[ad_1]
Cybersecurity experts are sounding the alarm about a sophisticated malware campaign that leverages malicious advertisements targeting system administrators through weaponized PuTTY downloads.
This emerging threat represents a significant shift in attack vectors, with malicious advertisements now surpassing traditional phishing methods as the primary delivery mechanism for malware infections.
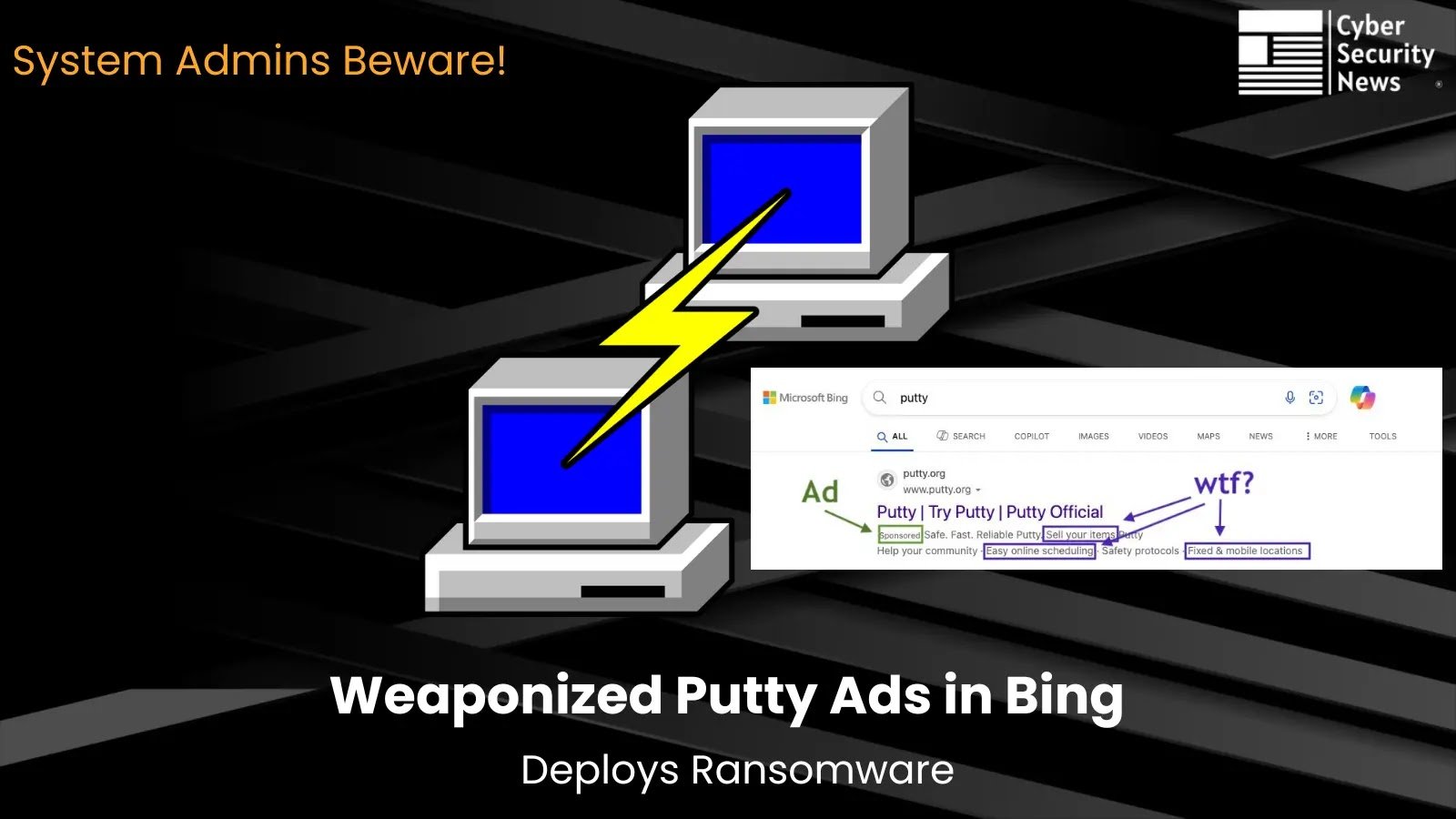
The current campaign uncovered by ExpelSecurity specifically targets users searching for PuTTY, the widely used SSH and telnet client essential for system administration tasks.
According to threat intelligence analysts at Expel, attackers have strategically positioned malicious advertisements at the top of Bing search results, displaying what appears to be the legitimate PuTTY domain while secretly redirecting visitors to attacker-controlled websites.

This deceptive technique exploits the trust that system administrators place in familiar tools and search engine results.
When unsuspecting users click on these fraudulent advertisements, they unknowingly download compromised software that appears legitimate but contains dangerous payloads.
Sophisticated Attack Chain Leads to Ransomware
Once downloaded and executed, the malicious PuTTY installer deploys Oyster/Broomstick, a remote access tool with established connections to the notorious Rhysida ransomware group.
This multi-stage attack demonstrates the increasing sophistication of cybercriminal operations, combining social engineering tactics with advanced technical capabilities.
The malware establishes persistence on infected systems by creating a scheduled task named “Security Updater” that operates from the user’s AppData directory.
This naming convention cleverly mimics legitimate system maintenance processes, making detection more challenging for both users and security software.
The financial resources behind this campaign highlight the professionalization of cybercrime.
Threat researchers report that attackers have invested several thousand dollars in recent weeks to purchase legitimate code-signing certificates, adding an additional layer of apparent authenticity to their malicious software.
These certificates, obtained from entities including “GALVIN & ASSOCIATES LLC,” “Shanxi Jiusheng Tongtai Trading Co., Ltd.,” and “THE COMB REIVERS LIMITED,” help the malware bypass security controls that typically flag unsigned executables.
Technical Indicators
ExpelSecurity shared security indicators for network defenders.
The fake PuTTY installer IoCs
- Fake PuTTY MD5: f42dae36a47882391da920ce56f497b8, Signed by “GALVIN & ASSOCIATES LLC”
- Persistence: MD5: 18b77f4f10e0a17341fdfb2371e88fb2, Signed by “Shanxi Jiusheng Tongtai Trading Co., Ltd.”
- Persistence: MD5: 90f0412fa7e5f3cd5f84cb80f951d539, Signed by “THE COMB REIVERS LIMITED”
- Domains: fmwyd[.]com, put[.]mxcue[.]com, mvmmoving[.]com, putty[.]run
Cybersecurity experts recommend implementing ad blockers as a first line of defense against malicious advertisements.
Organizations should also enhance their detection capabilities to quickly identify and respond to suspicious activities, particularly focusing on scheduled tasks and processes running from user directories.
System administrators should exclusively download software from official vendor websites and verify digital signatures before installation.
Power up early threat detection, escalation, and mitigation with ANY.RUN’s Threat Intelligence Lookup. Get 50 trial searches.
[ad_2]
Source link


.png
)