[ad_1]

Redazione RHC : 17 July 2025 13:56
HackerHood, Red Hot Cyber’s team of ethical hackers, has created something rarely seen outside of the most exclusive conferences: a live workshop demonstrating, step by step, a complete ransomware attack.
This is not a theoretical simulation, but a real journey into the dark side of the internet, where a simple phishing email can lead to a completely compromising a computer system in just a few minutes. All this was possible thanks to the collaboration with OMNIA and With Secure, two companies that have always focused on a culture of security.
In fact, this exclusive workshop presented by Antonio Montillo and Alessandro Moccia of Framework Security was shown during a closed-door event organized by Omnia and WithSecure, on July 2, 2025, at the modern Tier IV datacenter in Siziano (PV).
The goal? See, understand, and protect yourself in time!
The two professionals were able to explain in simple yet detailed terms the technical complexity behind a cyber attack. What we normally read in reports, between acronyms and diagrams, here comes to life before our eyes: from the initial lure that induces the victim to click, to the execution of the malware, up to data encryption and the classic ransom screen. A journey that isn’t spectacular like a cyber attack seen in a top-rated movie, but it is real and profoundly educational.
The beauty of this workshop is that it didn’t just show “what” ransomware does, but also explained “how” and “why” it works. It’s clear how important the technical preparation of defense professionals is: Knowing the tactics, techniques, and procedures used by criminals is the only way to build effective barriers.
It’s often thought that a good antivirus or a few updates is enough to keep you safe, but the reality is quite different: cybersecurity is an ongoing, shared effort, involving study, testing, simulations, and constant updating.
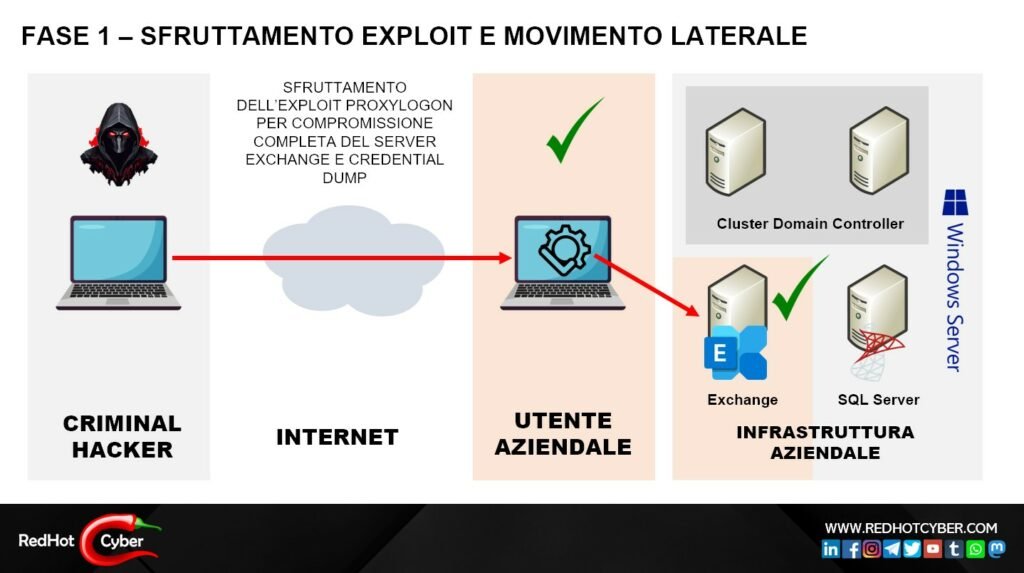
The infrastructure was composed of the following software components:
- Client workstations
- Windows domain controller
- Microsoft Exchange mail server
- SQL Server Server
Precisely for this reason, we decided not to keep this content just for those who were present at the event, but to share it with everyone.
A video of part of the workshop is available on our YouTube channel : yes, it’s a bit long, but believe us, it’s worth every second. By watching it, you’ll understand not only the destructive power of ransomware, but also how subtle and convincing the initial attack can be. It’s a concrete way to raise awareness among companies, professionals, and the simply curious about a threat that affects organizations large and small every day.
In a world where technology is ever faster, initiatives like this one by Omnia and With Secure help us stop for a moment and truly observe the risks we face.
HackerHood and Red Hot Cyber want to take the culture of security beyond technical environments and make it accessible to everyone, because only by understanding how an attack works can we truly learn to defend ourselves. And now it’s your turn: watch the workshop, share it, and become part of this daily battle against cyber threats.
Because ransomware isn’t stopping. And neither should we!
 Redazione
RedazioneThe editorial team of Red Hot Cyber consists of a group of individuals and anonymous sources who actively collaborate to provide early information and news on cybersecurity and computing in general.
Lista degli articoli
[ad_2]
