[ad_1]
Online criminal forums, both on the public internet and on the “dark web” of Tor .onion sites, are a rich resource for threat intelligence researchers. The Sophos Counter Threat Unit (CTU) have a team of darkweb researchers collecting intelligence and interacting with darkweb forums, but combing through these posts is a time-consuming and resource-intensive task, and it’s always possible that things are missed.
As we strive to make better use of AI and data analysis, Sophos AI researcher Francois Labreche, working with Estelle Ruellan of Flare and the Université de Montréal and Masarah Paquet-Clouston of the Université de Montréal, set out to see if they could approach the problem of identifying key actors on the dark web in a more automated way. Their work, originally presented at the 2024 APWG Symposium on Electronic Crime Research, has recently been published as a paper.
The approach
The research team combined a modification of a framework developed by criminologists Martin Bouchard and Holly Nguyen to separate professional criminals from amateurs in an analysis of the criminal cannabis industry with social-network analysis. With this, they were able to connect accounts posting in forums to exploits of recent Common Vulnerabilities and Exposures (CVEs), either based upon the naming of the CVE or by matching the post to the CVEs’ corresponding Common Attack Pattern Enumerations and Classifications (CAPECs) defined by MITRE.
Using the Flare threat research search engine, they gathered 11,558 posts by 4,441 individuals from between January 2015 and July 2023 on 124 different e-crime forums. The posts mentioned 6,232 different CVEs. The researchers used the data to create a bimodal social network that connected CAPECs to individual actors based on the contents of the actors’ posts. In this initial stage, they focused the dataset down to eliminate, for instance, CVEs that have no assigned CAPECs, and overly general attack methods that many threat actors use (and the posters who only discussed those general-purpose CVEs). Filtering such as this ultimately whittled the dataset down to 2,321 actors and 263 CAPECs.
The research team then used the Leiden community detection algorithm to cluster the actors into communities (“Communities of Interest”) with a shared interest in particular attack patterns. At this stage, eight communities stood out as relatively distinct. On average, individual actors were connected to 13 different CAPECs, while CAPECs were linked with 118 actors.
Figure 1: Bimodal actor-CAPEC networks, colored according to Communities of Interest; the CAPECs are shown in red for clarity
Pinpointing the key actors
Next, key actors were identified based on the expertise they exhibited in each community. Three factors were used to measure level of expertise:
1) Skill Level: This was based on the measurement of skill required to use a CAPEC, as assessed by MITRE: ‘Low,’ ‘Medium,’ or ‘High,’ using the highest skill level among all the scenarios related to the attack pattern, to prevent underestimating actors’ skills. This was done for every CAPEC associated with the actor. To establish a representative skill level, the researchers used the 70th percentile value from each actor’s list of CAPECs and their associated skill levels. (For example, if John Doe discussed 8 CVEs that MITRE maps to 10 CAPECs – 5 rated High by MITRE, 4 rated Medium, and one rated Low – his representative skill level would be considered High.) Choosing this percentile value ensured that only actors with over 30 percent of their values equivalent to “High” would be classified as actually highly skilled.
OVERALL DISTRIBUTION OF SKILL LEVEL VALUES
| Skill Level Value | CAPECs | % of Skill Level Values among all values in actors’ list |
| Low | 118 (44.87%) | 57.71% |
| Medium | 66 (25.09%) | 24.14% |
| High | 79 (30.04%) | 18.14% |
SKILL LEVEL VALUES PROPORTION STATISTICS
| Skill Level Value | Average proportion of members in the list of actors |
Median | 75th percentile | Std |
| High | 29.07% | 23.08% | 50.00% | 30.76% |
| Medium | 36.12% | 30.77% | 50.00% | 32.41% |
| Low | 33.74% | 33.33% | 66.66% | 31.72% |
Figure 2: A breakdown of the skill-level assessments of the actors analyzed in the research
2) Commitment Level: This was quantified by the proportion of ‘in-interest’ posts (posts relating to a set of related CAPECs based on similar Communities of Interest) relative to an actor’s total posts. Actors who had three or fewer posts were disregarded, reducing the set to be evaluated to 359 actors.
3) Activity Rate: The researchers added this element to the Bouchard/Nguyen framework to quantify each actor’s activity level in forums. It was measured by dividing the number of posts with a CVE and corresponding CAPEC by the number of days of the actor’s activity on the relevant forums. Activity rate actually turns out to be inverse to the skill level at which threat actors operate. More highly skilled actors have been on the forums for a long time, so their relative activity rate is much lower, despite having significant numbers of posts.
DESCRIPTIVE STATISTICS OF SAMPLE
|
Figure 3: A breakdown of the skill, commitment, and activity rate scores for the sample group
As shown above, the sample for the identification of key actors consisted of 359 actors. The average actor had 36.68% of posts committed to their Community of Interest and had a skill level of 2.19 (‘Medium’). The average activity rate was 0.72.
COMMUNITIES OF INTEREST (COI) OVERVIEW
|
Figure 4. The relative scores of actors grouped into each Community of Interest
14 needles in a haystack
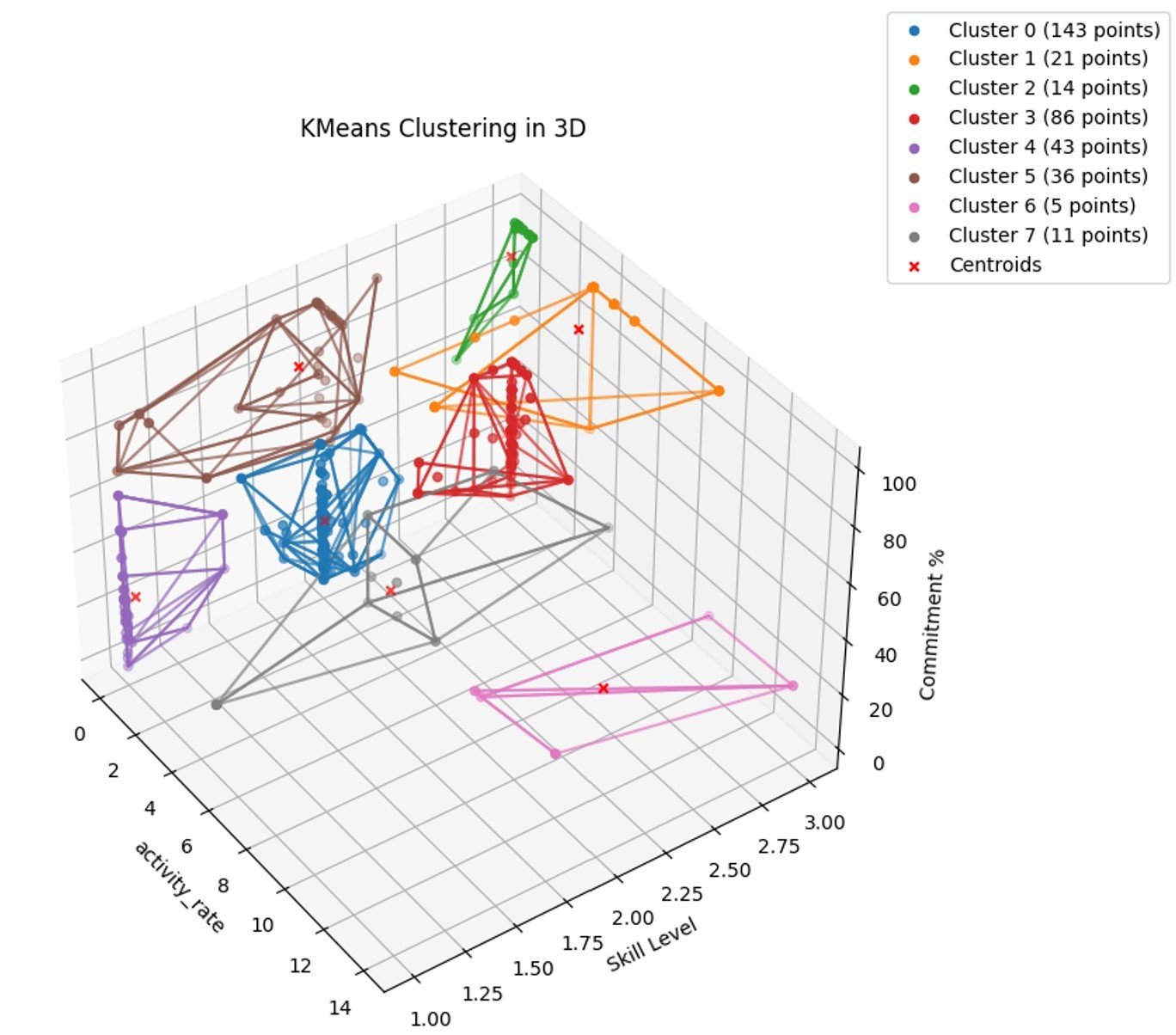
Finally, to identify the truly key actors — those with high enough skill level and commitment and activity rate to identify them as experts in their domains — the researchers used the K-means clustering algorithm. Using the three measurements created for each actor’s relationship with CAPECs, the 359 actors were clustered into eight clusters with similar levels of all three measurements.
OVERVIEW OF CLUSTERS
|
Figure 5: An analysis of the eight clusters with scoring based on the methodology from the framework developed from the work of criminologists Martin Bouchard and Holly Nguyen; as described above, activity rate was added as a modification to that framework. Note the low number of truly professional actors, even among the dataset of 359
One cluster of 14 actors was graded as “Professionals” — key individuals; the best in their field; with high skill and commitment and low activity rate, again because of the length of their involvement with the forums (an average of 159 days) and a post rate that averaged about one post every 3-4 days. They focused on very specific communities of interest and did not post much beyond them, with a commitment level of 90.37%. There are inherent limitations to the analysis approach in this research— primarily because of the reliance on MITRE’s CAPEC and CVE mapping and the skill levels assigned by MITRE.
Conclusion
The research process includes defining problems and seeing how various structured approaches might lead to greater insight. Derivatives of the approach described in this research could be used by threat intelligence teams to develop a less biased approach to identifying e-crime masterminds, and Sophos CTU will now start looking at the outputs of this data to see if it can shape or improve our existing human-led research in this area.
[ad_2]
Source link
Click Here For The Original Source.