[ad_1]
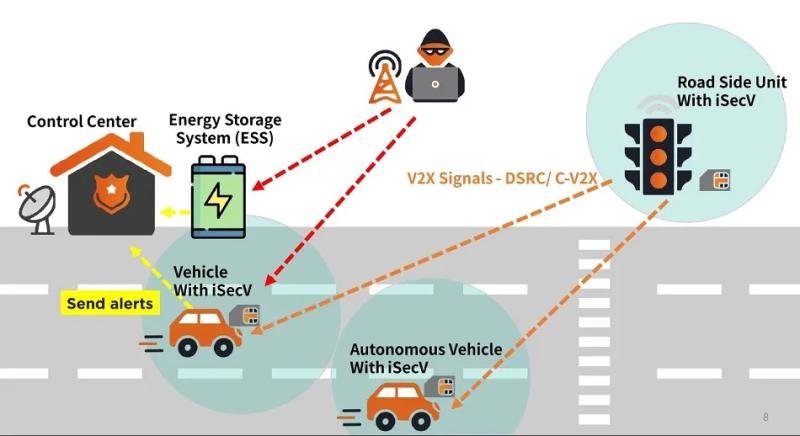
V2X (Vehicle-To-Everything) Cybersecurity
The global V2X (Vehicle-To-Everything) Cybersecurity market is expected to be valued at approximately USD 975 million in 2024, and it is projected to reach around USD 4.12 billion by 2033, growing at a compound annual growth rate (CAGR) of 17.5% from 2025 to 2033.
V2X (Vehicle-To-Everything) Cybersecurity Market Overview:
The V2X Cybersecurity market is expanding rapidly, fueled by the increasing integration of connected vehicle technologies and the growing need to protect vehicle communication systems from cyber threats. V2X enables vehicles to communicate with each other, infrastructure, pedestrians, and networks, creating a critical need for robust cybersecurity frameworks to ensure data integrity, privacy, and safety. As autonomous and electric vehicles gain momentum, the risk of cyberattacks targeting vehicle software and communication protocols also rises. Governments and automotive OEMs are investing heavily in V2X infrastructure and secure communication standards. Moreover, the push toward intelligent transportation systems and smart cities is further accelerating the adoption of advanced V2X cybersecurity solutions globally.
Request a sample copy of this report at: https://www.omrglobal.com/request-sample/v2x-cybersecurity-market
Advantages of requesting a Sample Copy of the Report:
1) To understand how our report can bring a difference to your business strategy
2) To understand the analysis and growth rate in your region
3) Graphical introduction of global as well as the regional analysis
4) Know the top key players in the market with their revenue analysis
5) SWOT analysis, PEST analysis, and Porter’s five force analysis
The report further explores the key business players along with their in-depth profiling
Qualcomm Technologies Inc., Harman International, Continental AG, Autotalks Ltd., Robert Bosch GmbH, Infineon Technologies AG, Cisco Systems Inc., NXP Semiconductors, ESCRYPT GmbH (a Bosch company), and Argus Cyber Security Ltd.
V2X (Vehicle-To-Everything) Cybersecurity Market Segments:
By Communication Type:
• Vehicle-to-Vehicle (V2V)
• Vehicle-to-Infrastructure (V2I)
• Vehicle-to-Network (V2N)
• Vehicle-to-Pedestrian (V2P)
• Vehicle-to-Grid (V2G)
• Vehicle-to-Device (V2D)
By Security Type:
• Network Security
• Application Security
• Endpoint Security
• Cloud Security
• Wireless Security
By Offering:
• Hardware
• Software
• Services
By Vehicle Type:
• Passenger Vehicles
• Commercial Vehicles
• Electric Vehicles (EVs)
By End User:
• Automotive OEMs
• Aftermarket
• Government & Transportation Authorities
Report Drivers & Trends Analysis:
The report also discusses the factors driving and restraining market growth, as well as their specific impact on demand over the forecast period. Also highlighted in this report are growth factors, developments, trends, challenges, limitations, and growth opportunities. This section highlights emerging V2X (Vehicle-To-Everything) Cybersecurity Market trends and changing dynamics. Furthermore, the study provides a forward-looking perspective on various factors that are expected to boost the market’s overall growth.
Competitive Landscape Analysis:
In any market research analysis, the main field is competition. This section of the report provides a competitive scenario and portfolio of the V2X (Vehicle-To-Everything) Cybersecurity Market’s key players. Major and emerging market players are closely examined in terms of market share, gross margin, product portfolio, production, revenue, sales growth, and other significant factors. Furthermore, this information will assist players in studying critical strategies employed by market leaders in order to plan counterstrategies to gain a competitive advantage in the market.
Regional Outlook:
The following section of the report offers valuable insights into different regions and the key players operating within each of them. To assess the growth of a specific region or country, economic, social, environmental, technological, and political factors have been carefully considered. The section also provides readers with revenue and sales data for each region and country, gathered through comprehensive research. This information is intended to assist readers in determining the potential value of an investment in a particular region.
» North America (U.S., Canada, Mexico)
» Europe (Germany, U.K., France, Italy, Russia, Spain, Rest of Europe)
» Asia-Pacific (China, India, Japan, Singapore, Australia, New Zealand, Rest of APAC)
» South America (Brazil, Argentina, Rest of SA)
» Middle East & Africa (Turkey, Saudi Arabia, Iran, UAE, Africa, Rest of MEA)
If you have any special requirements, Request customization: https://www.omrglobal.com/report-customization/v2x-cybersecurity-market
Key Benefits for Stakeholders:
⏩ The study represents a quantitative analysis of the present V2X (Vehicle-To-Everything) Cybersecurity Market trends, estimations, and dynamics of the market size from 2025 to 2032 to determine the most promising opportunities.
⏩ Porter’s five forces study emphasizes the importance of buyers and suppliers in assisting stakeholders to make profitable business decisions and expand their supplier-buyer network.
⏩ In-depth analysis, as well as the market size and segmentation, help you identify current V2X (Vehicle-To-Everything) Cybersecurity Market opportunities.
⏩ The largest countries in each region are mapped according to their revenue contribution to the market.
⏩ The V2X (Vehicle-To-Everything) Cybersecurity Market research report gives a thorough analysis of the current status of the V2X (Vehicle-To-Everything) Cybersecurity Market’s major players.
Key questions answered in the report:
➧ What will the market development pace of the V2X (Vehicle-To-Everything) Cybersecurity Market?
➧ What are the key factors driving the V2X (Vehicle-To-Everything) Cybersecurity Market?
➧ Who are the key manufacturers in the market space?
➧ What are the market openings, market hazards,s and market outline of the V2X (Vehicle-To-Everything) Cybersecurity Market?
➧ What are the sales, revenue, and price analysis of the top manufacturers of the V2X (Vehicle-To-Everything) Cybersecurity Market?
➧ Who are the distributors, traders, and dealers of V2X (Vehicle-To-Everything) Cybersecurity Market?
➧ What are the market opportunities and threats faced by the vendors in the V2X (Vehicle-To-Everything) Cybersecurity Market?
➧ What are deals, income, and value examination by types and utilizations of the V2X (Vehicle-To-Everything) Cybersecurity Market?
➧ What are deals, income, and value examination by areas of enterprises in the V2X (Vehicle-To-Everything) Cybersecurity Market?
Purchase Now Up to 25% Discount on This Premium Report: https://www.omrglobal.com/buy-now/v2x-cybersecurity-market?license_type=license-single-user
Reasons To Buy The V2X (Vehicle-To-Everything) Cybersecurity Market Report:
➼ In-depth analysis of the market on the global and regional levels.
➼ Major changes in market dynamics and competitive landscape.
➼ Segmentation on the basis of type, application, geography, and others.
➼ Historical and future market research in terms of size, share growth, volume, and sales.
➼ Major changes and assessment in market dynamics and developments.
➼ Emerging key segments and regions
➼ Key business strategies by major market players and their key methods
Contact Us:
Mr. Anurag Tiwari
Email: anurag@omrglobal.com
Contact no: +91 780-304-0404
Website: www.omrglobal.com
Follow Us: LinkedIn | Twitter
About Orion Market Research
Orion Market Research (OMR) is a market research and consulting company known for its crisp and concise reports. The company is equipped with an experienced team of analysts and consultants. OMR offers quality syndicated research reports, customized research reports, consulting and other research-based services. The company also offers Digital Marketing services through its subsidiary OMR Digital and Software development and Consulting Services through another subsidiary Encanto Technologies.
This release was published on openPR.
[ad_2]
