[ad_1]

Ransomware of the week
CYFIRMA Research and Advisory Team would like to highlight ransomware trends and insights gathered while monitoring various forums. This includes multiple – industries, geography, and technology – that could be relevant to your organization.
Type: Ransomware
Target Technologies: Windows
Introduction
CYFIRMA Research and Advisory Team has found RedFox Ransomware while monitoring various underground forums as part of our Threat Discovery Process.
RedFox Ransomware
RedFox is a newly identified ransomware strain that encrypts files and appends both a unique victim ID and the “.redfox” extension. Upon infection, it drops a ransom note titled “README.TXT,” which outlines payment instructions and contact details, including a Session messenger ID and an email address

Screenshot of files encrypted by ransomware (Source: Surface Web)
The note urges victims to make contact within 12 hours, promising a ransom reduction of 30–50% for early communication. It threatens to leak or sell sensitive data—such as emails, certificates, payment records, staff details, and financial documents—if the ransom remains unpaid. Additionally, the attackers warn they may publicize the incident to damage the organization’s reputation. They claim that, upon receiving payment, a decryption tool will be provided within 30 minutes. The tone of the message combines urgency with coercion, pressuring victims into prompt payment by exploiting both financial and reputational risk.
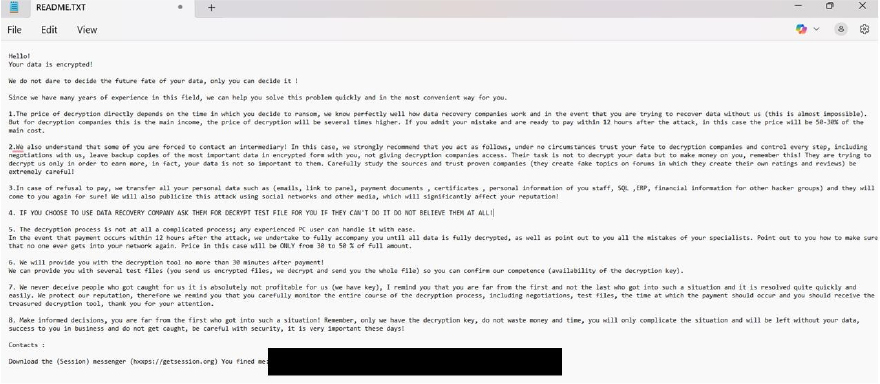
The appearance of RedFox’s text file (“README.TXT”) (Source: Surface Web)
Following are the TTPs based on the MITRE Attack Framework
| Tactic | Technique ID | Technique Name |
| Execution | T1047 | Windows Management Instrumentation |
| Execution | T1059 | Command and Scripting Interpreter |
| Execution | T1129 | Shared Modules |
| Persistence | T1112 | Modify Registry |
| Persistence | T1542.003 | Pre-OS Boot: Bootkit |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Persistence | T1574 | Hijack Execution Flow |
| Privilege Escalation | T1055 | Process Injection |
| Privilege Escalation | T1134 | Access Token Manipulation |
| Privilege Escalation | T1543.003 | Create or Modify System Process: Windows Service |
| Privilege Escalation | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder |
| Privilege Escalation | T1548 | Abuse Elevation Control Mechanism |
| Privilege Escalation | T1574 | Hijack Execution Flow |
| Defense Evasion | T1006 | Direct Volume Access |
| Defense Evasion | T1014 | Rootkit |
| Defense Evasion | T1027.005 | Obfuscated Files or Information: Indicator Removal from Tools |
| Defense Evasion | T1036 | Masquerading |
| Defense Evasion | T1055 | Process Injection |
| Defense Evasion | T1070 | Indicator Removal |
| Defense Evasion | T1112 | Modify Registry |
| Defense Evasion | T1134 | Access Token Manipulation |
| Defense Evasion | T1222 | File and Directory Permissions Modification |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion |
| Defense Evasion | T1542.003 | Pre-OS Boot: Bootkit |
| Defense Evasion | T1548 | Abuse Elevation Control Mechanism |
| Defense Evasion | T1562.001 | Impair Defenses: Disable or Modify Tools |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories |
| Defense Evasion | T1574 | Hijack Execution Flow |
| Credential Access | T1056.001 | Input Capture: Keylogging |
| Credential Access | T1552.001 | Unsecured Credentials: Credentials In Files |
| Discovery | T1007 | System Service Discovery |
| Discovery | T1010 | Application Window Discovery |
| Discovery | T1016 | System Network Configuration Discovery |
| Discovery | T1033 | System Owner/User Discovery |
| Discovery | T1049 | System Network Connections Discovery |
| Discovery | T1057 | Process Discovery |
| Discovery | T1083 | File and Directory Discovery |
| Discovery | T1087 | Account Discovery |
| Discovery | T1135 | Network Share Discovery |
| Discovery | T1497 | Virtualization/Sandbox Evasion |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery |
| Discovery | T1614.001 | System Location Discovery: System Language Discovery |
| Collection | T1005 | Data from Local System |
| Collection | T1056.001 | Input Capture: Keylogging |
| Collection | T1074 | Data Staged |
| Collection | T1114 | Email Collection |
| Command and Control | T1071 | Application Layer Protocol |
| Command and Control | T1095 | Non-Application Layer Protocol |
| Command and Control | T1105 | Ingress Tool Transfer |
| Command and Control | T1573 | Encrypted Channel |
| Impact | T1485 | Data Destruction |
| Impact | T1486 | Data Encrypted for Impact |
| Impact | T1489 | Service Stop |
| Impact | T1496 | Resource Hijacking |
Relevancy and Insights:
- This ransomware specifically targets the widely used Windows Operating System, which is prevalent across numerous industries and organizations.
- Detect-Debug-Environment: Debugging environments are used by developers to analyze and troubleshoot software. The ransomware uses this technique to determine whether it is operating in a debug environment. This feature aids the ransomware in avoiding analysis and detection attempts.
- Calls to WMI: The ransomware is making calls to the Windows Management Instrumentation (WMI) framework. WMI is a powerful tool used by many legitimate applications and services, but it can also be exploited by malware to execute commands, collect information, or perform system modifications.
- Ransomware utilizes extended sleep intervals to evade detection by security software, enabling it to operate stealthily and increasing the likelihood of completing file encryption before being identified.
ETLM Assessment:
CTFIRMA’s assessment with available data suggests that RedFox ransomware is likely to evolve with enhanced anti-analysis capabilities, broader targeting of enterprise systems, and greater reliance on stealth techniques such as extended sleep intervals and WMI abuse. Its coercive ransom tactics and emphasis on reputational damage hint at future campaigns aimed at sectors with low tolerance for operational disruption. Continued innovation in evasion methods and multi-stage persistence mechanisms indicates a sustained threat to Windows-based infrastructures across diverse industries.
Sigma rule:
title: Uncommon File Created In Office Startup Folder tags:
– attack.resource-development
– attack.t1587.001 logsource:
product: windows category: file_event
detection: selection_word_paths:
– TargetFilename|contains: ‘\Microsoft\Word\STARTUP’
– TargetFilename|contains|all:
– ‘\Office’
– ‘\Program Files’
– ‘\STARTUP’
filter_exclude_word_ext:
TargetFilename|endswith:
– ‘.docb’ # Word binary document introduced in Microsoft Office 2007
– ‘.docm’ # Word macro-enabled document; same as docx, but may contain macros and scripts
– ‘.docx’ # Word document
– ‘.dotm’ # Word macro-enabled template; same as dotx, but may contain macros and scripts
– ‘.mdb’ # MS Access DB
– ‘.mdw’ # MS Access DB
– ‘.pdf’ # PDF documents
– ‘.wll’ # Word add-in
– ‘.wwl’ # Word add-in selection_excel_paths:
– TargetFilename|contains: ‘\Microsoft\Excel\XLSTART’
– TargetFilename|contains|all:
– ‘\Office’
– ‘\Program Files’
– ‘\XLSTART’
filter_exclude_excel_ext: TargetFilename|endswith:
– ‘.xll’
– ‘.xls’
– ‘.xlsm’
– ‘.xlsx’
– ‘.xlt’
– ‘.xltm’
– ‘.xlw’ filter_main_office_click_to_run:
Image|contains: ‘:\Program Files\Common Files\Microsoft Shared\ClickToRun\’
Image|endswith: ‘\OfficeClickToRun.exe’
filter_main_office_apps: Image|contains:
– ‘:\Program Files\Microsoft Office\’
– ‘:\Program Files (x86)\Microsoft Office\’ Image|endswith:
– ‘\winword.exe’
– ‘\excel.exe’
condition: ((selection_word_paths and not filter_exclude_word_ext) or (selection_excel_paths and not filter_exclude_excel_ext)) and not 1 of filter_main_*
falsepositives:
– False positive might stem from rare extensions used by other Office utilities. level: high(Source: Surface Web)
STRATEGIC RECOMMENDATION
- Implement competent security protocols and encryption, authentication, or access credentials configurations to access critical systems in your cloud and local environments.
- Ensure that backups of critical systems are maintained which can be used to restore data in case a need arises.
MANAGEMENT RECOMMENDATION
- A data breach prevention plan must be developed considering, (a) the type of data being managed by the company; (b) the remediation process; (c) where and how the data is stored; (d) if there is an obligation to notify the local authority.
- Enable zero-trust architecture and multifactor authentication (MFA) to mitigate the compromise of credentials.
- Foster a culture of cybersecurity, where you encourage and invest in employee training so that security is an integral part of your organization.
TACTICAL RECOMMENDATION
- Update all applications/software regularly with the latest versions and security patches alike.
- Add the Sigma rule for threat detection and monitoring which will help to detect anomalies in log events, identify and monitor suspicious activities.
Trending Malware of the Week
Type: Remote Access Trojan | Objectives: Espionage, Data Theft, Remote Access, Data Exfiltration | Target Technology: Windows OS| Target Geography: Russia
CYFIRMA collects data from various forums based on which the trend is ascertained. We identified a few popular malware that were found to be distributed in the wild to launch cyberattacks on organizations or individuals.
Active Malware of the week
This week “PureRAT” is trending.
PureRAT
Researchers have uncovered a significant rise in cyberattacks targeting Russian organizations, driven by a malware known as PureRAT. First identified in mid-2022, PureRAT is part of a growing trend in Malware-as-a-Service offerings, meaning it can be purchased and used by anyone with malicious intent. While the campaign targeting Russian businesses has been active since March 2023, the beginning of 2025 has marked a significant shift—with attack volumes rising fourfold compared to the same period in 2024. This surge underscores the growing risks posed by accessible and scalable malware services in today’s cyber threat landscape.
Attack Method
The attackers behind the PureRAT campaign are relying on a familiar but effective method: spam emails carrying malicious attachments. These emails typically include a RAR archive or a link to one, disguised with file names that appear routine—often mimicking accounting-related terms or document titles. Common keywords include variations like “doc,” “akt,” “sverka,” “buh,” and “oplata,” designed to trick recipients into thinking the files are legitimate. In many cases, the files use a double extension, such as .pdf.rar, to appear less suspicious at first glance and increase the chances of being opened.
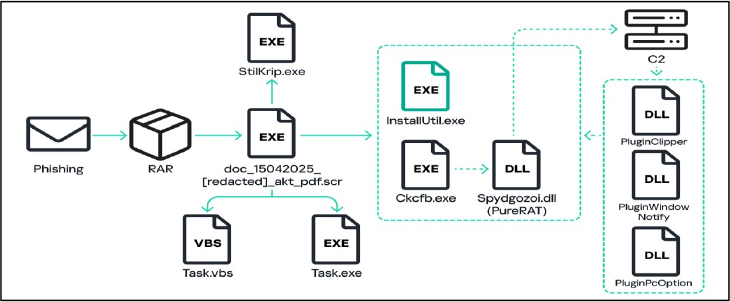
Fig: Infection Chain
The attack begins with a deceptive email containing a seemingly harmless archive file, often disguised as a PDF document. When the user opens it, the file secretly installs itself on the system under the name Task.exe and sets up a script to ensure it runs automatically whenever the computer starts. In the background, additional hidden files are unpacked and executed, gradually setting the stage for the full infection. As the process unfolds, the malware quietly connects to a remote command server using encrypted communication. It sends key information about the infected system—such as the device ID, OS version, installed antivirus, user and computer name, and more—back to the attackers. In return, the server sends back a set of instructions along with additional tools designed to expand the malware’s capabilities. While PureRAT supports a wide range of these add-ons, researchers observed the following three specific modules (plugins) being used in this campaign.
- PluginPcOption
- PluginWindowNotify
- PluginClipper
PluginPcOption
This module enables the attacker to control basic system functions on the infected machine. It can delete itself, restart the malware, or even shut down or reboot the entire computer. These actions are likely used to maintain stealth or disrupt system use when needed.
PluginWindowNotify
This module acts as a silent observer. It monitors the names of active windows and looks for specific keywords linked to financial services or sensitive terms like “password,” “bank,” or “WhatsApp.” When a match is found, it takes a screenshot and sends the image—along with the matching keyword and window title—to the attackers. This functionality helps alert the botnet operator in real time when the victim begins interacting with a financial service. Once notified, the attacker can
immediately connect to the infected system through remote desktop mode, gaining access to the session to potentially steal funds or perform other malicious actions.
PluginClipper
This module monitors the clipboard for text resembling cryptocurrency wallet addresses. When it finds one, it silently replaces it with an attacker-controlled address and captures a screenshot. The original and substituted addresses, along with the screenshot, are then sent to the command server. This tactic enables cybercriminals to redirect cryptocurrency transactions without the victim’s knowledge. Although this function is more commonly associated with broad opportunistic attacks, it appears to be part of PureRAT’s standard toolkit and was left active even in this targeted campaign.
While only these three plugins were active in the current campaign, PureRAT is capable of much more. Its complete arsenal includes tools for downloading files, accessing webcams and microphones, logging keystrokes, and taking full control of infected systems—making it a powerful threat in the hands of cybercriminals.
PureCrypter & PureLogs: Expanding the Threat Beyond Remote Access
The infection chain becomes more covert after the initial infection. The malware silently loads a hidden component called StilKrip.exe, which acts as the first stage of PureCrypter, a custom loader developed by the operators behind PureRAT. StilKrip.exe downloads a second-stage payload disguised as a .wav file to evade detection. Instead of writing files to disk, it decrypts and executes the payload directly in memory, minimizing its footprint. StilKrip.exe is then copied to the system’s AppData directory and set to auto-start via a VBS script. It triggers additional components, eventually launching PureLogs, an advanced stealer module. Once active, PureLogs connects to its command-and-control server to download its main module and begin harvesting sensitive information.
PureLogs targets a broad range of applications, including browsers, email clients, FTP tools, messaging apps, VPNs, and crypto wallets. It also keeps an eye on browser extensions tied to password managers and digital assets. What makes PureLogs especially dangerous is its secondary role as a downloader—it can fetch and launch malicious files and exfiltrate documents on command. For organizations, this combination of stealth, persistence, and multi-functionality represents a serious risk to data security and system integrity.
INSIGHTS
- PureRAT’s resurgence signals a broader shift in how threat actors are blending accessibility with sophistication. The malware’s roots in a Malware-as-a-Service (MaaS) model have made it appealing to both seasoned cybercriminals and less technical actors, allowing it to scale quickly across regions and targets. What sets this campaign apart is not just the increase in volume but the strategic targeting of Russian organizations, suggesting a more focused and perhaps geopolitically influenced effort. The campaign’s consistent activity since 2023, combined with the spike in early 2025, reflects how threat actors are evolving long-term infrastructure to sustain persistent and tailored attacks.
- What makes PureRAT especially concerning is its layered approach—integrating not only remote access but also data theft and modular expansion capabilities. The inclusion of PureCrypter and PureLogs reveals a deliberate attempt to embed flexibility and stealth at every stage of the infection chain. Unlike traditional malware that performs one task, PureRAT’s ecosystem enables dynamic functions like downloading new components, harvesting sensitive data, and maintaining persistence with minimal user detection. This modularity allows the attackers to adapt the payload based on the target, increasing its utility across different sectors and user profiles.
- Another noteworthy aspect is the way PureRAT has been built for versatility. While the campaign highlights a few core plugins in use, it’s clear the malware is designed to support a wide range of actions depending on the target environment. This adaptability gives attackers the flexibility to shift tactics mid-operation, whether they want to spy on user behavior, hijack cryptocurrency transactions, or silently collect browser and application data. PureRAT is less about one method of compromise and more about maintaining access and control through a cohesive, layered attack.
ETLM ASSESSMENT
From the ETLM perspective, CYFIRMA anticipates that PureRAT’s evolution may contribute to a broader shift in how cybercriminals operate—favoring low-noise, persistent threats over quick, high-profile attacks. With email-based delivery still the primary access point, attackers are counting on human error to gain a foothold inside organizations. What’s especially concerning is how long this campaign has remained active without major changes, showing that even well-known malware can be devastating when deployed persistently and strategically. The pairing of PureRAT with powerful tools like PureLogs gives threat actors extensive control over compromised systems, allowing them to quietly extract sensitive data over time. As this trend continues, we may see a growing number of less-sophisticated attackers leveraging these ready-made tools, leading to more frequent and unpredictable intrusions across organizations and potentially affecting everyday users as well.
IOCs:
Kindly refer to the IOCs Section to exercise controls on your security systems.
Recommendations:
STRATEGIC:
- Deploy an Extended Detection and Response (XDR) solution as part of the organization’s layered security strategy that provides detection/prevention for malware and malicious activities that do not rely on signature-based detection methods.
- Configure organization’s intrusion detection systems (IDS), intrusion prevention systems (IPS), or any network defence mechanisms in place to alert on — and upon review, consider blocking connection attempts to and from — the external IP addresses and domains listed in the appendix.
MANAGEMENT:
- Security Awareness training should be mandated for all company employees. The training should ensure that employees:
- Avoid downloading and executing files from unverified sources.
- Incorporate a written software policy that educates employees on good practices in relation to software and potential implications of downloading and using restricted software.
- Move beyond the traditional model of security awareness towards Improved Simulation and training exercises that mimic real attack scenarios, account for behaviors that lead to a compromise, and are measured against real attacks the organization receives.
TACTICAL RECOMMENDATIONS
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defence based on the tactical intelligence provided.
- Exert caution when opening email attachments or clicking on embedded links supplied via email communications.
- Enforce policies to validate third-party software before installation.
- Use multi-factor authentication (MFA) to mitigate credential theft and prevent attacker access. Keep MFA always-on for privileged accounts and apply risk-based MFA for normal accounts.
CYFIRMA’S WEEKLY INSIGHTS
1. Weekly Attack Types and Trends
Key Intelligence Signals:
- Attack Type: Ransomware Attacks, Phishing, Vulnerabilities & Exploits, Data Leaks.
- Objective: Unauthorized Access, Data Theft, Data Encryption, Financial Gains, Espionage.
- Business Impact: Data Loss, Financial Loss, Reputational Damage, Loss of Intellectual Property, Operational Disruption.
- Ransomware – Qilin Ransomware, ArcusMedia Ransomware | Malware – PureRAT
- Qilin Ransomware– One of the ransomware groups.
- ArcusMedia Ransomware – One of the ransomware groups.
Please refer to the trending malware advisory for details on the following: - Malware – PureRAT
Behavior – Most of these malwares use phishing and social engineering techniques as their initial attack vectors. Apart from these techniques, exploitation of vulnerabilities, defense evasion, and persistence tactics are being observed
2. Threat Actor in Focus
Macro-Based Espionage: TAG-110’s New Attack Chain Against Tajikistan
- Threat Actor: TAG-110
- Attack Type: Spear phishing
- Objective: Espionage
- Target Technology: Microsoft Office (Word) with VBA Macro-enabled Templates (.dotm files), C2 Infrastructure
- Target Geography: Tajikistan
- Target Industries: Government organizations, Educational institutions, Research organizations
- Business Impact: Data Theft, Long-term Compromise, Operational Disruption, Reputational Damage
Summary:
Recent analysis has uncovered a phishing campaign conducted by TAG-110, a Russia-aligned threat actor linked to APT28 (BlueDelta) and overlapping with UAC- 0063, targeting Tajikistan between January and February 2025. The campaign employed macro-enabled Word template files (.dotm) as the initial infection vector, representing a tactical shift from the group’s previous reliance on HTA-based HATVIBE payloads. The malicious documents, themed on Tajik government topics, were designed to deceive recipients and triggered execution through the document.open event. Upon opening, the macro unprotected the document, suppressed spell checks, and attempted visual obfuscation by setting the font line width to zero. It then copied itself into %APPDATA%\Microsoft\Word\STARTUP\
If executed, it collected system information—computer name, username, region, monitor resolution, language, and system version—and formatted it in JSON. After a short delay, it initiated the getInfo() Sub procedure, which created an HTTP POST request to http[:]//38[.]180[.]206[.]61/engine[.]php, with unique Base64-encoded identifiers and obfuscated POST data. If the response started with “%%%%,” the remainder was passed to the start() procedure; otherwise, it waited ten seconds and retried. One sample sent data every tenth POST request, while another sent it on the first.
The start() procedure parsed C2 response strings using the delimiter “###,” creating an array used to build and execute additional VBA code. The code likely created a WScript.shell COM object and modified the registry key HKEY_CURRENT_USER\Software\Microsoft\Office\Word\Security\AccessVBOM to enable macro manipulation. It also likely used the Word. Application COM object to open Word silently, generate a new document, inject a VBA module, and execute it. Both samples communicated with the same C2 server, previously associated with HATVIBE, and may lead to the deployment of additional malware including HATVIBE, CHERRYSPY, LOGPIE, or custom payloads.
Relevancy & Insights:
TAG-110, a Russia-linked cyber-espionage group associated with APT28 (BlueDelta), has a history of targeting human rights groups, private security firms, and state institutions across Central Asia, East Asia, and Europe. Since July, over 60 victims in Tajikistan, Kyrgyzstan, Turkmenistan, and Kazakhstan have been compromised using custom malware like Hatvibe and Cherryspy. These infections were primarily delivered via malicious Microsoft Word attachments and exploited vulnerable public-facing services.
In the current campaign, TAG-110 targeted government, educational, and research institutions in Tajikistan using macro-enabled Microsoft Word .dotm templates and VBA-based persistence techniques to facilitate espionage operations. This shift from HTA-based payloads like Hatvibe to macro-based templates shows an evolution in tactics while maintaining the group’s consistent strategy of leveraging legitimate- looking documents for initial access. The campaign underscores TAG-110’s ongoing focus on intelligence collection from public sector entities in Central Asia, aligned with Russia’s broader geopolitical interests in the region.
ETLM Assessment:
TAG-110, a Russia-aligned threat actor linked to APT28 (BlueDelta), has consistently targeted Central Asian entities since at least 2021, with past campaigns employing HTA-based HATVIBE payloads delivered via weaponized documents to compromise government, diplomatic, and research organizations in Kazakhstan, Uzbekistan, and Tajikistan. The group’s latest February 2025 campaign against Tajikistan represents a tactical evolution, replacing HATVIBE with macro-enabled .dotm templates while maintaining consistent TTPs—document-themed lures, registry-based persistence (HKEY_CURRENT_USER\Software\Microsoft\Office settings), and C2 infrastructure overlap (38[.]180[.]206[.]61). Their operations align with Russia’s strategic objective of maintaining regional influence through cyber espionage, evidenced by targeting election-related documents and military communications.
This incident could be a continuation of TAG-110’s intelligence-gathering operations, likely supporting Kremlin-aligned geopolitical interests in Central Asia. The shift to .dotm templates reflects adaptation to macro security controls while retaining core capabilities. High-risk entities include Tajik government agencies, educational/research institutions, and organizations involved in elections or military affairs. Defenders should prioritize macro security policies (disabling AutoExec), monitor Word STARTUP directories, and scrutinize registry modifications to AccessVBOM keys.
Recommendations:
Strategic Recommendations:
- Incorporate Digital Risk Protection (DRP) as part of the overall security posture to proactively defend against impersonations and phishing attacks.
- Deploy Zero Trust Policy that leverages tools like security information management, advanced security analytics platforms, security user behaviour analytics, and other analytics systems to help the organization’s security personnel observe in real-time what is happening within their networks so they can orient defences more intelligently.
- Deploy a unified threat management strategy – including malware detection, deep learning neural networks, and anti-exploit technology – combined with vulnerability and risk mitigation processes.
Tactical Recommendations:
- Set up DMARC (Domain-based Message Authentication Reporting & Conformance) to stop phishers from spoofing your domain (that is, making their emails look like they come from your organization).
- Exert caution when opening email attachments or clicking on embedded links supplied via email communications.
- For better protection coverage against email attacks (like spear phishing, business email compromise, or credential phishing attacks), organizations should augment built-in email security with layers that take a materially different approach to threat detection.
Operational Recommendations:
- Look for email security solutions that use ML- and AI-based anti-phishing technology for BEC protection to analyze conversation history to detect anomalies, as well as computer vision to analyze suspect links within emails.
- Secure your organization’s internet-facing assets with robust security protocols and encryption, including authentication or access credentials configuration, to ensure that critical information stored in databases/servers is always safe.
| MITRE FRAME WORK | ||
| Tactic | ID | Technique |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Execution | T1204.002 | User Execution: Malicious File |
| Execution | T1059 | Command and Scripting Interpreter |
| Persistence | T1137.001 | Office Application Startup: Office Template Macros |
| Privilege Escalation | T1055 | Process Injection |
| Defense Evasion | T1027.013 | Obfuscated Files or Information: Encrypted/Encoded File |
| Defense Evasion | T1221 | Template Injection |
| Credential Access | T1003.008 | OS Credential Dumping: /etc/passwd and /etc/shadow |
| Discovery | T1082 | System Information Discovery |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
IOCs:
Kindly refer to the IOCs (Indicators of Compromise) Section to exercise controls on your security systems.
3. Major Geopolitical Developments in Cybersecurity
Russia stepping up its cyber campaigns against the West
Intelligence agencies from the United States, Europe, Australia, and Canada have issued a joint advisory warning of an ongoing Russian cyberespionage campaign targeting Western logistics firms and IT companies. These targets include organizations involved in the coordination, transport, and delivery of foreign aid to Ukraine. The campaign has been attributed to the Russian GRU’s 85th Main Special Service Center, military unit 26165—better known as APT28 or “Fancy Bear.” The advisory links this activity to the group’s broader operations, including the widespread targeting of IP cameras in Ukraine and neighboring NATO countries.
The threat actors are using tactics such as password spraying, spear phishing, and manipulating Microsoft Exchange mailbox permissions to gain access to sensitive systems.
Separately, Dutch intelligence agencies have identified a previously unknown Russian cyber group named “Laundry Bear.” Although its tactics overlap with those of APT28, Dutch authorities consider Laundry Bear to be a distinct entity. According to the Netherlands’ Ministry of Defence, Laundry Bear was behind multiple cyberattacks in September 2024, including a significant data breach at the Dutch national police. The group appears to be focused on infiltrating armed forces, government agencies, defense contractors, non-governmental organizations, and IT service providers. Laundry Bear has also targeted companies developing advanced technologies that are currently inaccessible to Russia due to Western sanctions.
In related developments, cybersecurity researchers have released a report on another Russian-linked cyberespionage group known as “Void Blizzard.” This group is engaged in opportunistic but highly targeted operations to advance Russian strategic interests. While Void Blizzard employs relatively unsophisticated methods for initial access—such as password spraying and using stolen credentials—they have conducted high-volume campaigns against intelligence-rich targets. The group often acquires authentication data, including cookies and login credentials, from criminal marketplaces. These are then used to infiltrate systems such as Microsoft Exchange and SharePoint Online for data collection.
ETLM Assessment:
All three campaigns bear all the hallmarks of a state-driven espionage campaign with the goal of providing the Russian government and defense establishments with strategic intelligence and possibly also intellectual property. There are likely many similar campaigns ongoing at the same time, primarily attacking the West and West-aligned governments and organizations around the globe.
4. Rise in Malware/Ransomware and Phishing
The Qilin Ransomware Impacts Straits Construction
- Attack Type: Ransomware
- Target Industry: Construction
- Target Geography: Singapore
- Ransomware: Qilin Ransomware
- Objective: Data Theft, Data Encryption, Financial Gains
- Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary:
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from Singapore; Straits Construction(www[.]straitsconstruction[.]com), was compromised by Qilin Ransomware. Straits Construction Group is a leading building construction and project management company based in Singapore. The company has played a significant role in shaping Singapore’s urban landscape, especially through its long-standing partnership with the Housing and Development Board (HDB) for public housing projects. Straits Construction has expanded its portfolio to include residential, commercial, and industrial developments across both public and private sectors. The compromised data consists of internal data, financial data, clients’ contract data, ongoing and finished projects’ drawing and design documents, contracts, employee data, etc. The total size of the compromised data is approximately 350 GB.
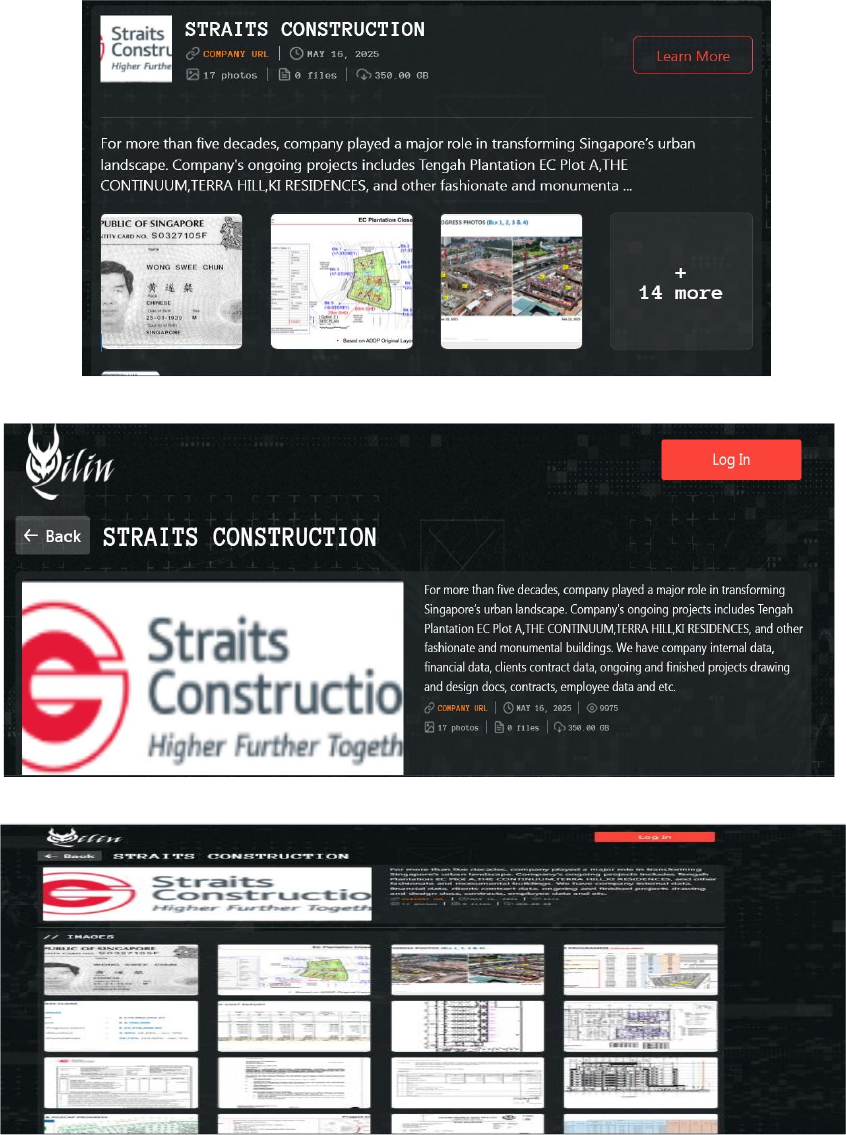
Relevancy & Insights:
- Qilin (also known as Agenda) is a Ransomware-as-a-Service (RaaS) group first observed in July 2022. It employs a double extortion method, encrypting victims’ data and exfiltrating it, threatening to leak it on their data leak site (DLS) if the ransom is not paid.
- In recent campaigns, the Qilin Ransomware group has been observed using a new, heavily obfuscated .NET-based loader known as NETXLOADER to covertly deploy payloads such as SmokeLoader, significantly complicating both detection and analysis.
- Recently, we observed that the North Korean threat group Moonstone Sleet is using Qilin ransomware in limited attacks, marking the first known use of Qilin by a nation-state actor.
- The Qilin Ransomware group primarily targets countries such as the United States of America, Canada, France, Spain, and the United Kingdom.
- The Qilin Ransomware group primarily targets industries, including Health Care Providers, Business Support Services, Heavy Construction, Manufacturing, and Industrial Machinery.
- Based on the Qilin Ransomware victims list from 1st January 2024 to 28th May 2025, the top 5 Target Countries are as follows:
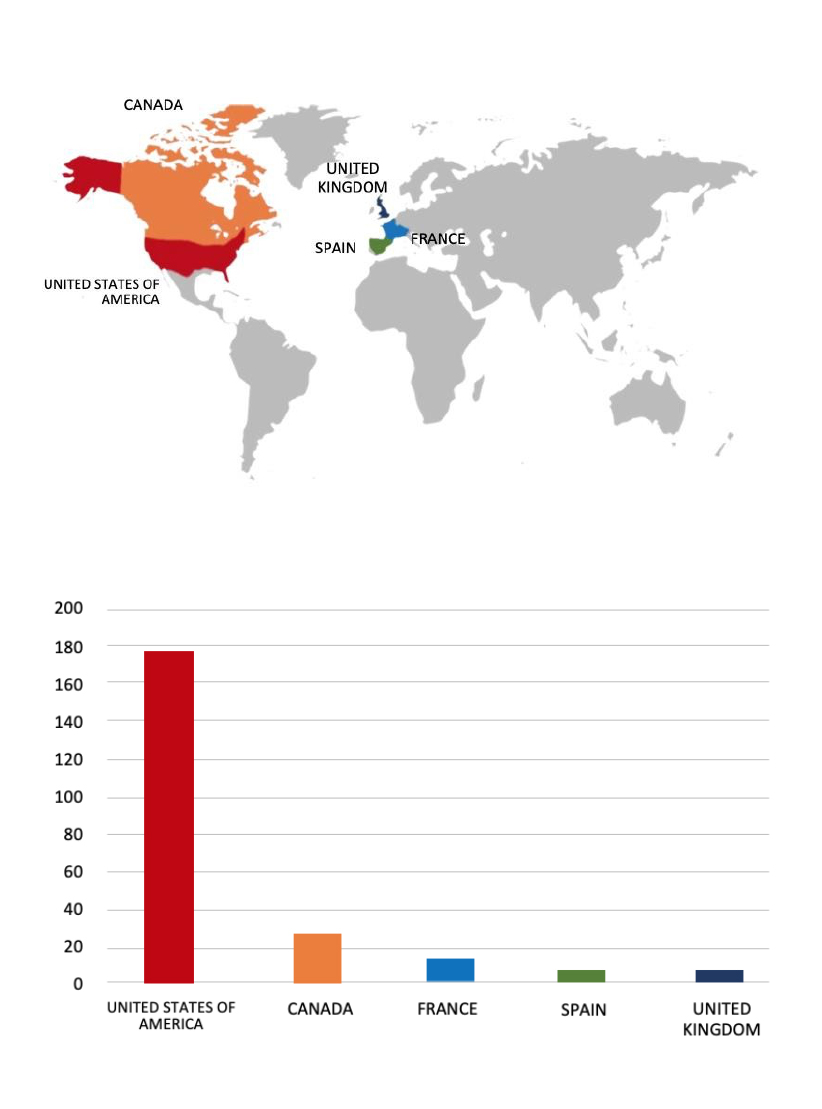
- The Top 10 Industries most affected by the Qilin Ransomware from 1st January 2024 to 28th May 2025 are as follows:
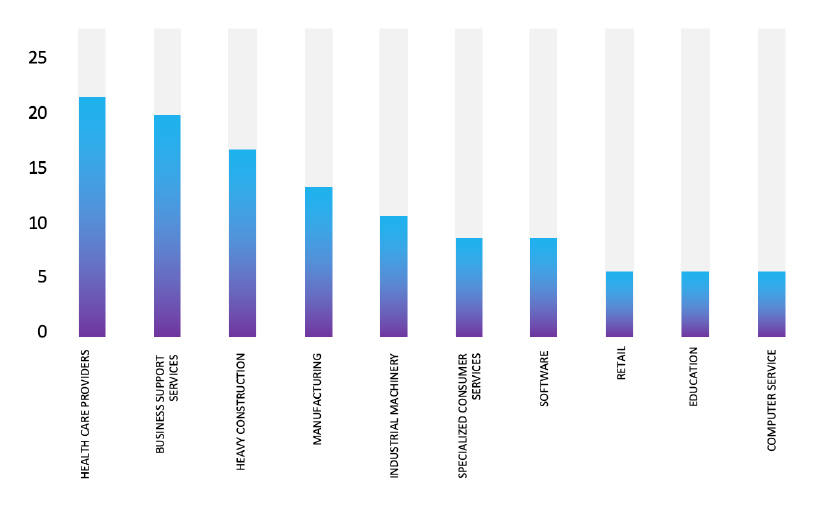
ETLM Assessment:
According to CYFIRMA’s assessment, Qilin ransomware poses a significant threat to organizations of all sizes. Its evolving tactics, including double extortion (data encryption and leak threats), cross-platform capabilities (Windows and Linux, including VMware ESXi), and focus on speed and evasion, make it a particularly dangerous actor.
The ArcusMedia Ransomware Impacts Fong Shann Printing Philippines Inc.
- Attack Type: Ransomware
- Target Industry: Printing and Packaging
- Target Geography: Philippines
- Ransomware: ArcusMedia Ransomware
- Objective: Data Theft, Data Encryption, Financial Gains
- Business Impact: Financial Loss, Data Loss, Reputational Damage
Summary
From the External Threat Landscape Management (ETLM) Perspective, CYFIRMA observed in an underground forum that a company from the Philippines, Fong Shann Printing Philippines Inc(https[:]//fongshann[.]com[.]ph/), was compromised by ArcusMedia Ransomware. Fong Shann Printing Philippines Inc. is a printing services company based in the Philippines. The company specializes in high-quality printing solutions for a variety of business needs. The compromised data consists of confidential and sensitive information related to the organization.
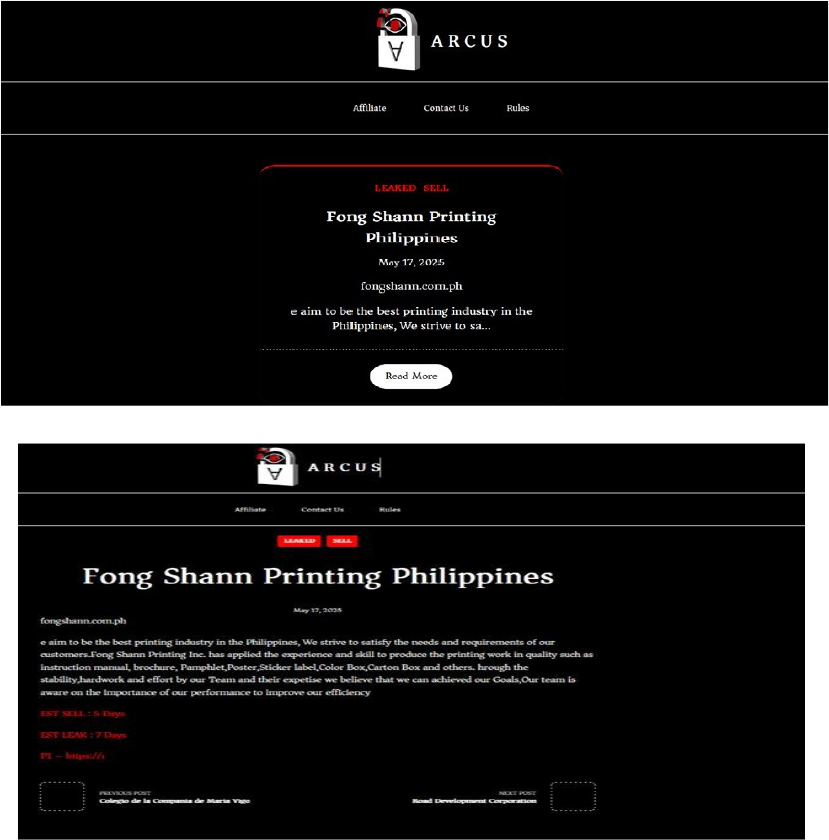
Source: Dark Web
Relevancy & Insights:
- ArcusMedia ransomware began operations in May 2024 and has quickly gained attention in the cybersecurity community. The group employs phishing emails to gain initial access, deploying custom ransomware binaries and using obfuscation techniques to evade detection.
- ArcusMedia Ransomware uses the ChaCha20 encryption algorithm for file encryption, with RSA-2048 used to secure encryption keys. It employs a dual encryption strategy.
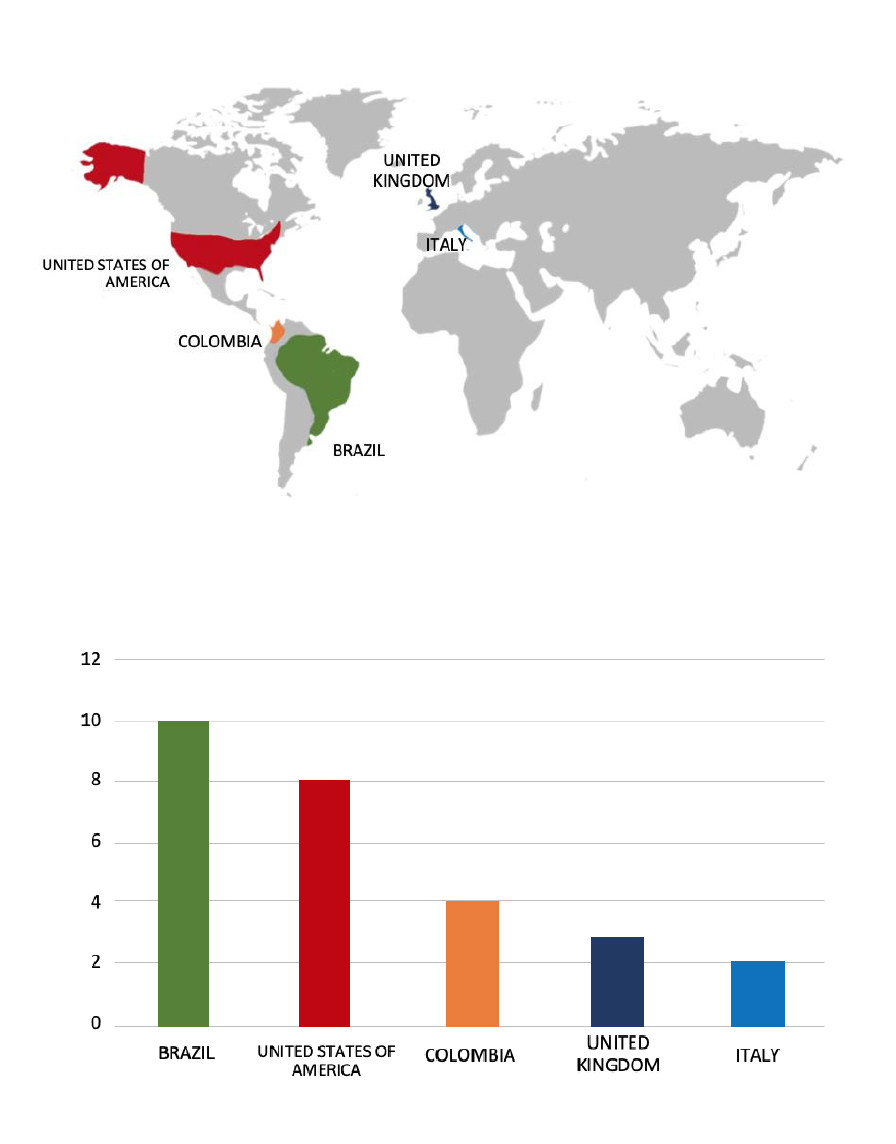
- The ArcusMedia Ransomware group primarily targets countries like Brazil, the United States of America, Colombia, the United Kingdom, and Italy.
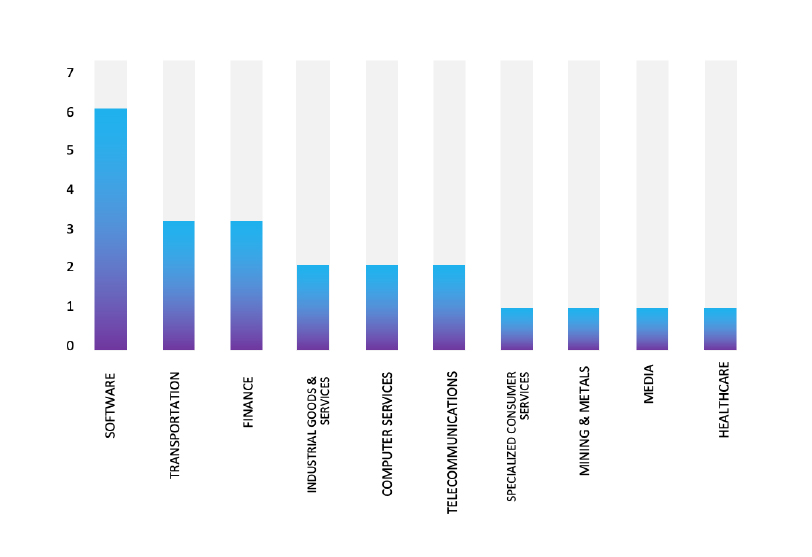
- The ArcusMedia Ransomware group primarily targets industries such as Software, Transportation, Finance, Industrial Goods & Services, and Computer Services.
- Based on the ArcusMedia Ransomware victims list from 1st May 2024 to 28th May 2025, the top 5 Target Countries are as follows:
- The Top 10 Industries, most affected by the ArcusMedia Ransomware from 1st May 2024 to 28th May 2025 are as follows:
ETLM Assessment:
Based on recent assessments by CYFIRMA, ArcusMedia ransomware represents a significant new threat in the cybersecurity landscape, characterized by its sophisticated tactics and aggressive approach to extortion. Organizations are advised to enhance their cybersecurity defenses, including employee training on phishing awareness, regular updates to systems, and comprehensive incident response plans to mitigate risks associated with this evolving threat actor. Continuous monitoring of ArcusMedia’s activities will be essential for understanding its impact on global cybersecurity efforts.
5. Vulnerabilities and Exploits
Vulnerability in vBulletin
- Attack Type: Vulnerabilities & Exploits
- Target Technology: Forum & blogging software
- Vulnerability: CVE-2025-48827
- CVSS Base Score: 10.0 Source
- Vulnerability Type: Improper Protection of Alternate Path
- Summary: The vulnerability allows a remote attacker to compromise the affected system.
Relevancy & Insights:
The vulnerability exists due to missing authorization checks within protected API controller methods. A remote non-authenticated attacker can send a specially crafted request to the website and execute arbitrary PHP code on the system.
Impact: Successful exploitation of the vulnerability requires PHP 8.1 to be used by the web application.
Affected Products: https[:]//kevintel[.]com/CVE-2025-48827
Recommendations:
Monitoring and Detection: Implement monitoring and detection mechanisms to identify unusual system behavior that might indicate an attempted exploitation of this vulnerability.
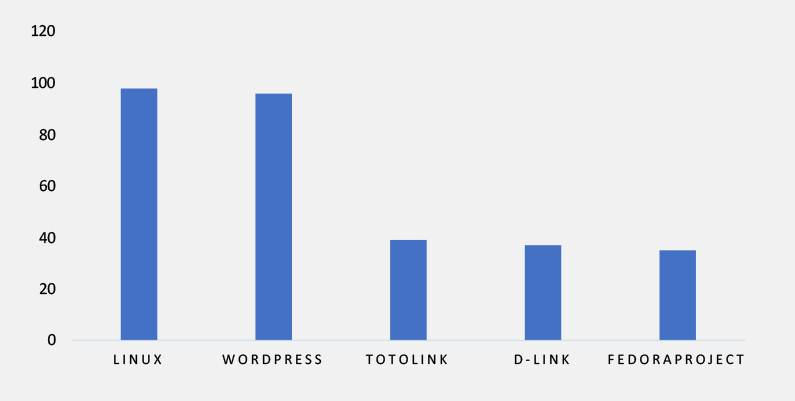
TOP 5 AFFECTED TECHNOLOGIES OF THE WEEK
This week, CYFIRMA researchers have observed significant impacts on various technologies, due to a range of vulnerabilities. The following are the top 5 most affected technologies.
ETLM Assessment
Vulnerability in vBulletin can pose significant threats to user privacy and security. This can impact various industries globally, including technology, gaming, education, and online communities. Ensuring the security of vBulletin is crucial for maintaining the integrity and protection of users’ data worldwide. Therefore, addressing these vulnerabilities is essential to safeguarding forum-based communication, user authentication, and content management operations across different geographic regions and sectors.
6. Latest Cyber-Attacks, Incidents, and Breaches
IMNCrew Ransomware attacked and published the data of ABDA Insurance
- Threat Actor: IMNCrew Ransomware
- Attack Type: Ransomware
- Objective: Data Leak, Financial Gains
- Target Technology: Web Applications
- Target Industry: Financial Services
- Target Geography: Indonesia
- Business Impact: Operational Disruption, Data Loss, Financial Loss, Potential Reputational Damage
Summary:
Recently, we observed that IMNCrew Ransomware attacked and published the data of ABDA Insurance (www[.]abdainsurance[.]co[.]id) on its dark web website. PT Asuransi Bina Dana Arta Tbk (ABDA) is a prominent general insurance company in Indonesia. ABDA offers a comprehensive range of insurance products, including motor vehicle, property, health, personal accident, travel, and cargo insurance.
The data leak, following the ransomware attack, encompasses sensitive and confidential records originating from the organizational database.
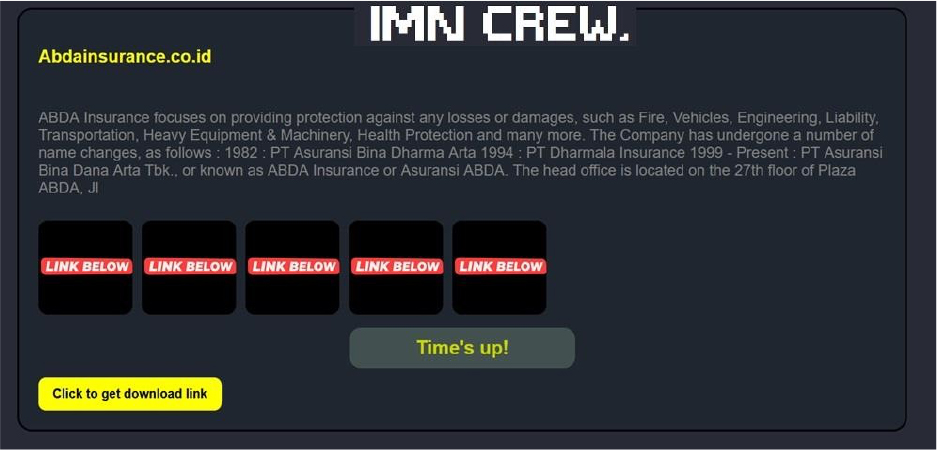
Source: Dark Web
Relevancy & Insights:
- IMNCrew Ransomware is a newly emerged ransomware and data extortion group, first identified in late March 2025.
- IMNCrew Ransomware exploits vulnerable external-facing services, such as firewalls and VPNs, to gain entry into target networks.
ETLM Assessment:
According to CYFIRMA’s assessment, IMNCrew is a rapidly developing ransomware and extortion group with a focus on small to medium-sized organizations worldwide. Their tactics are opportunistic, leveraging exposed services and quick lateral movement, and their operations combine data theft with file encryption for maximum extortion leverage. With a dedicated leak site and a professional approach to negotiations, IMNCrew poses a growing threat, particularly to organizations with unpatched external services and limited cybersecurity resources.
7. Data Leaks
Indonesian Telecom Telkomsel’s SIM Management Panel Advertised on a Leak Site
- Attack Type: Access Sale
- Target Industry: Telecommunication
- Target Geography: Indonesia
- Objective: Financial Gains
- Business Impact: Data Loss, Reputational Damage
Summary:
The CYFIRMA Research team observed an Access sale related to Indonesian Telecom Telkomsel (https[:]//www[.]telkomsel[.]com/) in an underground forum. Telkomsel is Indonesia’s largest mobile network operator, boasting a vast subscriber base and playing a critical role in the nation’s digital infrastructure. A control panel, identified as the “TELKOMSEL CENTER PANEL,” is reportedly being offered for sale, potentially exposing sensitive customer and network data.
The exposed panel, which appears to be a real-time SIM management interface, allegedly provides capabilities to view, activate, suspend, or test SIM cards, monitor billing statuses, and access comprehensive SIM data overviews. This includes detailed information such as ICCID, IMSI, MSISDN, PIN, data plans, and APN groups. Furthermore, the panel seemingly offers advanced filtering and search functionalities to analyze SIM fleet data by various metrics, along with live data usage tracking, and batch actions for bulk updates and rule-based operations.
The information allegedly accessible includes a wide array of critical data points that span user identification, service usage, technical metrics, and billing details. This includes identifiers such as CSP ID, Account ID, ICCID, MSISDN, IMSI, Thing ID, Tag ID, and External Account Number. It also encompasses data traffic details like Data Traffic Detail ID, total data usage (raw, uplink, and downlink), and data usage roundup. Service-related information includes the billing cycle, current technical and billing status, service type, and details about the assigned rate plan, including its ID, name, type, and version. Technical specifics such as APN name, device IP address, operator network, RAT (Radio Access Technology), and various network identifiers like CGI, SAI, RAI, TAI, ECGI, and the serving SGSN are also included.
Session-related data points such as record received date, record open time, session duration, session close cause, record sequence number, time slice, zone, and charging details including Charging ID, TAP Code, and Stream ID are also part of the accessible information. This extensive dataset provides a comprehensive view of user activity, device behavior, and network interaction.
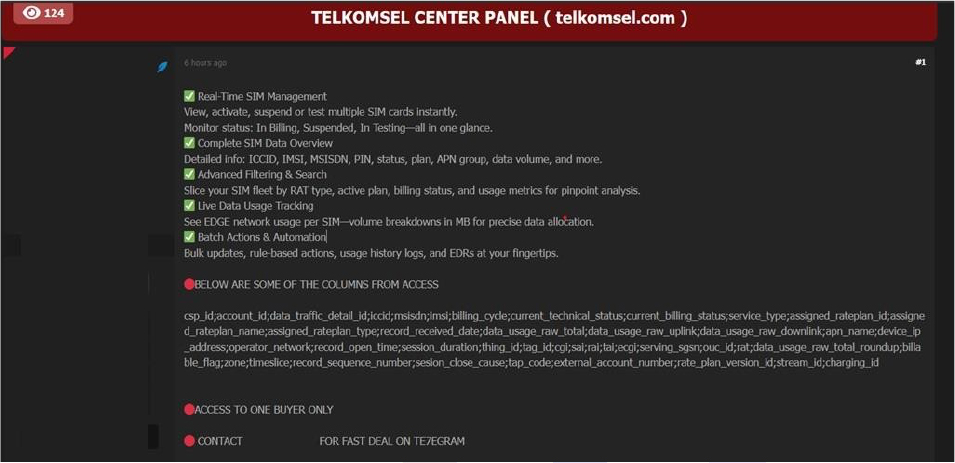
Source: Underground Forums
Institute of Cost Accountants of India (ICMAI) Data Advertised on a Leak Site
- Attack Type: Data Leak
- Target Industry: Education and Professional Certification
- Target Geography: India
- Objective: Data Theft, Financial Gains
- Business Impact: Data Loss, Reputational Damage
Summary:
The CYFIRMA Research team observed a data sale related to the Institute of Cost Accountants of India (ICMAI) (https[:]//icmai[.]in/icmai/) in an underground forum. The Institute of Cost Accountants of India (ICMAI) is a leading professional accounting organization in the country, entrusted with the responsibility of regulating and overseeing the profession of Cost and Management Accountancy in India. The compromised data reportedly includes a wide range of personal and professional information such as Date of Birth (DOB), Date of Enrollment (DOE), Salary (SAL), RPIN, STAR, CPEDT, Email addresses, First Name (FNAME), Middle Name (MNAME), multiple address fields (RADD1 to RADD4), City (RCITY), Surname (SNAME), Academic Qualifications (AQUALI), Membership Number (MEMBNO), Membership Category (MEMCAT), Firm Name, Registration Letter Date (RLETTERDT), State Name (STATENAME), Telephone number, Region Code, Certificate Validity (VALID_UPTO), Certificate Dates (CERTIFICATEDT, RCERTIFICATEDT), Proprietary Firm Registration Number (PROP_FIRM_REGNNO), and other repeated fields such as Email, Phone, Membership Number, Registration Number, Name, Address, and Date of Insertion (Inserted_On). The total size of the data being offered is approximately 3.83 GB and is allegedly available free of charge. The breach and subsequent data exposure have been linked to a threat actor using the alias “ZERO LEGION CREW.”
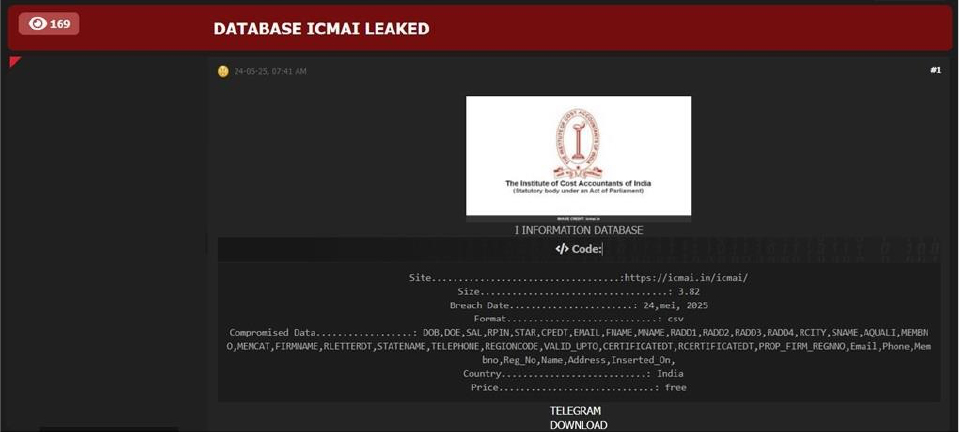
Source: Underground Forums
Relevancy & Insights:
Financially motivated cybercriminals are continuously scouring for exposed and vulnerable systems and applications to exploit. A significant number of these malicious actors congregate within underground forums, where they discuss cybercrime and trade stolen digital assets. Operating discreetly, these opportunistic attackers target unpatched systems or vulnerabilities in applications to illicitly gain access and steal valuable data. Subsequently, the pilfered data is advertised for sale within underground markets, where it can be acquired, repurposed, and utilized by other malicious actors in further illicit activities.
ETLM Assessment:
The threat actor identified as “ZERO LEGION CREW” has been associated with several data breaches, with credible sources reporting their involvement in unauthorized system intrusions and the sale of stolen data on dark web forums. The group’s continued presence and activity highlight the persistent and evolving nature of cyber threats emerging from the dark web. These incidents emphasize the critical need for organizations to enhance their cybersecurity measures by adopting continuous monitoring, leveraging threat intelligence, and implementing proactive defense strategies to safeguard vital data assets.
Recommendations: Enhance the cybersecurity posture by:
- Updating all software products to their latest versions is essential to mitigate the risk of vulnerabilities being exploited.
- Ensure proper database configuration to mitigate the risk of database-related attacks.
- Establish robust password management policies, incorporating multi-factor authentication and role-based access to fortify credential security and prevent unauthorized access.
8. Other Observations
The CYFIRMA Research team has uncovered a critical development that could significantly impact the global cyber threat landscape. The complete source code of the sophisticated and multi-platform ransomware known as VanHelsing has been leaked on underground forums operating over the TOR network.
The leaked package includes functional ransomware payloads targeting Windows, Linux, and all versions of ESXi systems, along with a fully featured command-and- control panel, a chat system for victim communication, a data leak blog infrastructure, and a file server. Additionally, several hardcoded private keys and database schemas were also exposed.
This leak poses a serious threat as it enables even low-skilled threat actors to repurpose the code and launch their own ransomware campaigns with minimal effort. In response, organizations are strongly advised to implement offline and segmented backup strategies, ensure all systems—especially ESXi hosts—are fully patched, deploy EDR/XDR solutions for behavioral detection, enforce the principle of least privilege, require multi-factor authentication across all access points, and activate anomaly detection systems to proactively mitigate the risk of emerging ransomware variants.
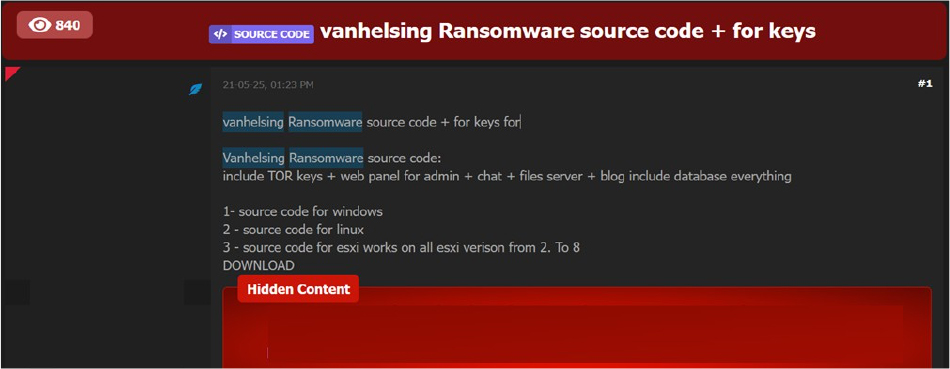
Source: Underground Forums
STRATEGIC RECOMMENDATIONS
- Attack Surface Management should be adopted by organisations, ensuring that a continuous closed-loop process is created between attack surface monitoring and security testing.
- Delay a unified threat management strategy – including malware detection, deep learning neural networks, and anti-exploit technology – combined with vulnerability and risk mitigation processes.
- Incorporate Digital Risk Protection (DRP) in the overall security posture that acts as a proactive defence against external threats targeting unsuspecting customers.
- Implement a holistic security strategy that includes controls for attack surface reduction, effective patch management, and active network monitoring, through next-generation security solutions and a ready-to-go incident response plan.
- Create risk-based vulnerability management with deep knowledge about each asset. Assign a triaged risk score based on the type of vulnerability and criticality of the asset to help ensure that the most severe and dangerous vulnerabilities are dealt with first.
- Take advantage of global Cyber Intelligence providing valuable insights on threat actor activity, detection, and mitigation techniques.
- Proactively monitor the effectiveness of risk-based information security strategy, the security controls applied, and the proper implementation of security technologies, followed by corrective actions remediations, and lessons learned.
- Consider implementing Network Traffic Analysis (NTA) and Network Detection and Response (NDR) security systems to compensate for the shortcomings of EDR and SIEM solutions.
- Detection processes are tested to ensure awareness of anomalous events. Timely communication of anomalies and continuously evolved to keep up with refined ransomware threats.
- Patch software/applications as soon as updates are available. Where feasible, automated remediation should be deployed since vulnerabilities are one of the top attack vectors.
- Consider using security automation to speed up threat detection, improved incident response, increased the visibility of security metrics, and rapid execution of security checklists.
- Build and undertake safeguarding measures by monitoring/ blocking the IOCs and strengthening defences based on the tactical intelligence provided.
- Deploy detection technologies that are behavioral anomaly-based to detect ransomware attacks and help to take appropriate measures.
- Implement a combination of security control such as reCAPTCHA (completely Automated Public Turing test to tell Computers and Humans Apart), Device fingerprinting, IP backlisting, Rate-limiting, and Account lockout to thwart automated brute-force attacks.
- Ensure email and web content filtering uses real-time blocklists, reputation services, and other similar mechanisms to avoid accepting content from known and potentially malicious sources.
MANAGEMENT RECOMMENDATIONS
TACTICAL RECOMMENDATIONS
Situational Awareness – Cyber News
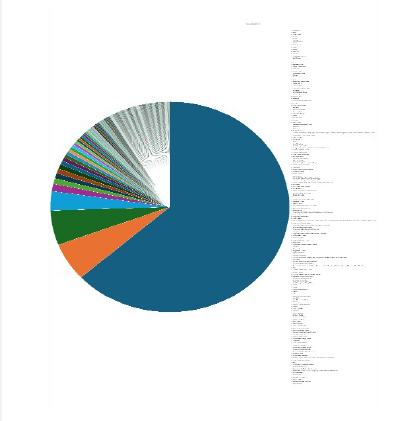
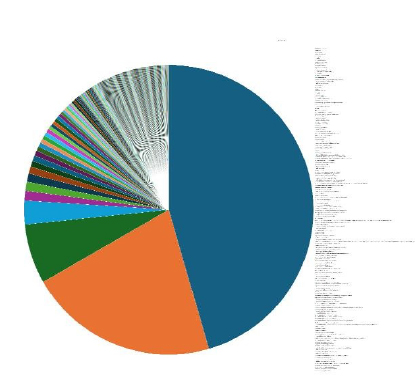
Please find the Geography-Wise and Industry-Wise breakup of cyber news for the last 5 days as part of the situational awareness pillar.
Geography-Wise Graph
Industry-Wise Graph
For situational awareness intelligence and specific insights mapped to your organisation’s geography, industry, and technology, please access DeCYFIR.
[ad_2]
Source link

