[ad_1]
Today INTERPOL announced the results of Operation Serengeti 2.0, a sweeping crackdown on cybercrime across Africa that shows how large-scale, coordinated efforts can disrupt illicit activity. The operation led to 1,209 arrests, the dismantling of more than 11,000 malicious infrastructures, and the recovery of nearly USD 100 million. More than numbers, these results are proof that proactive intelligence and collaboration across borders deliver measurable impact against global cybercrime.
TRM is proud to have supported INTERPOL in Operation Serengeti 2.0.
Running from June to August 2025, Serengeti 2.0 brought together investigators from 18 African countries and the United Kingdom to tackle ransomware, online scams, business email compromise, and other high-impact threats. These crime types were highlighted as top risks in INTERPOL’s Africa Cyberthreat Assessment Report, and the operation mobilized international agencies alongside private sector partners to act on those risks at scale. Authorities seized fraudulent infrastructure, disrupted illicit mining centers, and dismantled scam networks spanning multiple jurisdictions.
INTERPOL investigators used actionable blockchain intelligence to expand the scope of Operation Serengeti 2.0 and move more quickly against cybercriminal infrastructure. Leads provided by TRM on ransomware and fraud activity in Ghana and the Seychelles gave authorities critical insights ahead of the operation.
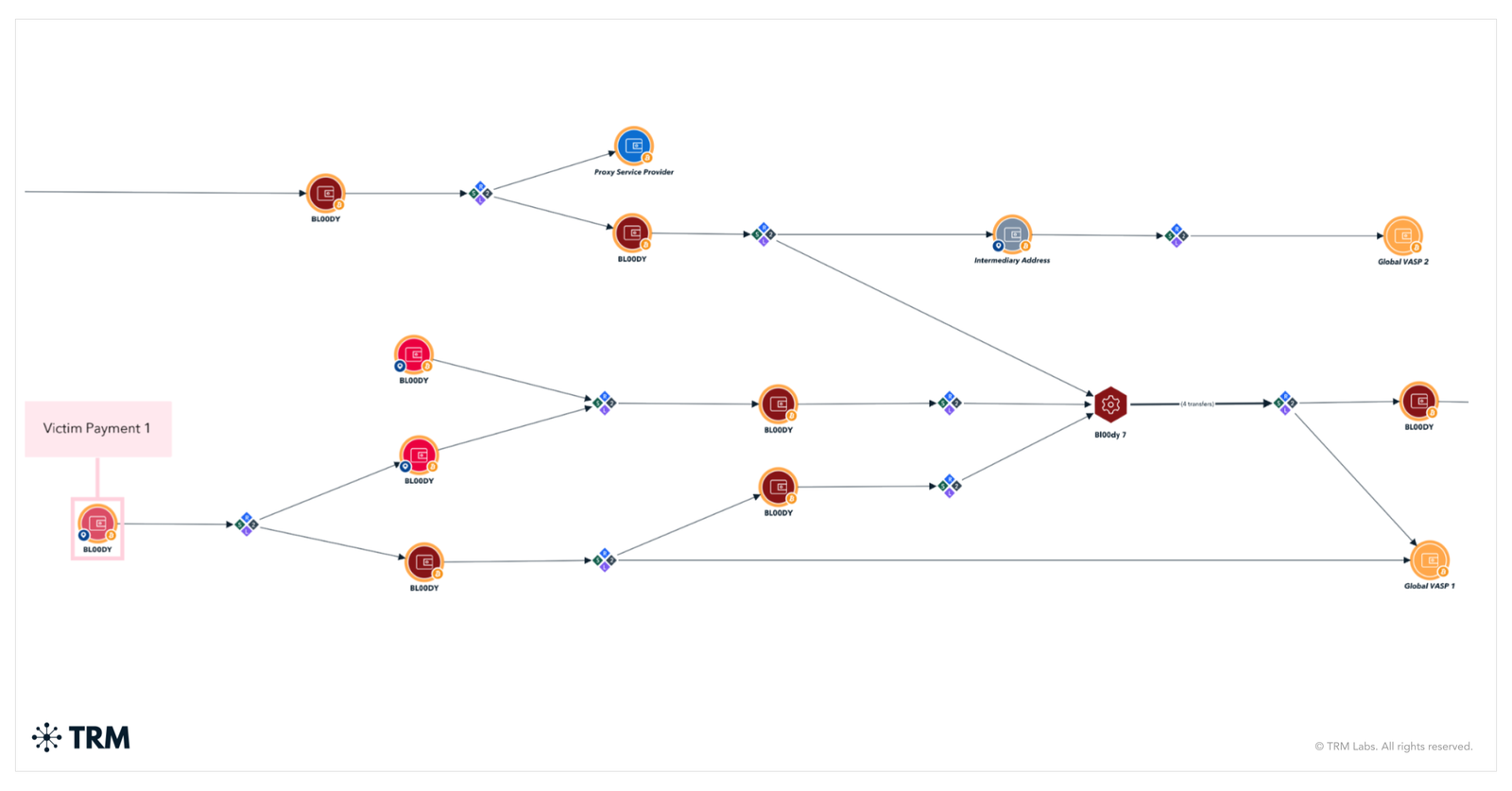
In Ghana, investigators pursued leads tied to the Bl00dy ransomware group, a Conti spin-off that has targeted education, healthcare, and public sector victims worldwide. Analysis suggested that elements of Bl00dy’s laundering infrastructure were active in the country, pointing to an affiliate or operator on the ground.
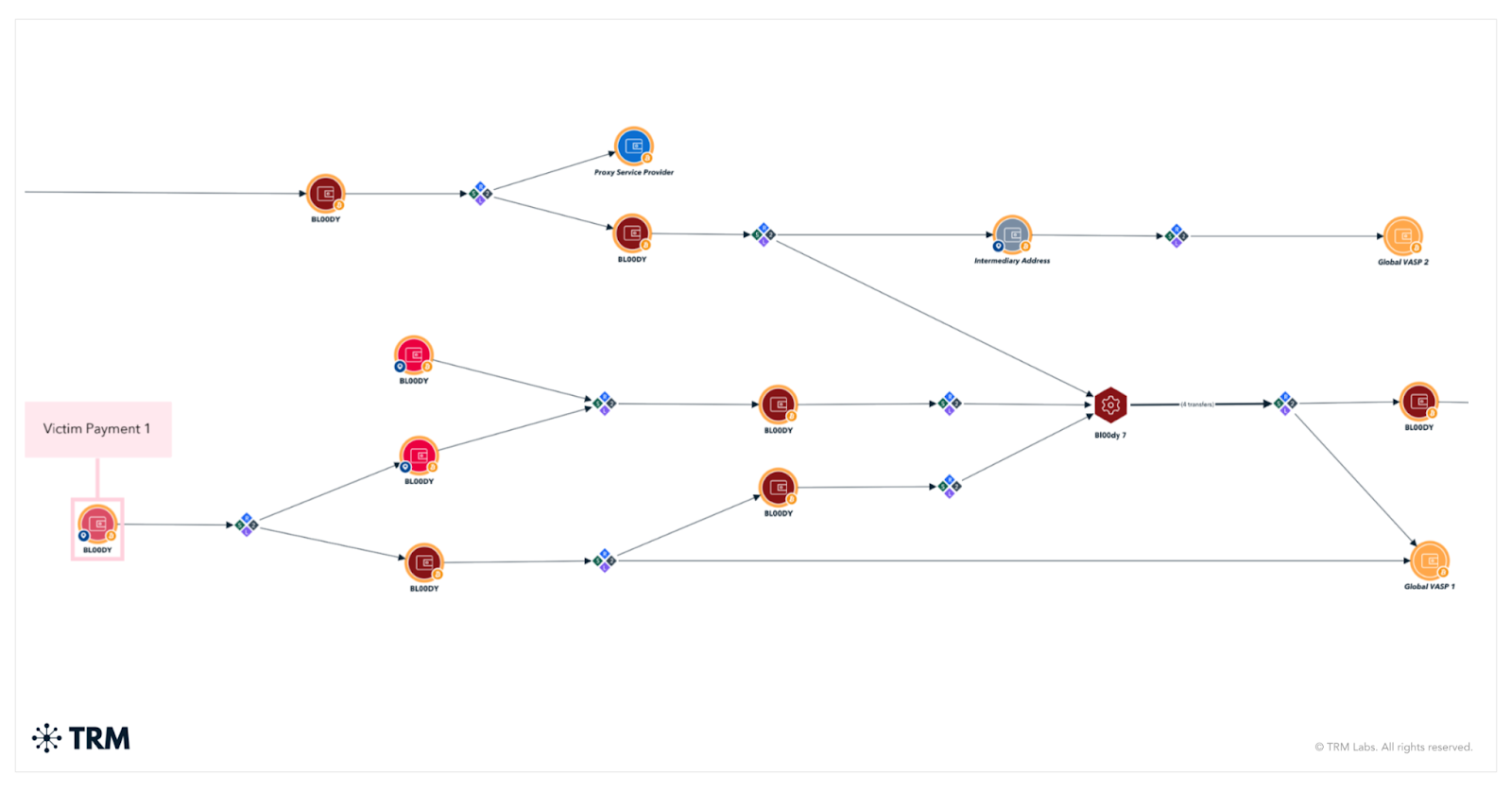
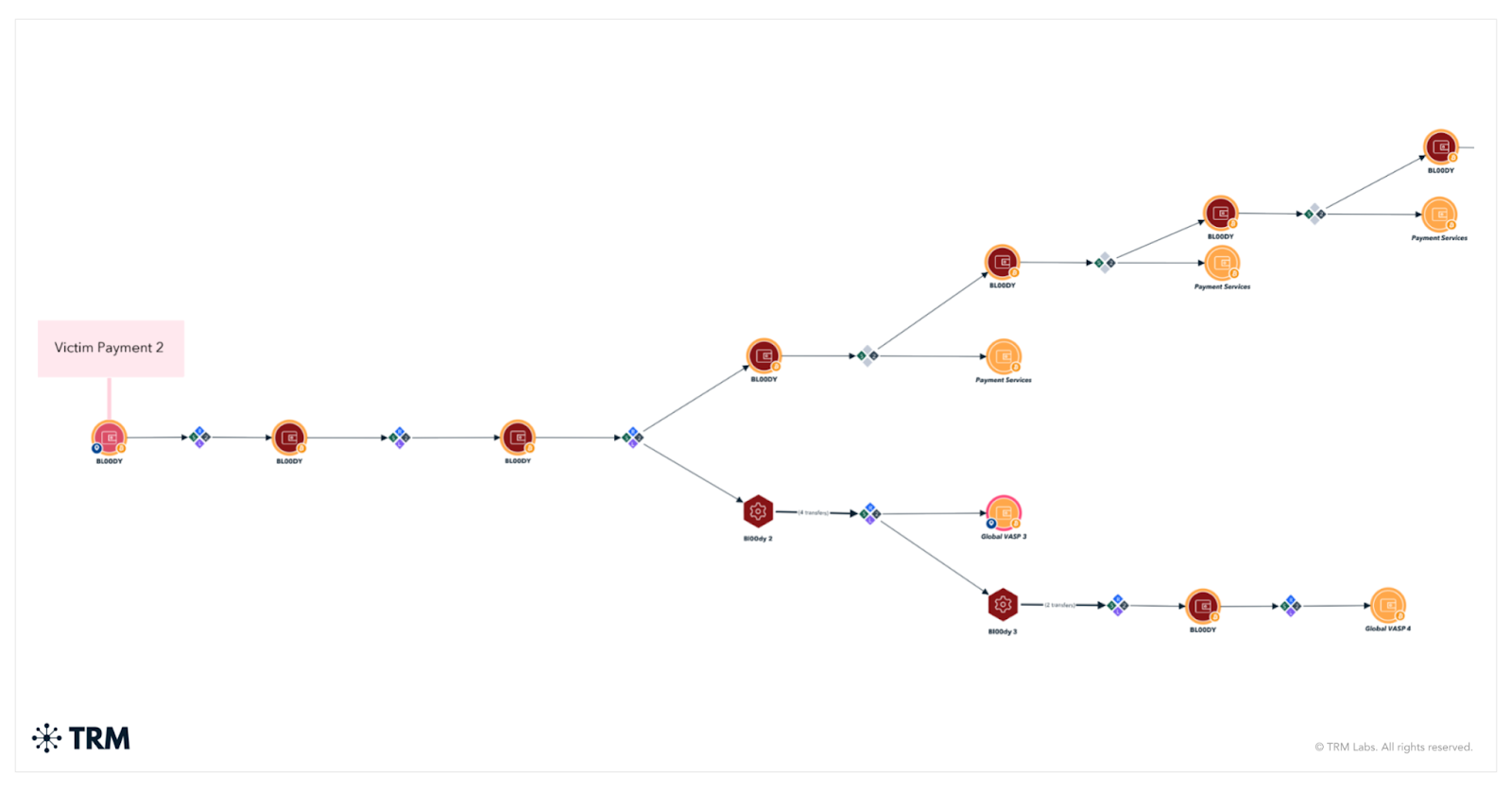
In the Seychelles, investigators acted on intelligence connected to the RansomHub ransomware group, a rebrand of Knight ransomware that has rapidly expanded its operations since 2024. These insights allowed INTERPOL to broaden the range of targets and dismantle additional criminal infrastructure during the campaign.
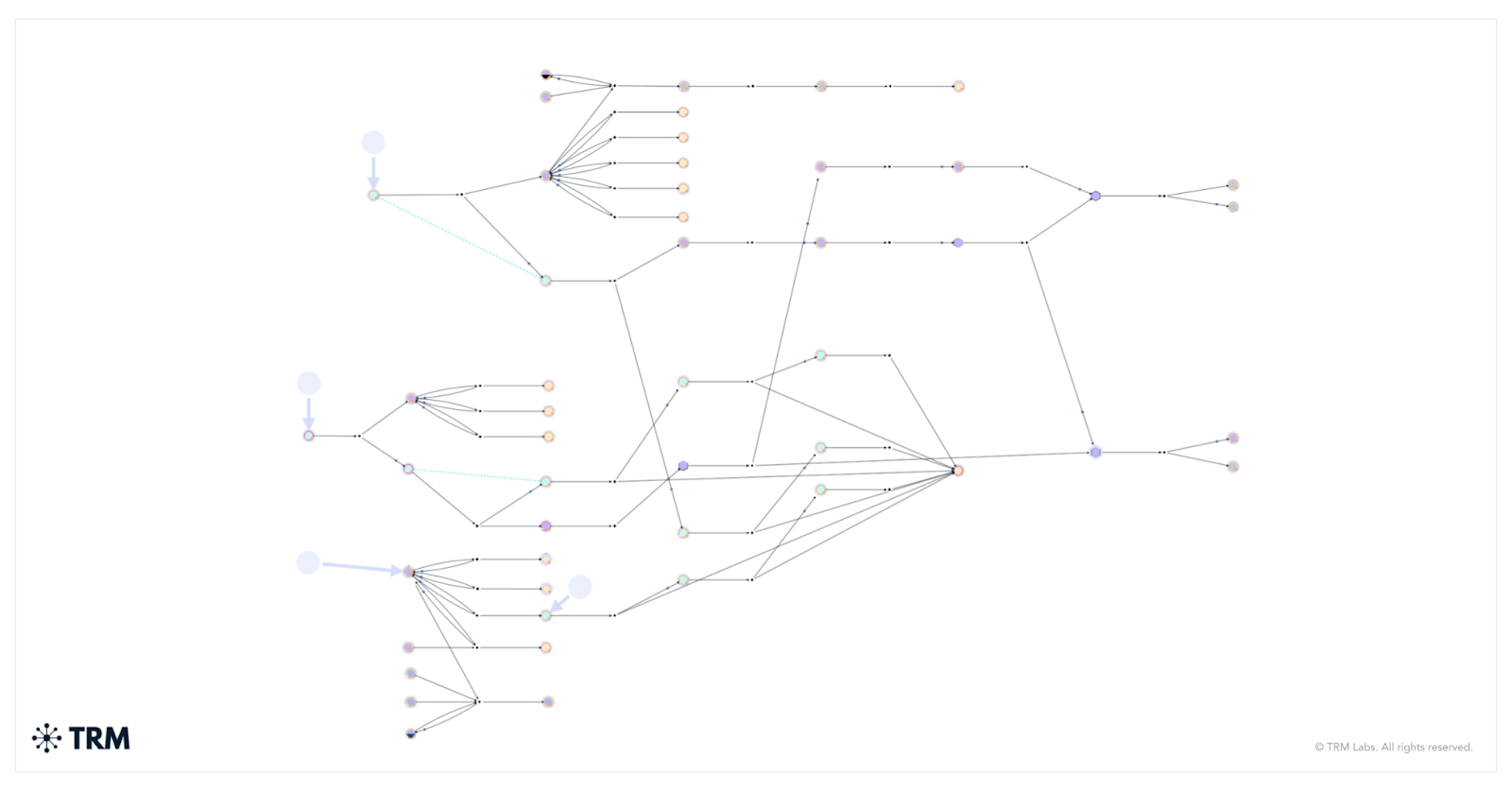
By entering Serengeti 2.0 with these leads in hand, INTERPOL was able to accelerate its response, trace illicit flows more effectively, and deliver a wider set of disruptions.
Operational highlights were significant. In Angola, authorities dismantled 25 illicit cryptocurrency mining centers run by foreign nationals, seizing mining equipment and power stations worth more than USD 37 million. In Zambia, investigators disrupted a large-scale investment fraud scheme impacting an estimated 65,000 victims who collectively lost over USD 300 million. Authorities in Côte d’Ivoire dismantled an international inheritance scam originating in Germany, arresting the ringleader and seizing vehicles, cash, and luxury goods. Across the continent, investigators confiscated forged passports, shut down scam centers, and disrupted transnational criminal networks that had victimized nearly 88,000 people.
These results underscore the importance of intelligence sharing and joint operations in countering modern cybercrime. Actionable data provided ahead of operations gave investigators time to prepare and align resources, while private sector collaboration ensured that crypto-related activity could be traced and disrupted in real time.
The results also come the same week that TRM announced the launch of the Beacon Network, the first real-time crypto crime response system. If Serengeti 2.0 demonstrates what is possible during coordinated, time-bound operations, Beacon points toward a standing capability: an always-on ecosystem where law enforcement, industry, and independent researchers share intelligence in real time to stop illicit funds before they disappear. Serengeti proved that when information sharing happens before and during an operation, results follow. Beacon is about making that same model the default rather than the exception.
[ad_2]