[ad_1]
Microsoft Threat Intelligence has released fresh research uncovering how financially motivated actor Storm-0501 has shifted away from traditional ransomware deployment to cloud-native ransomware operations.
Known for earlier campaigns targeting U.S. schools and healthcare providers, Storm-0501 has evolved rapidly, adapting to hybrid cloud environments and exploiting critical gaps in security visibility across enterprises.
Instead of relying purely on malware to encrypt local endpoints, Storm-0501 now abuses cloud-native capabilities. Their modern approach involves data exfiltration at scale, deletion of backups, and the compromise of Azure resources, followed by extortion demands.
The shift signals an escalation of the ransomware threat landscape, where valid administrative credentials and cloud services themselves replace the need for persistent malware.
How the Attack Unfolds
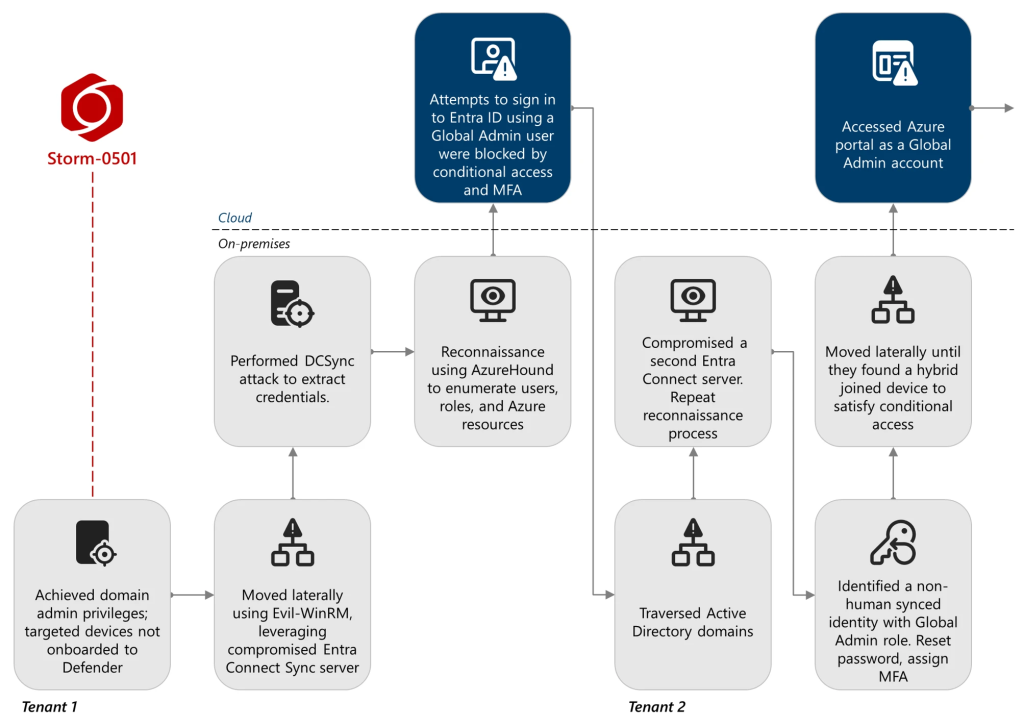
In recent incidents, Storm-0501 began by breaching Active Directory (AD) through compromised domain administrator accounts. They then pivoted into Microsoft Entra ID (formerly Azure AD) by exploiting synchronization servers.
A key tactic involved compromising Entra Connect Sync Directory Synchronization Accounts (DSA), which enabled the enumeration of cloud resources using tools such as AzureHound.
Microsoft Threat Intelligence has released fresh research uncovering how financially motivated actor Storm-0501 has shifted away from traditional ransomware deployment to cloud-native ransomware operations.
Known for earlier campaigns targeting U.S. schools and healthcare providers, Storm-0501 has evolved rapidly, adapting to hybrid cloud environments and exploiting critical gaps in security visibility across enterprises.
Instead of relying purely on malware to encrypt local endpoints, Storm-0501 now abuses cloud-native capabilities. Their modern approach involves data exfiltration at scale, deletion of backups, and the compromise of Azure resources, followed by extortion demands.
The shift signals an escalation of the ransomware threat landscape, where valid administrative credentials and cloud services themselves replace the need for persistent malware.
How the Attack Unfolds
In recent incidents, Storm-0501 began by breaching Active Directory (AD) through compromised domain administrator accounts. They then pivoted into Microsoft Entra ID (formerly Azure AD) by exploiting synchronization servers.
A key tactic was compromising Entra Connect Sync Directory Synchronization Accounts (DSA), which allowed enumeration of cloud resources using tools such as AzureHound.
The group then escalated privileges through a misconfigured non-human Global Admin account lacking multi-factor authentication (MFA). By resetting its password on-premises—propagated via cloud sync—they obtained full Entra ID access.
Conditional Access policies slowed the attack, but Storm-0501 circumvented restrictions by moving laterally across hybrid-joined devices until they validated sign-ins as Global Admin.
Once inside, persistence was established by registering a maliciously federated domain with AADInternals, enabling the threat actors to impersonate legitimate users with Security Assertion Markup Language (SAML) tokens.
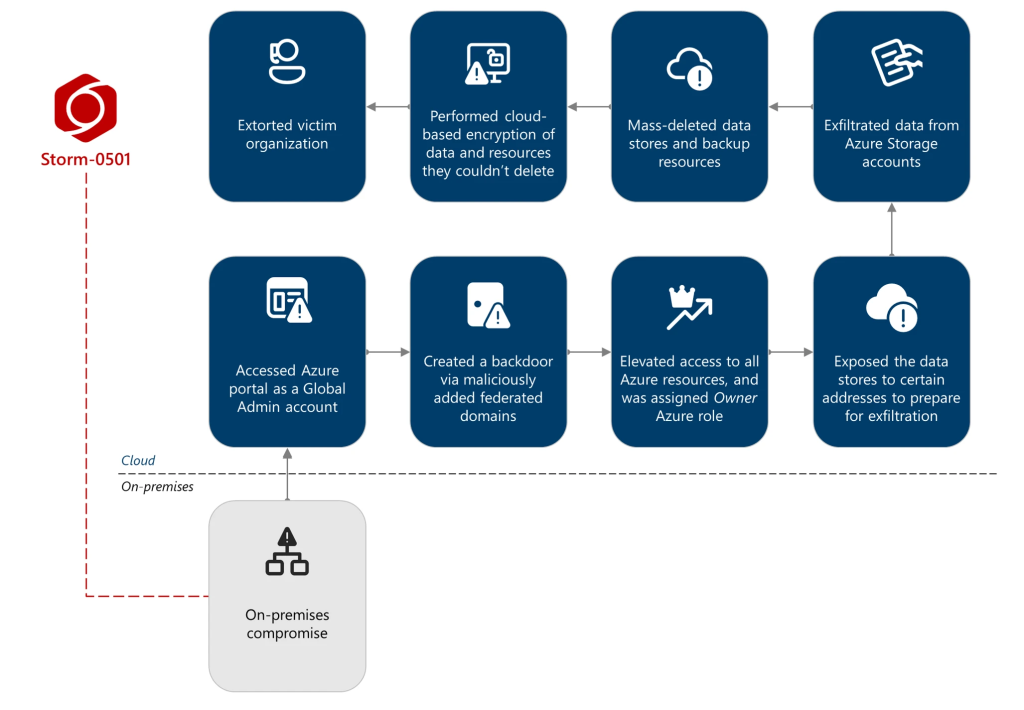
Using Microsoft.Authorization/elevateAccess/action, Storm-0501 escalated privileges further to User Access Administrator and Owner roles across multiple Azure subscriptions, granting unfettered control.
From there, discovery and exfiltration operations began. Sensitive data was accessed and transferred out using AzCopy CLI. To cripple recovery, they mass‑deleted snapshots, restore points, storage accounts, and Recovery Services vaults by abusing legitimate Azure APIs.
When deletion protections were encountered, the actor attempted to dismantle immutability policies and resource locks. For remaining assets, they deployed customer-managed keys in new Azure Key Vaults, encrypted blobs, and then deleted the keys—effectively locking victims out.
Microsoft noted final-stage extortion often occurred directly through Microsoft Teams messages from compromised accounts.
Mitigation Guidance
Microsoft stresses several countermeasures: enforcing comprehensive endpoint monitoring, deploying Defender for Cloud and Defender for Storage, mandating MFA, preferably phishing-resistant methods, for all privileged accounts, restricting DSA accounts via Conditional Access, and applying Azure immutability and purge protection on backups.
The analysis highlights a concerning trend: Storm-0501 leverages legitimate cloud features and misconfigurations, rendering its operations stealthier and more complex to detect than conventional malware-based ransomware.
As hybrid cloud adoption grows, organizations must prepare for this new wave of cloud-native ransomware.
Once inside, persistence was established by registering a maliciously federated domain with AADInternals, enabling the threat actors to impersonate legitimate users with Security Assertion Markup Language (SAML) tokens.
Using Microsoft.Authorization/elevateAccess/action, Storm-0501 escalated privileges further to User Access Administrator and Owner roles across multiple Azure subscriptions, granting unfettered control.
From there, discovery and exfiltration operations began. Sensitive data was accessed and transferred out using AzCopy CLI. To cripple recovery, they mass‑deleted snapshots, restore points, storage accounts, and Recovery Services vaults by abusing legitimate Azure APIs.
When deletion protections were encountered, the actor attempted to dismantle immutability policies and resource locks. For remaining assets, they deployed customer-managed keys in new Azure Key Vaults, encrypted blobs, and then deleted the keys—effectively locking victims out.
Microsoft noted final-stage extortion often occurred directly through Microsoft Teams messages from compromised accounts.
Mitigation Guidance
Microsoft stresses several countermeasures: enforcing comprehensive endpoint monitoring, deploying Defender for Cloud and Defender for Storage, mandating MFA, preferably phishing-resistant methods, for all privileged accounts, restricting DSA accounts via Conditional Access, and applying Azure immutability and purge protection on backups.
The analysis highlights a concerning trend: Storm-0501 leverages legitimate cloud features and misconfigurations, rendering its operations stealthier and more complex to detect than conventional malware-based ransomware.
As hybrid cloud adoption grows, organizations must prepare for this new wave of cloud-native ransomware.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates
[ad_2]
Source link

