[ad_1]
Researchers at Infoblox have released new findings on VexTrio, a large criminal enterprise that uses a set of traffic distribution systems (TDSs), lookalike domains and registered domain generation algorithms (RDGAs) to deliver malware, scams and illegal content.
The researchers have been able to link nine individuals, shell companies and a sprawling infrastructure to the global ad fraud and scam operation.
The security firm is expected to share an 80-page report detailing its new findings during Black Hat USA, in Las Vegas, on August 6.
Understanding the VexTrio Cybercrime-Enabling Operation
VexTrio, also known as Vextrio Viper, is a cyber fraud network that has been active since at least 2017. It was discovered by Infoblox in February 2022.
VexTrio operators are known to leverage compromised websites, particularly those running WordPress, to inject malicious scripts that redirect users to harmful content. They act as a middlemen connecting threat actors with infrastructure providers, enabling a wide range of cybercrime activities.
They typically use TDS to filter and redirect web traffic based on specific criteria, such as geolocation, device type or user behavior. These systems often rely on compromised websites and malicious advertisements to funnel unsuspecting users into their malicious ecosystems.
VexTrio employs TDS to ensure that victims are directed to the most relevant malicious payload, whether it’s malware, scams or exploit kits.
Additionally, VexTrio relies heavily on Domain Name System (DNS) manipulation to facilitate its operations. By controlling or compromising DNS records, the group can redirect victims to malicious servers without their knowledge.
Some of these sophisticated DNS manipulation techniques employed by VexTrio include:
- Fast-flux DNS techniques, rapidly changing the IP addresses associated with their domains to evade detection and takedown efforts
- DNS tunnelling, a technique that encodes data within DNS queries (e.g., requests to malicious domains) to bypass security controls, exfiltrate data, or establish covert command-and-control (C2) communication
- Domain generation algorithms (DGAs) to maintain communication with infected systems while staying under the radar
VexTrio’s primary content delivery network domain is a top 10,000 domain in global popularity, as measured by both Tranco and Infoblox.
New Revelations on VexTrio’s Origins, Operators and Infrastructure
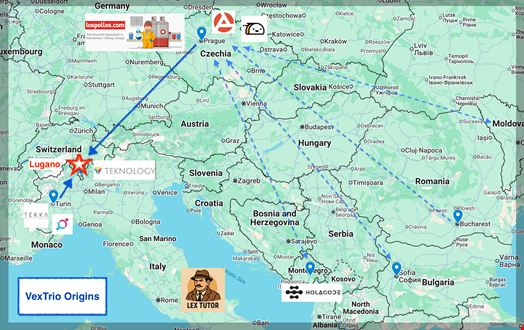
The Infoblox report uncovered for the first time that VexTrio’s owners operate dozens of businesses across Europe in several industries, including several in affiliate marketing.
The businesses all originated from two distinct networks:
- An Italian group (with affiliates like Tekka Group or Crownstone LLC) with a history of spam and fake dating sites
- An Eastern European group (with affiliates like Los Pollos, AdsPro) with deep technical expertise and infrastructure capabilities.
These two networks allegedly merged in 2020 into a multinational criminal enterprise, comprising nearly 100 companies and brands across industries, including adtech, mobile apps, energy, construction and even ski resorts.
AdsPro Group (also referred to as AdsPro Digital and AdsPro Global) is a multinational shell company network responsible for the creation of the VexTrio TDS which is used for redirecting massive volumes of internet traffic into scams.
“While posing as a legitimate adtech firm, operating several brands under the guise of affiliate marketing, it is responsible for orchestrating many types of fraud,” the Infoblox report reads.
Additionally, the new report shed light on the full extent of VexTrio’s current activities. These include:
- Operating its own scams, including fake dating and porn sites, fake antivirus and adblock apps, sweepstakes and prize scams, subscription fraud via push notifications and fake e-commerce and crypto investment platforms
- Developing and distributing malicious apps under names like HolaCode, LocoMind, Hugmi, Klover Group and AlphaScale Media
- Running payment processors (e.g., Pay Salsa) and email validation services (e.g., DataSnap)
- Controlling both the publishing and advertising sides of affiliate networks via websites like Los Pollos, TacoLoco and Adtrafico
![The Los Pollos website in May 2024, as recorded by archive.org, claimed two billion unique users. Several of the testimonial brands listed on the site, including Teknology, tacolo[.]co, and Adtrafico are part of VexTrio. Source: Infoblox](https://nationalcybersecurity.com/wp-content/uploads/2025/08/b9c59ed7-d278-4080-9466-573322259663.png)
Infoblox also revealed that, despite the wide range of malicious activities, VexTrio’s global operation runs on fewer than 250 virtual machines across a few hosting providers.
Finally, the Infoblox report exposed for the first time some individuals linked to the VexTrio network – namely Giulio Cerutti, Igor Voronin, Andrew Kunitsa, Dzmitry Laptsevich, Kroum Vassilev, Matteo Costa, Marco Rufa and Giulio Lingua.
These individuals, connected to dozens of VexTrio-affiliated entities across Switzerland, Czechia, Bulgaria, Moldova and Canada, were identified by analyzing corporate transparency records, trademarks, social media activity and more publicly available documents.
[ad_2]
Source link
Click Here For The Original Source.

