[ad_1]

Redazione RHC : 5 August 2025 15:37
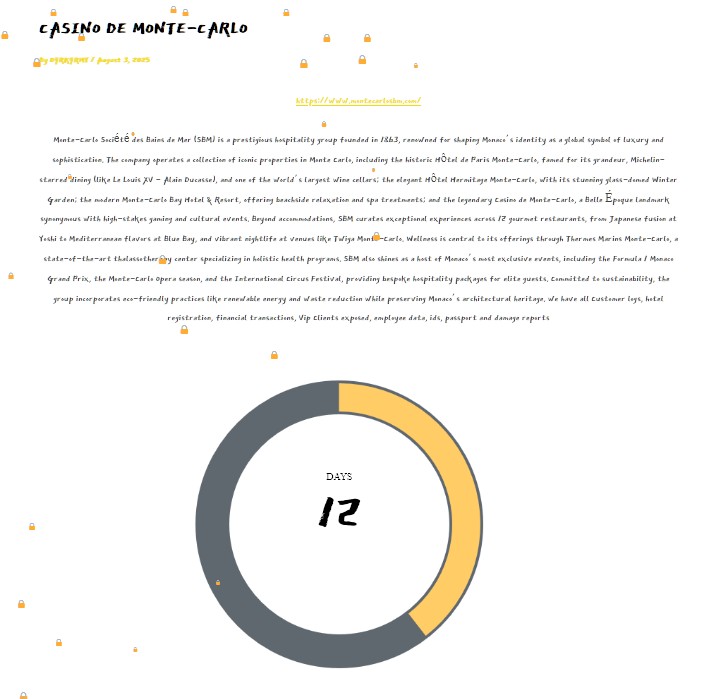
The criminal organization known as D4rk4rmy has claimed responsibility for the cyber attack against the Monte-Carlo Société des Bains de Mer (SBM) on its Data Leak Site (DLS). The site contains a post stating that an update will be available in 12 days.
Founded in 1863, SBM is the leading operator in the luxury hotel sector in the Principality of Monaco.
Among the most renowned properties managed by the company are the Hôtel de Paris and the Monte Carlo Casino, which play a key role in shaping the Principality’s international image of refinement and prestige.
Attackers report the theft of sensitive customer data and internal company records, posing a serious threat to the brand’s global reputation, guest privacy, and business continuity.
Disclaimer: This report includes screenshots and/or text from publicly available sources. The information provided is for threat intelligence and cybersecurity awareness purposes only. Red Hot Cyber condemns any unauthorized access, improper disclosure, or illicit use of such data. At this time, it is not possible to independently verify the authenticity of the reported information, as the organization involved has not yet released an official statement on its website. Accordingly, this article should be considered for informational and intelligence purposes only.

As cybercriminals increasingly target high-profile sectors, this incident serves as a stark reminder: not even the most exclusive establishments are immune. The potential impact could impact partnerships, customer trust, and the very identity that defines the Monegasque luxury sector.
Serving an elite clientele, SBM offers gaming, hotel, fine dining, and entertainment services.The Monegasque government holds a majority stake in the company. The D4rk4rmy cyber gang has added Monte-Carlo Société des Bains de Mer (SBM) to the list of victims on its Tor dark web leak site.
D4rk4rmy is a hacker group primarily known for ransomware attacks and data breaches observed in 2025. The group has They target companies across various industries, including logistics, technology, and hospitality. They often publish stolen data on data leak sites to extort money from victims.
Operating as Ransomware-as-a-Service (RaaS), they offer paid hacking services, claiming not to target hospitals and critical infrastructure. Open-source intelligence links D4rk4rmy to active communities on forums, Telegram, and Discord, with alleged origins in white/grey hat circles that evolved into criminal activities.
While some claims may lack evidence of genuine malware, recent operations demonstrate real exfiltrations and threats.
What is ransomware as a service (RaaS)
Ransomware is a type of malware that is injected into an organization to encrypt data and render systems unavailable. Once the data is encrypted, the criminals demand a ransom from the victim, to be paid in cryptocurrency, in order to decrypt it.
If the victim refuses to pay the ransom, the criminals will proceed with double extortion, threatening to publish sensitive data previously exfiltrated from the victim’s IT infrastructure.
To better understand how criminal organizations operate within the ransomware-as-a-service (RaaS) business, we refer you to these articles:
How to protect yourself from ransomware
Ransomware infections can be devastating for an organization, and data recovery can be a difficult and laborious process that requires highly specialized operators for reliable recovery. Even without a data backup, recovery has often been unsuccessful.
In fact, users and administrators are advised to adopt preventative security measures to protect their networks from ransomware infections. They are listed in order of complexity:
- Train staff through awareness courses;
- Use a data backup and recovery plan for all critical information. Perform and test regular backups to limit the impact of data or system loss and speed up the recovery process. Keep in mind that network-connected backups can also be affected by ransomware.Critical backups should be isolated from the network for optimal protection.
- Keep your operating system and all software updated with the latest patches. Vulnerable applications and operating systems are the target of most attacks. Ensuring these are patched with the latest updates significantly reduces the number of exploitable entry points available to an attacker.
- Keep your antivirus software up to date and scan all software downloaded from the Internet before running it.
- Limit users’ ability (permissions) to install and run unwanted software applications and apply the principle of “least privilege” to all systems and services. Restricting these privileges can prevent malware from running or limit its ability to spread across the network.
- Avoid Enable macros from email attachments. If a user opens the attachment and enables macros, the embedded code will run malware on the computer.
- Do not follow unsolicited web links in emails.
- Never expose Remote Desktop Protocol (RDP) connections directly to the Internet. If internet access is required, everything must be mediated by a VPN;
- Implement Intrusion Prevention Systems (IPS) and Web Application Firewalls (WAF) as perimeter protection around internet-facing services.
- Implement a natively automated XDR security platform, possibly supported by a 24/7 MDR service, enabling complete and effective protection and visibility across endpoints, users, networks, and applications, regardless of resources, team size, or skill level, while also providing detection, correlation, analysis, and response. Automated.
Both individuals and organizations are discouraged from paying the ransom, as even after payment, cyber gangs may not release the decryption key, or recovery operations may be subject to errors and inconsistencies.
Cybersecurity is a serious matter and can profoundly undermine a company’s business today.
Today, we need to immediately change our mindset and think of cybersecurity as an integral part of business, not just after a cybersecurity incident.
 Redazione
RedazioneThe editorial team of Red Hot Cyber consists of a group of individuals and anonymous sources who actively collaborate to provide early information and news on cybersecurity and computing in general.
[ad_2]
Source link

