[ad_1]
Since 2022, ransomware campaigns have grown increasingly adept at evading endpoint detection and response (EDR) systems.
Sophisticated malware known as EDR killers, specifically ‘AVKiller’, are now routinely deployed as the first stage in multi-pronged attacks, neutralizing security software to enable ransomware execution.
The emergence of AVKiller highlights a mature criminal marketplace: some tools are engineered by ransomware gangs, while others are purchased off underground forums and delivered via “packer-as-a-service” offerings like HeartCrypt, designed to obfuscate malware payloads.
AVKiller: Technical Analysis and Deployment
AVKiller is most commonly found disguised within legitimate applications, such as Beyond Compare’s Clipboard Compare tool, where attackers inject loader code and embed heavily protected malicious resources.
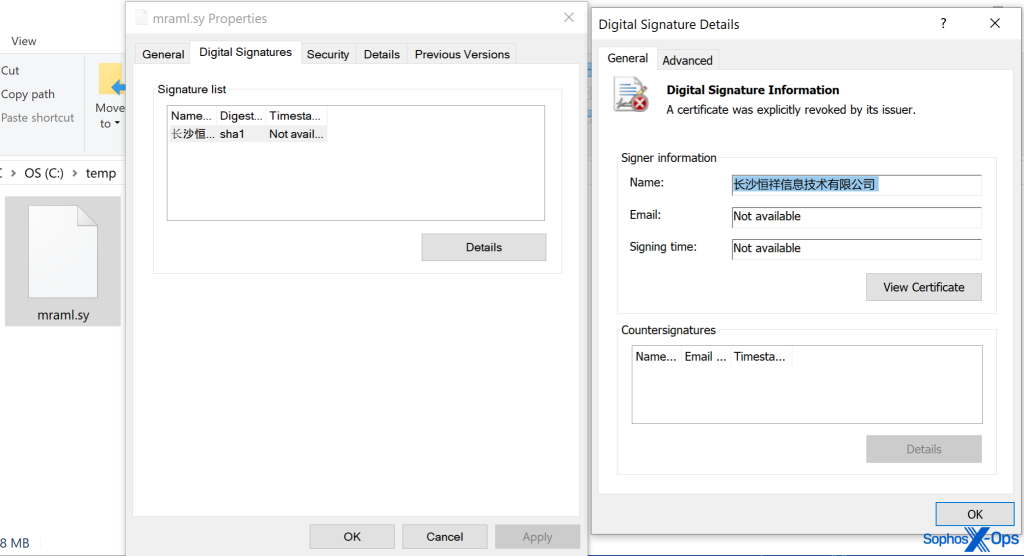
Upon execution, AVKiller searches for a specifically named driver file (e.g., mraml.sys), usually signed using a compromised digital certificate that is often expired and linked to companies that the Chinese government has abused.
If found, the driver is designed to escalate privileges and disable security defenses by forcibly terminating processes and services associated with leading EDR and AV products, including Sophos, Microsoft, SentinelOne, Bitdefender, Fortinet, Kaspersky, Trend Micro, and others.
Distinct versions of AVKiller demonstrate targeted adaptability: some variants aim at only a few vendors, while others carry a lengthy process kill-list (such as MsMpEng.exe, SophosHealth.exe, and SAVService.exe).
If the required driver is missing, AVKiller halts and returns an error, but often leaves behind a malicious service for persistence.
Coordination and Tool-Sharing Among Ransomware Actors
What makes the threat landscape more complex is evidence of tool and knowledge sharing among rival ransomware gangs.
Groups including RansomHub, Medusa, Qilin, Dragonforce, Inc., and others have all been documented deploying unique builds of the AVKiller in attacks, each sample individually packed with HeartCrypt “as-a-service.”
This reuse is not the result of a leaked binary, but of a shared approach where multiple actors buy builds, customize targets, and apply layered packers, highlighting a sophisticated, semi-cooperative cybercrime ecosystem.
In several cases, EDR killers like AVKiller are detected as the precursor to rapid ransomware deployment.
For instance, after AVKiller disables endpoint defenses, families such as RansomHub and Medusa swiftly execute file encryption, leaving behind ransom notes and unique file extensions.
Notably, some attacks leveraged zero-day exploits (like on SimpleHelp remote access), allowing rapid initial compromise even before EDR deployment could react.
The tactic of using packer-protected EDR killers as the initial salvo in ransomware attacks represents a dangerous evolution.
The apparent coordination and information sharing among competing ransomware crews amplify risk, making endpoint defense circumvention easier, faster, and more reliable.
Defenders must anticipate not only improved technical lures but also collaborative tool development across criminal enterprises further complicating an already challenging threat landscape.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates
[ad_2]
Source link

