[ad_1]
Find out how recent changes in cybersecurity compliance rules impact how RIAs handle sensitive investor data
RIAs have become a prime target for cybercriminals due to the sensitivity of data they hold and the value of assets they manage. If successful, a cyberattack often results in devastating losses not just for advisory firms but also for their clients.
To protect investors and maintain market integrity, the SEC has imposed strict cybersecurity compliance rules for financial institutions. Among these is Regulation S-P, which was amended recently.
In this guide, we’ll discuss what these changes mean for your RIA and what you can do to remain compliant. We also talked to an industry expert who shared insights into the most important aspects of SEC’s new regulations.
Regulation S-P is a rule established by the Securities and Exchange Commission (SEC) governing how financial institutions, including RIAs, handle sensitive costumer information. Also called the Privacy of Consumer Financial Information rule, it is designed to protect private client data against unauthorized access, misuse, and theft.
Regulation S-P requires financial institutions to:
For RIAs, protecting sensitive customer information is not just a matter of regulatory compliance; it is also key to building trust and improving reputation. The recent spate of cyberattacks, however, has prompted the SEC to make amendments to the S-P rule.
Get more information about cybersecurity compliance by visiting our Technology News Section. Don’t forget to bookmark this page for easy access to breaking news and the latest industry updates.
In May 2024, the SEC finalized the changes to Regulation S-P, which have major implications on cybersecurity compliance. According to the SEC, these updates are designed to “modernize and enhance the protection of consumer financial information.”
Here are some of the key amendments to the rule and what they mean for RIAs:
Incident response program
RIAs must develop and maintain written policies and procedures for an incident response plan. The program must be “reasonably designed to detect, respond to, and recover from unauthorized access to or use of customer information.”
The program must also have these core elements:
- assessment of incidents involving unauthorized access to client data
- measures to contain the data breach
- steps for notifying clients if their private information is compromised
Breach notification procedures
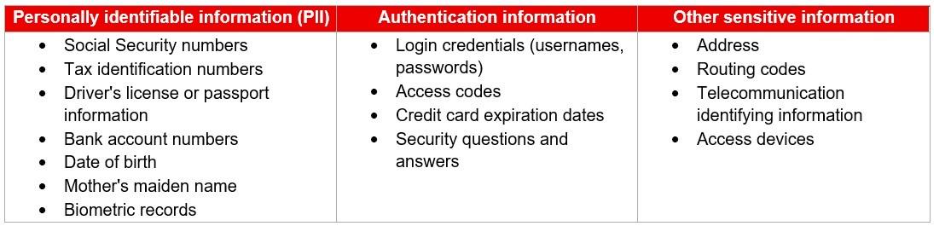
Firms must notify individuals “whose sensitive customer information was, or is reasonably likely to have been, accessed, or used without authorization.” The table details what can be considered sensitive client data under Regulation S-P:
RIAs must also notify affected clients of the data breach within 30 days after it was first detected, unless a waiver applies. The notifications must include:
- the nature and date of the incident
- the type of sensitive customer information breached
- the firm’s contact information
Even a suspected data breach can trigger notification requirements under the new Regulation S-P.
Service provider oversight
As part of their incident response programs, firms must have procedures for managing service providers, including due diligence and monitoring. This is aimed at ensuring providers are managing potential privacy risks effectively.
Expanded scope of safeguards and disposal rules
The 2024 Regulation S-P broadened the definition of “customer information” to include any record containing non-public personal information (NPI) about a client. This is regardless of whether the records are on paper, digital, or other forms.
Firms must also keep written records detailing their compliance with the safeguards and disposal rules. For RIAs, the retention period is five years; certain records must be easily accessible for the first two years.
Compliance dates
The compliance period varies depending on the firm’s size:
|
Size
|
Assets under management
|
Compliance date
|
|---|---|---|
|
Larger RIAs
|
$1.5 billion or more
|
December 2025
|
|
Smaller RIAs
|
Less than $1.5 billion
|
June 2026
|
So, what are the most important aspects of the SEC’s new cybersecurity regulation that RIAs must pay attention to? Jonathan Addington, president of CyberSecureRIA, points out “three non-negotiables:”
- written cybersecurity policies
- 30-day customer breach notifications
- complete vendor accountability
“The SEC is done with handshake agreements and informal procedures – they want everything documented and provable,” Addington explains. “Here’s the kicker: you can outsource IT tasks, but you can’t outsource liability. Your cloud provider’s security failure becomes your compliance nightmare.”
Part of maintaining cybersecurity compliance is building an effective RIA tech stack. This guide shows you how.
The SEC’s cybersecurity rules are designed to better prepare financial firms against looming cyber threats. While compliance can be complicated, there are practical ways for RIA firms to meet new requirements.
Here’s a step-by-step guide:
Step 1: Do an in-depth risk assessment
To create an effective cybersecurity compliance program, the first step is identifying and evaluating potential risks. Begin with an inventory of your digital assets, including hardware, software, and data. Assess vulnerabilities and document your findings. Prioritize cyber risks based on potential losses and come up with steps to safeguard against them.
“If you don’t know where your data is, you can’t protect it,” Addington says. “Start with a comprehensive inventory of every piece of client information and implement technical controls like multi-factor authentication and endpoint detection.”
Step 2: Develop and maintain written policies and procedures
Your policies and procedures must align with the findings of your risk assessment. These must be as detailed and clear as possible. Be sure that your policies cover all aspects of your cybersecurity program. Some key areas include:
“The SEC doesn’t want to hear about your cybersecurity program – they want to see it in writing,” Addington says. “Develop tested incident response plans and conduct rigorous vendor due diligence with SOC 2 reports and contractual security commitments. Documentation isn’t just good practice anymore; it’s your get-out-of-jail-free card during an SEC examination.”
It is also important to review your procedures regularly and update them as new cybersecurity threats emerge.
Step 3: Boost incident response readiness
Your incident response plan must provide detailed steps for detecting and responding to a cyberattack. It must also establish a clear process for determining which incidents require reporting to the SEC and how these should be reported. It also helps to test your incident response plan regularly through tabletop exercises.
Step 4: Strengthen vendor management
Practice due diligence when choosing a service provider. Find out if they have sufficient cybersecurity controls in place. It helps to include cybersecurity compliance requirements, including breach notifications, in vendor contracts. Have a plan ready for addressing vendor-related cyberattacks.
Step 5: Establish continuous training and monitoring
To maintain compliance, your RIA firm needs to monitor your cybersecurity status regularly. This includes conducting vulnerability assessments and penetration testing. You also need to provide employees with ongoing training to increase awareness of evolving cyber risks.
Performing a cyber mock audit is a good strategy that’s often underutilized. This lets your firm identify the strengths and weaknesses of your cybersecurity program. It also allows you to correct gaps before getting a regulatory audit.
The SEC does annual reviews of cybersecurity programs, so take steps to ensure that your firm remains compliant.
Step 6: Keep records accurate and secure
Regulation S-P requires RIAs to maintain accurate records of all cybersecurity activities. These include:
- policies and procedures
- risk assessments
- incident response plan
- vendor due diligence
Make sure that your recordkeeping practices comply with SEC requirements.
Here’s a downloadable checklist of the steps on how to make your RIA cyber-compliant:

Having the right tools is also key to maintaining cybersecurity compliance. Among these is RIA in a Box. Find out if the platform fits your business’ needs in this review.
There are a few more rules that the SEC has imposed to protect investors and ensure that RIAs are prepared to address cybersecurity threats. These include:
SEC Rule 206(4)-7
Also known as the Investment Adviser Compliance Program Rule, this requires RIAs to develop and maintain written compliance policies and procedures. These include measures to protect client data and prevent cyber breaches.
Regulation S-ID
Also known as the Identity Theft Red Flags Rule, this requires RIA firms to develop and implement a program to detect, prevent, and mitigate identity theft. Rule 201, in particular, states that firms must implement an identity theft prevention program (ITPP) related to the opening or maintenance of covered accounts.
Compliance is among the hallmarks of a top wealth management team. Get to know America’s most distinguished firms in the industry in this special report.
RIAs handle sensitive client information, making them attractive targets for hackers.
“RIAs are sitting on a goldmine of sensitive data that cybercriminals desperately want – Social Security numbers, account details, and complete financial profiles,” Addington explains. “To boot: this is often data on the wealthiest individuals!”
He adds that unlike many businesses, RIAs act as fiduciaries with a legal obligation to protect client interests, which extends to safeguarding their data.
“A single breach can destroy decades of trust and trigger regulatory penalties. With the SEC’s updated Regulation S-P amendments, cybersecurity has moved from ‘nice to have’ to ‘must have;’ it’s now both a legal requirement and a business survival issue.”
For more information on cybersecurity compliance and SEC regulations, subscribe to InvestmentNews+. Here, you can access premium content, data, and investment analysis.
[ad_2]

