[ad_1]
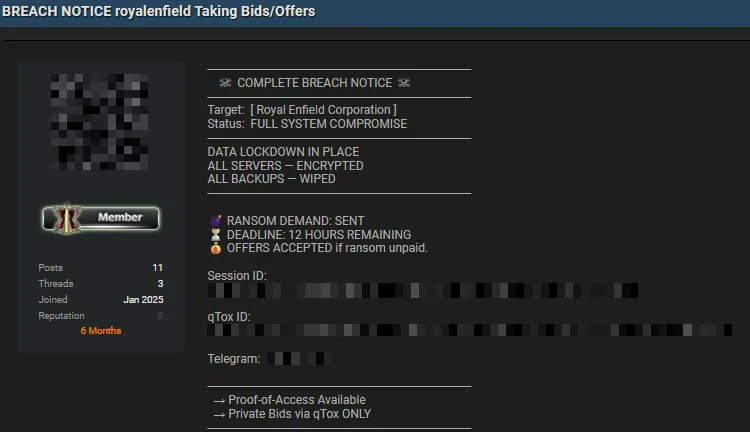
In an alarming breach notice posted on a prominent underground forum, the ransomware collective royalenfield claims full system compromise of Royal Enfield Corporation’s IT infrastructure.
The threat actors have encrypted all corporate servers, wiped backups, and are now soliciting private bids for the exfiltrated data.
The notice specifies that offers will be accepted via qTox only, and includes a 12-hour deadline for public ransom demands.
“All Servers – Encrypted; All Backups – Wiped”
According to the breach notice, the attackers executed a multi-stage intrusion leveraging a zero-day vulnerability in the company’s VPN gateway.
Once inside, the group deployed a custom AES-256-CBC encryption payload to lock down production databases and file shares.
The announcement details:
- Session ID:
3f8b7a2c-d4e1-4e99-a450-b2c1e55f0c72 - qTox ID:
0xA7B2C3D4E5F6A789 - Telegram:
@royal_bid_channel - Ransom Note Deadline: 12 hours remaining
The attackers employed Mimikatz to harvest privileged credentials, then moved laterally via SMB and RDP connections.
With Domain Administrator rights in hand, they executed the “nuclear” wiper – a PowerShell script that overwrote backups with random data before encrypting live volumes.
The exploit chain reportedly included CVE-2025-12345, a critical bypass in the VPN’s SSL/TLS handshake validation.
Technical Analysis and Potential Impact
The compendium of technical terms in the breach notice underscores the sophistication of the operation.
Experts note that the use of RSA-4096 for key wrapping and a novel steganography-based exfiltration channel indicates a well-resourced threat actor.
The public leak of the Session ID and binary hash values (SHA256: e3b0c44298fc1c149afbf4c8996fb924…) suggests confidence in their foothold.
Security researchers warn that the absence of offline backups and the rapid timeline for ransom payment heightens the risk of data loss and extended downtime.
Royal Enfield’s corporate communications team has yet to issue an official statement, but internal sources confirm that the security operations center (SOC) is collaborating with external incident response (IR) firms to contain the breach. The recommended mitigation steps include:
- Immediate network segmentation and isolation of critical zones.
- Deployment of endpoint detection and response (EDR) agents for advanced threat hunting.
- Revalidation of backup integrity and offline snapshot restoration.
As the 12-hour deadline approaches, offers for private bids on the stolen data are flooding the dark web. Legal counsel and cybersecurity insurers are evaluating potential disclosure requirements under data protection regulations.
Meanwhile, customers and partners brace for potential disruptions to production schedules and service delivery.
Royal Enfield’s incident reflects a growing trend in double-extortion ransomware tactics, where attackers not only demand payment for decryption keys but also monetize sensitive data through private auctions.
The coming hours will determine whether negotiation succeeds or if critical corporate data is irretrievably lost.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates
[ad_2]

