[ad_1]
The greatest cyber vulnerabilities for supply chains exist in operating technology (OT), which includes Internet of Things (IoT) devices, robots, industrial control systems, supervisory control and data acquisition systems, programmable logic controllers, and other technology that organizations use to connect, monitor, manage, and secure their industrial operations. These tools and technologies are increasingly at risk, and many organizations are woefully unprepared.
IT—the technology that organizations use to monitor and manage core functions like email and data storage—is not necessarily the problem. Although strategies like phishing attacks and sending malicious links through email are still common, many organizations offer training and require practices like multifactor authentication to reduce the risks of these attacks.
That’s why many supply chain organizations are currently on a collision course with cybercrime. Closing these gaps and getting serious about OT cybersecurity is increasingly critical to the future stability of our supply chains.
We’re losing focus at the worst possible time
Each year, APQC surveys supply chain professionals about their organization’s top priorities, challenges and focus areas for supply chain. Only about one-third of respondents this year are expecting cybersecurity to have a major impact on supply chains compared with 2024 (34% versus 43% in 2024). Unfortunately, it’s highly unlikely that bad actors will take a holiday from cyberattacks in 2025. Instead, the opposite appears to be true: The risks have never been greater, and they continue to evolve.
Vulnerabilities within OT are a critical piece of the picture that many organizations can easily miss. For example, there are now countless IoT devices connected to each other and to major systems within supply chains. While these devices have become indispensable tools for many organizations, any of them are hackable. The risks are even greater when organizations use outdated security protocols or improperly configured firewalls.
By taking advantage of vulnerabilities in the supply chain, bad actors are already making billions of dollars stealing physical cargo, and they don’t even need to leave their homes to do it. “Strategic theft” is the practice of using identify theft, social engineering, or other forms of deception to fraudulently broker cargo and change its destination. Experts say that this form of theft saw a 1,475% increase from Q1 of 2022 to Q4 of 2024 and that it now represents about a third of all cargo theft.
As these threats continue to grow and proliferate, there’s never been a worse time to let our vigilance slip. But this is exactly what many organizations are beginning to do.
We’re not spending enough
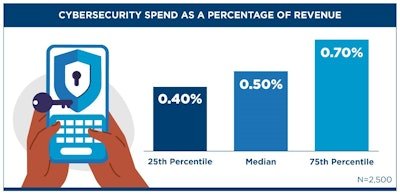
While cyber threats continue to grow, spending on cyber security isn’t necessarily keeping up. We found that at the median, organizations only spend half of one percent of their total revenue on cybersecurity. This means that a hypothetical company with two billion dollars in annual revenue would only spend $10 million on cybersecurity, including both for IT and OT.
 APQC
APQC
While $10 million dollars may seem like a lot just to spend on cybersecurity, it looks more like a drop in the ocean when putting that number against broader spending patterns. For example, the survey also found that organizations spend a median of 49.6% of their revenue on manufacturing—close to a billion dollars for an organization with two billion in revenue. Is $10 million enough to protect a manufacturing investment this large, let alone the rest of your supply chain and enterprise?
Outsourcing cybersecurity is one potential strategy for securing your OT, but it can’t be the full story. We found that at the median, organizations only outsource 25% of their cybersecurity processes for OT security. Outsourcing doesn’t provide any guarantee of safety from cyberattacks either, as we’ve learned from high-profile incidents. While it can be an important part of the picture, outsourcing can’t replace a lack of in-house investment in cyber security.
Current cybersecurity practices are not enough
The declining prioritization of cybersecurity and inadequate investment in it are bad enough on their own. However, it’s also deeply concerning to see just how lax many organizations currently are when it comes to planning and preparedness for a cyberattack.
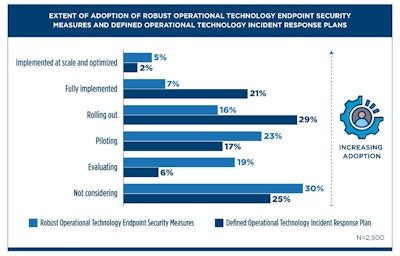
The APQC survey also found that almost one-third of surveyed organizations are not considering robust OT endpoint security measures, while one-quarter don’t have any plans in place for how to respond if a cyberattack happens. Are these companies just playing the odds and hoping nothing happens to them? Hope is not an effective strategy, but it’s hard to see anything else at play here.
 APQC
APQC
By contrast, only one out of every 20 respondents said that their organization has robust OT endpoint security measures implemented at scale and optimized, and only one out of every 50 said the same about an OT incident response plan. In other words, very few organizations are fully mature with respect to cyber security preparedness or infrastructure.
It’s time to act
The cybercrime business is booming for bad actors of all kinds, from lone wolf hackers to organized crime and even nation-states. Collectively, we are not focusing enough, investing enough, doing enough, or planning enough to prevent these attacks from occurring or to mitigate the damage when it occurs.
As some high-profile incidents have shown, cyberattacks against OT in supply chains can cripple infrastructure for days and cause billions of dollars in losses. Even if you don’t have a lot of money to invest in cybersecurity for OT right now, at least have a plan in place for how you will act to minimize losses and get back on your feet as quickly as possible when an attack occurs.
[ad_2]
Source link
Click Here For The Original Source.

