[ad_1]
Security researchers have discovered a new ransomware variant that exploits previously known SharePoint vulnerabilities. The 4L4MD4R ransomware, based on open-source code, spreads via a failed PowerShell attack and demands a ransom of 0.005 BTC.
This is according to research by Palo Alto Networks. A failed exploitation attempt on July 27, 2025, led to the discovery of the 4L4MD4R ransomware. Palo Alto identified a loader designed to download and execute ransomware from a remote server.
The attackers attempted to bypass security mechanisms via an encrypted PowerShell command by disabling real-time monitoring and ignoring certificate validation. This tactic is commonly seen in modern cyberattacks.
Technical analysis of the payload
Further investigation reveals that the 4L4MD4R ransomware is written in GoLang and compressed with UPX. The program works in several steps: first, it decrypts an AES-encrypted payload in memory, then it allocates memory to load the decrypted PE file, and finally, it creates a new thread for execution.
This malware is based on the open-source Mauri870 code, which explains why it generates two specific files on the desktop: DECRYPTION_INSTRUCTIONS.html with the ransom note and ENCRYPTED_LIST.html with an overview of encrypted files. The message looks like this.
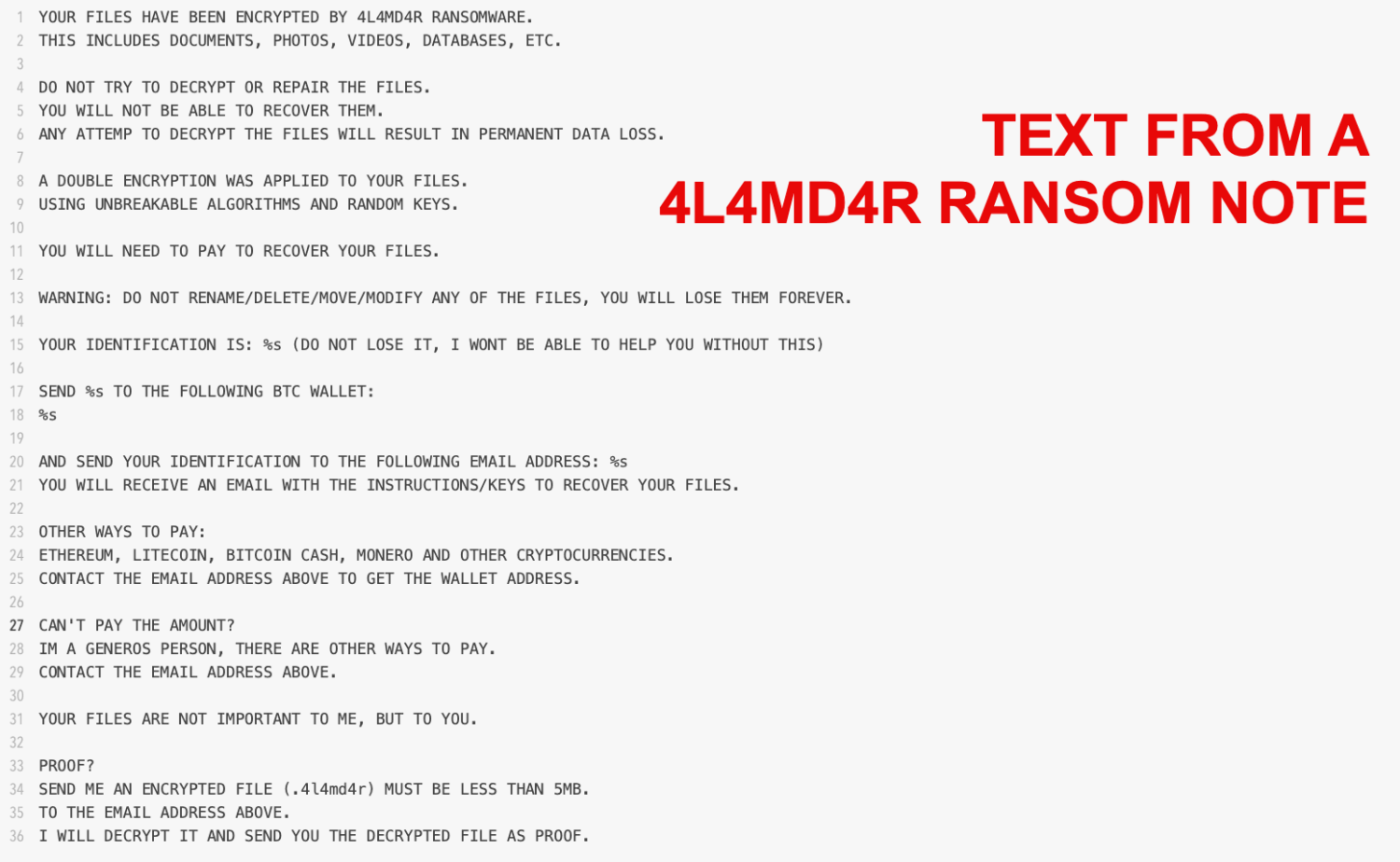
Victims are asked to pay 0.005 BTC, a relatively low amount compared to other ransomware attacks. For this payment, they receive a contact email address (m4_cruise@proton[.]me) and a Bitcoin wallet address. The modest ransom demand suggests that the attackers are aiming for a high volume of infections rather than large payments per victim.
The ransomware is configured to communicate with a C2 server via POST requests. These requests send encrypted JSON objects containing information about the infected system.
This infrastructure shows similarities to previous attacks. As we saw with the recent SharePoint exploits, cybercriminals often reuse proven techniques for different campaigns.
[ad_2]
Source link
