[ad_1]
WatchGuard has released its latest Internet Security Report, covering malware, network, and endpoint threats spotted by its Threat Lab in the first quarter of 2025. The report shows a 171% jump in unique malware detections compared to the previous quarter, the highest number the Threat Lab has seen so far. Along with that, there was a large rise in zero-day malware, pointing to a growing trend in threats designed to slip past traditional security tools that depend on known patterns.
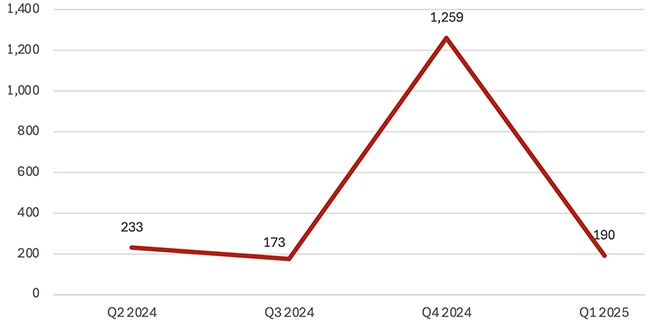
Ransomware detections by quarter (Source: WatchGuard)
Malware increase
One key takeaway is a 323% increase in malware caught by WatchGuard’s machine learning-based detection system. Gateway AntiVirus detections rose 30%, and malware using encrypted TLS channels went up by 11 percentage points. These trends suggest attackers are increasingly hiding their activity through encryption and evasion techniques, making it harder for conventional tools to catch them.
On endpoints, the Threat Lab found a 712% spike in new malware threats. That’s a major shift after three quarters of steady decline. The most common malware at the endpoint was an LSASS dumper, a tool used to steal credentials by targeting a key Windows process involved in login authentication and password management. Attackers often use this method to gain deeper access to systems by working around standard user controls.
“The latest findings in the Q1 2025 Internet Security Report seem to support a larger cybersecurity industry trend: the AI war is here. Attackers are increasingly relying on social engineering and phishing techniques supercharged by AI tools,” said Corey Nachreiner, CSO, WatchGuard Technologies. “Attackers now have the capabilities to launch highly targeted campaigns at scale using automated pipelines, emphasizing the need for organizations to adopt precise, and powerful security measures to stay ahead of the advancements in AI and the evolving cyber risks.”
Additional key findings
Ransomware declined 85% from the previous quarter, although the second most detected malware threat was a ransomware payload: Termite ransomware. This supports the industry trend of a decrease in crypto ransomware, the malware that encrypts files. Attackers are now shifting toward data theft instead of encryption, as improvements in data backups and recovery have been made.
Scripts, files derived from or using a scripting programming language, are down by about half this quarter, the lowest they’ve ever been. Historically, the Threat Lab has observed scripts as the number one attack vector for malware detection on endpoints. Other Living off The Land (LoTL) techniques, such as Windows, saw the highest increase from quarter to quarter at 18%, filling the gap left by scripts.
The top malware detected over encrypted connections was Trojan.Agent.FZPI, a new malicious HTML file that merges legitimate-looking files with encrypted communication. This threat combines several techniques that threat actors have employed over the last few years into one super phishing attachment. Organizations must implement TLS inspection, behavioral analysis, and endpoint protection to detect and neutralize this threat.
In Q1 2025, the most widespread malware was Application.Cashback.B.0835E4A4, a newly identified threat and among the most prevalent malware families ever recorded, with the highest impact in Chile at 76% and Ireland in second at 65%. The prevalence of Application.Cashback variants signal the need for region-specific defenses to address these sophisticated threats.
The unique number of network signatures triggered, or known attacks detected on networks, decreased by 16% from last quarter as attackers focused on a narrower set of exploits. The network attack landscape highlights that while new exploits do emerge, attackers continue to heavily exploit unpatched legacy vulnerabilities at scale, forcing organizations to address both fronts simultaneously.
Malware threats are continuing to emerge via email rather than the web, suggesting that threat actors are targeting users with traditional phishing techniques, as AI makes it easier to compose believable spear phishing messages. However, AI and machine learning-based tools are detecting significantly more threats at the network and endpoint perimeter in Q1 2025.
[ad_2]

