the computer were meant to run offline. Available to purchase on compact discs (CDs), the software came bundled with a single-user activation key. However, software files on the CD allowed anyone to install the programme.
While some applications allowed limited functionality without activation, others required a valid key from the very start. This led to the widespread use of key generators (keygens), tiny tools that could churn out an infinite number of activation keys that could bypass the ownership check. Cracked software, which involved modifying the original application to bypass licensing restrictions, usually by replacing the main .exe file in the programme folder, was equally common.

Earlier, laptops used to come with CD drives (Getty Images)
Unlike the subscription model for most services today, software purchase used to be a one-time affair. Yet, many people—especially students with limited pocket money or small shops offering printing services—used to head towards piracy to save money on Adobe Photoshop, Adobe Pagemaker, Corel Draw, MS Office, and other popular programmes.
Even the Windows operating system wasn’t immune. In those days, it was common to see a “Windows is not genuine” warning at the bottom-right corner of the desktop, triggered when Microsoft identified the pirated copy during online validation whenever the system was hooked to a dial-up connection.
Software copies require a product key to establish genuine purchase (Windows)
Another common thing to witness in those days was frequent malware infestation in computer systems, brought upon by the installation of cracked versions or illegal keygens. Such piracy tools have always been popular vectors for viruses, which easily deflected rudimentary and resource-hungry antivirus solutions of the time. However, since not everyone could access the internet back then, most people treated viruses as system bugs and would simply format the machine once they started hindering the primary use case or significantly slowing down the PC.
However, today the risk is greater than ever. Not only do computer systems hold our personal identification information, but they also store our personal photos, financial information, passwords, and whatnot. The hunt for cracked software today is like stepping into a minefield or gambling with the possibility that the wooden structure might not be a Trojan Horse.

In Greek mythology, the Trojan Horse was a wooden horse said to have been used by the Greeks during the Trojan War to enter the city of Troy and win the war – A Trojan Horse Virus is a type of malware that downloads onto a computer disguised as a legitimate program. (ETV Bharat)
Cybersecurity firms have repeatedly warned that pirated software often comes bundled with droppers for malware. The recent CloudSEK finding reinforces this concern, as it highlights a Pakistan-based threat network actively utilising the user hunt for cracked software to spread infostealer—malicious software created to breach computer systems and steal sensitive information, such as login details and financial credentials.
Cracked software malware distribution campaign
CloudSEK uncovered an extensive, long-running malware distribution campaign run by a group of threat actors, based primarily in Bahawalpur and Faisalabad, Pakistan. As per the report, a cybercrime operation created thousands of malicious websites to distribute infected software. They employed Search Engine Optimisation (SEO) poisoning to rank highly on Google Search, targeting users looking for cracked versions of popular programs such as Adobe After Effects and Internet Download Manager (IDM). Additionally, they exploited online forums and platforms to expand their reach through social networks, mimicking the growth strategies of direct-sales models.
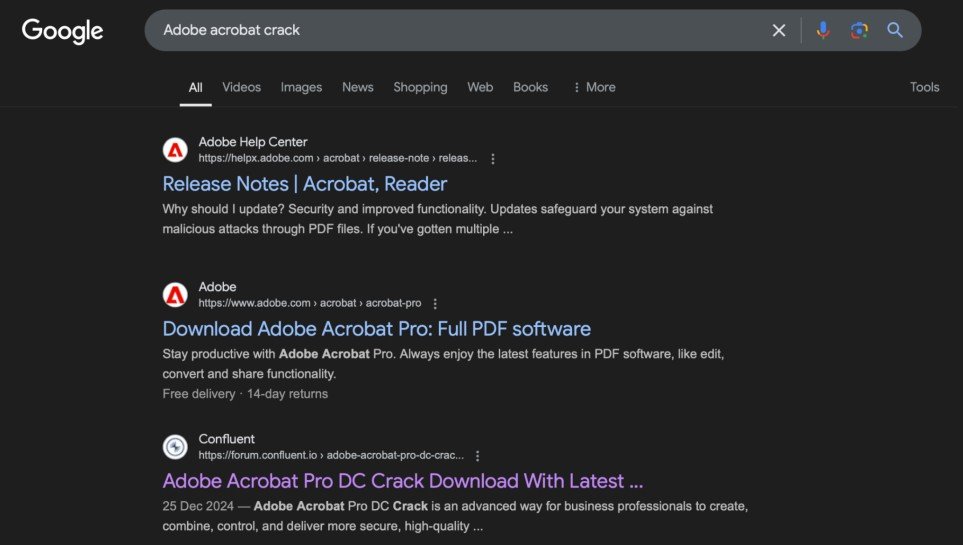
Confluent forum abuse to spread Trojanized Adobe Acrobat Warez (CloudSEK)
Over a period of five years, these sites delivered Lumma Stealer, Meta Stealer, and AMOS within password-protected archives. According to the research, these sites got over 449 million clicks, leading to 1.88 million malware installs. Monetisation remained the core driver of the campaign, achieved through Pay-Per-Install (PPI) networks, run by over 5,000 affiliates, earning at least $4.67 million in lifetime revenue.
One such network, InstallBank, was active from 2018 to 2025, paying out via Payoneer and Bitcoin before going offline. Its successor, SpaxMedia—now rebranded as Installstera—has been active since 2022 and recruits helpers through Facebook ads in Pakistan.
How investigators sniffed the threat campaign
On October 14, 2024, cybersecurity researchers came across a suspicious forum post on Honor’s UK site offering “Adobe After Effects Crack Free Download Full Version 2024”. The post contained an external link, which redirected to a public Google Document. They used tools to trace the document’s metadata to an individual, linking the forum post to a specific threat actor.
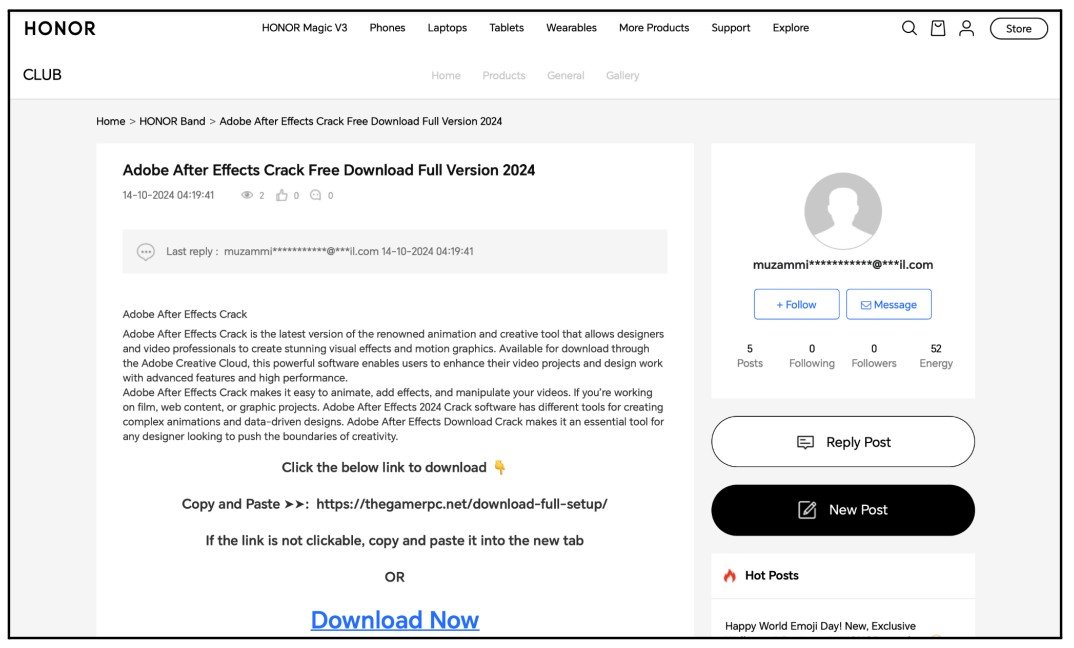
The malware distribution network posted on Honor UK forum to bait piracy enthusiasts (CloudSEK)
“We were already tracking platform abuse as part of routine investigations, especially around warez/SEO results. During one of those hunts, the Honor UK forum unexpectedly showed up on the first page of search results. From there, we used xeuledoc, an OSINT utility that extracts emails from shared documents,” Pavan Karthick M, Threat Intelligence Researcher at CloudSEK, told ETV Bharat.
Further analysis of malware logs uncovered a significant overlap in sites used to distribute malware, with another threat actor linked through shared credentials and infrastructure. It revealed connections between multiple cracked software domains and WordPress sites, with over 2,500 credentials, with numerous mentions of a common surname, hinting towards a potential family-run operation.
“A threat actor’s OPSEC lapse exposed their distribution affiliate email, which we pivoted on. Linking that email with domains being pushed revealed compromised WordPress sites, and further analysis connected those to broader affiliate infrastructure, eventually pointing us to Pay-Per-Install (PPI) networks,” Karthick explained.
Threat actors compromised themselves
Ironically, the breakthrough in the investigation came when threat actors themselves were compromised by infostealer malware. The exfiltrated logs from their own machines provided unprecedented insight into their identities, command structure, infrastructure, communications, and finances, ultimately leading to their unmasking, CloudSEK explained.
“The biggest surprise was how public and careless this network was. Unlike the stereotype of stealthy cybercriminals, their affiliates operated openly, even under their real names in some cases,” Karthick said.
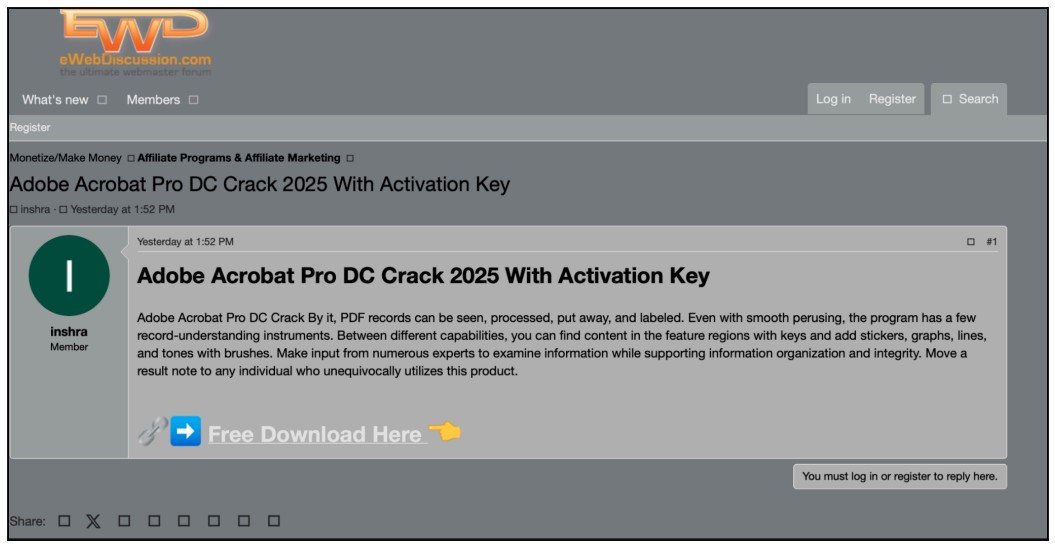
EWD forum abuse to spread Trojanized Adobe Acrobat Warez (CloudSEK)
“While we had access only to a partial ledger (covering cash-outs), we cross-referenced with Crypto wallet activity observed in parallel, revenue columns embedded in the affiliate dashboards, and known affiliate counts,” he said. “This triangulation let us estimate a minimum lifetime earning figure that far exceeded the 2020 dataset alone. The scale and transparency of their affiliate recruitment were shocking for an operation of this size.”
When asked about the ethical considerations of analysing stealer logs, Karthick said, “Our methodology involves monitoring open and closed underground sources that CloudSEK routinely tracks for customer protection. Some of the very actors distributing malware inadvertently leaked or exposed their own stealer logs, which surfaced in these forums and channels.”
“Once accessed, we filtered only for credentials tied to distribution activities, which included WordPress admin panels, hosting accounts, and email logins used for PPI. Importantly, we did not access or misuse victim accounts,” he said. “Credentials were used purely as attributional artefacts to connect infrastructure and affiliates. All sensitive data was handled under TLP:GREEN restrictions with strict internal guidelines.”
A lesson for those hunting for cracked software
The victims of this malware operation are primarily individuals seeking free or cracked software. According to the firm, the consequences are severe as the stolen personal data is sold for as little as $0.47 per victim. The $4.67 million revenue points to massive privacy violations, suggesting that over 10 million people may have been affected.
The firm says that combating this threat requires coordinated action across multiple fronts:
- Users should steer clear of cracked software, rely on official sources, maintain strong passwords, and use reliable antivirus tools.
- Tech companies like Google and forum platforms must proactively block spam links, while domain hosts such as Cloudflare should remove malicious sites.
- Law enforcement agencies, particularly in Pakistan, are urged to freeze Payoneer and Bitcoin accounts linked to the network and leverage leaked data to pursue arrests.
- On the technical side, antivirus programs need updates to detect malware like Lumma stealer, and known malicious domains (listed by CloudSEK) should be blocked.
Highlighting how piracy websites can fuel cybercrime, the cybersecurity firm said that stronger cooperation among law enforcement, financial institutions, and tech companies could reduce such operations by up to 70 per cent in a short time.
[ad_2]
Source link
Click Here For The Original Source.

