[ad_1]
The Qilin ransomware gang has introduced a “Call Lawyer” feature for its affiliates, announced on a Russian-speaking darknet forum.
This Ransomware-as-a-Service (RaaS) enhancement provides on-demand legal assistance during extortion negotiations, leveraging the perceived authority of legal counsel to amplify pressure on victims.
According to the gang’s post, affiliates can invoke Qilin’s “legal department” to offer victims a “legal evaluation of potential damages,” projecting substantial economic and reputational losses from regulatory fines, lawsuits, and compliance breaches stemming from the ransomware incident.
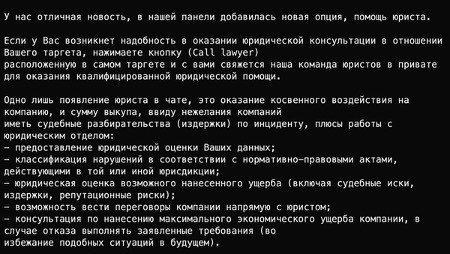
This approach shifts the extortion narrative from direct threats by cybercriminals to indirect projections of governmental or legal repercussions, potentially coercing organizations into paying ransoms to mitigate amplified risks.
Innovative Extortion Strategies
Cybersecurity analysts liken this to previous innovations, such as ransomware groups filing Securities and Exchange Commission (SEC) complaints against non-disclosing victims, thereby weaponizing regulatory frameworks against breached entities.
Qilin, ranked as the third most active ransomware operation this year with technically mature infrastructure since late 2022, positions this feature as a value-add for affiliates, alongside tools for spamming corporate emails and an in-house “journalism” team for propaganda support.
While some experts dismiss it as a marketing ploy to lure affiliates from competing RaaS platforms, recent law enforcement actions such as the Thai raid uncovering a Chinese ransomware group co-located with scammers underscore the plausibility of criminal enterprises employing legal expertise, akin to organized crime syndicates retaining attorneys for operational legitimacy.
Delving deeper into the underpinnings, criminological frameworks like crime convenience theory provide insight into why legal professionals might align with such illicit operations.
This theory posits that financial motives, coupled with low detection risks afforded by attorney-client privileges, can drive lawyers toward facilitating crime, especially amid personal stressors such as financial hardship or career setbacks.
Potential Vulnerabilities
According to the report, Studies highlight how lawyers in diverse roles from compliance officers in under-scrutinized financial institutions to those establishing shell companies often operate in gray areas, enabling illicit activities with minimal repercussions.
For instance, protections like privileged communications allow lawyers to shield client interactions, a tactic echoed in defenses of hacktivists where operational security measures thwart investigations.
In Qilin’s context, even non-licensed individuals with legal knowledge could simulate expertise, fostering victim belief in credible threats during negotiations.
However, this “legal department” may inadvertently create vulnerabilities for the gang.
Ransomware operators typically maintain stringent operational security, but lawyers, potentially lacking equivalent technical acumen, could expose communications through insecure records, billable hour logs, or traceable interactions.
Targeting law firms has become a ransomware trend due to their repositories of sensitive data, and Qilin’s integration of legal services could yield evidentiary trails for attribution by investigators.
Law enforcement might exploit this by focusing on direct extortion involvement, bypassing traditional privileges when lawyers actively participate in crimes.
To counter such influence, victim organizations should verify claims independently, engage their own counsel for negotiations, and report incidents promptly to regulatory bodies, thereby diffusing intimidation tactics.
As ransomware evolves, this development signals a convergence of cybercrime with professional services, urging enhanced scrutiny of legal enablers in illicit ecosystems.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
[ad_2]

