[ad_1]
Key Points
-
The decline of legacy ransomware groups has created a vacuum that’s quickly been filled by emerging groups like “Qilin.” Nonetheless, this quarter still saw a 31% decrease in named victims compared to the previous quarter.
-
Leading ransomware-as-a-service (RaaS) groups like Qilin and “Akira” rely on the mass exploitation of vulnerabilities to compromise organizations with speed and precision.
-
Future ransomware leaders are likely to succeed by combining automated discovery tools with public proof-of-concept (POC) exploits, accelerating compromises and propelling them to the forefront of the ransomware race.
-
To counter these threats, organizations must prioritize asset discovery and implement a strict patch management framework to ensure exposed and critical devices cannot be exploited by ransomware actors.
The second quarter of 2025 (Q2 2025) brought notable shifts in the ransomware landscape, with groups like “Qilin” and “DragonForce” rising to prominence as some long-standing operations faded into the background. In this report, we’ll look into:
-
The rise of new ransomware groups shaping the threat landscape.
-
How initial access vulnerabilities are enabling large-scale compromises.
-
Ransomware predictions for the rest of 2025.
-
Actionable recommendations to safeguard your organization against evolving threats.
By analyzing the driving forces behind these trends and their ripple effects across industries, this report equips organizations with actionable insights to stay ahead in the battle against ransomware.
Qilin Prospers as Clop Goes Dormant
Following a meteoric surge in ransomware victims in Q1 2025, Q2 saw a 31% decrease in the number of organizations named on ransomware data-leak sites, marking a return to more typical levels. However, this shift brought a changing of the guard: Qilin overtook “Clop” to become the most active ransomware-as-a-service (RaaS) group this quarter.
Clop is notorious for staying dormant until an exploitable weakness is identified; right now, it’s likely searching for its next vulnerability before staging another high-profile resurgence. In Q1 2025, Clop exploited Cleo vulnerabilities CVE-2024-50623 and CVE-2024-55956 to launch a mass campaign, naming 389 victims on its data-leak site in February alone—more than any other ransomware group during that period. This highlights a recurring challenge for organizations: Unpatched systems remain a critical weakness, enabling widespread ransomware deployment and data exfiltration. Clop’s ability to exploit vulnerabilities en masse reinforces the importance of proactive patch management as a key defense against ransomware.
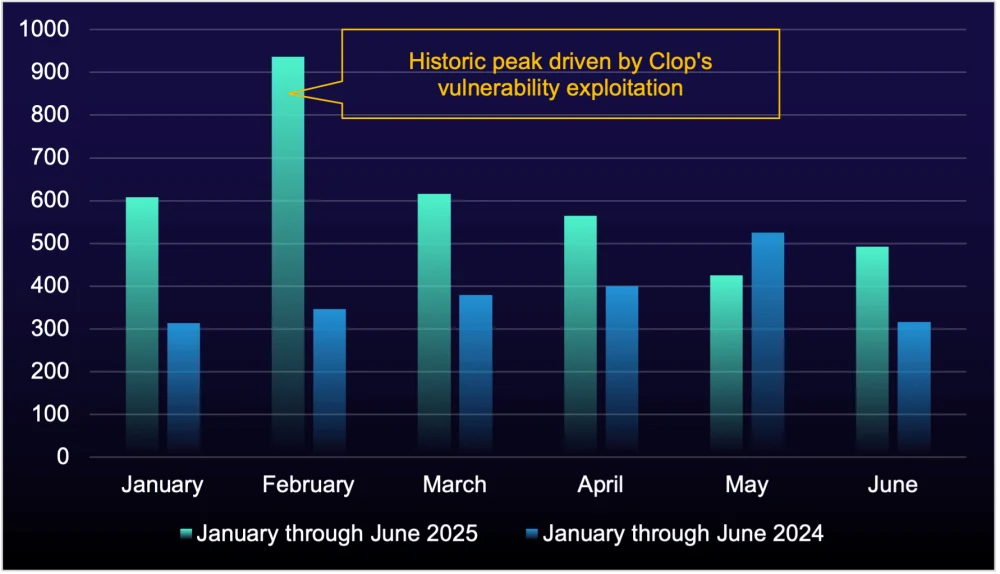
Figure 1: Number of compromised organizations listed on data-leak sites, January through June 2025 vs. January through June 2024
Meanwhile, the “SafePay” RaaS group has emerged as a growing threat, with activity increasing by 42% compared to Q1. Throughout Q2, SafePay heavily targeted organizations in the US and Germany, likely exploiting vulnerabilities in external services to gain initial access. Despite its victimology until now, SafePay’s tactics are globally applicable. In one extortion note sent to an Australia-based construction company, the group stated it breached the organization by “exploiting misconfigurations in network-based software.” This serves as another stark reminder of how RaaS groups are increasingly relying on vulnerabilities to ensure successful ransomware deployment.
Despite a 41% drop in activity between Q1 and Q2 2025, the “Lynx” ransomware group remains a key player, regularly naming new victims on its data-leak site. Last quarter, we identified Lynx as a group to watch, and its continued presence among the top five RaaS groups validates that assessment. Amid ongoing fragmentation in the ransomware ecosystem, Lynx is likely actively working to solidify its reputation as a dominant force. Its persistence amid this turbulence signals that organizations can’t afford to underestimate its potential threat.
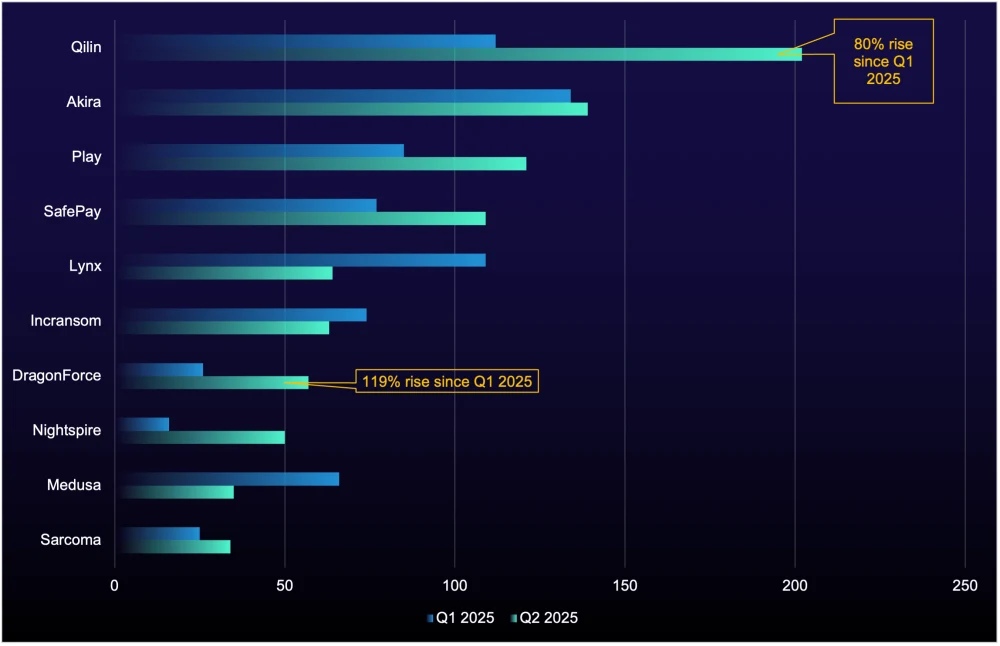
Figure 2: Number of compromised organizations listed on data-leak sites by ransomware group, Q2 2025 vs Q1 2025
Qilin and Akira Rise as Ransomware Giants Falter
Significant law enforcement action against former ransomware leader “LockBit” in early 2024 caused a sharp decline in the group’s activity. Despite teasing the release of “LockBit 4.0” in December 2024, the group has struggled to regain its dominance, naming just 24 organizations on its data-leak site in Q2 2025—just 11% of its Q2 2024 figures. The lasting impact of these enforcement efforts is clear and is highly likely to persist in the mid-term (next three months to one year).
The decline of several other highly active RaaS groups, like “RansomHub” and “Black Basta,” has created an opening for emerging players. Both RansomHub and Black Basta failed to name any organizations on their data-leak sites in Q2, forcing their affiliates to seek new opportunities. This vacuum is now being exploited by emerging groups like Qilin and “Akira,” which have stepped into the spotlight and significantly increased their activity.
Akira’s Activity Skyrockets with 348% Growth
The Akira ransomware group has proven itself remarkably consistent, listing approximately 130 organizations to its data-leak site each quarter this year. However, its activity has increased exponentially compared to 2024, with a staggering 348% rise in the number of organizations named in Q2 2025 compared to the same period last year. Even more striking, Akira has already listed 15% more victims in the first half of 2025 than it did throughout the entirety of 2024. This sharp rise in activity signals a group operating at full force, and it’s highly likely Akira will sustain these elevated activity levels into Q3, continuing to pose a major threat to organizations.
Qilin Leads with 80% Surge
Qilin has emerged as the top ransomware threat this quarter, following an 80% increase in activity in Q2 compared to Q1 2025. This sharp increase is likely attributed to its exploitation of critical Fortinet/FortiGate vulnerabilities—CVE-2024-55591 and CVE-2024-21762—for initial access. It’s likely that Qilin employed automated scripts to identify and exploit these CVEs at scale, consistent with patterns observed in its previous campaigns.
Initially, Qilin’s campaign appeared to focus on Spanish-speaking organizations. However, Q2 revealed a shift in this trend. 80% of the organizations named were based in the US, while Spain and other Spanish-speaking countries each accounted for less than 4% of the total volume. This expansion indicates that the group’s operations were far broader than originally observed and underscores the growing risks posed by vulnerabilities in external remote services, which ransomware operators increasingly exploit to launch large-scale attacks.
The shifting ransomware landscape, marked by the rise of groups like Qilin, presents major challenges for defenders. These emerging operators depend on high attack volumes not only to secure ransom payments, but to establish their reputation and attract affiliates. By directly exploiting critical vulnerabilities, these groups demonstrate greater technical skill and operational independence, enabling faster attacks and wider reach—forcing organizations to confront increasingly sophisticated threats.
Group To Watch
Name: “DragonForce”
Type: RaaS Group
Emergence: December 2023
Victimology: US- and Europe-based wholesale trade; retail trade; and professional, scientific, and technical services (PSTS) organizations.
Highlight: Activity up 119% between Q1 and Q2 2025.
RaaS Model: In April 2025, the group introduced a new “cartel” model, enabling affiliates to conduct attacks under their own branding with technical support from DragonForce. This approach is unique among RaaS operators and is likely to drive future growth.
Competition: DragonForce has defaced the data-leak sites of competitor RaaS groups—including “Blacklock,” “Mamona,” and RansomHub—replacing their branding with its own. These bold moves demonstrate the group’s aggressive expansion strategy and its willingness to take risks to fuel growth.
Scattered Spider: In Q1 and Q2 2025, DragonForce ransomware was likely deployed by “Scattered Spider” against Europe-based retail trade organizations. The group gained initial access by socially engineering IT help desks. This trend of established cybercriminals adopting DragonForce ransomware is likely to grow in the short term (within three months).
Take Action
To remain proactive against threats like Qilin and Akira, organizations should implement AI-powered anomaly detection systems designed to identify unusual behaviors, such as cross-platform operations or the use of custom exploitation scripts. These systems allow security teams to detect and respond to evolving tactics before they’re fully operationalized. Organizations should also prioritize patch management for external-facing devices to prevent threat actors from exploiting vulnerabilities to gain access.
To defend against Qilin, defenders should focus on three key strategies:
-
Enforce Strict Password Polices and MFA: Qilin often gains initial access through valid employee credentials obtained via phishing or purchased on the dark web. Organizations must enforce strict password policies, such as prohibiting password reuse or similarities, and implement multifactor authentication (MFA) to ensure accounts remain secure and inaccessible to threat actors.
-
Disable Unused RMM Tools: Qilin leverges remote monitoring and management (RMM) tools like PsExec and RDP for lateral movement. Organizations should disable RMM tools that aren’t explicitly required for business purposes to limit potential attack surfaces.
-
Monitor Anomalous SSH Traffic: Secure Shell (SSH) is commonly used for remotely accessing network devices. Organizations should monitor SSH traffic originating from accounts or targeting devices that fall outside the scope of the environment. For instance, unusual SSH traffic directed toward VMware ESXi environments—a method frequently exploited by Qilin—may signal a potential attack attempt.
US Remains Primary Ransomware Target as Germany Rises
The US remains the most targeted country, accounting for 67% of the total organizations named on ransomware data-leak sites in Q2. Month after month, RaaS groups focus on the region likely because of its significant financial resources and stringent cybersecurity regulations, which increase the likelihood that organizations will pay ransoms. However, German organizations have now risen to second place, climbing two spots from fourth in Q1 2025. This change is likely influenced by SafePay, which heavily targets organizations in both the US and Germany. While the exact motivation behind this focus is unclear, it’s realistically possible that the group is exploiting vulnerabilities in German-made software or software popular with German organizations. This trend reflects the broader preference of RaaS groups for Western European and North American organizations, which offer similar financial incentives and high ransom payout likelihoods.
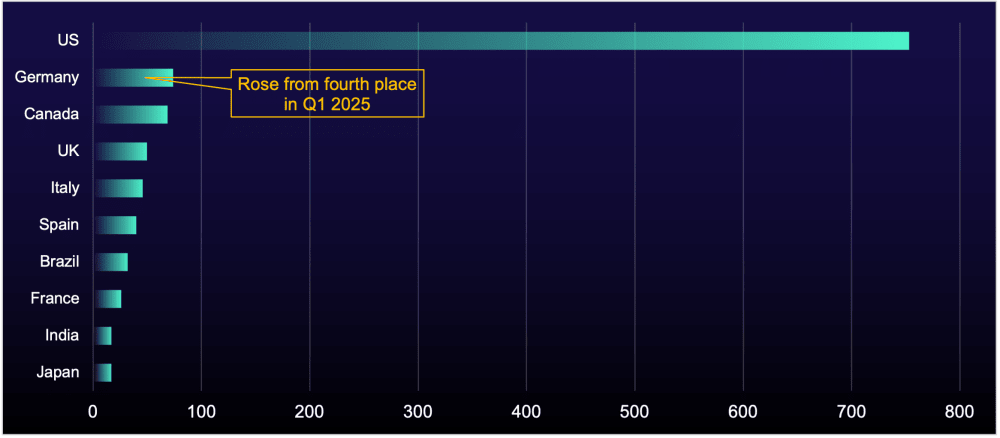
Figure 3: Number of compromised organizations listed on data-leak sites by geography, Q2 2025
As is now standard, manufacturing and professional, scientific, and technical services (PSTS) continue to top the list of targeted sectors. Returning to ransomware normality, construction has regained third place this quarter. In Q1 2025, the retail sector experienced a surge in attacks following Clop’s exploitation of vulnerabilities in Cleo—a software widely used by retail trade organizations. However, this quarter, retail trade accounted for only 4% of total victims in Q2, which is showing how the activity of sophisticated groups like Clop can dramatically shape ransomware trends.
Despite victimology trends, ransomware is inherently opportunistic. The fracturing of established groups and the emergence of new players increases unpredictability, as these groups refine their own tactics to establish dominance. This makes vigilance essential for organizations everywhere. Without robust defenses, businesses face heightened risks of data theft, encryption, and reputational damage.
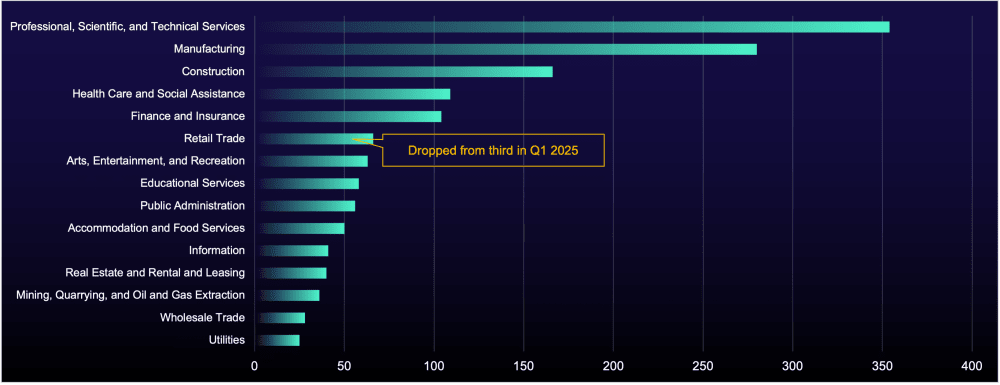
Figure 4: Number of compromised organizations listed on data-leak sites by sector, Q2 2025
Critical Vulnerabilities Drive Ransomware Success
Quarter after quarter, the most successful RaaS groups rely on mass exploitation of CVEs, often paired with automation to efficiently identify and compromise organizations. In Q2 2025, Qilin and Akira continued this trend, leveraging vulnerabilities at scale to drive their campaigns. Similarly, previous leaders like Clop (Q1 2025) and RansomHub (Q4 2024) have repeatedly demonstrated the effectiveness of exploiting unpatched vulnerabilities en masse to gain initial access.
This consistent reliance on vulnerabilities highlights the critical need for organizations to prioritize patch management, as unpatched and unmanaged vulnerabilities remain the most significant ransomware threat facing organizations. The table below outlines key CVEs exploited by RaaS groups in recent ransomware campaigns.
|
Group |
CVE |
|---|---|
|
Qilin |
CVE-2024-55591: FortiOS and FortiProxy authentication bypass vulnerability CVE-2024-21762: Fortinet FortiOS out-of-bound Write vulnerability in sslvpnd |
|
Akira |
CVE-2024-40766: SonicWall SonicOS remote code execution (RCE) vulnerability CVE-2023-20269: Cisco Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) software remote access VPN authentication bypass vulnerability |
|
Clop |
CVE-2024-50623: Cleo managed file transfer products CVE-2023-34362: Progress Software’s MoveIt Transfer |
|
RansomHub |
CVE-2024-57726, CVE-2024-57727, CVE-2024-57728: SimpleHelp RMM RCE vulnerability CVE-2023-27997: FortiOS RCE vulnerability CVE-2023-46604: Apache OpenWire RCE vulnerability |
The mass exploitation of CVEs by RaaS groups places organizations at significant risk, with 69% of organizations experiencing cyber attacks targeting unknown, unmanaged, or poorly understood assets. These hidden assets are often difficult—or even impossible—to patch quickly, leaving them exposed to critical vulnerabilities long enough for proof-of-concept (POC) exploits to be released. For instance, over a month after CVE-2024-21762—the vulnerability that propelled Qilin to top ransomware spot this quarter—was patched, security researchers found more than 150,000 Forniet FortiOS and FortiProxy devices still vulnerable.
Unpatched CVEs also give RaaS groups the opportunity to develop automated tools for exploitation, enabling faster attacks and significantly reducing the time defenders have to respond. With an average breakout time of just 48 minutes from initial access to lateral movement, organizations face immense pressure to detect and mitigate threats before they escalate.
ReliaQuest GreyMatter Discover provides a proactive solution by empowering organizations to move beyond observation and confidently resolve exposures. With built-in automation to eliminate silos and deliver real-time attack surface insights, GreyMatter Discover ensures continuous monitoring to identify and address gaps, vulnerabilities, and misconfigurations. By reducing the attack surface targeted by RaaS groups, organizations can take decisive steps to minimize risk and stay ahead of fast-paced threats.
Step Up Your Defenses Against Ransomware
ReliaQuest’s Approach
ReliaQuest GreyMatter leverages agentic AI to optimize security operations, empowering customers to accelerate threat detection, containment, investigation, and response. By automating security alerts and freeing security teams of Tier 1 and Tier 2 tasks, GreyMatter strengthens defenses and helps teams stay ahead of RaaS groups that are increasingly using AI and automation to scale their attacks.
Threat Intelligence: ReliaQuest continuously monitors the dynamic ransomware landscape to deliver actionable insights. This includes tracking emerging threat groups, updating threat profiles, monitoring data-leak site activity, and refining indicators of compromise (IOCs). These efforts equip organizations with the intelligence necessary to stay ahead of ransomware threats and strengthen defenses.
Detection Rules: ReliaQuest’s extensive library of detection rules is developed using the latest threat intelligence and proprietary research. These rules are tailored to defend against both known and evolving ransomware threats.
By combining GreyMatter Automated Response Playbooks with targeted detection capabilities, organizations can cut their mean time to contain (MTTC) threats from hours to as little as five minutes—essential for minimizing the impact of ransomware incidents. To enhance incident response effectiveness, we recommend integrating the following Automated Response Playbooks into security protocols for faster and more robust defenses:
-
Isolate Host: Disconnects compromised hosts from the network to prevent lateral movement, data exfiltration, and the spread of malware. This Playbook ensures threats are contained quickly, allowing investigation and remediation to proceed without further risk to the environment.
-
Disable User: Threat actors often exploit compromised user accounts to access sensitive systems or deploy ransomware. Disabling these accounts halts unauthorized activity, helping contain the attack and limit further damage.
-
Reset Passwords and Terminate Active Sessions: Stolen credentials are frequently used to escalate privileges and facilitate lateral movement. This Playbook revokes compromised credentials and ends active sessions, disrupting the attacker’s foothold and preventing further compromise.
Your Action Plan
This report offers critical insights into the latest, most pressing ransomware threats, but here are three actionable measures that organizations should prioritize without delay.
-
Prioritize Asset Discovery: Conduct a thorough audit of the network for visibility into all deployed technologies and software. Document and monitor configuration details to quickly identify vulnerable assets and respond before they’re exploited.
-
Build a Patch Management Framework: Develop a structured framework to guide patch management teams in triaging and prioritizing patch deployment for vulnerable devices. Externally facing devices, such as VPNs, should be patched first, as they’re the most likely to be targeted. Devices storing or providing access to critical information should follow. Swiftly addressing these vulnerabilities is crucial to preventing initial access attempts from RaaS groups.
-
Implement a Tiered Network Architecture: Design a network structure with independent layers logically separated by function. This segmentation separates critical systems, applications, and databases from routine user traffic, reducing the risk of lateral movement from compromised user accounts. It also helps defenders detect abnormal traffic on critical systems faster by filtering out the noise of day-to-day user operations.
Top Lessons and What’s Next
Q2 2025 marks a significant turning point in the ransomware landscape, with once-dominant groups declining as emerging players surged to prominence. The widespread exploitation of CVEs by RaaS groups continues to drive ransomware activity at scale, enabling these groups to compromise organizations at consistently high volumes quarter after quarter. As vulnerabilities and shifting group dynamics shape the ecosystem, the following predictions offer insight into what’s likely to come as 2025 progresses:
Automated vulnerability exploitation will continue to drive ransomware growth: The next major ransomware group in Q3 is likely to be the one quickest to exploit a significant initial access vulnerability. Leveraging public POC exploits and automated discovery tools, RaaS groups will identify and compromise vulnerable organizations with speed and precision, maximizing their impact. Organizations can mitigate this risk by prioritizing asset discovery to enable the rapid patching of initial access vulnerabilities.
DragonForce’s rise signals a shift in power dynamics: Emerging as a key contender, DragonForce is actively working to establish itself as a leading RaaS group through aggressive tactics like defacing rival data-leak sites, expanding its affiliate network, and compromising an increasing number of organizations. Based on its activity in early 2025, DragonForce is highly likely to secure a spot among the top five RaaS groups in the near future by targeting and attracting affiliates from groups like Lockbit and RansomHub. By coordinating large-scale campaigns, DragonForce has the potential to amplify its impact and further solidify its reputation as a dominant ransomware force.
[ad_2]
Source link

