[ad_1]
On 20 May 2025, the cyber threat landscape was unsettled once again when a developer linked to the VanHelsing ransomware-as-a-service (RaaS) group leaked critical components on a well-known hacking forum. Going by the name “th30c0der”, this former associate of the group tried to sell the entire source code for the VanHelsing ransomware on the Russian Anonymous Marketplace (RAMP) forum for $10,000.1
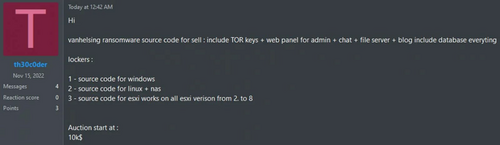
Source: https://x.com/Ransom_DB/status/1924907198813024301/photo/1
The leaked materials included:
- The affiliate control panel, which is used to manage victims and track payments.
- The data leak site, a Tor-based blog for publishing data of non-paying victims.
- Builders for various platforms, including Windows, Linux, BSD, ARM, and VMware ESXi.
In response, the main VanHelsing operators decided to release the source code themselves, accusing the developer of being a scammer who was trying to con potential buyers. This bold move seems to be an attempt to maintain their reputation within the cybercrime community, where trust is crucial for ongoing collaboration.2
The VanHelsing group first appeared in March 2025 and quickly gained attention for its aggressive targeting of cross-platform systems. By May, they had at least eight known victims, though the actual number is likely higher. Their ransomware can encrypt both Windows and Unix-based systems, making it a threat to a wide range of organisations, including those with hybrid or cloud-native infrastructure.
So what?
The leak of the ransomware builder and backend infrastructure is significant for cybersecurity professionals, law enforcement, risk managers, and business leaders alike.
Lowering the barrier to entry
With the source code now public, even those with limited technical skills can customise and deploy their own versions of VanHelsing. This lowers the bar for launching ransomware attacks, increasing the potential for widespread exploitation by low-level cybercriminals or new threat groups. This is a common theme in modern cybercrime ecosystems, in which it has become much easier to participate, thanks to user-friendly malware, specialist roles and ever-more ways to launder the proceeds with anonymity.
Fragmentation and mutation
History shows that leaked ransomware code often leads to new variants. These “franken-ransomware” threats can be more evasive or destructive, making them harder to detect. The VanHelsing leak could lead to many spinoff groups, complicating attribution and threat modelling.
Targeting of critical infrastructure
VanHelsing’s support for Linux, ARM, and VMware ESXi is particularly concerning, as these platforms are common in enterprise and critical infrastructure environments, such as:
- Cloud computing infrastructure
- Government networks
- Healthcare systems
- Industrial control systems (ICS)
The availability of the builder increases the risk that unsophisticated actors could target complex systems.
Opportunity for defenders and law enforcement
On the plus side, the leak offers opportunities for cybersecurity defenders. Access to the source code allows for:
- Better reverse engineering
- Development of detection signatures and network behaviour profiles
- Potential creation of decryption tools
- Attribution work linking VanHelsing to other groups or infrastructure
Organisations like Europol, the FBI, CERTs, the NCSC and NCA might use this intelligence to track affiliates, block infrastructure, or help victims decrypt data.
What should businesses do?
In light of this development, organisations should:
- Review their ransomware resilience posture, including backup, restoration, and incident response plans.
- Harden systems commonly targeted by Linux/ESXi malware, such as disabling unnecessary SSH, RDP, and remote admin ports.
- Update endpoint detection and response (EDR) systems to monitor for VanHelsing-related behaviours.
- Educate IT and executive teams about the increased risk of ransomware from open-source builders.
The VanHelsing ransomware builder leak is an archetypal example of how quarrels between cybercriminals can have wide-reaching security implications. As seen with similar leaks in the past, this kind of exposure doesn’t eliminate the ransomware threat – it makes the problem worse.
Organisations across all sectors should treat this as an early warning and prepare accordingly. In the evolving arms race of cybercrime, leaked code means an impending wave of attacks is likely on the way.
[ad_2]
Source link

