[ad_1]
A new report from the Cyber Threat Alliance warns that the era of quantum risk is already underway, and security teams need to stop treating it like a problem for tomorrow.
The report, Approaching Quantum Dawn: Closing the Cybersecurity Readiness Gap Before It’s Too Late, urges companies to prepare for a world where today’s encryption could be broken by quantum computers. But it’s not all doom and gloom. The report focuses on what can be done now: starting with building what it calls cryptographic agility.
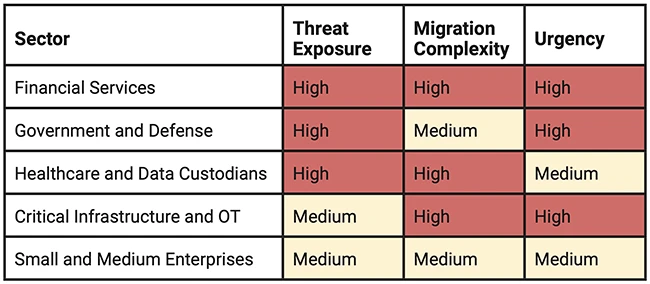
Sector Quantum Risk Readiness Heatmap (2025–2030 Outlook) – Source: Cyber Threat Alliance
But there’s a catch. For many organizations, especially in tightly regulated sectors like finance and healthcare, sticking to fixed cryptographic standards is the norm. These are the rules, and those don’t always leave much room for agility.
Cryptographic agility meets compliance challenges
“This creates a critical tension that must be managed not by choosing one over the other, but by embedding agility within compliant frameworks,” Emerson Johnston, CTA’s Cyber Threat Report Analyst, told Help Net Security.
That means designing systems that don’t lock organizations into one cryptographic choice for the next ten years. Instead, the report’s authors urge companies to use modular architectures, which are systems built to support algorithm changes with minimal disruption.
“Cryptographic agility should be treated as a strategic capability,” Johnston said. “It enables organizations to meet standards while being prepared to pivot as threats evolve or standards shift.”
This idea of being ready to pivot is central to the report’s message. Quantum computing may still be years away from breaking encryption at scale, but attackers aren’t waiting. Tactics like Harvest Now, Decrypt Later involve stealing encrypted data now and cracking it when quantum capabilities catch up. That puts long-lived sensitive data such as medical records, intellectual property, and classified documents at risk now, not later.
QKD sounds promising but falls short for most
One option that often comes up in quantum discussions is Quantum Key Distribution (QKD). It uses principles of quantum physics to secure data and detect eavesdropping. The report acknowledges the potential but urges caution.
“While it offers compelling theoretical benefits… it remains constrained by significant scalability, infrastructure, and integration limitations,” Johnston said. “QKD should not be viewed as a substitute for post-quantum cryptography, but rather as a niche complement suited to specific, high-security use cases.”
In plain terms: QKD is interesting, but not ready for broad use. It’s expensive, hard to scale, and doesn’t integrate easily with most systems. That makes it a poor match for most organizations, at least for now.
Post-quantum readiness starts with practical steps
So what should security leaders focus on instead?
“Post-quantum cryptography (PQC) solutions, particularly hybrid schemes, offer a more practical and widely deployable path to quantum resilience,” Johnston said. These schemes combine classical and post-quantum algorithms, offering stronger protection without requiring wholesale infrastructure changes.
The report recommends starting with pilot deployments, building visibility into where cryptography is used (through cryptographic bills of materials, or CBOMs), and treating agility not as a buzzword but a core part of risk management.
Quantum disruption may not happen overnight, but the time to act is now.
[ad_2]