[ad_1]

Ransomware of the week
CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: MS Windows
Introduction
The CYFIRMA Research and Advisory Team has found Backups Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
Puld Ransomware
Puld is a ransomware variant associated with the MedusaLocker group. Upon infection, it encrypts files by adding a “.Puld39” extension and drops a ransom note titled “How_to_back_files.html,” demanding payment for decryption.

Screenshot of files encrypted by ransomware (Source: Surface Web)
The ransom note notifies victims that their company network has been breached, resulting in the encryption of all files and the theft of sensitive business data, including employee and customer information. The attackers demand payment in exchange for a decryption key and software, which are necessary to restore access to the encrypted files.
To prove their ability to decrypt the data, the attackers allow victims to submit up to two small files (under 2MB) for free decryption. Victims are given a five-day deadline to make contact and arrange payment. Failure to comply results in escalating consequences, including the permanent deletion of 24 files every 24 hours and the threat of leaking stolen data on the dark web or sharing it with other malicious actors.
The note strongly warns against any attempts to tamper with or independently recover the files, claiming it could result in irreversible loss. The attackers encourage victims to communicate via email or the TOX encrypted messaging platform for reliability.
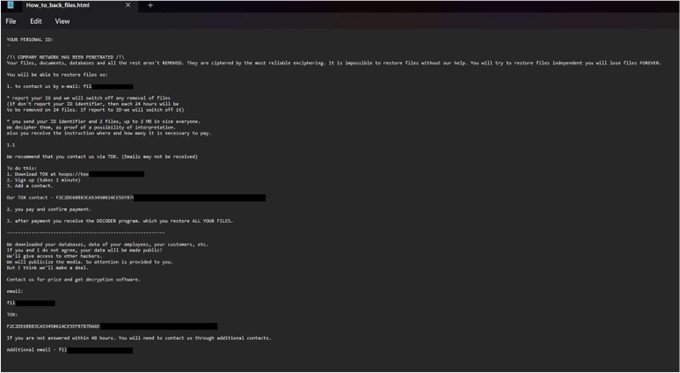
Screenshot of Puld ransomware’s text file (“How_to_back_files.html “):(Source: Surface Web)
Following are the TTPs based on the MITRE Attack Framework
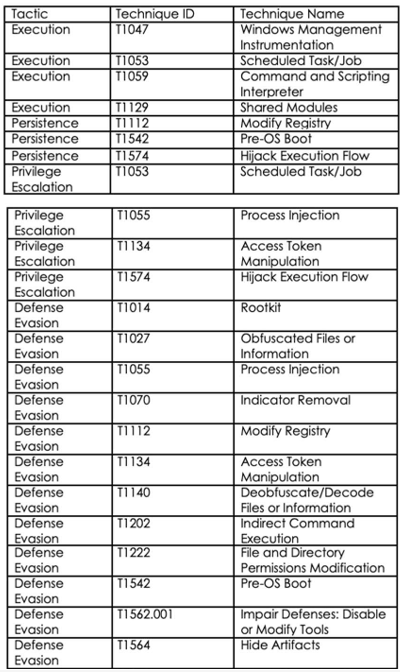
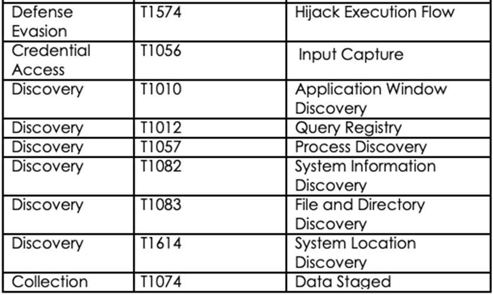
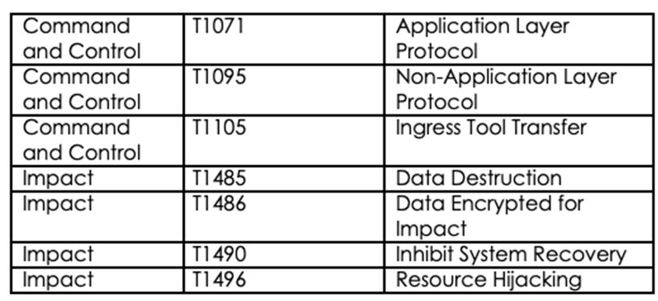
Relevancy and Insights:
- This ransomware specifically targets the widely used Windows Operating System, which is prevalent across numerous industries and
- Detect-Debug-Environment: Debugging environments are used by developers to analyze and troubleshoot The ransomware uses this technique to determine whether it is operating in a debug environment. This feature aids the ransomware in avoiding analysis and detection attempts.
- Calls to WMI: The ransomware is making calls to the Windows Management Instrumentation (WMI) WMI is a powerful tool used by many legitimate applications and services, but it can also be exploited by malware to execute commands, collect information, or perform system modifications.
- The ransomware’s attempt to delete Volume Shadow Copies (VSS) indicates a deliberate effort to hinder data recovery options for victims.
ETLM Assessment:
CYFIRMA’s analysis reveals that the Medusa Locker ransomware group, historically known for targeting enterprise environments, has released a new variant named Puld. Medusa Locker’s past focus on high-value enterprise targets suggests that this new strain, Puld, may similarly aim at critical sectors with significant assets globally.
Given Medusa Locker’s established enterprise focus and Puld’s evolving capabilities, this variant may pose a growing global cybersecurity threat, underscoring the urgent need for strengthened defenses across all industry sectors.
Sigma rule:
title: Suspicious Windows Service Tampering
tags:
-defense-evasion
-impact
-t1489 logsource:
category: process_creation product: windows
detection: selection_tools_img:
-OriginalFileName:
-‘net.exe’
-‘net1.exe’
-‘PowerShell.EXE’
-‘psservice.exe’
-‘pwsh.dll’
-‘sc.exe’
-Image|endswith:
-‘\net.exe’
-‘\net1.exe’
-‘\powershell.exe’
-‘\PsService.exe’
-‘\PsService64.exe’
-‘\pwsh.exe’
-‘\sc.exe’ selection_tools_cli:
-CommandLine|contains:
-‘ delete ‘
-‘ pause ‘ # Covers flags from: PsService and EXE
-‘ stop ‘ # Covers flags from: PsService.EXE, EXE and Sc.EXE
-‘Stop-Service ‘
-‘Remove-Service ‘
CommandLine|contains|all:
-‘config’
-‘start=disabled’ selection_services:
CommandLine|contains:
– ‘143Svc’
-‘Acronis VSS Provider’
-‘AcronisAgent’
-‘AcrSch2Svc’
-‘AdobeARMservice’
-‘AHS Service’
-‘Antivirus’
-‘Apache4’
-‘ARSM’
-‘aswBcc’
-‘AteraAgent’
-‘Avast Business Console Client Antivirus Service’
-‘avast! Antivirus’
-‘AVG Antivirus’
-‘avgAdminClient’
-‘AvgAdminServer’
-‘AVP1’
-‘BackupExec’
-‘bedbg’
-‘BITS’
-BrokerInfrastructure’
-‘CASLicenceServer’
-‘CASWebServer’
-‘Client Agent 60’
-‘Core Browsing Protection’
-‘Core Mail Protection’
-‘Core Scanning Server’
-‘DCAgent’
-‘dwmrcs’
-‘EhttpSr’
-‘ekrn’
-‘Enterprise Client Service’
-‘epag’
-‘EPIntegrationService’
-‘EPProtectedService’
-‘EPRedline’
-‘EPSecurityService’
-‘EPUpdateService’
-‘EraserSvc11710’
-‘EsgShKernel’
-‘ESHASRV’
-‘FA_Scheduler’
-‘FirebirdGuardianDefaultInstance’
-‘FirebirdServerDefaultInstance’
-‘FontCache3.0.0.0’
-‘HealthTLService’
-‘hmpalertsvc’
-‘HMS’
-‘HostControllerService’
-‘hvdsvc’
-‘IAStorDataMgrSvc’
-‘IBMHPS’
-‘ibmspsvc’
-‘IISAdmin’
-‘IMANSVC’
-‘IMAP4Svc’
-‘instance2’
-‘KAVFS’
-‘KAVFSGT’
-‘kavfsslp’
-‘KeyIso’
-‘klbackupdisk’
-‘klbackupflt’
-‘klflt’
-‘klhk’
-‘KLIF’
-‘klim6’
-‘klkbdflt’
-‘klmouflt’
-‘klnagent’
-‘klpd’
-‘kltap’
– ‘KSDE1.0.0’
-‘LogProcessorService’
-‘M8EndpointAgent’
-‘macmnsvc’
-‘masvc’
-‘MBAMService’|
-‘MBCloudEA’
-‘MBEndpointAgent’
-‘McAfeeDLPAgentService’
-‘McAfeeEngineService’
-‘MCAFEEEVENTPARSERSRV’
-‘McAfeeFramework’
-‘MCAFEETOMCATSRV530’
-‘McShield’
-‘McTaskManager’
-‘mfefire’
-‘mfemms’
-‘mfevto’
-‘mfevtp’
-‘mfewc’
-‘MMS’
-‘mozyprobackup’
-‘mpssvc’
-‘MSComplianceAudit’
-‘MSDTC’
-‘MsDtsServer’
-‘MSExchange’
-‘msftesq1SPROO’
-‘msftesql$PROD’
-‘msftesql$SQLEXPRESS’
-‘MSOLAP$SQL_2008’
-‘MSOLAP$SYSTEM_BGC’
-‘MSOLAP$TPS’
-‘MSOLAP$TPSAMA’
-‘MSOLAPSTPS
-‘MSOLAPSTPSAMA’
-‘mssecflt’
-‘MSSQ!I.SPROFXENGAGEMEHT’
-‘MSSQ0SHAREPOINT’
-‘MSSQ0SOPHOS’
-‘MSSQL’
-‘MSSQLFDLauncher$’
-‘MySQL’
-‘NanoServiceMain’
-‘NetMsmqActivator’
-‘NetPipeActivator’
-‘netprofm’
-‘NetTcpActivator’
-‘NetTcpPortSharing’
-‘ntrtscan’
-‘nvspwmi’
-‘ofcservice’
-‘Online Protection System’
-‘OracleClientCache80
-‘OracleDBConsole’
-‘OracleMTSRecoveryService’
-‘OracleOraDb11g_home1’
-‘OracleService’
-‘OracleVssWriter’
-‘osppsvc’
-‘PandaAetherAgent’
-‘PccNTUpd’
-‘PDVFSService’
-‘POP3Svc’
-‘postgresql-x64-4’
-‘POVFSService’
-‘PSUAService’
-‘Quick Update Service’
-‘RepairService’
-‘ReportServer’
-‘ReportServer$’
-‘RESvc’
-‘RpcEptMapper’
-‘sacsvr’
-‘SamSs’
-‘SAVAdminService’
-‘SAVService’
-‘ScSecSvc’
-‘SDRSVC’
-‘SearchExchangeTracing’
-‘sense’
-‘SentinelAgent’
-‘SentinelHelperService’
-‘SepMasterService’
-‘ShMonitor’
-‘Smcinst’
-‘SmcService’
-‘SMTPSvc’
-‘SNAC’
-‘SntpService’
-‘Sophos’
-‘SQ1SafeOLRService’
-‘SQL Backups’
-‘SQL Server’
-‘SQLAgent’
-‘SQLANYs_Sage_FAS_Fixed_Assets’
-‘SQLBrowser’
-‘SQLsafe’
-‘SQLSERVERAGENT’
-‘SQLTELEMETRY’
-‘SQLWriter’
-‘SSISTELEMETRY130’
-‘SstpSvc’
-‘storflt’
-‘svcGenericHost’
-‘swc_service’
-‘swi_filter’
-‘swi_service’
-‘swi_update’
-‘Symantec’
-‘sysmon’
-‘TeamViewer’
-‘Telemetryserver’
-‘ThreatLockerService’
-‘TMBMServer’
-‘TmCCSF’
-‘TmFilter’
-‘TMiCRCScanService’
-‘tmlisten’
-‘TMLWCSService’
-‘TmPfw’
-‘TmPreFilter’
-‘TmProxy’
-‘TMSmartRelayService’
-‘tmusa’
-‘Tomcat’
-‘Trend Micro Deep Security Manager’
-‘TrueKey’
-‘UFNet’
-‘UI0Detect’
-‘UniFi’
-‘UTODetect’
-‘vds’
-‘Veeam’
-‘VeeamDeploySvc’
-‘Veritas System Recovery’
-‘vmic’
-‘VMTools’
-‘vmvss’
-‘VSApiNt’
-‘VSS’
-‘W3Svc’
-‘wbengine’
-‘WdNisSvc’
-‘WeanClOudSve’
-‘Weems JY’
-‘WinDefend’
-‘wmms’
-‘wozyprobackup’
-‘WPFFontCache_v0400’
-‘WRSVC’
-‘TmProxy’
-‘TMSmartRelayService’
-‘tmusa’
-‘Tomcat’
-‘Trend Micro Deep Security Manager’
-‘TrueKey’
-‘UFNet’
-‘UI0Detect’
-‘UniFi’
-‘UTODetect’
-‘vds’
-‘Veeam’
-‘VeeamDeploySvc’
-‘Veritas System Recovery’
-‘vmic’
-‘VMTools’
-‘vmvss’
-‘VSApiNt’
-‘VSS’
-‘W3Svc’
-‘wbengine’
-‘WdNisSvc’
-‘WeanClOudSve’
-‘Weems JY’
-‘WinDefend’
-‘wmms’
-‘wozyprobackup’
-‘WPFFontCache_v0400’
-‘WRSVC’
-‘wsbexchange’
-‘WSearch’
-‘wscsvc’
-‘Zoolz 2 Service’ condition: all of selection_*
condition: all of selection_*
falsepositives:
– Administrators or tools shutting down the services due to upgrade or removal purposes. If you experience some false
positive, please consider adding filters to the parent process launching this command and not removing the entry
level: high
source: surface web
IOCs:
Kindly refer to the IOCs section to exercise control of your security systems.
STRATEGIC RECOMMENDATION
- Implement competent security protocols and encryption, authentication, or access credentials configurations to access critical systems in your cloud and local
- Ensure that backups of critical systems are maintained which can be used to restore data in case a need arises.
MANAGEMENT RECOMMENDATION
- A data breach prevention plan must be developed considering, (a) the type of data being managed by the company; (b) the remediation process; (c) where and how the data is stored; (d) if there is an obligation to notify the local
- Enable zero-trust architecture and multifactor authentication (MFA) to mitigate the compromise of credentials.
- Foster a culture of cybersecurity, where you encourage and invest in employee training so that security is an integral part of your organization.
TACTICAL RECOMMENDATION
- Update all applications/software regularly with the latest versions and security patches
- Add the Sigma rule for threat detection and monitoring which will help to detect anomalies in log events, identify and monitor suspicious
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defence based on the tactical intelligence provided.
Trending Malware of the Week [New]
Type: Botnet| Objectives: Operational Disruption, Stealing Sensitive Information, Data Exfiltration| Target Technology: Linux OS | Target Geography: Global
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “Prometei” is trending.
Prometei
Researchers have identified a new variant of Prometei that signals a renewed focus on targeting Linux systems. Originally uncovered in mid-2020, it is designed to quietly infiltrate machines and exploit them for two main purposes: stealing credentials and mining cryptocurrency, particularly Monero. What makes Prometei especially dangerous is its adaptability—new features and tools are continually being added by its operators.
The latest variant includes a backdoor that enables a wide range of malicious activities, allowing threat actors to maintain control over infected systems. It also employs techniques like domain generation for command-and-control communication and self-updating mechanisms to avoid detection and ensure long-term persistence. The malware’s modular structure means it can evolve easily, posing an ongoing threat across different platforms. As cybercriminals continue to refine Prometei, it’s becoming a more versatile and persistent tool in their arsenal.
Evolution of Prometei
The Prometei botnet has steadily evolved into a more adaptable and financially motivated threat. While its early activity focused on Windows systems, the Linux variant soon followed, and by 2025, newer versions have emerged with more advanced capabilities. These recent versions continue to pursue the botnet’s original goals while adopting stronger strategies to remain active in compromised environments.
Prometei relies on various methods to spread, including password-guessing tactics and known vulnerabilities. It’s capable of moving through internal networks and staying connected to its operators through rotating domain names and self-updating functionality. These features make the botnet difficult to track or shut down, ensuring it can stay operational even when parts of its infrastructure are blocked.
Though mining cryptocurrency remains its main purpose, Prometei is also equipped to harvest credentials and deploy additional malware when needed. Built with a modular structure, the botnet operates through independent components for each task—whether infiltration, data theft, or communication—making it easier for attackers to update or swap out specific components without interrupting overall functionality.
Attack method
Prometei’s latest attack method reveals a shift in how the botnet is delivered and executed on Linux systems. The malware is distributed through a deceptively named web link ending in a “.php” extension, masking an executable file intended to infect targets.
This file isn’t tied to any specific region, allowing wide-scale distribution from a server based in Indonesia. Although the filename suggests it’s a harmless script, the reality is much more deceptive.
The latest Prometei versions, particularly those observed in 2025, are compressed using packing techniques that make them smaller and more difficult to examine. This method conceals the true nature of the file until it’s activated on a compromised system. To further complicate detection and analysis, the malware includes a hidden configuration layer that prevents standard tools from unpacking it. Only after removing this hidden layer can researchers inspect the malware properly—and even then, reattaching the configuration is necessary for it to operate as intended.
Once active, the malware quietly gathers detailed information about the infected system, such as hardware details and how long the system has been running. It then transmits this data to a remote server under the attackers’ control. These enhancements show how Prometei continues to be refined for stealth, persistence, and adaptability, reinforcing its status as a serious and evolving cyber threat.
Following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Persistence | T1543 | Create or Modify System
Process |
|
Persistence |
T1543.002 |
Create or Modify System Process: Systemd Service |
| Privilege Escalation | T1543 | Create or Modify System
Process |
|
Privilege Escalation |
T1543.002 |
Create or Modify System Process: Systemd Service |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1070 | Indicator Removal |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion |
| Defense Evasion | T1070.006 | Indicator Removal: Timestomp |
|
Defense Evasion |
T1222 |
File and Directory Permissions Modification |
| Defense Evasion | T1564 | Hide Artifacts |
|
Defense Evasion |
T1564.001 |
Hide Artifacts: Hidden Files and Directories |
| Credential Access | T1003 | OS Credential Dumping |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1518 | Software Discovery |
|
Discovery |
T1518.001 |
Software Discovery: Security Software Discovery |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1090 | Proxy |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1105 | Ingress Tool Transfer |
INSIGHTS
- Prometei’s continued evolution highlights a broader trend in modern botnet operations—one where flexibility, resilience, and cross-platform capability are becoming Its expansion from Windows to Linux is not just a technical adaptation but a calculated move to diversify its reach into environments that are often overlooked or assumed to be more secure. This reflects a shift in attacker mindset, where previously niche systems are now seen as lucrative targets for persistent, profit-driven campaigns.
- Prometei is differentiated due to the level of autonomy built into its The use of mechanisms like dynamic domain switching and self-updating logic suggests that the botnet is designed to operate with minimal human intervention once deployed. This allows attackers to scale campaigns efficiently, without needing constant oversight. It also hints at the growing sophistication of criminal toolsets, where automation and evasion techniques are not reserved for nation- state actors alone but are now routine features in financially motivated malware.
- Prometei’s structure also reflects a high level of Each component within the malware serves a dedicated purpose, whether it’s spreading, harvesting data, or managing communication. This modular design not only improves reliability but also allows the botnet to keep functioning even if parts of it are interrupted or removed. Such organization demonstrates an intentional design built for efficiency, resilience, and continuity in operations.
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that Prometei is likely to operate with greater stealth and autonomy, making it increasingly difficult for anyone to detect its presence or trace its activities. As it evolves, it may quietly degrade system performance by consuming processing power for unauthorized tasks like mining, all while remaining hidden through self-updating and domain-switching capabilities. Its continued ability to extract sensitive information without raising alarms could lead to wider compromises across interconnected platforms and services. As more systems become targets regardless of their operating environment, Prometei’s silent persistence may result in prolonged exposure, unnoticed data leaks, and system misuse that gradually erode digital trust and stability.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
YARA Rule
rule Prometei_Botnet_Indicators
{
meta:
description = “Detects Prometei Botnet-related strings (sha256, urls)” author = “CYFIRMA”
malware_family = ” Prometei ”
strings:
// SHA-256 Hashes
$sha256_1 = “d4566c778c2c35e6162a8e65bb297c3522dd481946b81baffc15bb7d7a4fe531”
$sha256_2 = “d21c878dcc169961bebda6e7712b46adf5ec3818cc9469debf1534ffa8d74fb7”
$sha256_3 = “b1d893c8a65094349f9033773a845137e9a1b4fa9b1f57bdb57755a2a2dcb708”
$sha256_4 = “87f5e41cbc5a7b3f2862fed3f9458cd083979dfce45877643ef68f4c2c48777e”
$sha256_5 = “7a027fae1d7460fc5fccaf8bed95e9b28167023efcbb410f638c5416c6af53ff”
$sha256_6 = “67279be56080b958b04a0f220c6244ea4725f34aa58cf46e5161cfa0af0a3fb0”
$sha256_7 = “656fa59c4acf841dcc3db2e91c1088daa72f99b468d035ff79d31a8f47d320ef”
$sha256_8 = “205c2a562bb393a13265c8300f5f7e46d3a1aabe057cb0b53d8df92958500867”
$sha256_9 = “cc7ab872ed9c25d4346b4c58c5ef8ea48c2d7b256f20fe2f0912572208df5c1a”
// urls
$url1 = “http://103.41.204.104/k.php”
$url2 = “http://152.36.128.18/cgi-bin/p.cgi”
condition:
any of ($sha256_*) or any of ($url*)
}
Recommendations:
STRATEGIC:
- Maintain an up-to-date inventory of all active software used within the organization and perform regular self-audit of workstations, servers, laptops, mobile devices to identify unauthorized/ restricted software.
- Configure organization’s intrusion detection systems (IDS), intrusion prevention systems (IPS), or any network defence mechanisms in place to alert on — and upon review, consider blocking connection attempts to and from — the external IP addresses and domains listed in the appendix.
MANAGEMENT:
- Security Awareness training should be mandated for all company employees. The training should ensure that employees:
- Avoid downloading and executing files from unverified sources.
- Regularly reinforce awareness related to different cyberattacks using impersonated domains/spoofed webpages with end-users across the environment and emphasize the human weakness in mandatory information security training sessions.
- Move beyond the traditional model of security awareness towards Improved Simulation and training exercises that mimic real attack scenarios, account for behaviors that lead to a compromise, and are measured against real attacks the organization receives.
TACTICAL RECOMMENDATIONS:
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defence based on the tactical intelligence provided.
- Add the Yara rules for threat detection and monitoring which will help to detect anomalies in log events and identify and monitor suspicious
CYFIRMA’S WEEKLY INSIGHTS
1. Weekly Attack Types and Trends
Key Intelligence Signals:
- Attack Type: Ransomware Attacks, Vulnerabilities & Exploits, Data
- Objective: Unauthorized Access, Data Theft, Data Encryption, Financial Gains,
- Business Impact: Data Loss, Financial Loss, Reputational Damage, Loss of Intellectual Property, Operational Disruption.
- Ransomware – Qilin Ransomware, Dire Wolf Ransomware| Malware – Prometei
- Qilin Ransomware– One of the ransomware
- Dire Wolf Ransomware – One of the ransomware
Please refer to the trending malware advisory for details on the following: - Malware – Prometei
Behavior – Most of these malwares use phishing and social engineering techniques as their initial attack vectors. Apart from these techniques, exploitation of vulnerabilities, defense evasion, and persistence tactics are being observed.
2. Threat Actor in Focus
North Korea’s TA444 (also known as Bluenoroff, Lazarus Group) continues to evolve its tactics, with a persistent focus on targeting cryptocurrency assets and infrastructure
- Threat Actor: TA444 aka (Bluenoroff, Lazarus Group)
- Attack Type: Social engineering, Spear Phishing, Malware deployment, Credential theft, Cryptocurrency theft, Exploitation of Zero-Day Vulnerabilities, Privilege Escalation, Wiper Malware and Data Destruction, Ransomware Deployment, Persistence Mechanism, Botnet usage, Commodity malware as launchpad, Vulnerabilities &
- Objective: Espionage, Financial Gain, Network Compromise
- Target Technology: Windows, Linux, macOS, cryptocurrency wallets, video conferencing platforms (Zoom, Google Meet), Telegram, Calendly
- Target Geography: Australia, Brazil, Brunei, Canada, Chile, China, Darussalam, Democratic People’s Republic of Korea, France, Germany, Guatemala, Hongkong, India, Indonesia, Islamic Republic of Iran, Japan, Myanmar, Philippines, Poland, Republic of Korea, Russia, Thailand, United Kingdom, United States, Vietnam, Bangladesh
- Target Industries: Aerospace & Defense, Capital Markets, Consumer Finance, Cryptocurrency, Diversified Financial Services, Energy, Entertainment, Government, Hotels, Investment Trusts (REITs), Media, NGO, Real Estate, Restaurants & Leisure, Technology, Telecommunications, Thrifts and Mortgage, Banks
- Business Impact: Financial Theft, System Compromise, Operational Disruption, Reputational damage
About the Threat Actor
Since at least 2009, the Lazarus Group and its affiliated entities have been identified as a highly sophisticated advanced persistent threat (APT) group, reportedly operating under the direction of the North Korean government, as noted by the Council on Foreign Relations (CFR). Operating under multiple aliases, the group is believed to be associated with Lab 110, a unit within the Democratic People’s Republic of Korea (DPRK) military intelligence apparatus.
Lazarus Group and its affiliates are known for their advanced capabilities in rapidly developing, modifying, and evolving malware and exploits through a dedicated malware development unit. In recent years, the group has increasingly focused its activities on targeting cryptocurrency exchanges and related financial platforms.
TA444, also known as Bluenoroff, is a distinct APT subgroup under the broader Lazarus umbrella. Active since at least 2017, TA444 is a North Korean state-sponsored threat actor primarily engaged in financially motivated cyber operations. The group’s key objectives include the monetization of cyber intrusions and the execution of global espionage campaigns, with a strong emphasis on compromising cryptocurrency firms.
TTPs based on MITRE ATT&CK Framework
| Tactic | ID | Technique |
| Resource Development | T1583.001 | Acquire Infrastructure: Domains |
| Resource Development | T1583.006 | Acquire Infrastructure: Web Services |
| Resource Development | T1587.001 | Develop Capabilities: Malware |
| Resource Development | T1588.004 | Obtain Capabilities: Digital Certificates |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Initial Access | T1189 | Drive-by Compromise |
| Initial Access | T1566.002 | Phishing: Spear phishing Link |
| Execution | T1059.002 | Command and Scripting Interpreter: AppleScript |
| Execution | T1203 | Exploitation for Client Execution |
| Execution | T1204.002 | User Execution: Malicious File |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows
Command Shell |
| Execution | T1059.001 | Command and Scripting Interpreter:
PowerShell |
| Execution | T1047 | Windows Management Instrumentation |
| Persistence | T1098 | Account Manipulation |
| Persistence | T1547.001 | Boot or Logon AutoStart Execution: Registry
Run Keys / Startup Folder |
| Persistence | T1547.009 | Boot or Logon AutoStart Execution: Shortcut
Modification |
| Persistence | T1543.003 | Create or Modify System Process: Windows
Service |
| Persistence | T1543.004 | Create or Modify System Process: Launch
Daemon |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Privilege Escalation | T1134.002 | Access Token Manipulation: Create Process
with Token |
| Privilege Escalation | T1547.001 | Boot or Logon AutoStart Execution: Registry
Run Keys / Startup Folder |
| Privilege Escalation | T1547.009 | Boot or Logon AutoStart Execution: Shortcut
Modification |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows
Service |
| Privilege Escalation | T1055.001 | Process Injection: Dynamic-link Library
Injection |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Name or
Location |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1134.002 | Access Token Manipulation: Create Process
with Token |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify System
Firewall |
| Defense Evasion | T1562.004 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1070.004 | Indicator Removal on Host: File Deletion |
| Defense Evasion | T1070.006 | Indicator Removal on Host: Timestomp |
| Defense Evasion | T1036.001 | Masquerading: Invalid Code Signature |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1055.001 | Process Injection: Dynamic-link Library Injection |
| Defense Evasion | T1218.001 | Signed Binary Proxy Execution: Compiled HTML File |
| Credential Access | T1110.003 | Brute Force: Password Spraying |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Credential Access | T1555 | Credentials from Password Stores |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1012 | Query Registry |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1124 | System Time Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Lateral Movement | T1021.001 | Remote Services: Remote Desktop Protocol |
| Lateral Movement | T1021.002 | Remote Services: SMB/Windows Admin Shares |
| Collection | T1560 | Archive Collected Data |
| Collection | T1560.002 | Archive Collected Data: Archive via Library |
| Collection | T1560.003 | Archive Collected Data: Archive via Custom Method |
| Collection | T1005 | Data from Local System |
| Collection | T1074.001 | Data Staged: Local Data Staging |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1115 | Clipboard Data |
| Collection | T1113 | Screen Capture |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Command and Control | T1132.001 | Data Encoding: Standard Encoding |
| Command and Control | T1001.003 | Data Obfuscation: Protocol Impersonation |
| Command and Control | T1573.001 | Encrypted Channel: Symmetric Cryptography |
| Command and Control | T1008 | Fallback Channels |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1571 | Non-Standard Port |
| Command and Control | T1090.002 | Proxy: External Proxy |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1102 | Web Service |
|
Exfiltration |
T1048.003 |
Exfiltration Over Alternative Protocol: Exfiltration Over Unencrypted/Obfuscated Non-C2 Protocol |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |
| Impact | T1485 | Data Destruction |
| Impact | T1491.001 | Defacement: Internal Defacement |
| Impact | T1561.001 | Disk Wipe: Disk Content Wipe |
| Impact | T1561.002 | Disk Wipe: Disk Structure Wipe |
| Impact | T1496 | Resource Hijacking |
| Impact | T1657 | Financial Theft |
| Impact | T1489 | Service Stop |
| Impact | T1529 | System Shutdown/Reboot |
Latest Developments Observed
Recently, the threat actor was suspected of targeting individuals within the Web3 and cryptocurrency sectors by leveraging misleading Zoom calls that feature deep- faked representations of company executives. These calls are designed to manipulate employees into installing malware on Apple macOS devices. The initial outreach is believed to occur via external contacts on Telegram. The primary motivation behind these activities appears to be the exfiltration of sensitive information and financial gains.
ETLM Insights:
The North Korean state-sponsored threat actor Lazarus Group and its affiliated entities hold a unique position as both an advanced persistent threat (APT) and a highly sophisticated cybercriminal group. Renowned for their agility and continual evolution in tactics and techniques, these groups consistently develop novel methods to target governments, organizations, and individuals globally.
Their operations serve dual objectives: conducting cyber-espionage and executing financially motivated attacks, particularly through the theft of cryptocurrency assets. These activities are largely driven by the need to circumvent international sanctions and secure funding for North Korea’s defence programs, including missile development and nuclear technology initiatives. In addition to direct cyberattacks, the group is also known to offer Hacker-as-a-Service (HaaS) capabilities to other nation-state actors, enabling them to acquire sensitive information in exchange for financial compensation or technological support.
IOCs
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
YARA Rules
rule APT_Lazarus_DTrack_Manuscrypt
{
meta:
description = “Detects malware associated with Lazarus Group (DTrack/Manuscrypt variants)”
author = “CYFIRMA” date = “2025-06-24”
threat_group = “Lazarus Group (APT38 / TA404 / Bluenoroff)” malware_family = “DTrack, Manuscrypt”
strings:
$s1 = “dtrack_report_” ascii
$s2 = “rundll32.exe” ascii
$s3 = “regsvr32.exe” ascii
$s4 = “Kaspersky Lab” wide
$s5 = “Software\\Microsoft\\Windows\\CurrentVersion\\Run” wide
$s6 = “SCardDlgClass” wide
$s7 = “CreateToolhelp32Snapshot” ascii
$s8 = “NtQuerySystemInformation” ascii
$s9 = “cmd.exe /c” ascii
$c2_1 = “update.microsoft-support[.]org” ascii
$c2_2 = “dtrack[.]com” ascii
$c2_3 = “172.104.” ascii |
condition:
(uint16(0) == 0x5A4D)
and (1 of ($s*) or 1 of ($c2*))
}
Recommendations
Strategic
- Incorporate Digital Risk Protection (DRP) as part of the overall security posture to proactively defend against impersonations and phishing attacks.
- Deploy Zero Trust Policy that leverages tools like security information management, advanced security analytics platforms, security user behaviour analytics, and other analytics systems to help the organization’s security personnel observe in real-time what is happening within their networks so they can orient defences more intelligently.
- Block exploit-like Monitor endpoints memory to find behavioural patterns that are typically exploited, including unusual process handle requests. These patterns are features of most exploits, whether known or new. This will be able to provide effective protection against zero-day/critical exploits and more, by identifying such patterns.
Management
- Invest in user education and implement standard operating procedures for the handling of financial and sensitive data transactions commonly targeted by impersonation Reinforce this training with context-aware banners and in-line prompts to help educate users.
- Look for email security solutions that use ML- and AI-based anti-phishing technology for BEC protection to analyze conversation history to detect anomalies, as well as computer vision to analyze suspect links within emails.
Tactical
- For better protection coverage against email attacks (like spear phishing, business email compromise, or credential phishing attacks), organizations should augment built-in email security with layers that take a materially different approach to threat detection.
- Employ robust endpoint security options that will allow your IT team to identify what confidential information is being stolen, when, and through what specific channel or device.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defenses based on the tactical intelligence
- Add the YARA rules for threat detection and monitoring which will help to detect anomalies in log events, and identify and monitor suspicious activities.
3. Major Geopolitical Developments in Cybersecurity
Salt Typhoon breached North American telecom organizations
The Canadian Centre for Cyber Security and the U.S. FBI issued a joint bulletin warning that the Chinese state-sponsored group Salt Typhoon is targeting Canadian telecommunications, with at least one breach confirmed earlier this year. The bulletin notes, “In mid-February 2025, Salt Typhoon actors likely compromised three network devices belonging to a Canadian telecom company, exploiting CVE-2023-20198 to access configuration files and modifying at least one to establish a GRE tunnel for network traffic collection.”
It further states, “We assess that PRC cyber actors will likely continue targeting Canadian organizations, including telecom providers and their clients, for espionage over the next two years.”
Meanwhile, Viasat is the latest U.S. telecom identified as a victim of Salt Typhoon’s cyberespionage campaign. Viasat reported, “Following an investigation with a third- party cybersecurity partner, we found no evidence of customer impact from unauthorized access via a compromised device.” The company noted the incident has been remediated, with no recent activity detected, but could not disclose details of the ongoing government investigation. The campaign, which emerged last year, also targeted Verizon, AT&T, and Lumen, collecting tens of millions of phone records.
ETLM Assessment:
Last year campaigns by Volt Typhoon and Salt Typhoon have been focused on the countries surrounding the South China Sea, where China presses territorial claims on countries like the Philippines, Vietnam or Indonesia, as well as on the United States, with which China is in conflict over primacy in the region and global affairs as a whole. Guam; a US territory in the Western Pacific that is home to significant US military bases, has been especially targeted. Chinese hackers have been lately mainly focusing on the defense industrial base, successfully compromising the networks of contractors to the Pentagon’s
U.S. Transportation Command 20 times in a single year, while many other incursions have probably never been found. The increasingly assertive Chinese posturing likely means that Beijing’s hackers are trying to position themselves in a way that could try to paralyze
U.S. critical infrastructure in case of an eruption of conflict between the two countries over the issue of Taiwanese or Philippine waters. An attempt to induce societal panic in their adversary in case of conflict is an inherent part of Chinese military doctrine and targeting of telecoms could affect U.S. military operations in significant ways.
The US expects a heightened risk of Iranian cyberattacks
The U.S. Department of Homeland Security has issued a warning about an increased risk of Iranian cyberattacks following U.S. military strikes on Iran’s nuclear facilities. In a National Terrorism Advisory System Bulletin released yesterday, the ministry stated, “Pro- Iranian hacktivists are likely to conduct low-level cyberattacks against U.S. networks, and Iranian government-affiliated cyber actors may also target U.S. networks.” The bulletin noted that both hacktivists and Iranian state-linked actors often exploit poorly secured
U.S. networks and internet-connected devices for disruptive cyberattacks.
ETLM Assessment:
Amid the ongoing hot stage of the war between Israel and Iran, a parallel cyber conflict is unfolding—one that remains largely overshadowed by the spectacle of missile strikes and air raids. Yet this digital battlefield is just as strategically significant. Both nations are using cyber operations to sabotage infrastructure, disrupt military planning, and undermine financial networks. While the physical war dominates headlines so far, the cyber war may prove more enduring, with long-term impacts on critical systems and civilian life that are less visible but strongly contributing to the efforts of both nations.
Iran’s cyberattacks have yielded mixed results, often with exaggerated or fabricated impacts to heighten psychological effects. Overhyping these incidents risks amplifying the attackers’ influence. Still, individual businesses could face serious consequences and should adopt ransomware prevention measures to mitigate risks.
4. Rise in Malware/Ransomware and Phishing
The Qilin Ransomware Impacts the RMZ Oil Field
- Attack Type: Ransomware
- Target Industry: Manufacturing and Healthcare
- Target Geography: Japan
- Ransomware: Qilin Ransomware
- Objective: Data Theft, Data Encryption, Financial Gains
- Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Japan, Nipro Medical Corporation (https[:]//nipro[.]com/), was compromised by Qilin Ransomware. Nipro Medical Corporation, headquartered in Bridgewater, is a subsidiary of Nipro Corporation, headquartered in Osaka, Japan. Nipro Corporation is a Japanese multinational company specializing in medical devices, pharmaceutical products, and pharmaceutical packaging. The company operates globally, with subsidiaries and offices in more than 56 countries worldwide. The compromised data includes financial documents, export commercial invoices, purchase orders, trial balance reports, and other confidential and sensitive information related to the organization. The total volume of the exposed data is approximately 400 GB

Relevancy & Insights:
- In recent campaigns, Qilin employed sophisticated malware loaders such as NETXLOADER, a .NET-based loader that stealthily deploys additional payloads like Agenda ransomware and SmokeLoader. This loader is protected by .NET Reactor 6, making it difficult to The ransomware itself is Rust-based, offering enhanced evasion and customization capabilities for Windows, Linux, and ESXi systems. A new variant named Qilin.B has been spotted, featuring stronger encryption and better evasion techniques.
- Recently, we observed that Qilin now offers a “Call Lawyer” function on its affiliate panel, allowing affiliates to request legal consultation during ransom negotiations. This tactic is designed to increase pressure on victims by introducing legal risks and potentially inflating the ransom The presence of legal counsel in negotiations can intimidate organizations, making them more likely to pay to avoid legal complications.
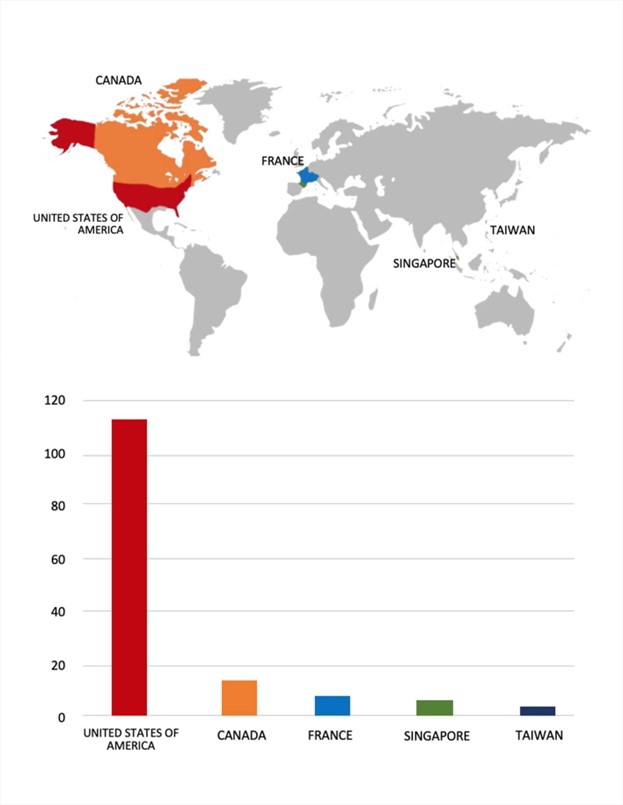
- The Qilin Ransomware group primarily targets countries such as the United States of America, Canada, France, Singapore, and Taiwan.
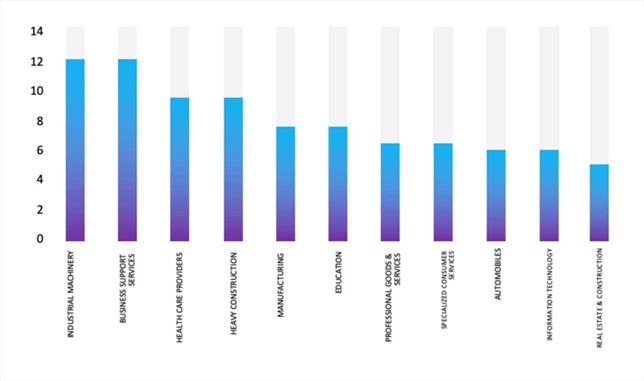
- The Qilin Ransomware group primarily targets industries, including Industrial Machinery, Business Support Services, Health Care Providers, Heavy Construction, and Manufacturing.
- Based on the Qilin Ransomware victims list from 1stJan 2025 to 25th June 2025, the top 5 Target Countries are as follows:
- The Top 10 Industries most affected by the Qilin Ransomware victims list from 1st Jan 2025 to 25th June 2025 are as follows:
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and focus on speed and evasion, make it a particularly dangerous actor.
Dire Wolf Ransomware Impacts Thairung Group
- Attack Type: Ransomware
- Target Industry: Automotive Manufacturing
- Target Geography: Thailand
- Ransomware: Dire Wolf Ransomware
- Objective: Data Theft, Data Encryption, Financial Gains
- Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Thailand, Thairung Group (https[:]//www[.]thairunggroup[.]co[.]th), was compromised by Dire Wolf Ransomware. Thairung Group is a comprehensive automotive and mobility solutions provider in Thailand. They span manufacturing, sales, rentals, property, hospitality, and service support. The compromised data includes the core business database, financial records, commercial contracts, sales documents, and customer information. The total volume of the exposed data is approximately 1 terabyte
Relevancy & Insights:
- Dire Wolf is a newly emerged ransomware group that surfaced in May It operates an onion-based data leak site (DLS) where it posts information about its victims, including file trees, sample files, and descriptions of stolen data.
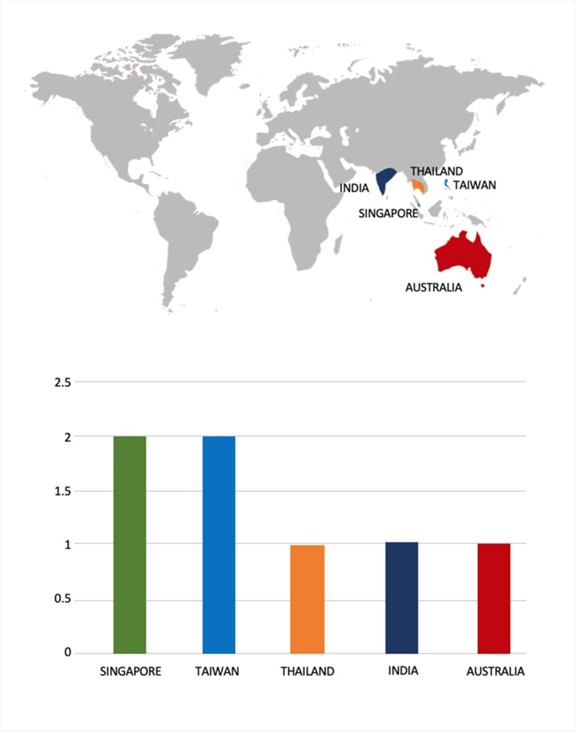
- The Dire Wolf Ransomware group primarily targets countries such as Singapore, Taiwan, Thailand, India, and Australia.
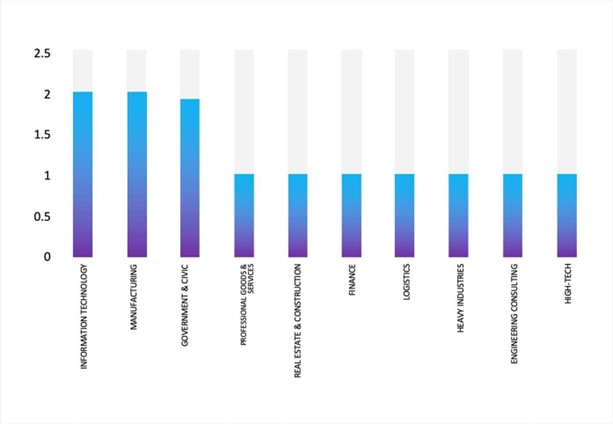
- The Dire Wolf Ransomware group primarily targets industries, including Manufacturing, Industrial Machinery, Information Technology, Business Support Services, and Heavy Construction.
- Based on the Dire Wolf Ransomware victims list from 1stJan 2025 to 25th June 2025, the top 5 Target Countries are as follows:
- The Top 10 Industries most affected by the Dire Wolf Ransomware victims list from 1st Jan 2025 to 25th June 2025 are as follows:
ETLM Assessment:
According to CYFIRMA’s assessment, Dire Wolf is a newly identified ransomware group that emerged in May 2025, distinguished by its use of double-extortion tactics combining data encryption with data theft and threats of public exposure via an onion- based leak site. The group appears to operate solely for financial gains, without ideological motives. Its emergence highlights the evolving nature of ransomware threats in 2025, particularly the increased reliance on data exfiltration to amplify extortion efforts. These activities reinforce the urgent need for strong cybersecurity defenses and effective incident response strategies across all sectors.
5. Vulnerabilities and Exploits
Vulnerability in TeamViewer
- Attack Type: Vulnerabilities & Exploits
- Target Technology: Client/Desktop applications
- Vulnerability: CVE-2025-36537
- CVSS Base Score: 0 Source
- Vulnerability Type: Incorrect Permission Assignment for Critical Resource
- Summary: The vulnerability allows a local user to escalate privileges on the
Relevancy & Insights:
The vulnerability exists due to incorrect permission assignment for critical resource within the Remote Management features: Backup, Monitoring, and Patch Management.
Impact:
A local unprivileged user can delete arbitrary files with SYSTEM privileges by leveraging the MSI rollback mechanism and escalating privileges on the system.
Affected Products:
https[:]//www[.]teamviewer[.]com/en/resources/trust- center/security-bulletins/tv-2025-1002/?
Recommendations:
- Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
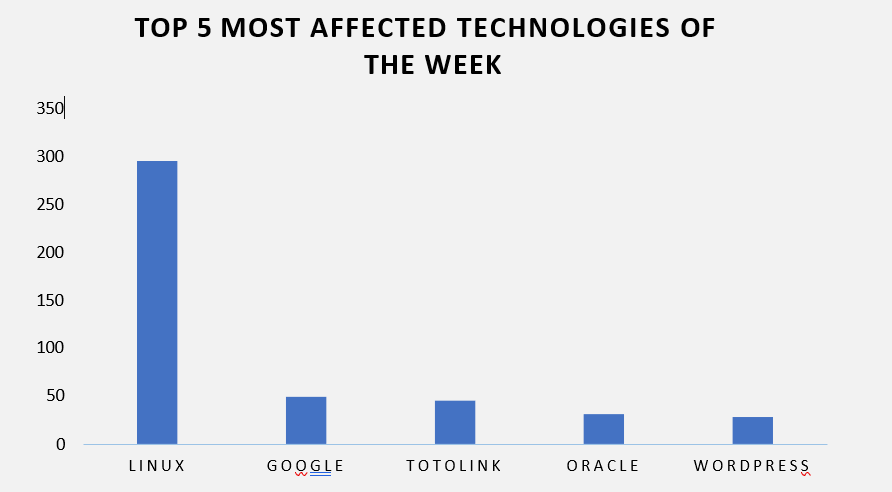
ETLM Assessment
Vulnerability in TeamViewer can pose significant threats to user privacy and security. This can impact various industries globally, including technology, healthcare, finance, and remote support services. Ensuring the security of TeamViewer is crucial for maintaining the integrity and protection of users’ data and systems worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding remote access, desktop sharing, and IT support operations across different geographic regions and sectors.
6. Latest Cyber-Attacks, Incidents, and Breaches
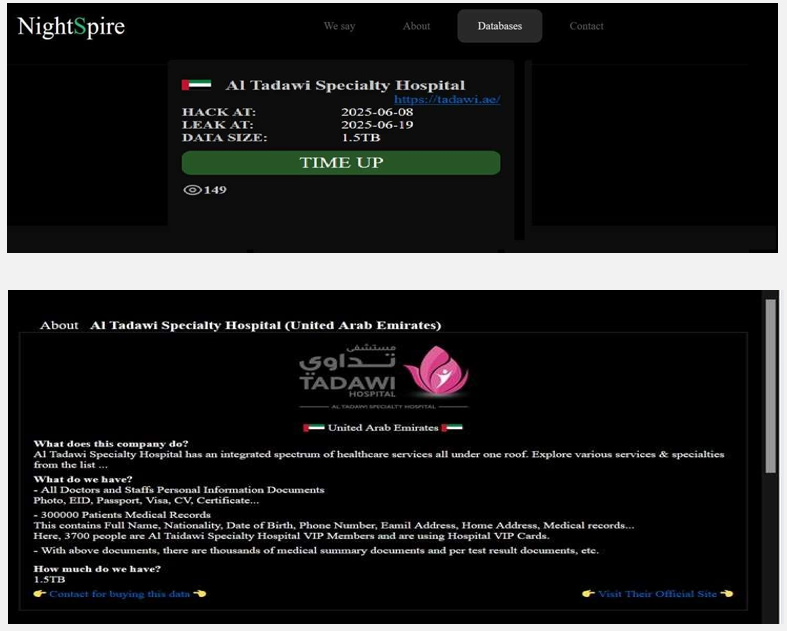
NightSpire Ransomware attacked and published the data of the Al Tadawi Specialty Hospital
- Threat Actor: NightSpire Ransomware
- Attack Type: Ransomware
- Objective: Data Leak, Financial Gains
- Target Technology: Web Applications
- Target Industry: Healthcare services
- Target Geography: United Arab Emirates (UAE)
- Business Impact: Operational Disruption, Data Loss, Financial Loss, Potential Reputational Damage
Summary:
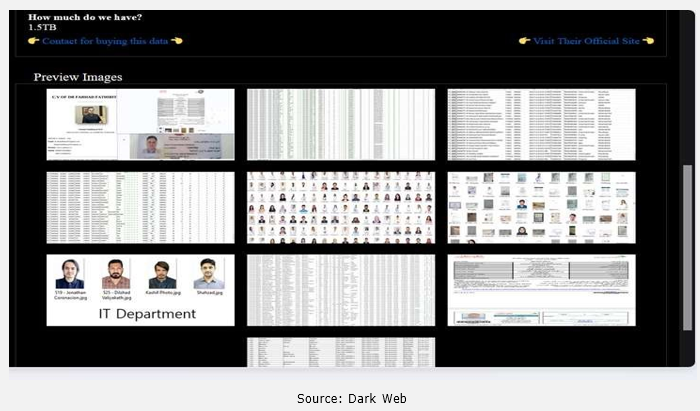
Recently, we observed that NightSpire Ransomware attacked and published the data of the Al Tadawi Specialty Hospital(https[:]//tadawi[.]ae/) on its dark web website. Al Tadawi Specialty Hospital is a multi-specialty healthcare provider based in Dubai, United Arab Emirates. The hospital is recognized for its integrated spectrum of healthcare services, offering comprehensive care across various specialties including gynaecology, cardiology, dermatology, pediatrics, and dentistry all under one roof. The facility emphasizes luxury, safe medical care, and patient-centered service, with a focus on providing accessible, high-quality healthcare for both adults and children. The data leak resulting from the ransomware attack includes comprehensive personal information of all doctors and staff, such as identification documents, photographs, Emirates ID, passport and visa copies, CVs, and professional certificates.
Additionally, the breach exposed the medical records of approximately 3 million patients. These records contain sensitive details including full names, nationalities, dates of birth, email addresses, home addresses, and medical histories.
Among the affected individuals, 3,700 are VIP members of Al Tadawi Specialty Hospital who use exclusive VIP cards. The compromised data set also includes thousands of medical summary reports and individual test result documents. The total size of the data compromised is approximately 1.5 TB.
Relevancy & Insights:
- NightSpire employs a double extortion strategy, encrypting data and threatening to leak stolen information unless a ransom is This approach is typical of modern ransomware groups and adds pressure on victims to comply with demands.
- NightSpire’s operations show strong influences from existing Ransomware-as-a- Service (RaaS) models, suggesting they might be an emerging group or a rebrand of an existing actor.
ETLM Assessment:
According to CYFIRMA’s assessment, NightSpire is a new ransomware group that emerged in early 2025, marking itself as a formidable player in the rapidly evolving ransomware landscape. Despite its recent appearance, NightSpire has already gained attention for its aggressive tactics and well-structured operations.
7. Data Leaks
BEAM Technologies Japan Data Advertised on a Leak Site
- Attack Type: Data Leak
- Target Industry: Semiconductor
- Target Geography: Japan
- Objective: Financial Gains
- Business Impact: Data Loss, Reputational Damage
Summary:
The CYFIRMA Research team observed a data leak related to BEAM Technologies Japan(https[:]//beam-tec[.]jp/) in an underground forum. BEAM Technologies Inc. is a Japanese startup specializing in the design and development of advanced optical semiconductor light sources, with a particular focus on Far-UVC emitters operating in the 200–230 nm wavelength range. The company’s core technology was developed in collaboration with RIKEN, one of Japan’s leading research institutes, and BEAM Technologies is officially recognized as a RIKEN-origin startup. The data leak includes confidential and sensitive information about the organization. The data leak is attributed to the threat actor “303.”
Thailand’s Cyber Police Access Advertised on a Leak Site
- Attack Type: Access sale
- Target Industry: Government, Law Enforcement
- Target Geography: Thailand
- Objective: Data Theft, Financial Gains
- Business Impact: Data Loss, Reputational Damage
Summary:
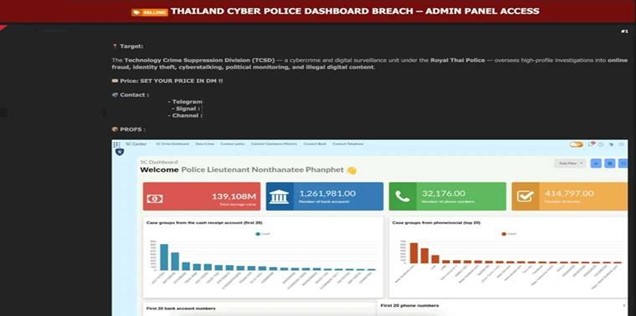
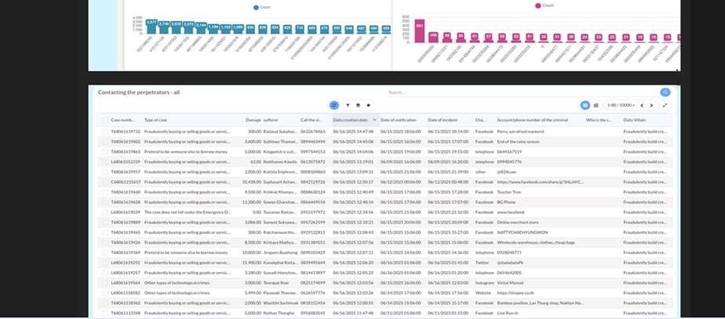
The CYFIRMA Research team observed an access sale related to Thailand’s Cyber Police in an underground forum. A threat actor has allegedly breached the internal systems of Thailand’s Technology Crime Suppression Division (TCSD) and is attempting to sell access on a dark web forum. The TCSD is a crucial unit of the Royal Thai Police, responsible for investigating a wide range of cybercrimes, including online fraud, identity theft, and illegal digital content. The division’s role in national security and digital surveillance makes this alleged breach particularly alarming, as it could compromise sensitive law enforcement data and ongoing investigations.
The seller posted screenshots purportedly showing administrative access to a “5C Center” dashboard. The images display highly sensitive information, suggesting a deep compromise of the cyber police’s operational data. The alleged breach appears to provide access to a vast database of criminal cases and citizen information. The exposure of such data could not only hamper police operations but also place victims and informants at significant risk.
The allegedly leaked data includes:
- Total damage value from reported crimes, amounting to 108M.
- Over 2 million bank account numbers.
- Over 32,000 phone
- More than 414,000 case stories or
- Detailed case files including type of case, financial damage, and personal information of individuals involved.
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor identified as “303” has been implicated in several data breaches, with reliable sources confirming their role in unauthorized system access and the trafficking of stolen data on dark web marketplaces. Their continued operations reflect the dynamic and persistent nature of cyber threats emerging from the dark web. These incidents emphasize the critical need for organizations to enhance their cybersecurity frameworks by adopting continuous monitoring, leveraging threat intelligence, and deploying proactive defense measures to safeguard sensitive information.
Recommendations: Enhance the cybersecurity posture by:
- Updating all software products to their latest versions is essential to mitigate the risk of vulnerabilities being
- Ensure proper database configuration to mitigate the risk of database-related
- Establish robust password management policies, incorporating multi-factor authentication and role-based access to fortify credential security and prevent unauthorized access.
8. Other Observations
The CYFIRMA Research team observed that a threat actor has allegedly leaked a massive trove of sensitive customer and payment data implicating several major financial, telecommunications, and technology firms across Asia. The data leak reportedly stems from a dispute over a penetration test conducted on RedDotPayment, a major Singapore-based payment gateway owned by global fintech giant PayU. The actor claims they are now selling the data after the company refused to honor a prior agreement. The breach potentially affects customers of RedDotPayment and other major companies, including Thailand’s fifth-largest bank, Krungsri (Bank of Ayudhya), the state-owned National Telecom of Thailand, and the Taiwanese online security and payment solutions firm, HiTRUST Inc.
The implicated companies are significant players in their respective markets. RedDotPayment is a critical component of the e-commerce infrastructure in Southeast Asia, processing online transactions for a vast network of merchants. The alleged involvement of Krungsri, a systemically important bank in Thailand, and National Telecom, a major Thai telecommunications provider, widens the potential impact to a large base of banking and telecom customers. Furthermore, the inclusion of HiTRUST, a company specializing in online transaction security, is particularly concerning. Given the nature of the exposed data, this incident poses a severe risk of financial fraud, identity theft, and other malicious activities targeting the affected individuals.
The leaked data samples appear to be raw transaction records containing highly sensitive personal and financial information. If the full database is as comprehensive as the samples suggest, the consequences for consumers could be severe. An analysis of the allegedly leaked information indicates it includes the following:
- Full Customer Names
- Contact Information (Email and Phone Numbers)
- Complete Credit Card Numbers
- Credit Card Expiry Dates
- Credit Card CVV Security Codes
- Transaction Details (Amount, Currency, Merchant Name)
- Customer’s IP Address and Browser Information
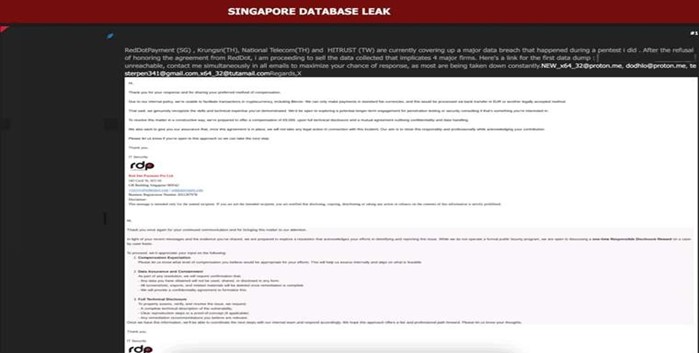
Source: Underground Forums
STRATEGIC RECOMMENDATIONS
- Attack Surface Management should be adopted by organisations, ensuring that a continuous closed-loop process is created between attack surface monitoring and security testing.
- Delay a unified threat management strategy – including malware detection, deep learning neural networks, and anti-exploit technology – combined with vulnerability and risk mitigation processes.
- Incorporate Digital Risk Protection (DRP) in the overall security posture that acts as a proactive defence against external threats targeting unsuspecting customers.
- Implement a holistic security strategy that includes controls for attack surface reduction, effective patch management, and active network monitoring, through next-generation security solutions and a ready-to-go incident response
- Create risk-based vulnerability management with deep knowledge about each asset. Assign a triaged risk score based on the type of vulnerability and criticality of the asset to help ensure that the most severe and dangerous vulnerabilities are dealt with first.
MANAGEMENT RECOMMENDATIONS
- Take advantage of global Cyber Intelligence providing valuable insights on threat actor activity, detection, and mitigation techniques.
- Proactively monitor the effectiveness of risk-based information security strategy, the security controls applied, and the proper implementation of security technologies, followed by corrective actions remediations, and lessons learned.
- Consider implementing Network Traffic Analysis (NTA) and Network Detection and Response (NDR) security systems to compensate for the shortcomings of EDR and SIEM
- Detection processes are tested to ensure awareness of anomalous Timely communication of anomalies and continuously evolved to keep up with refined ransomware threats.
TACTICAL RECOMMENDATIONS
- Patch software/applications as soon as updates are available. Where feasible, automated remediation should be deployed since vulnerabilities are one of the top attack vectors.
- Consider using security automation to speed up threat detection, improved incident response, increased the visibility of security metrics, and rapid execution of security checklists.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defences based on the tactical intelligence
- Deploy detection technologies that are behavioral anomaly-based to detect ransomware attacks and help to take appropriate measures.
- Implement a combination of security control such as reCAPTCHA (completely Automated Public Turing test to tell Computers and Humans Apart), Device fingerprinting, IP backlisting, Rate-limiting, and Account lockout to thwart automated brute-force attacks.
- Ensure email and web content filtering uses real-time blocklists, reputation services, and other similar mechanisms to avoid accepting content from known and potentially malicious sources.
Situational Awareness – Cyber News
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
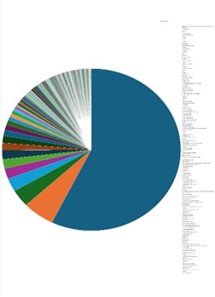
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.
[ad_2]
Source link

