[ad_1]

Ransomware of the week
CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows
Introduction
CYFIRMA Research and Advisory Team has found BlackFL Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
BlackFL Ransomware
Researchers have identified a new ransomware variant named BlackFL, which encrypts victims files and appends the extension “.BlackFL”. In addition to file encryption, BlackFL deletes accessible backups, both physical and virtual, and leaves behind a ransom note titled BlackField_ReadMe.txt. The ransomware campaign appears to be targeted, as the attackers claim they will determine the ransom amount based on the victim’s financial standing, including their income, savings, and insurance coverage. This approach suggests a tailored extortion method intended to maximize pressure while maintaining a degree of negotiation.

Screenshot of files encrypted by ransomware (Source: Surface Web)
The ransom note is written in a calculated tone, aiming to establish communication and push the victim toward payment. It asserts that a large volume of corporate data was exfiltrated prior to encryption and warns that if an agreement isn’t reached, the stolen data including personal information, source code, and trade secrets may be sold on the dark web or publicly leaked. The note offers victims a test decryption to prove the decryptor’s effectiveness and emphasizes that delay or refusal to engage may worsen the outcome. Additionally, the attackers claim they will provide a security report post payment, detailing how they infiltrated the network. Victims are instructed to make contact via two email addresses provided, with urgency implied throughout the message.
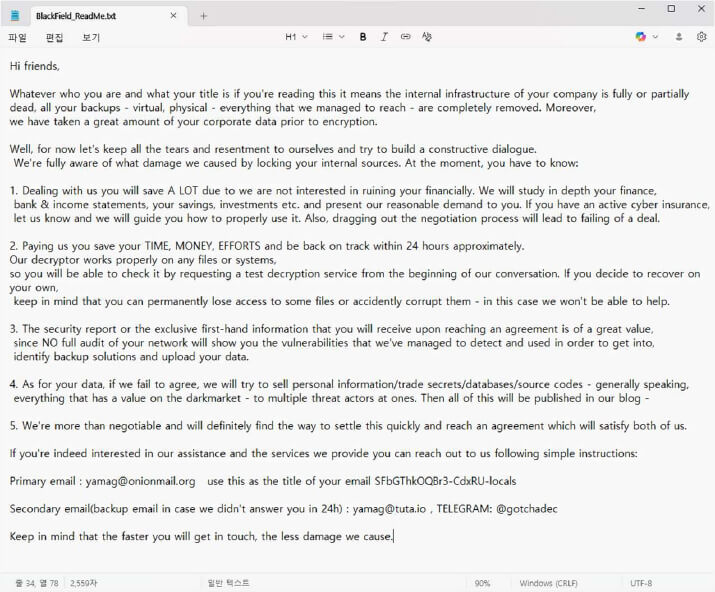
The appearance of BlackFL’s ransom note (“BlackField_ReadMe.txt”) (Source: Surface Web)
Following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1129 | Shared Modules |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1014 | Rootkit |
|
Defense Evasion |
T1027.005 |
Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1070 | Indicator Removal |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1562.001 |
Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1564.001 |
Hide Artifacts: Hidden Files and Directories |
| Credential Access | T1003 | OS Credential Dumping |
| Credential Access | T1552.001 |
Unsecured Credentials: Credentials In Files |
| Discovery | T1057 | Process Discovery |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1135 | Network Share Discovery |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
|
Discovery |
T1518.001 |
Software Discovery: Security Software Discovery |
| Lateral Movement | T1080 | Taint Shared Content |
| Collection | T1005 | Data from Local System |
| Collection | T1074 | Data Staged |
| Collection | T1114 | Email Collection |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1573 | Encrypted Channel |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1496 | Resource Hijacking |
Relevancy and Insights:
- The ransomware mainly targets the Windows operating system, which is widely used across various industries by enterprise environments.
- calls-wmi: The ransomware leverages Windows Management Instrumentation (WMI), a versatile Windows feature that enables it to discreetly collect system information, control processes, or execute commands. This technique is commonly used to avoid detection and carry out reconnaissance activities within the system.
- The ransomware terminates processes using WMIC.exe to delete Volume Shadow Copies, which are Windows built-in backup snapshots. This tactic is commonly used to prevent victims from restoring encrypted files through system restore points, effectively eliminating easy recovery options and increasing the pressure to pay the ransom.
- Detect-Debug-Environment: Debug environments are typically used by developers to examine and troubleshoot programs. The ransomware uses this technique to check if it is running in such an environment, helping it evades analysis and detection by security researchers or automated tools.
ETLM Assessment:
CYFIRMA’s analysis of the BlackFL ransomware indicates a sophisticated and targeted threat that combines data encryption with double extortion tactics, including the theft of sensitive corporate information and tailored ransom demands based on a victim’s financial profile. BlackFL reflects the behavior of a financially motivated and potentially well-resourced threat group capable of adapting its techniques. The ransomware’s use of personalized negotiation, threats of public data leaks, and multi-channel communication suggests an ongoing evolution toward more strategic and damaging attacks. Given these factors, CYFIRMA assesses that BlackFL or its future variants may resurface with enhanced capabilities, broader targeting, and increased operational stealth. Continuous monitoring, predictive intelligence, and proactive defense measures are critical to mitigating the risks posed by this emerging threat.
Sigma rule:
title: Shadow Copies Deletion Using Operating Systems Utilities description: Shadow Copies deletion using operating systems utilities tags:
– attack.defense-evasion
– attack.impact
– attack.t1070
– attack.t1490 logsource:
category: process_creation product: windows
detection: selection1_img:
– Image|endswith:
– ‘\powershell.exe’
– ‘\pwsh.exe’
– ‘\wmic.exe’
– ‘\vssadmin.exe’
– ‘\diskshadow.exe’
– OriginalFileName:
– ‘PowerShell.EXE’
– ‘pwsh.dll’
– ‘wmic.exe’
– ‘VSSADMIN.EXE’
– ‘diskshadow.exe’ selection1_cli:
CommandLine|contains|all:
– ‘shadow’ # will match “delete shadows” and “shadowcopy delete” and “shadowstorage”
– ‘delete’ selection2_img:
– Image|endswith: ‘\wbadmin.exe’
– OriginalFileName: ‘WBADMIN.EXE’ selection2_cli:
CommandLine|contains|all:
– ‘delete’
– ‘catalog’
– ‘quiet’ # will match -quiet or /quiet selection3_img:
– Image|endswith: ‘\vssadmin.exe’
– OriginalFileName: ‘VSSADMIN.EXE’ selection3_cli:
CommandLine|contains|all:
– ‘resize’
– ‘shadowstorage’ CommandLine|contains:
– ‘unbounded’
– ‘/MaxSize=’
condition: (all of selection1*) or (all of selection2*) or (all of selection3*) fields:
– CommandLine
– ParentCommandLine falsepositives:
– Legitimate Administrator deletes Shadow Copies using operating systems utilities for legitimate reason
– LANDesk LDClient Ivanti-PSModule (PS EncodedCommand) level: high
(Source: Surface Web)
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
STRATEGIC RECOMMENDATION
- Implement competent security protocols and encryption, authentication, or access credentials configurations to access critical systems in your cloud and local environments.
- Ensure that backups of critical systems are maintained which can be used to restore data in case a need arises.
MANAGEMENT RECOMMENDATION
- A data breach prevention plan must be developed considering, (a) the type of data being managed by the company; (b) the remediation process; (c) where and how the data is stored; (d) if there is an obligation to notify the local authority.
- Enable zero-trust architecture and multifactor authentication (MFA) to mitigate the compromise of credentials.
- Foster a culture of cybersecurity, where you encourage and invest in employee training so that security is an integral part of your organization.
TACTICAL RECOMMENDATION
- Update all applications/software regularly with the latest versions and security patches alike.
- Add the Sigma rule for threat detection and monitoring which will help to detect anomalies in log events, identify and monitor suspicious activities.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defence based on the tactical intelligence provided.
Trending Malware of the Week
Type: Backdoor| Objectives: Remote Access, Data Theft | Target Technology: macOS | Target Geography: Global
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “ZuRu” is trending.
About Malware ZuRu
A macOS backdoor known as ZuRu has resurfaced with new tactics, continuing its pattern of spreading through modified versions of legitimate applications. Initially observed targeting users searching for tools like iTerm2, the campaign has since expanded to include other widely used utilities, suggesting a clear focus on individuals who manage remote systems. Over time, the malware has evolved in both delivery and communication methods, now incorporating altered control frameworks to maintain access. A recent strain was found hidden within Termius, a popular cross-platform SSH client, showcasing updated techniques for compromising apps and preserving persistence. The evolving nature of ZuRu signals ongoing efforts to quietly infiltrate macOS environments with increasing stealth.
Attack Method
The backdoor is distributed via a disk image file that conceals a compromised version of the Termius app, crafted to closely resemble the official release. Although it appears legitimate at first glance, subtle changes—like a slightly larger file size and an altered code signature—hint at tampering. Hidden within this version are extra components designed to run in the background, one of which secretly downloads a secondary payload used for remote control. This approach differs from earlier techniques used by the same group, showing a shift in how they embed malicious functions within trusted apps to avoid detection and maintain long-term access.
Once launched, the disguised application quietly sets a series of actions into motion to secure its foothold on the system. It requests elevated permission and, if granted, installs a hidden background service that ensures the malware reactivates at regular intervals. To stay under the radar, it checks for any existing instances and runs only one copy at a time. In parallel, it verifies whether its secondary component is already in place; if missing or outdated, it retrieves a fresh copy from a remote server. Subtle clues within the code suggest the attackers may have repurposed elements from earlier campaigns, pointing to an evolving toolkit rather than a completely new creation.
Stealth and Control: ZuRu’s Tactical Shift
ZuRu’s latest evolution shows clear improvements in both evasion and control. To make detection more difficult, the malware now uses a layered method of hiding its data, replacing earlier, simple techniques with a more complex process built around a passphrase. This isn’t meant for true encryption but rather to confuse automated tools and slow down analysis. Beyond obfuscation, the malware’s control component has also been upgraded. The downloaded payload, specifically tailored to target newer macOS systems, is a customized version of an open-source command-and-control tool. This implant supports remote access, system monitoring, file transfers, and process control—all while blending in with legitimate traffic by using common services as decoys. The setup reflects a clear attempt to refine stealth and persistence, suggesting a deliberate shift toward more resilient and evasive behavior in ZuRu’s ongoing operations.
Following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1036.001 | Masquerading: Invalid Code Signature |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1553 | Subvert Trust Controls |
| Defense Evasion | T1553.002 | Subvert Trust Controls: Code Signing |
| Defense Evasion | T1564 | Hide Artifacts |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1573 | Encrypted Channel |
INSIGHTS
- ZuRu stands out as a macOS-targeting backdoor that carefully blends into environments where trusted applications are routinely used. What makes it particularly noteworthy is its choice of disguise—well-known tools used by IT professionals and developers. The threat actors behind ZuRu distribute their malware through software commonly relied on in technical workflows, increasing the likelihood that it blends in with expected activity. This approach reflects a deep understanding of operational environments rather than just a reliance on system- level exploits, emphasizing the social engineering side of the campaign.
- Beyond initial access, ZuRu’s operation reflects a well-orchestrated sequence of silent routines aimed at establishing long-term presence. Its ability to quietly install background services, manage system checks, and operate without triggering user suspicion highlights the discipline behind its design. The attackers have taken care to ensure that once ZuRu is active, it behaves in a way that mimics normal software behavior, reducing the chances of manual detection. This subtlety suggests a high level of intent behind each stage of execution, where stealth is prioritized over aggression.
- ZuRu also shows signs of ongoing development, with traces of older code and unused functions suggesting it has been updated over time. These details reveal that the malware wasn’t built all at once but gradually shaped to fit different use cases. Instead of being a one-time creation, ZuRu appears to be part of a larger toolkit that attackers can adjust and reuse as needed.
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that ZuRu’s continued evolution signals a rising threat to macOS users who depend on trusted applications for daily operations. As the malware blends into commonly used software, it increases the likelihood of silent installation during routine downloads or updates. This subtle approach creates potential blind spots in everyday system use, allowing attackers to gain access without raising suspicion. If such stealth techniques become more common, malicious tools could remain active for extended periods, quietly observing user behavior and adapting their actions over time. This prolonged presence raises the risk of sensitive data being accessed or misused, as future threats become increasingly tailored, persistent, and difficult to distinguish from legitimate software activity.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rule
rule ZuRu_macOS_Backdoor
{
meta:
description = “Detects ZuRu macOS backdoor indicators” author = “CYFIRMA”
malware_family = “ZuRu”
strings:
// URLs
$url1 = “http://download.termius.info/bn.log.enc”
$url2 = “http://download.termius.info/bn.log.md5”
// Domain
$domain_1 = “ctl01.termius.fun”
// IP address
$ip_1 = “47.238.28.21”
// SHA1 Hashes
$sha1_1 = “a7a9b0f8cc1c89f5c195af74ce3add74733b15c0”
$sha1_2 = “ace81626924c34dfbcd9a485437cbb604e184426”
$sha1_3 = “de8aca685871ade8a75e4614ada219025e2d6fd7”
$sha1_4 = “fa9b89d4eb4d47d34f0f366750d55603813097c1”
condition:
any of ($url*) or
any of ($domain*) or any of ($ip*) or
any of ($sha1*)
}
Recommendations:
STRATEGIC:
- Maintain an up-to-date inventory of all active software used within the organization and perform regular self-audit of workstations, servers, laptops, mobile devices to identify unauthorized/ restricted software.
- Configure organization’s intrusion detection systems (IDS), intrusion prevention systems (IPS), or any network defence mechanisms in place to alert on — and upon review, consider blocking connection attempts to and from — the external IP addresses and domains listed in the appendix.
MANAGEMENT:
- Effective implementation of security initiatives that encompass awareness building and training across the organization.
- Security Awareness training should be mandated for all company employees. The training should ensure that employees:
- Avoid downloading and executing files from unverified sources.
- Avoid free versions of paid software.
- Move beyond the traditional model of security awareness towards Improved Simulation and training exercises that mimic real attack scenarios, account for behaviors that lead to a compromise, and are measured against real attacks the organization receives.
TACTICAL RECOMMENDATIONS
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defence based on the tactical intelligence provided.
- Enforce policies to validate third-party software before installation.
- Add the Yara rules for threat detection and monitoring which will help to detect anomalies in log events and identify and monitor suspicious activities.
CYFIRMA’s WEEKLY INSIGHTS
1. Weekly Attack Types and Trends
Key Intelligence Signals:
- Attack Type: Ransomware Attacks, Vulnerabilities & Exploits, Data Leaks.
- Objective: Unauthorized Access, Data Theft, Data Encryption, Financial Gains, Espionage.
- Business Impact: Data Loss, Financial Loss, Reputational Damage, Loss of Intellectual Property, Operational Disruption.
- Ransomware – Lynx Ransomware, Everest Ransomware| Malware – ZuRu
- Lynx Ransomware– One of the ransomware groups.
- Everest ransomware– One of the ransomware groups.
Please refer to the trending malware advisory for details on the following: - Malware – ZuRu
Behavior – Most of these malwares use phishing and social engineering techniques as their initial attack vectors. Apart from these techniques, exploitation of vulnerabilities, defense evasion, and persistence tactics are being observed.
2. Threat Actor in Focus
APT43 (Kimsuki): The North Korean Nation-State Adversary with Hybrid Operational Model
- Threat Actor: APT43 aka (Kimsuki).
- Attack Type: Credential Harvesting, Vulnerabilities & Exploits, Social Engineering.
- Objective: Espionage, Information Theft.
- Target Technology: Bandizip, Hangul Word Processor, Social Platforms, macOS, and Windows.
- Target Geography: Belgium, Bulgaria, Canada, Croatia, Denmark, Estonia, Finland, France, Germany, Greece, Hungary, Iceland, Italy, Latvia, Lithuania, Luxembourg, Montenegro, North Macedonia, Norway, Poland, Portugal, Romania, Slovakia, Slovenia, the Czech Republic, the Netherlands, Albania, Japan, South Korea, Thailand, the USA, and Vietnam.
- Target Industries: Aerospace, Construction, Consulting, Defence, Education, Government, Hi-Tech, Manufacturing, Media & Entertainment, NGO, Pharmaceuticals, Professional Services, Research, Telecommunications, Think Tanks.
- Business Impact: Data Exfiltration, Operational Disruption, Reputational Damage.
About the Threat Actor
APT43, active since 2013 and demonstrating characteristics of an Advanced Persistent Threat (APT) actor since 2018, is believed to operate out of North Korea. The group is reportedly self-funded and operates in alignment with the strategic interests of the North Korean regime. Its collection priorities appear closely aligned with the objectives of the Reconnaissance General Bureau (RGB), North Korea’s primary foreign intelligence agency.
The adversary exhibits moderately sophisticated technical capabilities, often coupled with aggressive social engineering techniques. Its operations have predominantly targeted government entities, academic institutions, and think tanks, particularly those based in South Korea and the United States, with a focus on geopolitical developments concerning the Korean Peninsula. They blend traditional espionage with cybercrime for operational funding.
Vulnerabilities Exploite
| CVE | CVSS | Role | Exploit |
| CVE-2017-11882 | 7.8 | Arbitrary Code Execution |
|
| CVE-2019- 0708 (BlueKeep Vulnerability) | 9.8 | Remote Code Execution |
|
TTPs based on MITRE ATT&CK Framework
| MITRE FRAMEWORK | ||
| Tactic | ID | Technique |
| Reconnaissance | T1589.002 | Gather Victim Identity Information: Email Addresses |
| Reconnaissance | T1589.003 | Gather Victim Identity Information: Employee Names |
| Reconnaissance | T1591 | Gather Victim Org Information |
| Reconnaissance | T1598.003 | Phishing for Information: Spear phishing Link |
| Reconnaissance | T1596 | Search Open Technical Databases |
| Reconnaissance | T1593.001 | Search Open Websites/Domains: Social Media |
| Reconnaissance | T1593.002 | Search Open Websites/Domains: Social Engines |
| Reconnaissance | T1594 | Search Victim-Owned Websites |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains |
| Resource Development | T1583.004 | Acquire Infrastructure: Server |
| Resource Development | T1583.006 | Acquire Infrastructure: Web Services |
| Resource Development | T1586.002 | Compromise Accounts: Email Accounts |
| Resource Development | T1584.001 | Compromise Infrastructure: Domains |
| Resource Development | T1587.001 | Develop Capabilities: Malware |
| Resource Development | T1585.001 | Establish Accounts: Social Media Accounts |
| Resource Development | T1585.002 | Establish Accounts: Email Accounts |
| Resource Development | T1588.002 | Obtain Capabilities: Tool |
| Resource Development | T1588.003 | Obtain Capabilities: Code Signing Certificates |
| Resource Development | T1588.005 | Obtain Capabilities: Exploits |
| Resource Development | T1608.001 | Stage Capabilities: Upload Malware |
| Initial Access | T1190 | Exploit Public-Facing Application |
| Initial Access | T1133 | External Remote Services |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Initial Access | T1566.002 | Phishing: Spear phishing Link |
| Initial Access | T1078.003 | Valid Accounts: Local Accounts |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell |
| Execution | T1059.005 | Command and Scripting Interpreter: Visual Basic |
| Execution | T1059.006 | Command and Scripting Interpreter: Python |
| Execution | T1059.007 | Command and Scripting Interpreter: JavaScript |
| Execution | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Execution | T1204.001 | User Execution: Malicious Link |
| Execution | T1204.002 | User Execution: Malicious File |
| Persistence | T1098.007 | Account Manipulation: Additional Local or Domain Groups |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1136.001 | Create Account: Local Account |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Persistence | T1546.001 | Event Triggered Execution: Change Default File Association |
| Persistence | T1133 | External Remote Services |
| Persistence | T1112 | Modify Registry |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Persistence | T1505.003 | Server Software Component: Web Shell |
| Persistence | T1176.001 | Software Extensions: Browser Extensions |
| Persistence | T1205 | Traffic Signalling |
| Persistence | T1078.003 | Valid Accounts: Local Accounts |
| Privilege Escalation | T1098.007 | Account Manipulation: Additional Local or Domain Groups |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1546.001 | Event Triggered Execution: Change Default File Association |
| Privilege Escalation | T1055.012 | Process Injection: Process Hollowing |
| Privilege Escalation | T1053.005 | Scheduled Task/Job: Scheduled Task |
| Privilege Escalation | T1078.003 | Valid Accounts: Local Accounts |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| Defense Evasion | T1564.002 | Hide Artifacts: Hidden Users |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1562.004 | Impair Defenses: Disable or Modify System Firewall |
| Defense Evasion | T1656 | Impersonation |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1070.006 | Indicator Removal: Timestomp |
| Defense Evasion | T1036.004 | Masquerading: Masquerade Task or Service |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Resource Name or Location |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1027.002 | Obfuscated Files or Information: Software Packing |
| Defense Evasion | T1055.012 | Process Injection: Process Hollowing |
| Defense Evasion | T1620 | Reflective Code Loading |
| Defense Evasion | T1553.002 | Subvert Trust Controls: Code Signing |
| Defense Evasion | T1218.005 | System Binary Proxy Execution: Mshta |
| Defense Evasion | T1218.010 | System Binary Proxy Execution: Regsvr32 |
| Defense Evasion | T1218.011 | System Binary Proxy Execution: Rundll32 |
| Defense Evasion | T1205 | Traffic Signalling |
| Defense Evasion | T1550.002 | Use Alternate Authentication Material: Pass the Hash |
| Defense Evasion | T1078.003 | Valid Accounts: Local Accounts |
| Credential Access | T1557 | Adversary-in-the-Middle |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Credential Access | T1111 | Multi-Factor Authentication Interception |
| Credential Access | T1040 | Network Sniffing |
| Credential Access | T1003.001 | OS Credential Dumping: LSASS Memory |
| Credential Access | T1539 | Steal Web Session Cookie |
| Credential Access | T1552.001 | Unsecured Credentials: Credentials In Files |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1040 | Network Sniffing |
| Discovery | T1057 | Process Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Discovery | T1083 | System Information Discovery |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1007 | System Service Discovery |
| Lateral Movement | T1534 | Internal Spear phishing |
| Lateral Movement | T1021.001 | Remote Services: Remote Desktop Protocol |
| Lateral Movement | T1550.002 | Use Alternate Authentication Material: Pass the Hash |
| Collection | T1557 | Adversary-in-the-Middle |
| Collection | T560.001 | Archive Collected Data: Archive via Utility |
| Collection | T1560.003 | Archive Collected Data: Archive via Custom Method |
| Collection | T1185 | Browser Session Hijacking |
| Collection | T1005 | Data from Local System |
| Collection | T1074.001 | Data Staged: Local Data Staging |
| Collection | T1114.002 | Email Collection: Remote Email Collection |
| Collection | T1114.003 | Email Collection: Email Forwarding Rule |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1113 | Screen Capture |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1071.002 | Application Layer Protocol: File Transfer Protocols |
| Command and Control | T1071.003 | Application Layer Protocol: Mail Protocols |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1219.002 | Remote Access Tools: Remote Desktop Software |
| Command and Control | T1205 | Traffic Signalling |
| Command and Control | T1102.001 | Web Service: Dead Drop Resolver |
| Command and Control | T1102.002 | Web Service: Bidirectional Communication |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| Exfiltration | T1567.002 | Exfiltration Over Web Service: Exfiltration to Cloud Storage |
| Impact | T1657 | Financial Theft |
Latest Developments Observed
The threat actor is suspected of leveraging HappyDoor malware by sending installation packages disguised as Bandizip against organizations in South Korea. The threat actor is believed to use phishing attacks as part of initial access. The motive appears to be espionage and information theft.
ETLM Insights
APT43 is one of the nation-state adversaries of North Korea, which has become highly active, expanding its attack surface, digital footprints across industries and geographies. The adversary has a distinct feature of being known to engage in financially motivated cybercrime to fund its intelligence-gathering efforts, illustrating a dual-purpose operational model that combines espionage with illicit revenue generation.
Due to this, the adversary is potentially having close links to Reconnaissance General Bureau (RGB), North Korea’s primary foreign intelligence agency, as they are resourceful, persistent, and financially self-sustaining. Their threat activity continues to evolve, with an emphasis on stealth, social engineering, and long-term access within targeted environments.
YARA Rules
rule APT43_Generic_Activity
{
meta:
author = “CYFIRMA”
description = “Detects potential malware and document lures associated with APT43”
threat_group = “APT43”
malware_family = “KONNI, LONEWOLF, QUASARRAT” date = “2025-07-13”
version = “1.0” strings:
// KONNI-related strings
$s1 = “KONNI” wide ascii nocase
$s2 = “cmd.exe /c start” ascii
$s3 = “rundll32.exe” ascii
$s4 = “System.Diagnostics.Process” ascii
$s5 = “netstat -an” ascii
$s6 = “GetForegroundWindow” ascii
$s7 = “powershell -ep bypass” ascii
// Common in phishing decoys (doc macros)
$v1 = “AutoOpen” ascii
$v2 = “ThisDocument” ascii
$v3 = “Shell.Application” ascii
$v4 = “WScript.Shell” ascii
// Network beaconing (hardcoded)
$c2_1 = “http://update-service[.]xyz” ascii
$c2_2 = “https://mail-service[.]online” ascii condition:
(uint16(0) == 0x5A4D or uint32(0) == 0x504B0304) and 4 of ($s*) or
2 of ($v*) or
any of ($c2_*)
}
rule APT43_HappyDoor_Malware
{
meta:
author = “CYFIRMA”
description = “Detects HappyDoor malware associated with APT43” threat_group = “APT43”
malware_family = “HappyDoor” last_updated = “2025-07-13”
version = “1.0” strings:
// C2 IP address as hardcoded string
$c2_ip = “67.217.62.222”
// HappyDoor behavior or keywords (example placeholders)
$s1 = “HappyDoor” nocase ascii
$s2 = “InstallService” ascii
$s3 = “Backdoor_Connection” ascii
$s4 = “ProcessInjection” ascii
$s5 = “KeyloggingStarted” ascii condition:
// Match by hash or known patterns (filesize < 2MB and 3 of ($s*)) or
// Match by known C2 IP
$c2_ip or
// Match by known hashes (file hash matching for IOC reference) Md5 == “f4cd4449e556b0580c2282fec1ca661f” or
Md5 == “d1ec20144c83bba921243e72c517da5e” or Md5 == “16d30316a6b700c78d021df5758db775” or Md5 == “a6598bbdc947286c84f951289d14425c” or
Md5 == “07fbf46d3a595a6f82e477ed4571294b”
}
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
Recommendations
Strategic
- Incorporate Digital Risk Protection (DRP) as part of the overall security posture to proactively defend against impersonations and phishing attacks.
- Deploy Zero Trust Policy that leverages tools like security information management, advanced security analytics platforms, security user behaviour analytics, and other analytics systems to help the organization’s security personnel observe in real-time what is happening within their networks so they can orient defences more intelligently.
- Block exploit-like behaviour. Monitor endpoints memory to find behavioural patterns that are typically exploited, including unusual process handle requests. These patterns are features of most exploits, whether known or new. This will be able to provide effective protection against zero-day/critical exploits and more by identifying such patterns.
Management
- Invest in user education and implement standard operating procedures for the handling of financial and sensitive data transactions commonly targeted by impersonation attacks. Reinforce this training with context-aware banners and in-line prompts to help educate users.
- Look for email security solutions that use ML- and AI-based anti-phishing technology for BEC protection to analyse conversation history to detect anomalies, as well as computer vision to analyse suspect links within emails.
Tactical
- Set up DMARC (Domain-based Message Authentication Reporting & Conformance) to stop phishers from spoofing your domain (that is, making their emails look like they come from your organization).
- Protect accounts with multi-factor authentication. Exert caution when opening email attachments or clicking on embedded links supplied via email communications, SMS, or messaging.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defences based on the tactical intelligence provided.
- Add the YARA rules for threat detection and monitoring, which will help to detect anomalies in log events and identify and monitor suspicious activities.
3. Major Geopolitical Developments in Cybersecurity
Iranian ransomware gang offers bonuses for hitting US and Israeli targets
The Iranian ransomware-as-a-service operation Pay2Key.I2P is offering 10% incentive bonuses to affiliates who target U.S. and Israeli organizations. Affiliates can now claim an 80% share of ransom proceeds, up from the previous 70% when attacking countries adversarial to Iran. The researchers note that Pay2Key maintains connections with the Tehran-backed cyberespionage group Fox Kitten and has close ties to the Mimic ransomware operation. Since emerging in February 2025, Pay2Key has amassed over $4 million in ransom payments.
ETLM Assessment:
Last couple of weeks, CYFIRMA has warned that despite a declared ceasefire and ongoing negotiations towards a permanent solution in the conflict between Iran and Israel + USA, Iranian-affiliated cyber actors and hacktivist groups may still conduct malicious cyber activity in countries perceived as hostile to Iran, especially the US and Israel. American defense firms with investments in or partnerships with Israeli companies face an elevated risk of being targeted by Iran-linked state-sponsored hackers and other cybercriminal groups aligned with Tehran. The same advisory needs to be extended to all European powers, GCC countries, and India too.
India-aligned espionage campaign targets Italy
Researchers have released a report detailing a cyberespionage campaign by the DoNot APT group that has recently conducted a multi-stage cyber espionage campaign targeting the Italian Ministry of Foreign Affairs. DoNot APT, also known as Mint Tempest, Origami Elephant, or Viceroy Tiger, has been active since at least 2016 and is aligned with Indian interests and widely considered to have ties to the government of India. The attackers posed as European defense officials, referencing a visit to Bangladesh to add credibility, and enticed their victims to click a malicious Google Drive link. This led to the download of a harmful RAR archive, which ultimately deployed malware consistent with the group’s established toolkit. The incident highlights the group’s ongoing focus on governmental and diplomatic targets and their evolving tactics, including leveraging widely used cloud services to initiate infections.
ETLM Assessment:
The campaign bears all the hallmarks of a state-driven espionage campaign with a goal of providing strategic intelligence. Although the group has traditionally concentrated on South Asia, this operation targeting South Asian embassies in Europe demonstrates a clear broadening of their focus to include European diplomatic communications and intelligence. Besides Italy, similar operations have been active in Pakistan, Bangladesh, Sri Lanka, China, and possibly Australia.
4. Rise in Malware/Ransomware and Phishing
Lynx Ransomware Impacts the ITACCESS PTE. LTD.
- Attack Type: Ransomware
- Target Industry: Information Technology
- Target Geography: Singapore
- Ransomware: Lynx Ransomware
- Objective: Data Theft, Data Encryption, Financial Gains
- Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Singapore, ITACCESS PTE. LTD (https[:]//www[.]itaccess[.]com[.]sg/) was compromised by Lynx Ransomware. ITACCESS PTE. LTD. is a Singapore-based company specializing in information technology consultancy, with a core focus on data storage management, infrastructure virtualization, enterprise storage solutions, data protection, and business continuity services. The compromised data includes financial documents, purchase and sale deed bills, along with other confidential and sensitive information pertaining to the organization. The asking price for the leaked data is $10,000,000.
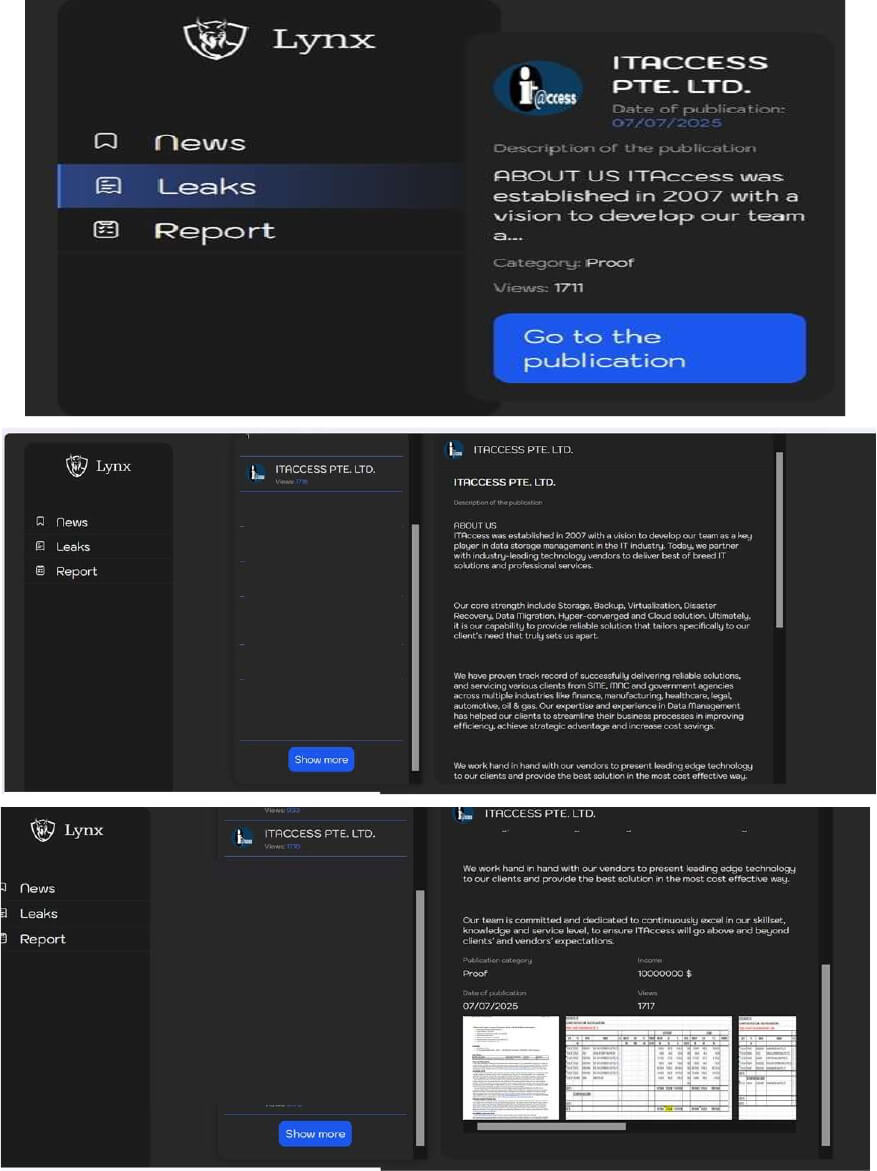
Source: Dark Web
Relevancy & Insights:
- Lynx offers multiple encryption modes (fast, medium, slow, and entire) to balance the speed and depth of encryption. It uses Curve25519 Donna and AES-128 encryption algorithms.
- Lynx offers cross-platform ransomware binaries for Windows and Linux environments, supporting various architectures like x86, ARM, MIPS, PPC, and ESXi.
- Lynx provides a comprehensive platform for affiliates, including tools for managing victims, negotiating ransoms, and sharing access with sub-affiliates.
- The Lynx Ransomware group primarily targets countries such as the United States of America, the United Kingdom, Germany, France, and Australia.
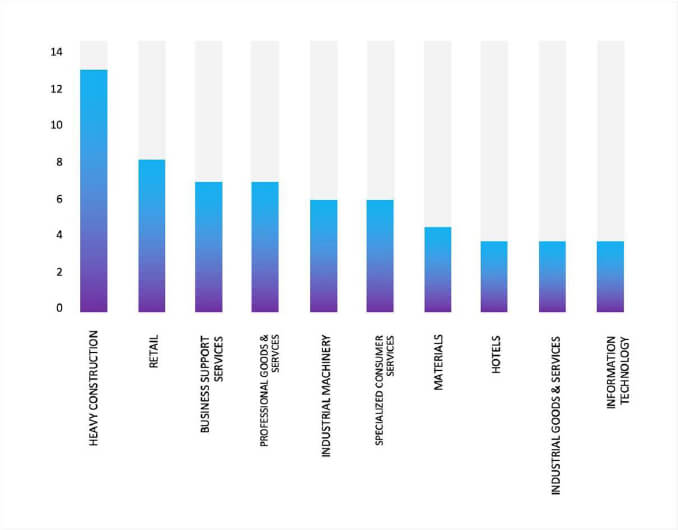
- The Lynx Ransomware group primarily targets industries, including Heavy Construction, Retail, Business Support Services, Professional Goods & Services, and Industrial Machinery.
- Based on the Lynx Ransomware victims list from 1st Jan 2025 to 16th July 2025, the top 5 Target Countries are as follows:
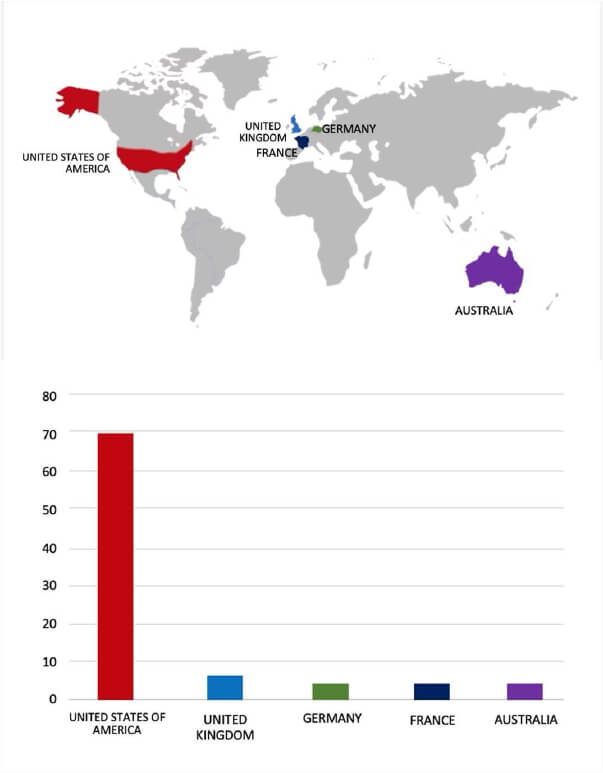
- The Top 10 Industries most affected by the Lynx Ransomware victims list from 1st Jan 2025 to 16th July 2025 are as follows:
ETLM Assessment:
According to CYFIRMA’s assessment, Lynx ransomware has emerged as a significant threat in the cybersecurity landscape, leveraging advanced encryption and double extortion tactics to target small and medium-sized businesses. Its structured affiliate program and versatile ransomware toolkit make it a formidable force in the RaaS ecosystem.
Everest ransomware impacts the Rezayat Group
- Attack Type: Ransomware
- Target Industry: Conglomerate Engineering & Contracting, Industrial, Logistics, Manufacturing, IT, Finance, Energy, and Hospitality
- Target Geography: Saudi Arabia
- Ransomware: Everest ransomware
- Objective: Data Theft, Data Encryption, Financial Gains
- Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Saudi Arabia, Rezayat Group (https[:]//www[.]rezayat[.]com/), was compromised by Everest ransomware. Rezayat Group is a diversified, Gulf-based conglomerate with extensive operations across engineering, manufacturing, logistics, IT, finance, and hospitality—serving global markets with a strong legacy in oil & gas and infrastructure sectors. The compromised data includes internal documents such as blueprints, architectural plans, financial records, and other sensitive materials, totaling 10 gigabytes of files.
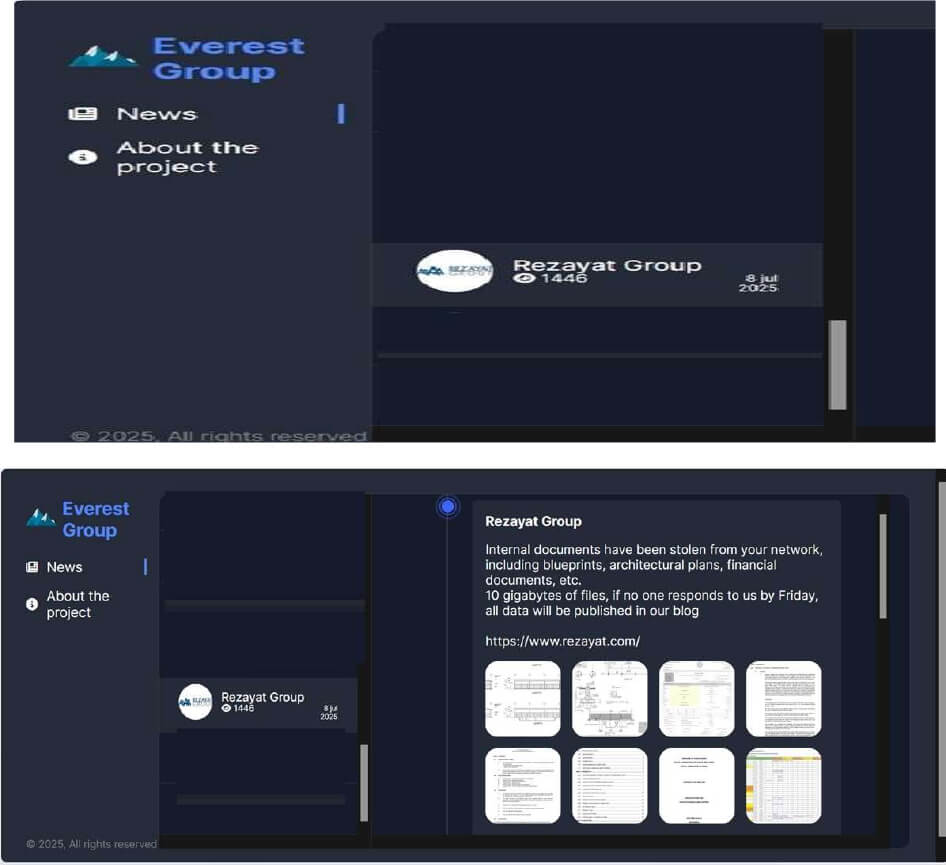
Source: Dark Web
Relevancy & Insights:
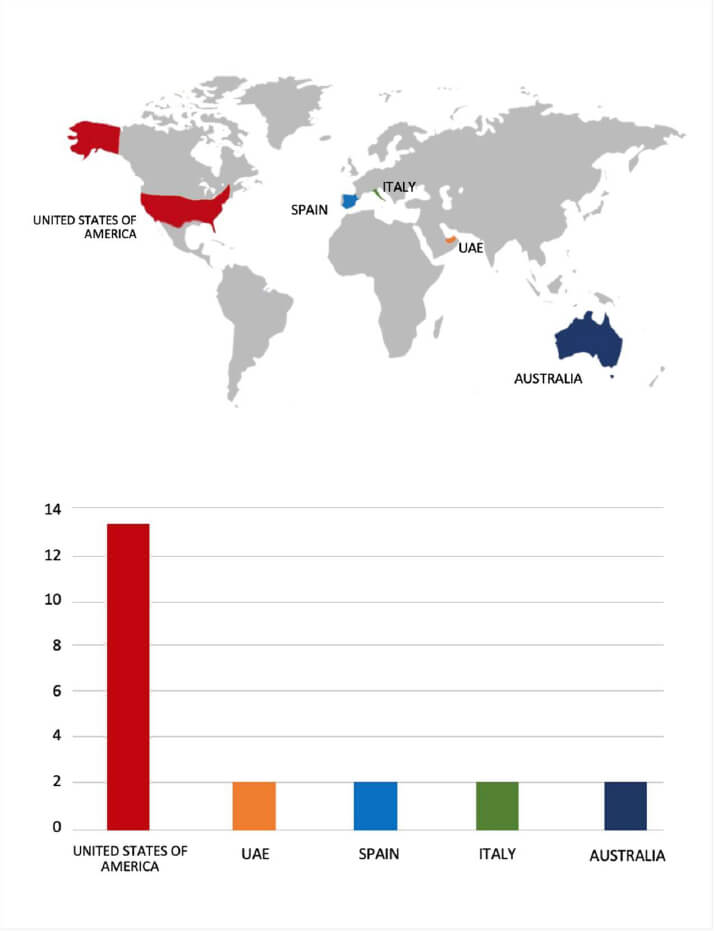
- The Everest Ransomware group primarily targets countries such as the United States of America, UAE, Spain, Italy, and Australia.
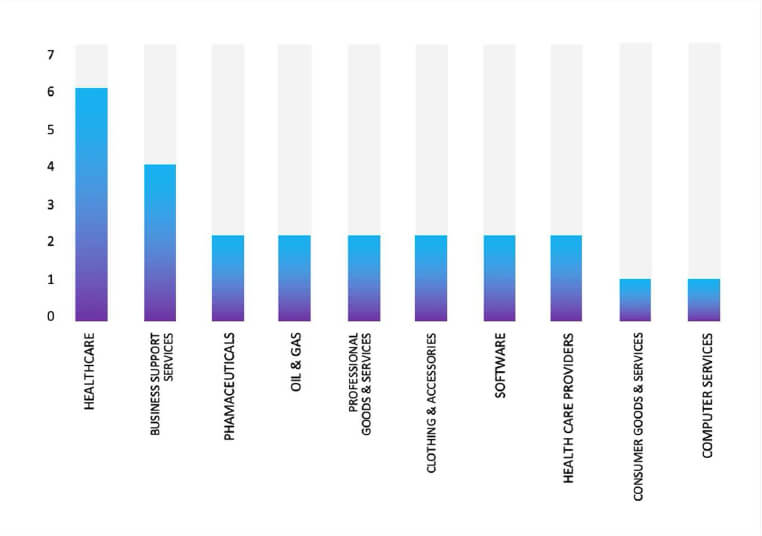
- The Everest Ransomware group primarily targets industries, including Healthcare, Business Support Services, Pharmaceuticals, Oil & Gas, and Professional Goods & Services.
- Based on the Everest ransomware victims list from 1st Jan 2025 to 16th July 2025, the top 5 Target Countries are as follows:
- The Top 10 Industries most affected by the Everest ransomware victims list from 1st Jan 2025 to 16th July 2025 are as follows:
ETLM Assessment:
According to CYFIRMA’s assessment, Everest Ransomware remains a persistent and evolving threat in 2025. Despite the takedown of its leak site, the group continues to target new sectors, expand its operations as an initial access broker, and leverage data leak extortion as its primary tactic. Organizations should remain vigilant, strengthen access controls, monitor for lateral movement and Cobalt Strike activity, and ensure robust incident response capabilities to defend against Everest’s ongoing campaigns.
5. Vulnerabilities and Exploits
Vulnerability in Siemens SIMATIC CN 4100
- Attack Type: Vulnerabilities & Exploits
- Target Technology: Hardware solutions / Firmware
- Vulnerability: CVE-2025-40593
- CVSS Base Score: 6.5 Source
- Vulnerability Type: Improper input validation
- Summary: The vulnerability allows a remote attacker to perform a denial of service (DoS) attack.
Relevancy & Insights:
The vulnerability exists due to the affected application allowing device control by storing arbitrary files in the SFTP folder of the device.
Impact:
A remote user can pass specially crafted input to the application and perform a denial of service (DoS) attack.
Affected Products:
https[:]//cert-portal[.]siemens[.]com/productcert/html/ssa- 626991.html
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
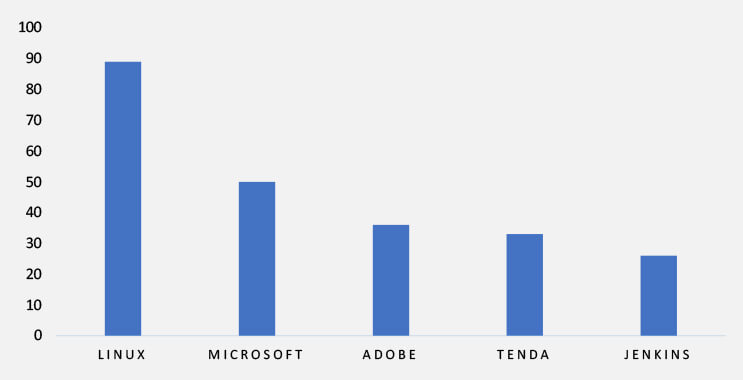
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Vulnerability in Siemens SIMATIC CN 4100 can pose significant threats to user privacy and security. This can impact various industries globally, including manufacturing, energy, transportation, and critical infrastructure. Ensuring the security of Siemens SIMATIC CN 4100 is crucial for maintaining the integrity and protection of industrial automation systems worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding network communication, system integration, and control operations across different geographic regions and sectors.
6. Latest Cyber-Attacks, Incidents, and Breaches
NightSpire Ransomware attacked and published the data of Tuna Processors Philippines, Inc. (TPPI)
- Threat Actor: NightSpire Ransomware
- Attack Type: Ransomware
- Objective: Data Leak, Financial Gains
- Target Technology: Web Applications
- Target Industry: Food and Beverages
- Target Geography: Philippines
- Business Impact: Operational Disruption, Data Loss, Financial Loss, Potential Reputational Damage
Summary:
Recently, we observed that NightSpire Ransomware attacked and published the data of the Tuna Processors Philippines, Inc. (TPPI)(https[:]//tppi[.]com/) on its dark web website. Tuna Processors Philippines, Inc. (TPPI) is a key player in the Philippine tuna industry, recognized as a pioneer in producing sashimi-quality frozen tuna using a proprietary “filtered smoke technology” for preserving and smoking tuna. The data leak, following the ransomware attack, encompasses sensitive and confidential records originating from the organizational database. The total size of the data compromised is approximately 1 GB.
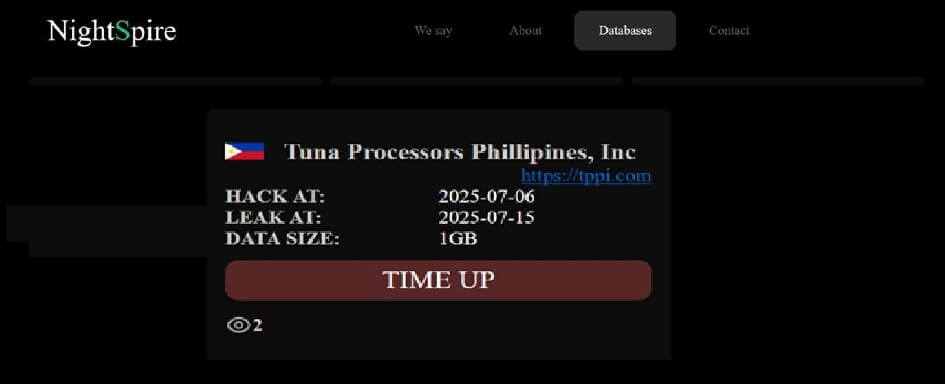
Source: Dark Web
Relevancy & Insights:
- NightSpire employs a double extortion strategy, encrypting data and threatening to leak stolen information unless a ransom is paid. This approach is typical of modern ransomware groups and adds pressure on victims to comply with demands.
- NightSpire’s operations show strong influences from existing Ransomware-as-a- Service (RaaS) models, suggesting they might be an emerging group or a rebrand of an existing actor.
ETLM Assessment:
According to CYFIRMA’s assessment, NightSpire is a new ransomware group that emerged in early 2025, marking itself as a formidable player in the rapidly evolving ransomware landscape. Despite its recent appearance, NightSpire has already gained attention for its aggressive tactics and well-structured operations.
7. Data Leaks
ShareKhan Ltd Data Advertised on a Leak Site
- Attack Type: Data Leak
- Target Industry: Finance
- Target Geography: India
- Objective: Financial Gains
- Business Impact: Data Loss, Reputational Damage
Summary:
The CYFIRMA Research team observed a data leak related to ShareKhan Ltd (https[:]//www[.]sharekhan[.]com/) in an underground forum. Sharekhan Ltd is one of India’s oldest and most recognized full-service retail brokerage firms. It offers a wide range of financial services, including equity trading, derivatives, mutual funds, IPOs, portfolio management services (PMS), and research-backed advisory. The threat actor known as RareData has posted on a dark web forum, claiming responsibility for a breach of ShareKhan Ltd.
The actor claims to possess 3.4 million PAN-linked user records, allegedly extracted from ShareKhan’s back-office platform. The data reportedly contains highly sensitive information, including:
- PAN (Indian Government ID)
- Full Name, Father/Husband Name
- Account Details (A/C Type, DP Internal Ref No)
- Email, Phone, Date of Birth
- Holdings, Transactions, Ledger Summaries
- Branch-Level Mapping and Segmentation
The threat actor is offering the data for sale to a single buyer only.
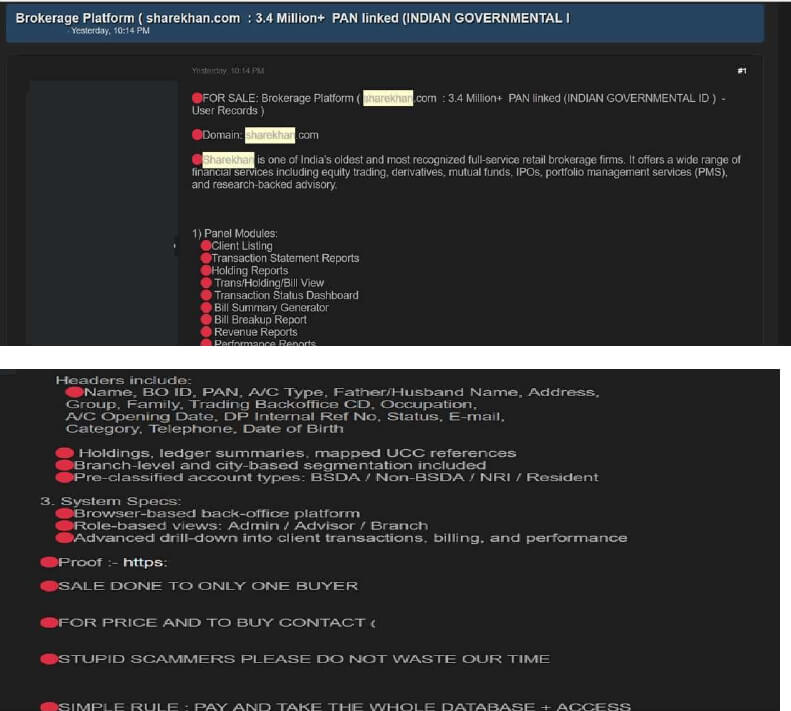
Source: Underground Forums
Naver Corporation Data Advertised on a Leak Site
- Attack Type: Data leak
- Target Industry: Information Technology
- Target Geography: South Korea
- Objective: Data Theft, Financial Gains
- Business Impact: Data Loss, Reputational Damage
Summary:
The CYFIRMA Research team observed a data leak related to Naver Corporation(https://www.naver.com/) in an underground forum. Naver[.]com, often described as the “Yahoo for Koreans” and owned by the Japanese company Line. The alleged breach includes a range of critical user information, which could have serious implications for the millions who rely on Naver’s services for everything from search and news to shopping and communication. While the full extent of the compromised data is still being assessed, the initial indications point to a significant security incident.
Leaked data allegedly includes:
- User IDs
- Password Hashes
- Emails
- Plaintext Passwords
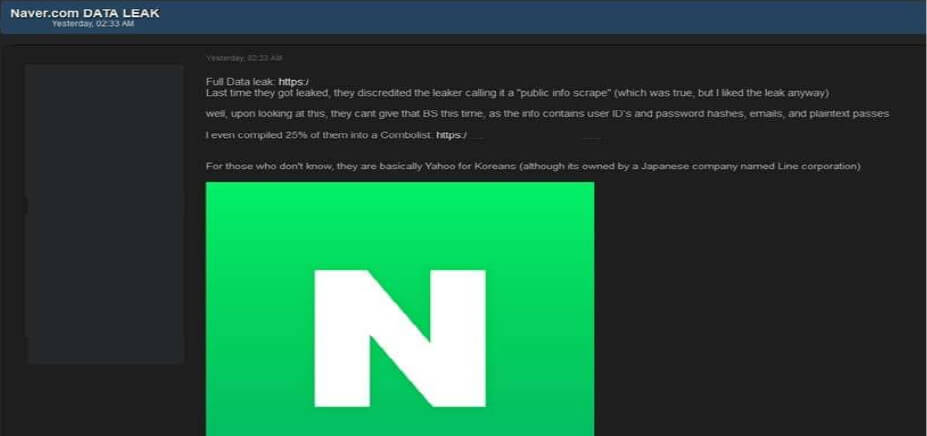
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor known as “RareData” has recently emerged as a highly active group focused on data leaks. Credible sources have linked the group to several security breaches involving unauthorized access and the attempted sale of stolen data on dark web marketplaces. Their continued activity reflects the persistent and evolving nature of cyber threats originating from underground forums. These incidents emphasize the urgent need for organizations to enhance their cybersecurity posture through continuous monitoring, robust threat intelligence, and proactive defense measures to safeguard critical information assets.
Recommendations: Enhance the cybersecurity posture by:
- Updating all software products to their latest versions is essential to mitigate the risk of vulnerabilities being exploited.
- Ensure proper database configuration to mitigate the risk of database-related attacks.
- Establish robust password management policies, incorporating multi-factor authentication and role-based access to fortify credential security and prevent unauthorized access.
8. Other Observations
The CYFIRMA Research team observed a data leak related to LAPOR! (Layanan Aspirasi dan Pengaduan Online Rakyat) (https[:]//www[.]lapor[.]go[.]id) in an underground forum. lapor[.]go[.]id is an official Indonesian government platform called LAPOR! (Layanan Aspirasi dan Pengaduan Online Rakyat). It serves as a public complaint and feedback system where citizens can submit complaints, suggestions, or feedback regarding public services and government activities. The database contains the personal information of over 400,000 users. The compromised data includes user ID, username, password, email, activation status, account status, profile photo hash, ban status and reason, password reset keys, password request timestamps, redirect URLs, authentication tokens, user metadata, new email addresses and associated keys, last known IP addresses, login history, account creation and modification dates, registration sources, Facebook and Twitter user IDs, user scores, access levels, institution IDs, display preferences, stream data, verification status, account closures, and user support actions.
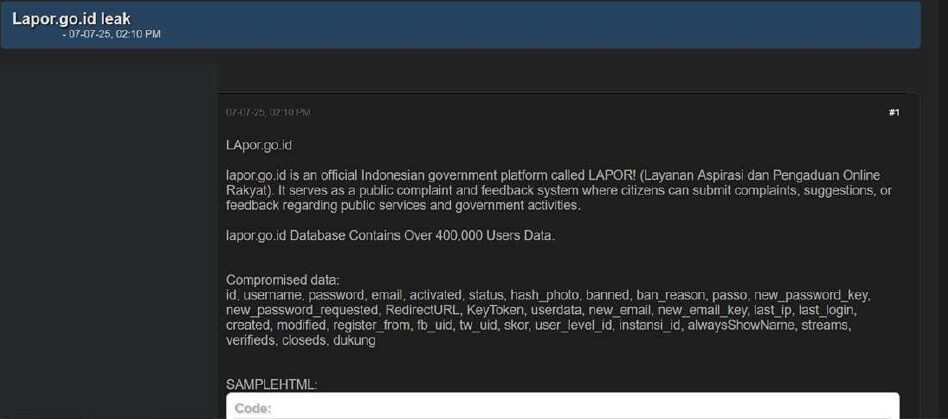
Source: Underground Forums
STRATEGIC RECOMMENDATIONS
- Attack Surface Management should be adopted by organisations, ensuring that a continuous closed-loop process is created between attack surface monitoring and security testing.
- Delay a unified threat management strategy – including malware detection, deep learning neural networks, and anti-exploit technology – combined with vulnerability and risk mitigation processes.
- Incorporate Digital Risk Protection (DRP) in the overall security posture that acts as a proactive defence against external threats targeting unsuspecting customers.
- Implement a holistic security strategy that includes controls for attack surface reduction, effective patch management, and active network monitoring, through next-generation security solutions and a ready-to-go incident response plan.
- Create risk-based vulnerability management with deep knowledge about each asset. Assign a triaged risk score based on the type of vulnerability and criticality of the asset to help ensure that the most severe and dangerous vulnerabilities are dealt with first.
MANAGEMENT RECOMMENDATIONS
- Take advantage of global Cyber Intelligence providing valuable insights on threat actor activity, detection, and mitigation techniques.
- Proactively monitor the effectiveness of risk-based information security strategy, the security controls applied, and the proper implementation of security technologies, followed by corrective actions remediations, and lessons learned.
- Consider implementing Network Traffic Analysis (NTA) and Network Detection and Response (NDR) security systems to compensate for the shortcomings of EDR and SIEM solutions.
- Detection processes are tested to ensure awareness of anomalous events. Timely communication of anomalies and continuously evolved to keep up with refined ransomware threats.
TACTICAL RECOMMENDATIONS
- Patch software/applications as soon as updates are available. Where feasible, automated remediation should be deployed since vulnerabilities are one of the top attack vectors.
- Consider using security automation to speed up threat detection, improved incident response, increased the visibility of security metrics, and rapid execution of security checklists.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defences based on the tactical intelligence provided.
- Deploy detection technologies that are behavioral anomaly-based to detect ransomware attacks and help to take appropriate measures.
- Implement a combination of security control such as reCAPTCHA (completely Automated Public Turing test to tell Computers and Humans Apart), Device fingerprinting, IP backlisting, Rate-limiting, and Account lockout to thwart automated brute-force attacks.
- Ensure email and web content filtering uses real-time blocklists, reputation services, and other similar mechanisms to avoid accepting content from known and potentially malicious sources.
Situational Awareness – Cyber News
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.
[ad_2]
Source link

