[ad_1]
If you’ve been even mildly tuned into tech headlines over the past few years, you’ve probably heard of ransomware.
But what is it, really? How does it sneak into our systems, take over files, and hold them hostage? Let’s lift the veil on ransomware, explore exactly how it works, and why it’s become one of the biggest threats on the web today.
What is Ransomware, Really?
In the simplest terms, ransomware is a type of malicious software — malware — that encrypts your files or even your entire system and demands payment, usually in the form of cryptocurrency, in exchange for granting you access again.
It’s extortion, plain and simple. Once installed on your system, it encrypts your files so that you can’t read or use them. Then a ransom note pops up on your screen, explaining exactly how much you do owe and how to pay.
No pay, no files. Imagine it like a kidnapper grabbing your family photo albums and your business files and placing them in a safe that can be unlocked only by them.
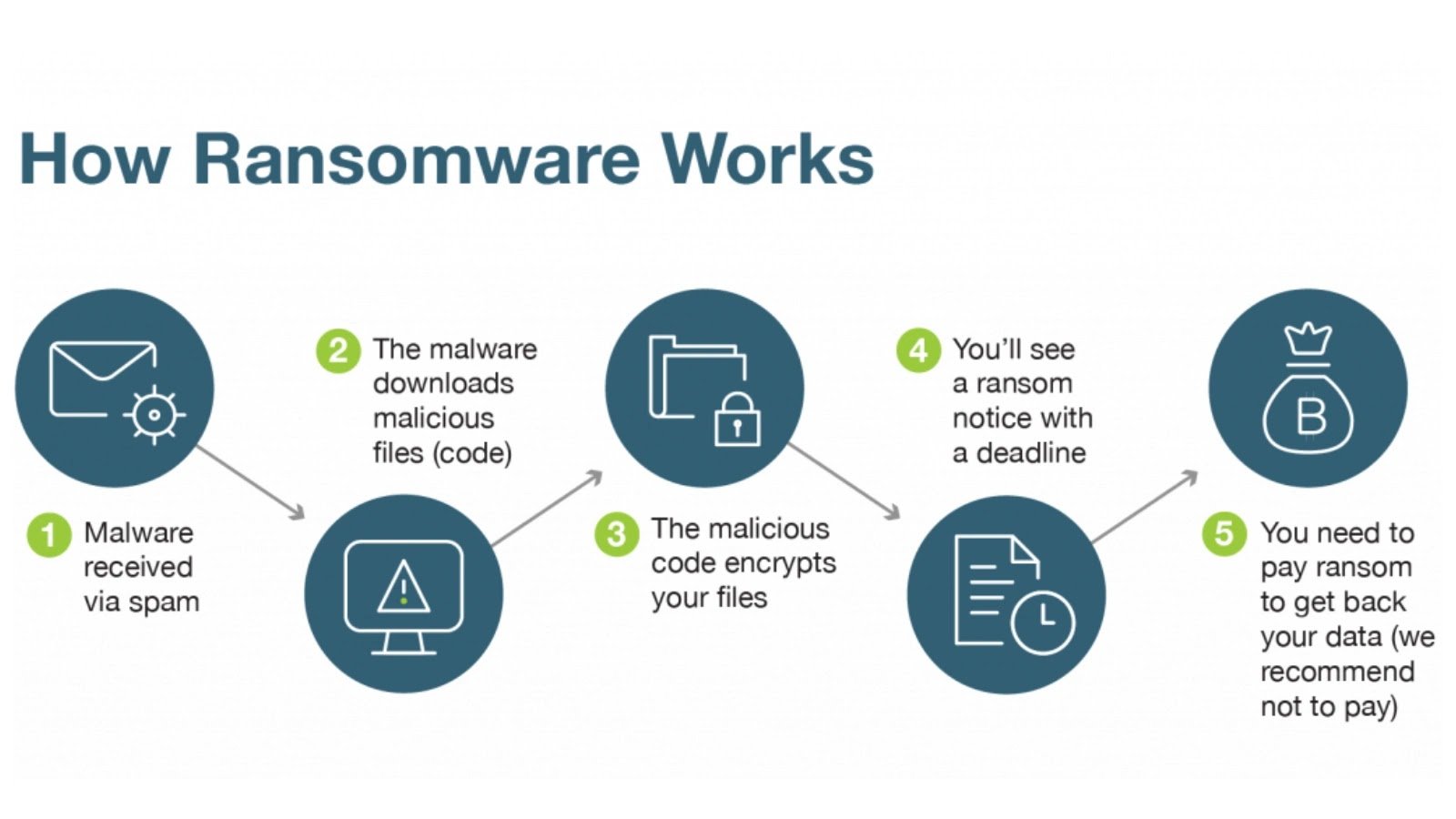
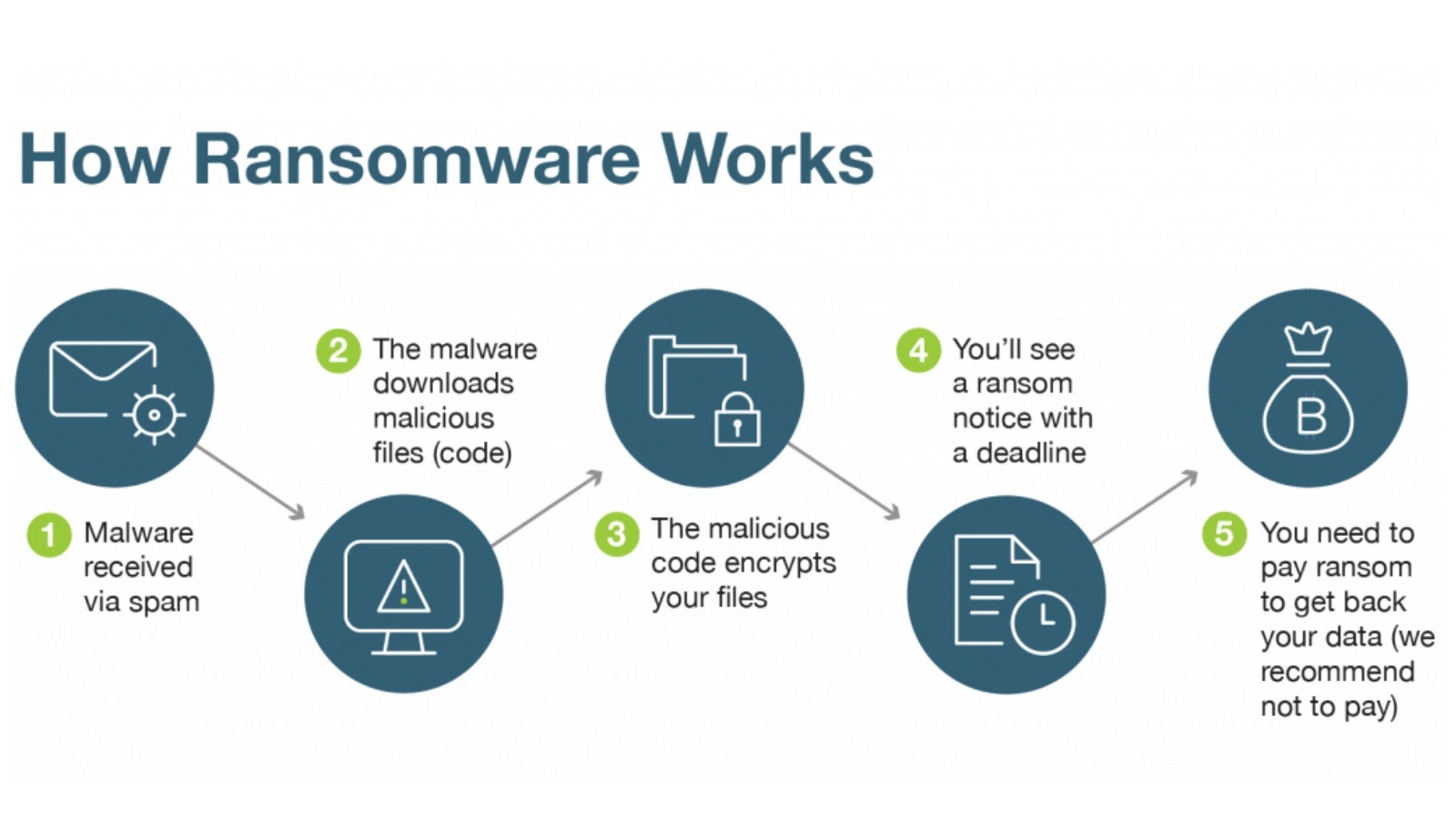
How Does Ransomware Get in?
There are no front-door invasions for ransomware. Instead, it insidiously infiltrates under the pretense of something you do trust — an email attachment, a false software update, or a link that is real but laced with a trap.
Most often, it insidiously infiltrates phishing emails. Click on a link, download an attachment, and wham — the malware sets itself up in the background silently.
Sometimes, it doesn’t attack you right away. It sits, scopes out your system, maps your files, possibly even infects other associated machines, and then strikes.
Another method that’s been on the increase is targeting security holes in outdated software. If your systems are not updated or patched, ransomware can attack known holes without ever having you click on a thing.
That’s why some of the biggest ransomware attacks — like WannaCry and NotPetya — were so successful. They infected every person in their path without anyone having to open so much as a shady file.
The Moment It Hits: What’s Next?
Once ransomware is inside your system and ready to do harm, it starts encrypting files. That is, it locks them with a special key known only to the attacker.
You will observe files change from their usual name to an unreadable name. Then, as the panic is starting, in comes the ransom note.
Usually, it contains instructions, an ultimatum, and a cold threat: pay us, or lose your files forever.
At times, even ransomware threatens to leak your data. The newer double extortion tactic is an additional threat.
Retrieving your files is no longer on the agenda — keeping your info under wraps or from competitors, regulators, or clients is. Hospitals, law firms, banks — businesses that hold private information are especially vulnerable to this tactic.
Why Ransomware is More Menacing Than Whensoever Before
There are a few big reasons ransomware’s become such a feared threat in recent years. The first one is the sophistication of the attackers. We are no longer facing lone-wolf hackers in a cramped, dingy basement.
Ransomware is now a professional operation, sometimes run by criminal syndicates that function like companies — complete with customer service, sales, and shared-profit programs.
There are even some that provide Ransomware-as-a-Service, where a team develops the software and others rent for their own operations.
Second, the payment methods like cryptocurrencies have made payment for attackers in an anonymized way. As such, less risk is incurred for them and the payoff is larger to attack. The money, once sent, is hardly retrievable or traceable.
Last but not least, hybrid work and cloud applications have introduced new attack surfaces. More networks, more devices, and more fragmented security equates to more opportunities for ransomware to breach.
And the more we are all interconnected, the farther the dominoes can topple when just a single piece is taken down.
What Can be Done to be Safe?
The best protection against ransomware is multi-layered security. That is, keeping software up to date, educating employees on recognizing phishing attacks, and backing up files often to an isolated system.
Using endpoint protection, network segmentation, multi-factor authentication — all those words you’ve heard from your IT department? Well, they do help.
And more and more companies are paying for professional network security services in an effort to stay one step ahead of threats.
You need an end-to-end security plan that assumes that the attackers will get in — and is prepared to contain the damage when they do.
One Threat That Won’t Disappear
Ransomware is not leaving anytime soon. If anything, it’s becoming wider, sophisticated, and even more lucrative for cybercriminals. As long as there are people willing to pay and open systems are present, the ransomware market will continue thriving.
The good news is that awareness is increasing. Organizations are no longer thinking about cybersecurity as an afterthought, but as an integral element to conducting business. And through the right mix of planning, technology, and keen thinking, keeping ahead is achievable.
[ad_2]